2014-10-04 - RIG EK AND UPATRE FROM EMAIL LINKS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
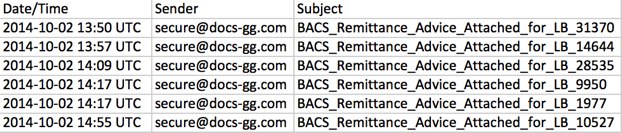
- On Thursday, 2014-10-02, I saw a few emails with secure@docs-gg[.]com listed as a sender that went to UK email addresses.
- These emails contain links to a zip file; however, these URLs also generate Rig EK traffic that will infect a vulnerable host with the same malware.
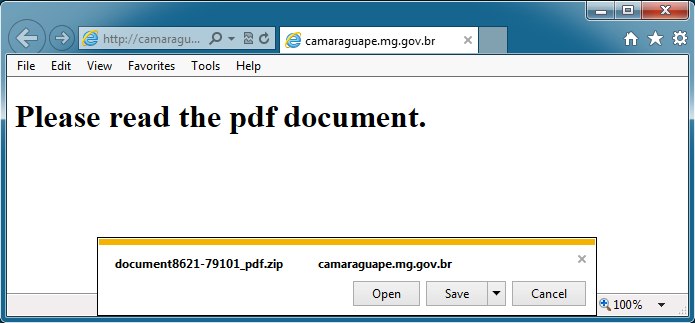
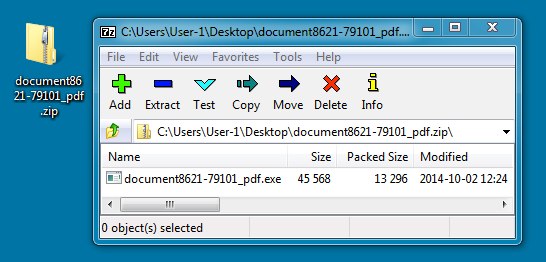
Shown above: The zip file offered as a download, while Rig EK happens in the background.
- Today's Upatre and follow-up malware are the same type I documented yesterday on 2014-10-03 (see the link below).
WAVES OF PHISHING EMAILS I'VE DOCUMENTED BY (WHAT I THINK IS) THE SAME ACTOR:
- 2014-09-18 - Phishing campaign - NatWest and fake fax messages
- 2014-09-22 - Phishing email - Subject: NatWest Statement
- 2014-10-03 - Phishing campaign - Incoming fax reports - fake HMRC tax notices
- 2014-10-04 - Rig EK and Upatre from phishing emails [emails dated 2014-10-02]
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 177.55.108[.]130 - camaraguape.mg[.]gov[.]br - Site with page for the malware download
- 37.200.69[.]87 - story.christophertawes[.]com - Rig EK
- various IP addresses - various domains - Post-infection traffic (see below)
PHISHING LINK FROM THE EMAIL (PROVIDES A ZIP FILE OF THE MALWARE):
- 2014-10-04 00:29:25 UTC - 177.55.108[.]130:80 - camaraguape.mg[.]gov[.]br - GET /go2/document.php
- 2014-10-04 00:29:27 UTC - 177.55.108[.]130:80 - camaraguape.mg[.]gov[.]br - POST /go2/document.php
- 2014-10-04 00:29:33 UTC - 91.121.220.193:80 - counter6.statcounterfree[.]com - GET /private/counter.js?c=
a9f26a8b178b1b373c1d6618b0a2ea72 - 2014-10-04 00:29:40 UTC - 177.55.108[.]130:80 - camaraguape.mg[.]gov[.]br - GET /go2/document.php?h=900&w=1440&ua=
Mozilla%2F4.0%20(compatible%3B%20MSIE%208.0%3B%20Windows%20NT%206.1%3B%20WOW64%3B%20Trident%2F4.0%3B%20SLCC2
%3B%20.NET%20CLR%202.0.50727%3B%20.NET%20CLR%203.5.30729%3B%20.NET%20CLR%203.0.30729%3B%20Media%20Center%20PC%206.0)&e=1
RIG EK (INFECTS A VULNERABLE HOST WITH THE SAME MALWARE):
- 2014-10-04 00:29:33 UTC - 37.200.69[.]87:80 - story.christophertawes[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDYxYWNlYzQwZDU3NDM0MzMyOGE4ZmU0NDU5ZjM1ZjE - 2014-10-04 00:29:37 UTC - 37.200.69[.]87:80 - story.christophertawes[.]com - GET /index.php?req=mp3&num=95&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZDYxYWNlYzQwZDU3NDM0MzMyOGE4ZmU0NDU5ZjM1ZjE - 2014-10-04 00:29:39 UTC - 37.200.69[.]87:80 - story.christophertawes[.]com - GET /index.php?req=swf&num=467&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDYxYWNlYzQwZDU3NDM0MzMyOGE4ZmU0NDU5ZjM1ZjE - 2014-10-04 00:29:46 UTC - 37.200.69[.]87:80 - story.christophertawes[.]com - GET /index.php?req=xml&num=4797&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDYxYWNlYzQwZDU3NDM0MzMyOGE4ZmU0NDU5ZjM1ZjE - 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - story.christophertawes[.]com - GET /index.php?req=jar&num=6704&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZDYxYWNlYzQwZDU3NDM0MzMyOGE4ZmU0NDU5ZjM1ZjE - 2014-10-04 00:29:48 UTC - 37.200.69[.]87:80 - story.christophertawes[.]com - GET /index.php?req=mp3&num=479131&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZDYxYWNlYzQwZDU3NDM0MzMyOGE4ZmU0NDU5ZjM1ZjE
POST-INFECTION TRAFFIC:
- 2014-10-04 00:29:43 UTC - 82.98.157[.]8:80 - msoluciona[.]com - GET /images/inicio/0210uk4.pdf
- 2014-10-04 00:29:44 UTC - 82.98.157[.]8:80 - www.msoluciona[.]com - GET /images/inicio/0210uk4.pdf
- 2014-10-04 00:29:53 UTC - 66.51.128[.]43:3478 - STUN traffic to stun.voip.aebc[.]com
- 2014-10-04 00:30:27 UTC - 77.72.169[.]155:3478 - STUN traffic to stun.voiparound[.]com
- 2014-10-04 00:30:45 UTC - 77.72.169[.]154:3479 - STUN traffic to stun.voiparound[.]com
- 2014-10-04 00:31:03 UTC - 203.183.172[.]196 - STUN traffic to s2.taraba[.]net
- 2014-10-04 00:31:21 UTC - 203.183.172[.]212 - STUN traffic to s2.taraba[.]net (?)
- 2014-10-04 00:29:39 UTC - 188.165.198[.]52:64078 - attempted TCP connection RST by server
- 2014-10-04 00:29:41 UTC - 188.165.198[.]52:64078 - attempted TCP connection RST by server
- 2014-10-04 00:29:47 UTC - 188.165.198[.]52:64078 - attempted TCP connection RST by server
- 2014-10-04 00:31:39 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:42 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:43 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:43 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:46 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:46 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:49 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:49 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
- 2014-10-04 00:31:54 UTC - 37.59.46[.]50:4443 - encrypted TCP traffic
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-04-Rig-EK-flash-exploit.swf
File size: 4,238 bytes
MD5 hash: 1ca3694873a7975dc4a286e11799a004
Detection ratio: 2 / 54
First submission: 2014-10-02 07:51:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/3f0c210787ecd044c48792635998e4574a4c5abed1b150c02c62083b757b02f9/analysis/
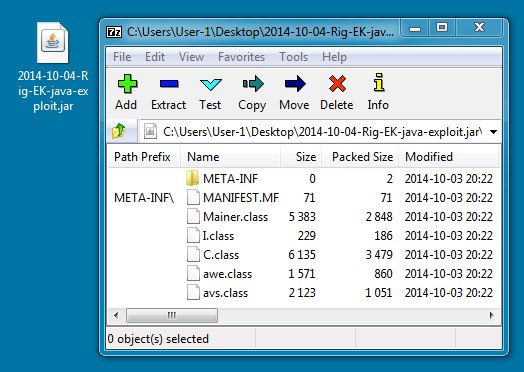
JAVA EXPLOIT:
File name: 2014-10-04-Rig-EK-java-exploit.jar
File size: 9,380 bytes
MD5 hash: 3fd18b6e0fb0f88d897fadbeae36c860
Detection ratio: 5 / 55
First submission: 2014-10-04 02:19:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/4840f1d8a86e25528b4b6931d5cfa198b9afef5bd84c7544a81b6a706f405960/analysis/
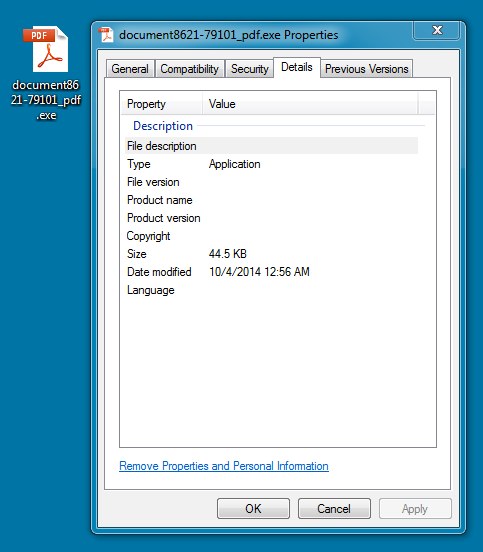
MALWARE PAYLOAD (SAME AS EXTRACTED MALWARE FROM ZIP FILE):
File name: document8621-79101_pdf.exe
File size: 45,568 bytes
MD5 hash: 322cc3be1d5b0c41d707867146304d85
Detection ratio: 23 / 53
First submission: 2014-10-02 14:42:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/3ac7b3e1c679134d3b63793dc6df49f8467f387b78e17947a22b516636b89aed/analysis/
ZIPE ARCHIVE FROM THE WEB PAGE:
File name: document8621-79101_pdf.zip
File size: 13,446 bytes
MD5 hash: c516abc8eb1acd38c57f3175032cb17c
Detection ratio: 26 / 55
First submission: 2014-10-02 14:40:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/39d8f256dcb91eab3c92dae72ab54fbb38157847336646ce23f26924f59a4b33/analysis/
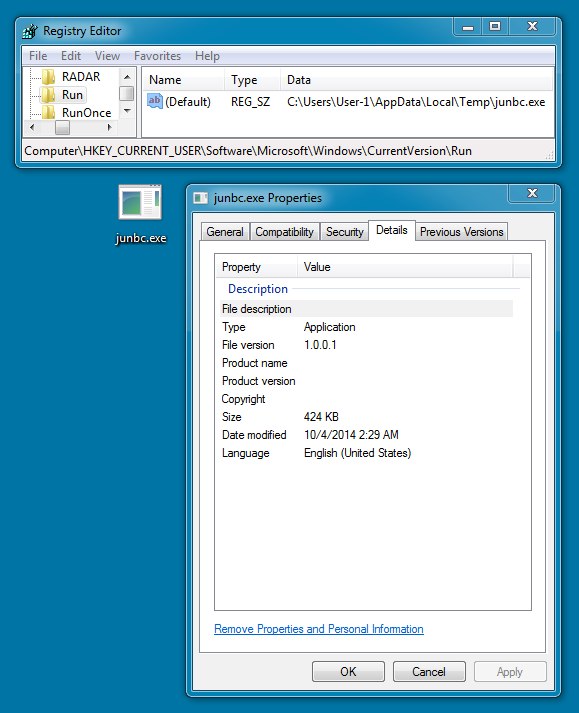
FOLLOW-UP MALWARE:
File name: junbc.exe
File size: 434,176 bytes
MD5 hash: 27b8d15950022f53ca4ca7004932cf2b
Detection ratio: 21 / 54
First submission: 2014-10-02 18:44:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/286938569b92147be5ec50e06d4d7429eb442a751c0772cb57e146a0a1d0b489/analysis/
SNORT EVENTS
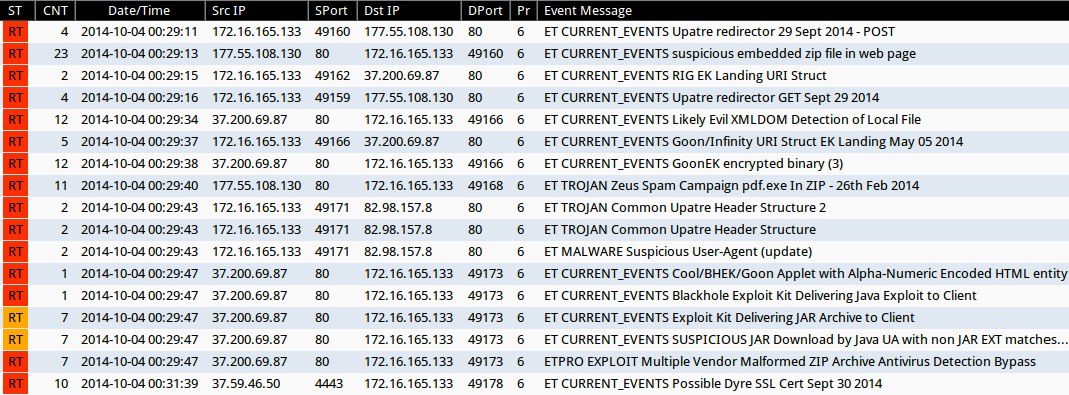
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-10-04 00:29:11 UTC - 177.55.108[.]130:80 - ET CURRENT_EVENTS Upatre redirector 29 Sept 2014 - POST (sid:2019321)
- 2014-10-04 00:29:13 UTC - 177.55.108[.]130:80 - ET CURRENT_EVENTS suspicious embedded zip file in web page (sid:2019324)
- 2014-10-04 00:29:15 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 2014-10-04 00:29:16 UTC - 177.55.108[.]130:80 - ET CURRENT_EVENTS Upatre redirector GET Sept 29 2014 (sid:2019311)
- 2014-10-04 00:29:34 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 2014-10-04 00:29:37 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-10-04 00:29:38 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 2014-10-04 00:29:40 UTC - 177.55.108[.]130:80 - ET TROJAN Zeus Spam Campaign pdf.exe In ZIP - 26th Feb 2014 (sid:2018182)
- 2014-10-04 00:29:43 UTC - 82.98.157[.]8:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 2014-10-04 00:29:43 UTC - 82.98.157[.]8:80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 2014-10-04 00:29:43 UTC - 82.98.157[.]8:80 - ET MALWARE Suspicious User-Agent (update) (sid:2003583)
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Cool/BHEK/Goon Applet with Alpha-Numeric Encoded HTML entity (sid:2017064)
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Java Exploit to Client (sid:2013961)
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 2014-10-04 00:31:39 UTC - 37.59.46[.]50:4443 - ET CURRENT_EVENTS Possible Dyre SSL Cert Sept 30 2014 (sid:2019320)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not including preprocessor events):
- 2014-10-04 00:29:37 UTC - 37.200.69[.]87:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure (x5)
- 2014-10-04 00:29:38 UTC - 37.200.69[.]87:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - [1:25562:4] FILE-JAVA Oracle Java obfuscated jar file download attempt
- 2014-10-04 00:29:47 UTC - 37.200.69[.]87:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
Click here to return to the main page.