2014-09-12 - NUCLEAR EK SENDS SILVERLIGHT EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is the first time I can remember seeing Nuclear EK send a Silverlight exploit.
- Today's payload is the same pharmacy spammer sent lately from Nuclear EK--the one that triggers ET rules for Win32/Tofsee.
PREVIOUS BLOG ENTRIES ON NUCLEAR EK FROM (WHAT I ASSUME IS) THIS SAME ACTOR:
- 2014-09-12 - Nuclear EK from 80.85.85[.]56 - sutileder.dnvgl[.]ro -- gate: 178.62.254[.]78 - quqylife.sydney-bedsheet[.]com/brunigibi16.html
- 2014-09-08 - Nuclear EK from 151.236.216[.]177 - bubleroska.smart-simchah[.]com -- gate: 178.62.147[.]65 - digirosmut.okephone[.]com/eghrhtrhfdgrehh16.html
- 2014-09-04 - Nuclear EK from 80.85.84[.]188 - afridun.autoth[.]com -- gate: 178.62.147[.]62 - puperlikis.taylormadecookies[.]com/ablousdec15.html?%a
- 2014-09-03 - Nuclear EK from 80.85.84[.]142 - giodulder.laurentiucozma[.]ro -- gate: 178.62.147[.]62:80 - ibirtused.nor-365[.]com/ravuekafo15.html
- 2014-08-28 - Nuclear EK from 80.85.84[.]142 - giodulder.laurentiucozma[.]ro -- gate: 178.62.156[.]134:80 - nikajumet.solutionoptic[.]com[.]ar/troisegahol15.html?
- 2014-08-17 - Nuclear EK from 176.58.126[.]215 - gegosima.rubiaguru[.]com[.]ar -- gate: 178.62.174[.]18:80 - exitalis.hulme[.]ca/bubahetar.cgi?15
- 2014-08-01 - Nuclear EK from 85.159.213[.]246 - paraletas.patmos-star[.]com -- gate: 95.85.17[.]107:80 - cucnaterafos.amtranexperts[.]com/roriskajetas15.html
- 2014-07-10 - Nuclear EK from 93.189.40[.]229 - gumeno.yahooaple[.]com -- gate: 188.226.208[.]231 - gosinaj.cynthiamartinez[.]com[.]ar/link15.hotbox
- 2014-06-02 - Nuclear EK from 80.240.139[.]203 - brozdec.uneekstudio[.]com -- gate: 80.240.139[.]203 - brozdec.uneekstudio[.]com/jtrsuyowertdhsrtj13.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 74.220.215[.]91 - incomingit[.]com - Compromised website
- 178.62.254[.]78 - quqylife.sydney-bedsheet[.]com - Redirect
- 80.85.85[.]56 - sutileder.dnvgl[.]ro - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT:
- Original referer: incomingit[.]com/blog/
- 13:39:53 UTC - 74.220.215[.]91:80 - incomingit[.]com - GET /blog/wp-includes/js/scriptaculous/scriptaculous.js?ver=1.8.0
- 13:39:55 UTC - 178.62.254[.]78:80 - quqylife.sydney-bedsheet[.]com - GET /brunigibi16.html
NUCLEAR EK:
- 13:39:56 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /68f5b0c4id43/1/9ffbf35e4190fbba62f70c8477fa3964.html
- 13:40:00 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /3984862731/2/1410529200.xap
- 13:40:01 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /f/2/1410529200/3984862731/8
- 13:40:04 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /3984862731/2/1410529200.swf
- 13:40:15 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /f/2/1410529200/3984862731/7
- 13:40:29 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /3984862731/2/1410529200.pdf
- 13:40:30 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /3984862731/2/1410529200.htm
- 13:40:33 UTC - 80.85.85[.]56:80 - sutileder.dnvgl[.]ro - GET /f/2/1410529200/3984862731/5/x00520804090407000700080150050f030
4045106565601;1;5
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-12-Nuclear-EK-flash-exploit.swf
File size: 5,818 bytes
MD5 hash: 7944c40f927a0f51b49783f5859138e8
Detection ratio: 2 / 53
First submission: 2014-09-12 12:41:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/7d39aa13f1463fd1d7be17a2ba0aa212ab95f76b6eaaaf1442c22c50ca84eee5/analysis/
PDF EXPLOIT:
File name: 2014-09-12-Nuclear-EK-pdf-exploit.pdf
File size: 9,970 bytes
MD5 hash: b8a7e7125298fb722a6f8837f1563fec
Detection ratio: 1 / 53
First submission: 2014-09-12 14:18:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/373523e0cff2e6f13fcf548dd089aed0e6267be98dccff79ef2f2f6aa2e55d9a/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-09-12-Nuclear-EK-silverlight-exploit.xap
File size: 8,283 bytes
MD5 hash: d106b3298ea33fdf8fe12c5aab321b4d
Detection ratio: 1 / 55
First submission: 2014-09-12 14:19:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/409c93d0363a10c28bd3652eb3ae0e95fad74532126243f58e2e01856179ea8b/analysis/
MALWARE PAYLOAD:
File name: 2014-09-12-Nuclear-EK-malware-payload.exe
File size: 331,776 bytes
MD5 hash: 3e98af224acfc0654835f22b2fa55d9b
Detection ratio: 3 / 55
First submission: 2014-09-12 14:19:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/d8a19f7f456554b8093cf84df9544ae8bf8b991b9da7ec959636e31918b55181/analysis/
ALERTS
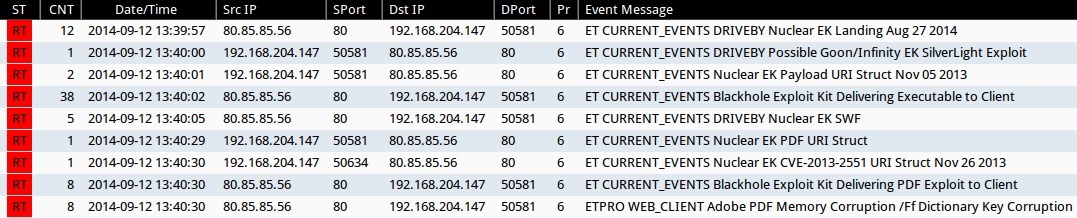
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 13:39:57 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Aug 27 2014 (sid:2019078)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS DRIVEBY Possible Goon/Infinity EK SilverLight Exploit (sid:2018402)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS Nuclear EK PDF URI Struct (sid:2017636)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013 (sid:2017774)
- 13:40:00 UTC - 80.85.85[.]56:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 13:40:00 UTC - 80.85.85[.]56:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 13:39:57 UTC - 80.85.85[.]56:80 - [1:31734:2] EXPLOIT-KIT Nuclear exploit kit landing page detection
- 13:40:00 UTC - 80.85.85[.]56:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x3)
- 13:40:00 UTC - 80.85.85[.]56:80 - [1:22002:5] FILE-IDENTIFY Microsoft Visual Basic v6.0 - additional file magic detected (x3)
- 13:40:02 UTC - 80.85.85[.]56 - [139:1:1] (spp_sdf) SDF Combination Alert (x3)
- 13:40:04 UTC - 74.220.215[.]91:80 - [138:4:1] SENSITIVE-DATA U.S. Social Security Numbers (w/out dashes)
- 13:40:34 UTC - 80.85.85[.]56:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 13:40:34 UTC - 80.85.85[.]56:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
SCREENSHOTS FROM THE TRAFFIC
Malicious iframe in javascript file from compromised website:
Redirect pointing to Nuclear EK:
Nuclear EK delivers Silverlight exploit. I cannot remember seeing a Silverlight from Nuclear EK before:
Click here to return to the main page.





