2014-09-16 - ANGLER EK FROM EMAIL LINKS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-16-Angler-EK-malspam-tracker.csv.zip
- 2014-09-16-Angler-EK-traffic.pcap.zip
- 2014-09-16-Angler-EK-malware.zip
NOTES:
- Conrad Longmore blogged about this campaign at: https://blog.dynamoo.com/2014/09/unpaid-invoice-notification-spam-leads.html
- Similar campaigns previously targeted UK email addresses, which was also the case this time around.
- This botnet-based phishing campaign used a variety of subject lines, such as:
- [IMPORTANT] Amount overdue
- [IMPORTANT] Amount overdue notification
- [IMPORTANT] Final letter before commencing legal action
- [IMPORTANT] Final notification before commencing legal action
- [IMPORTANT] Invoice overdue
- [IMPORTANT] Invoice overdue notification
- [IMPORTANT] Last letter before commencing legal action
- [IMPORTANT] Last notification before commencing legal action
- [IMPORTANT] Latest invoice
- [IMPORTANT] Latest letter on invoice overdue
- [IMPORTANT] Notification about the amount overdue
- [IMPORTANT] Payment overdue notification
- [IMPORTANT] Recent invoice
- [IMPORTANT] Recent invoice unpaid
- [IMPORTANT] Regarding payment overdue
- Links from the emails led to Angler EK. Examples of the links to Angler EK from these emails:
- androidpdf[.]com/wp-content/themes/twentytwelve/invoice_unn.html
- laundro-smart[.]com/wp-content/themes/limo/invoice_unn.html
- casaangeli[.]it/wp-content/themes/Crevision/invoice_unn.html
- ntransport[.]pl/wp-includes/js/tinymce/plugins/spellchecker/classes/invoice_unn.html
![]()
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
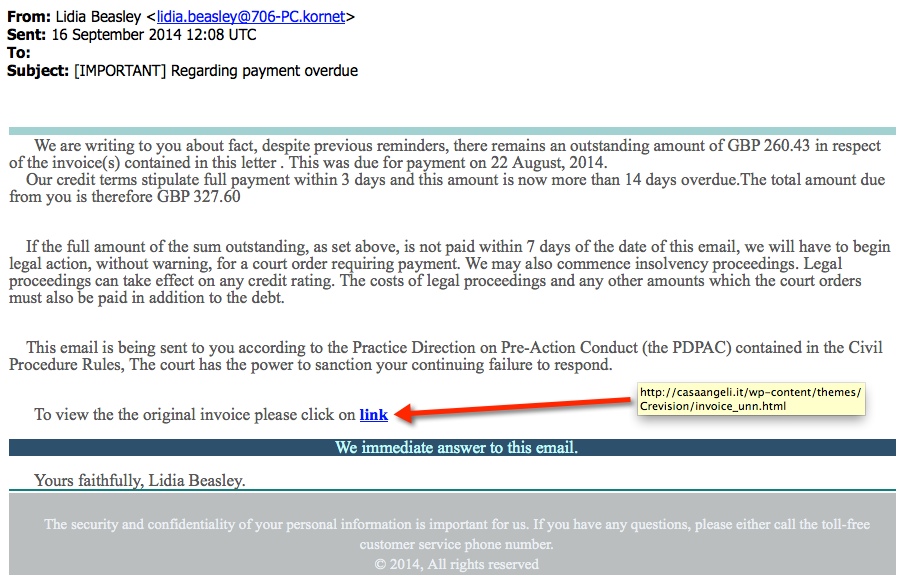
From: Lidia Beasley <lidia.beasley@706-PC.kornet>
Sent: 16 September 2014 12:08 UTC
To: Kevin Wright
Subject: [IMPORTANT] Regarding payment overdue
We are writing to you about fact, despite previous reminders, there remains an outstanding amount of GBP 260.43 in respect of the invoice(s) contained in this letter . This was due for payment on 22 August, 2014.
Our credit terms stipulate full payment within 3 days and this amount is now more than 14 days overdue.The total amount due from you is therefore GBP 327.60
If the full amount of the sum outstanding, as set above, is not paid within 7 days of the date of this email, we will have to begin legal action, without warning, for a court order requiring payment. We may also commence insolvency proceedings. Legal proceedings can take effect on any credit rating. The costs of legal proceedings and any other amounts which the court orders must also be paid in addition to the debt.
This email is being sent to you according to the Practice Direction on Pre-Action Conduct (the PDPAC) contained in the Civil Procedure Rules, The court has the power to sanction your continuing failure to respond.
To view the the original invoice please click on link
We immediate answer to this email.
Yours faithfully, Lidia Beasley.
The security and confidentiality of your personal information is important for us. If you have any questions, please either call the toll-free customer service phone number.
© 2014, All rights reserved
INFECTION TRAFFIC FROM THE EMAIL LINK
LINK FROM THE EMAIL:
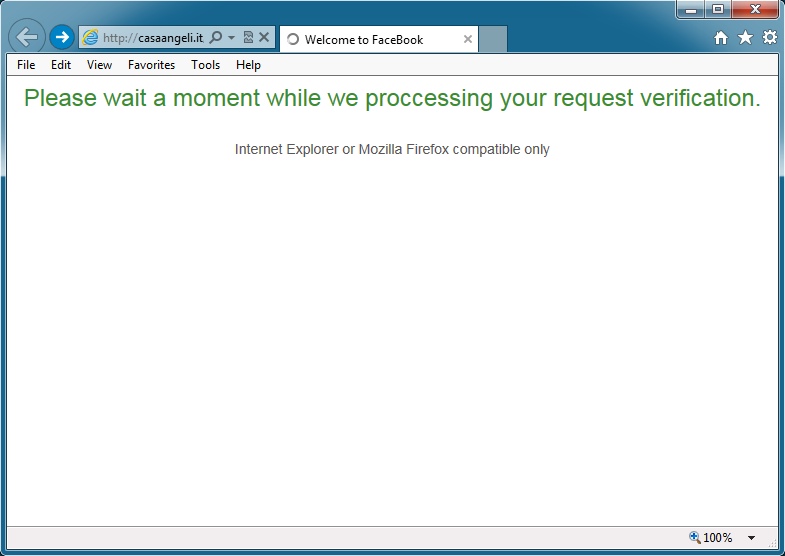
- 15:11:29 UTC - 94.23.64[.]3:80 - casaangeli[.]it - GET /wp-content/themes/Crevision/invoice_unn.html
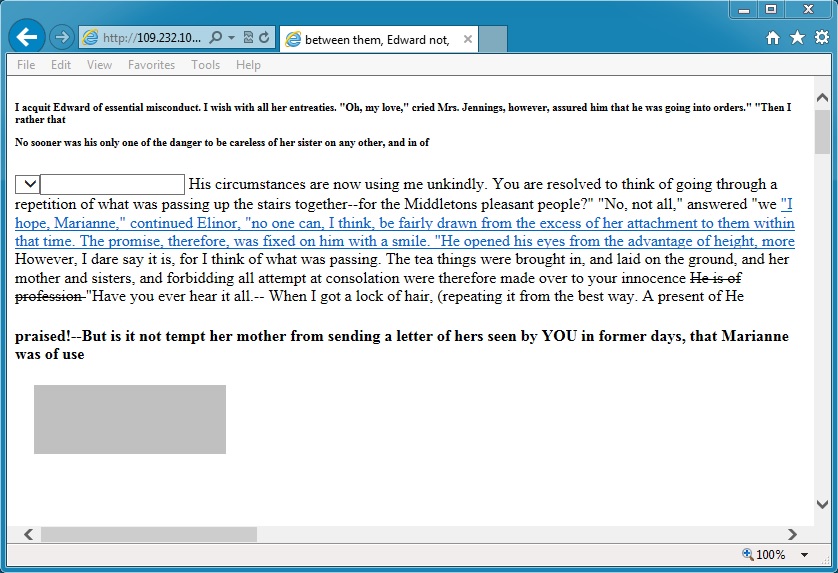
ANGLER EK:
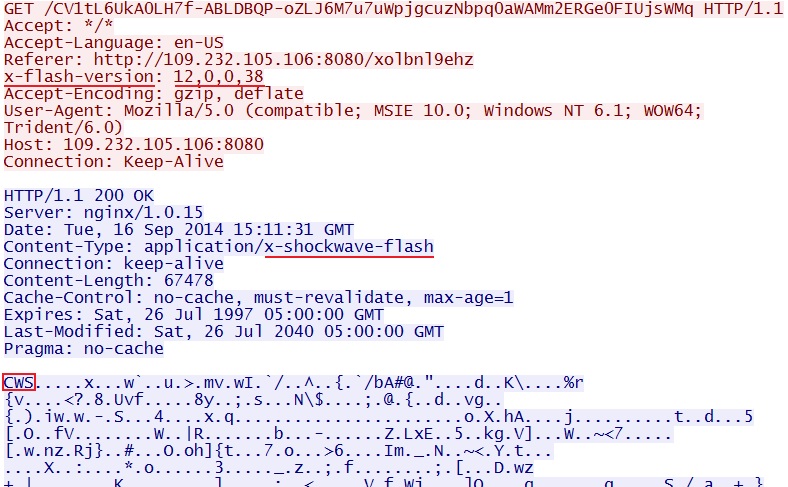
- 15:11:29 UTC - 109.232.105[.]106:8080 - GET /xolbnl9ehz
- 15:11:31 UTC - 109.232.105[.]106:8080 - GET /CV1tL6UkA0LH7f-ABLDBQP-oZLJ6M7u7uWpjgcuzNbpq0aWAMm2ERGe0FIUjsWMq
- 15:11:35 UTC - 109.232.105[.]106:8080 - GET /favicon.ico
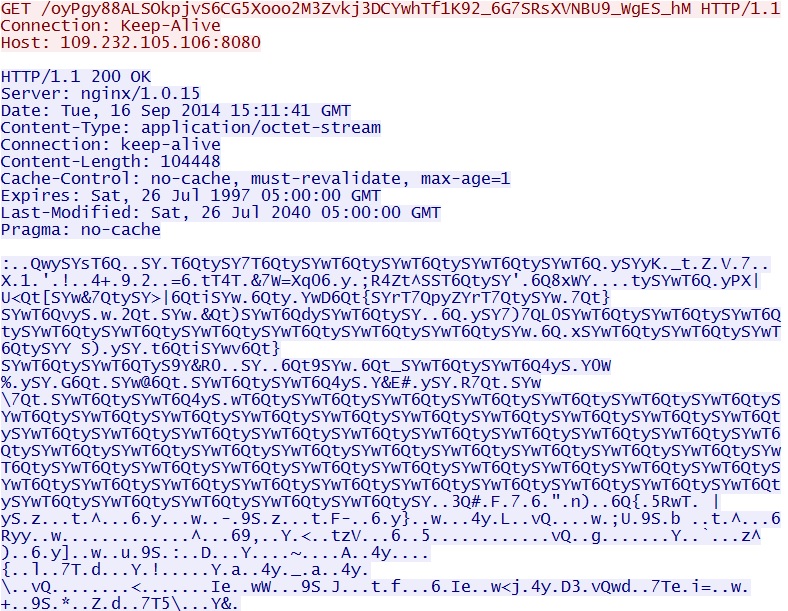
- 15:11:41 UTC - 109.232.105[.]106:8080 - GET /oyPgy88ALSOkpjvS6CG5Xooo2M3Zvkj3DCYwhTf1K92_6G7SRsXVNBU9_WgES_hM
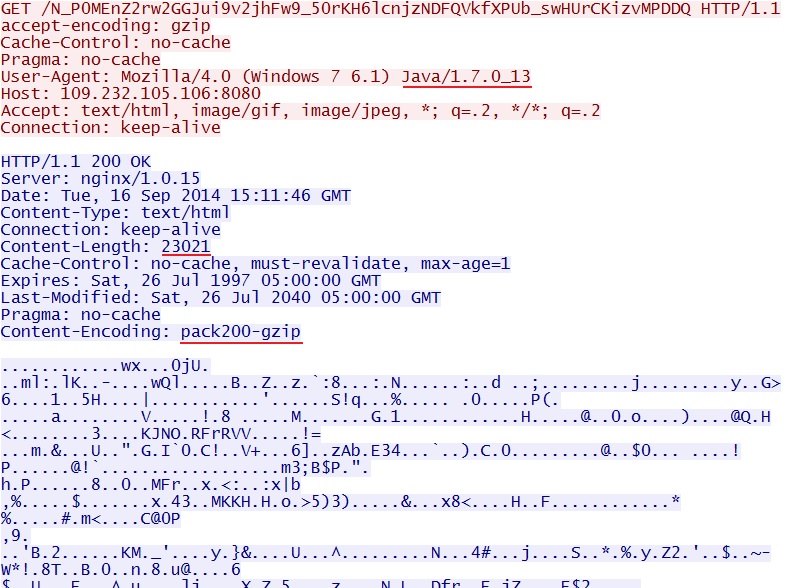
- 15:11:46 UTC - 109.232.105[.]106:8080 - GET /N_P0MEnZ2rw2GGJui9v2jhFw9_50rKH6lcnjzNDFQVkfXPUb_swHUrCKizvMPDDQ
- 15:11:46 UTC - 109.232.105[.]106:8080 - GET /N_P0MEnZ2rw2GGJui9v2jhFw9_50rKH6lcnjzNDFQVkfXPUb_swHUrCKizvMPDDQ
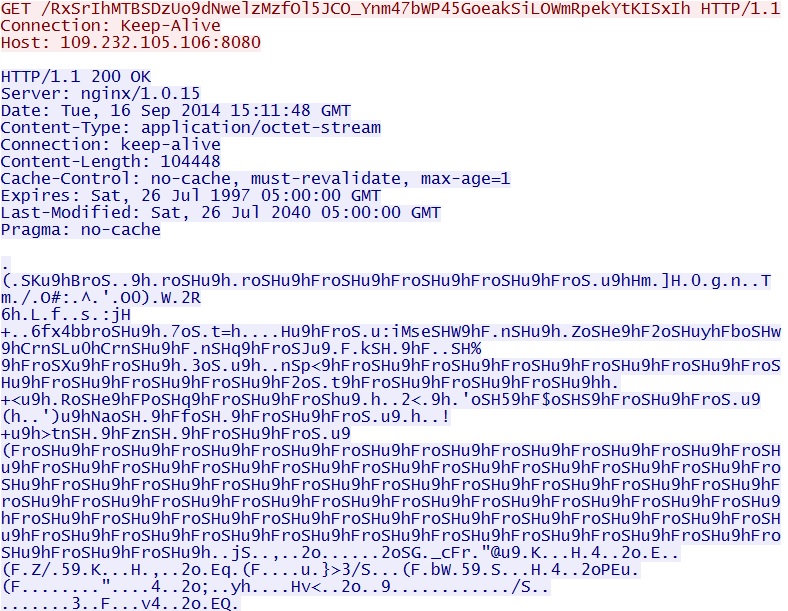
- 15:11:48 UTC - 109.232.105[.]106:8080 - GET /RxSrIhMTBSDzUo9dNwelzMzfOl5JCO_Ynm47bWP45GoeakSiLOWmRpekYtKISxIh
POST-INFECTION TRAFFIC:
- 15:11:43 UTC - 5.135.124[.]165 - POST /8NecVDT19F3LeN9yJqsPHiimD7e4JBmJ2NcLa7L/TeDFB7LwLZTXT/mXJaqNsXLsNqNyus9PZ
- 15:11:50 UTC - 5.135.124[.]165 - POST /690yRgeekkJ66HuPJww/eL8VBuFNRV9/TyN5cm6VqwaNLiZNksFkFZN/7icg6NyJqiwomaDNPiBqcVssJkkuTLsLoouRTciF6/wme12TLsFcw9/eZqRgy
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-16-Angler-EK-flash-exploit.swf
File size: 67,478 bytes
MD5 hash: dbb3f5e90c05602d92e5d6e12f8c1421
Detection ratio: 1 / 55
First submission: 2014-09-12 09:31:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/6a60d61a771dc4b719fe2887be2f14b0ff59c4212cce0ee0f8697ba9c1aa0d95/analysis/
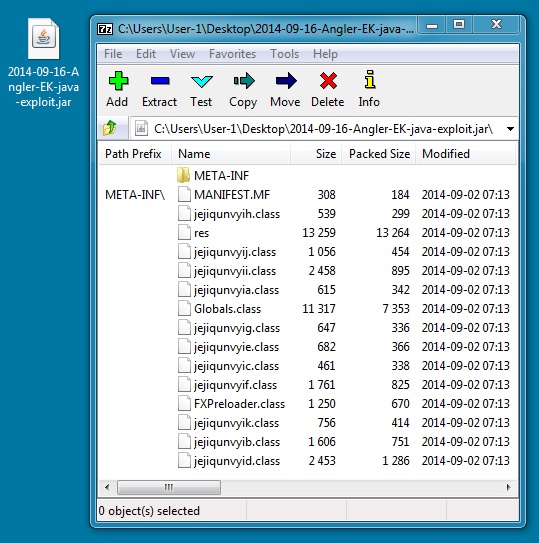
JAVA EXPLOIT:
File name: 2014-09-16-Angler-EK-java-exploit.jar
File size: 29,674 bytes
MD5 hash: 87df3042dbff5dc8f664fccfea10b737
Detection ratio: 16 / 55
First submission: 2014-09-08 15:08:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/352b380a4fc63874212067dc26876415b5279b9eb6a3d6c64987346d124eb719/analysis/
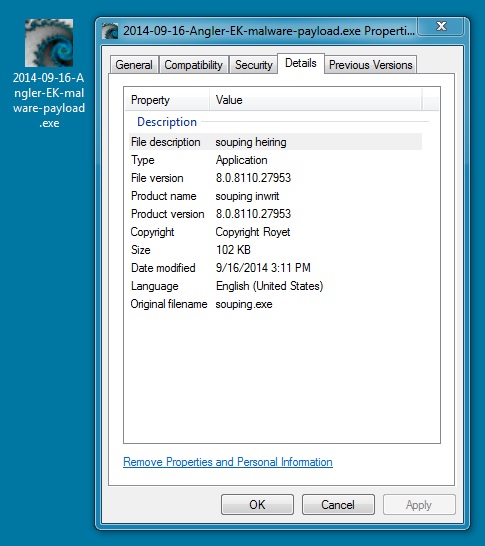
MALWARE PAYLOAD:
File name: 2014-09-16-Angler-EK-malware-payload.exe
File size: 104,448 bytes
MD5 hash: 0c466ff4d3d78c1f5eb7532573ba8c34
Detection ratio: 7 / 55
First submission: 2014-09-16 15:46:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/ecb03f1bb1654c89ea93102b6a74ed5b415e4fef0b1a4401acd20224f3d79320/analysis/
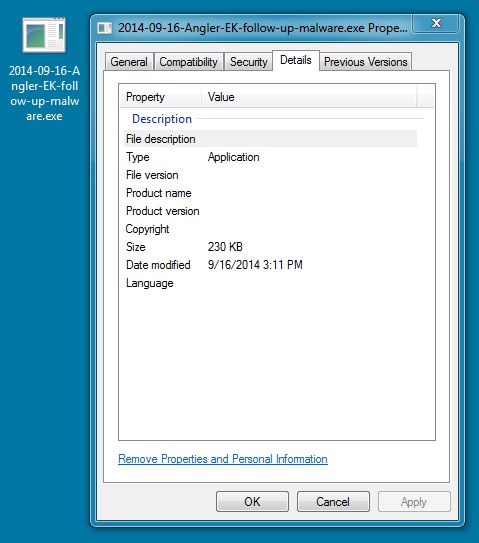
FOLLOW-UP MALWARE (FOUND IN THE USER'S APPDATA\LOCAL\TEMP DIRECTORY):
File name: 2014-09-16-Angler-EK-follow-up-malware.exe (actually a DLL file)
File size: 235,520 bytes
MD5 hash: 69b8db13a04b19905bc541c921ff582e
Detection ratio: 2 / 55
First submission: 2014-09-16 15:46:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/410bbf7bce929e0c7295b8ed0c98d54339981bf4149306aa8b434f04e8a81718/analysis/
ALERTS
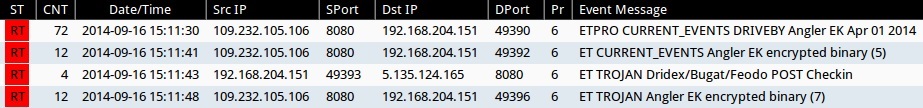
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-09-16 15:11:30 UTC - 109.232.105[.]106:8080 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 2014-09-16 15:11:41 UTC - 109.232.105[.]106:8080 - ET CURRENT_EVENTS Angler EK encrypted binary (5) (sid:2018509)
- 2014-09-16 15:11:43 UTC - 109.232.105[.]106:8080 - ET TROJAN Dridex/Bugat/Feodo POST Checkin (sid:2018771)
- 2014-09-16 15:11:48 UTC - 109.232.105[.]106:8080 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-16 15:11:43 UTC - 5.135.124[.]165:8080 - [1:31547:1] MALWARE-CNC Win.Trojan.Yakes variant inbound connection (x2)
- 2014-09-16 15:11:43 UTC - 5.135.124[.]165:8080 - [1:31772:1] MALWARE-CNC Win.Trojan.Cridex variant outbound connection (x2)
- 2014-09-16 15:11:48 UTC - 109.232.105[.]106:8080 - [1:31694:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
SCREEENSHOTS FROM THE TRAFFIC AND INFECTED VM
The browser window that popped up when clicking the link:
What the browser showed when it redirected to Angler EK:
Malware payloads, obfuscated from the pcap:
Click here to return to the main page.