2014-08-29 - KULUOZ INFECTION FROM EMAIL ATTACHMENT BY ASPROX BOTNET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-08-29-kuluoz-infection-traffic-from-sandbox-analysis.pcap.zip
- 2014-08-29-malware-from-Kuluoz-infection.zip
NOTES:
- The Asprox botnet continues to send malicious emails.
- This is merely a recent example.
PHISHING EMAIL:
SCREENSHOT:
MESSAGE TEXT:
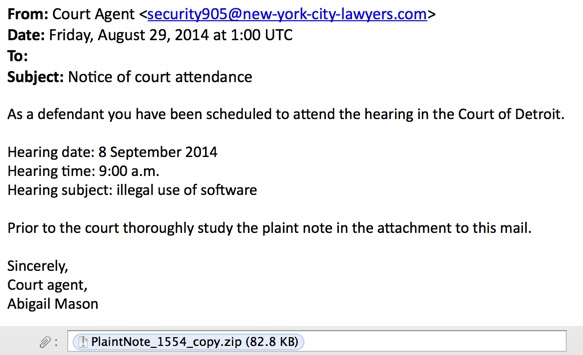
From: Court Agent <security905@new-york-city-lawyers[.]com>
Date: Friday, August 29, 2014 at 1:00 UTC
To:
Subject: Notice of court attendance
As a defendant you have been scheduled to attend the hearing in the Court of Detroit.
Hearing date: 8 September 2014
Hearing time: 9:00 a.m.
Hearing subject: illegal use of software
Prior to the court thoroughly study the plaint note in the attachment to this mail.
Sincerely,
Court agent,
Abigail Mason
Attachment: PlaintNote_1554_copy.zip (82.8)
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
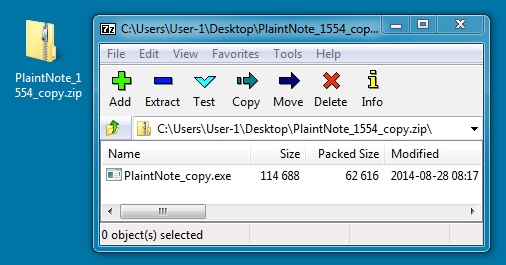
File name: PlaintNote_1554_copy.zip
File size: 62,752 bytes
MD5 hash: 4362e898eaec07b757f95a07032411d0
Detection ratio: 26 / 55
First submission: 2014-08-29 22:22:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/d2d4eac9d07ecf2548497d9aa0609d52438ae55ced6045992338b1e5092a836a/analysis/
EXTRACTED MALWARE:
File name: PlaintNote_copy.exe
File size: 114,688 bytes,
MD5 hash: 88e2cdde9022f7c35647cafd4335d134
Detection ratio: 25 / 55
First submission: 2014-08-29 22:09:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef8947456e520660a0423dc7f3589bf486d9da3e6b84129f7b899438b35ee6c8/analysis/
DROPPED FILE (FROM THE INFECTED HOST - USER'S APPDATA\LOCAL\TEMP FOLDER):
File name: 2014-08-29-phishing-malware-dropped-file.exe
File size: 86,016 bytes
MD5 hash: 5a3001be0abd7e6955cf39a285421279
Detection ratio: 5 / 54
First submission: 2014-08-29 18:38:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/f5cbd7c9d4cf37935bd44081b5695ff837a51e0dce9089645602e7f137b03fab/analysis/
INFECTION TRAFFIC
FROM SANDBOX ANALYSIS OF THE MALWARE:
- 22:15:45 UTC - 209.170.120[.]163:8080 - 209.170.120[.]163:8080 - POST /FD53D33E814055C3E79EA457D05BDD6C8D18FBF7C3
ALERTS FROM SANDBOX ANALYSIS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 209.170.120[.]163:8080 - ETPRO TROJAN Win32/Kuluoz.D Checkin (sid:2807771)
- 209.170.120[.]163:8080 - ET CURRENT_EVENTS Kuluoz/Asprox Activity Dec 23 2013 (sid:2017895)
- 209.170.120[.]163:8080 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 2 (sid:2018359)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-08-29 22:15:45 UTC - 209.170.120[.]163:8080 - [1:31244:2] MALWARE-CNC Win.Trojan.Kuluoz outbound connection attempt
Click here to return to the main page.