2014-11-12 - ASPROX BOTNET FAKE STARBUCKS EMAILS DELIVERED SIRIUS WIN 7 ANTIVIRUS 2014
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-12-Asprox-malware-and-artifacts.zip 369.8 kB (369,756 bytes)
- 2014-11-12-Asprox-malspam-6-examples.zip 12.8 kB (12,792 bytes)
NOTES:
- Saw a fresh wave of fake Starbucks emails from the Asprox botnet today. The links point to a zip file that infected my VM with malware called: Sirius Win 7 Antivirus 2014
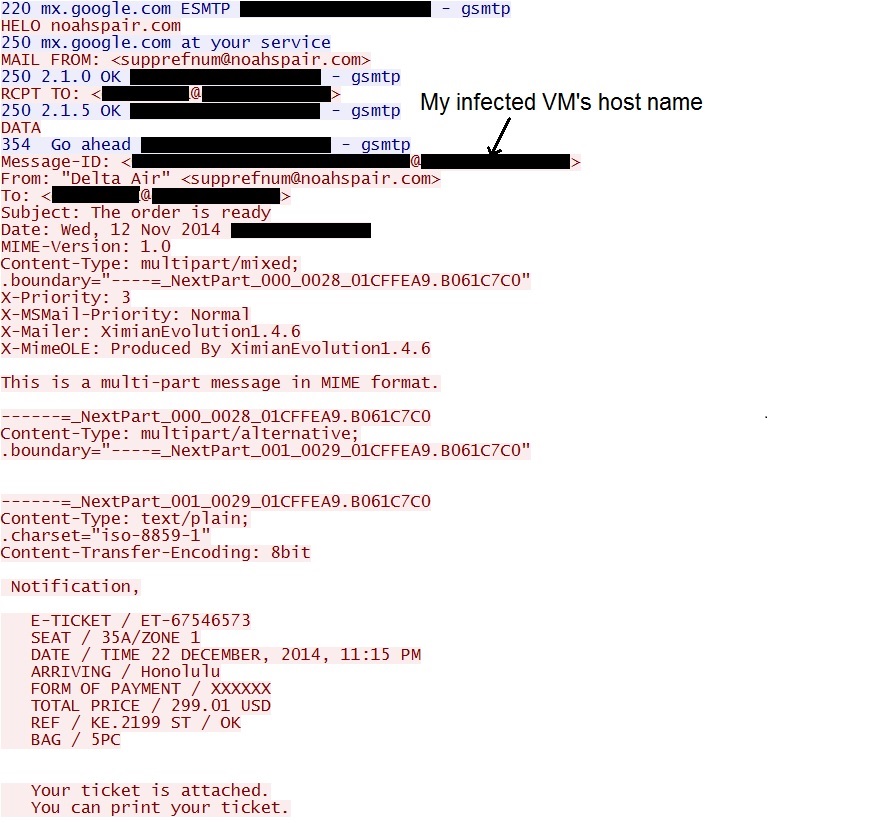
- My infected VM also did a bit of spamming, sending out fake Delta Airlines phishing emails before I took it off-line.
EXAMPLE OF THE EMAILS
SCREENSHOTS:
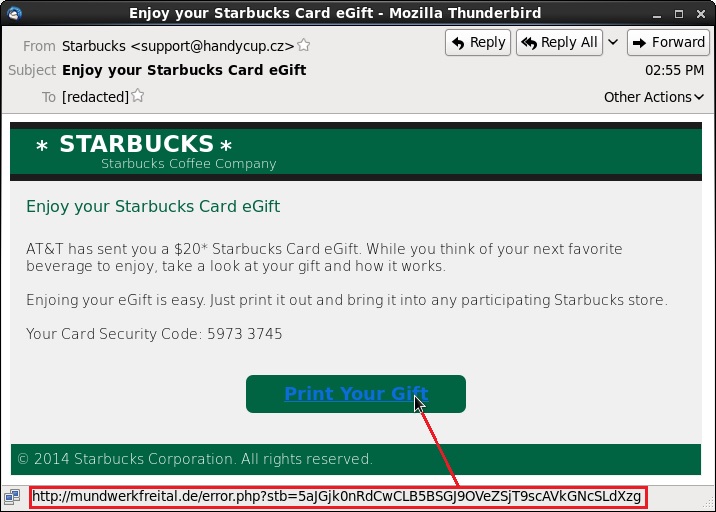
All six emails were fake Starbucks messages received on 2014-11-12, but this one has a few mistakes and
looks like it was originally sent on 2014-11-10.
LINK TO MALWARE FROM THESE EMAILS:
From: "Starbucks" <support@handycup[.]cz>
Subject: Enjoy your Starbucks Card eGift
Link: mundwerkfreital[.]de/error.php?stb=5aJGjk0nRdCwCLB5BSGJ9OVeZSjT9scAVkGNcSLdXzg
From: "Starbucks" <support@freighttraindigital[.]com>
Subject: Enjoy your Starbucks Card eGift
Link: ritphipsi[.]org/diff.php?stb=skw1QZozuKje0qjjrhzL8CaR1KIHwp6lcrmQ4iBrjpM
From: "Starbucks" <support@ulg.mediagiantdesign[.]com>
Subject: Starbucks Card eGift
Link: stormgeeks[.]com/dump.php?stb=KlHUP9Acz83sJOW8xdPVxSTPjF+I+6G6JrxViBND/C8
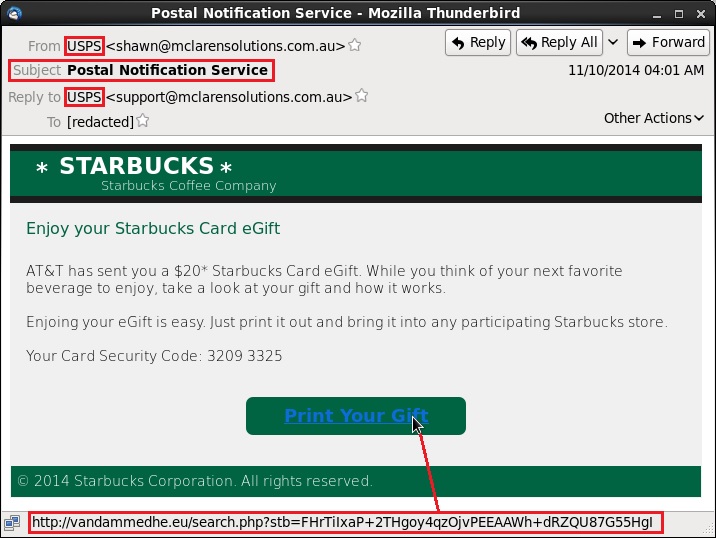
From: USPS <shawn@mclarensolutions[.]com[.]au>
Subject: Postal Notification Service
Link: vandammedhe[.]eu/search.php?stb=FHrTiIxaP+2THgoy4qzOjvPEEAAWh+dRZQU87G55HgI
From: "Starbucks" <support@alvarogl[.]com>
Subject: Starbucks Card eGift
Link: owireduyeboahandassociates[.]com/login.php?stb=UIUE39nFGpVxycMpyCfnSIc92jjwrISVcGz21oaNhTs
From: "Starbucks" <support@geldersespringkussenverhuur[.]nl>
Subject: Enjoy your Starbucks Card eGift
Link: postprodsons[.]com/defines.php?stb=9VyzWC5VJcDySbbeoYEaUqxjDeIjSUgpUpFpqT3M6Zo
PRELIMINARY MALWARE ANALYSIS
DOWNLOADED ZIP FILE:
File name: Starbucks_eGift.zip
File size: 71,950 bytes
MD5 hash: 3cb651464905715a0a571f6bd434a7a9
Detection ratio: 13 / 55
First submission: 2014-11-12 19:25:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/e6dc1655d31aec69533d9c8bec205615a164b66eed48176cd63140707a3a5cde/analysis/
EXTRACTED MALWARE:
File name: Starbucks_eGift.exe
File size: 109,568 bytes
MD5 hash: 37f9766153ea52766d11839868f10648
Detection ratio: 13 / 55
First submission: 2014-11-12 19:25:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/c21d40e8cd713a1dbdf6491abd9ce3dc11ba3f3312c7081fcb3be353b8b8e89f/analysis/
SOME DROPPED ARTIFACTS ON THE INFECTED VM:
DROPPED EXE (1 OF 2):
File name: pvmqjsqv.exe
File size: 111,616 bytes
MD5 hash: 3a682c34371938570231f466be7c53a8
Detection ratio: 5 / 54
First submission: 2014-11-12 19:26:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/a8ee33e4d8fc0900a3b99aff70437d4b878c7031eca48928300234e48938c77a/analysis/
DROPPED EXE (2 OF 2):
File name: reqxtpxq.exe
File size: 80.5 KB ( 82432 bytes )
MD5 hash: eae6fd5531d1101332b47b33ac7bdad3
Detection ratio: 4 / 53
First submission: 2014-11-12 17:23:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/0b1bfdd4a4fce450429fb9494b5d860cc1a0bdb2e4a122790596aa01bd6aa55e/analysis/
INFECTION TRAFFIC
DOWNLOADING THE MALWARE FROM LINK IN THE EMAIL:
- 18:27:18 UTC - 185.21.100[.]134:80 - mundwerkfreital[.]de - GET /error.php?stb=5aJGjk0nRdCwCLB5BSGJ9OVeZSjT9scAVkGNcSLdXzg
INFECTION TRAFFIC WHEN RUNNING THE MALWARE AND SEEING THE FAKE ANTI-VIRUS:
- 18:34:01 UTC - 212.129.21[.]210:443 - POST /index.php
- 18:34:09 UTC - 89.144.14[.]44:80 - glohhstt7.com - GET /FiGcq15uk9c0jEnSjQhDBrRmh4c5HvCnn8aPPAvnpVV2L9p2jjtNsJJPyVqNhQ==
- 18:36:04 UTC - 212.129.21[.]210:443 - POST /index.php
- 18:38:08 UTC - 212.129.21[.]210:443 - POST /index.php
- 18:40:10 UTC - 212.129.21[.]210:443 - POST /index.php
- 18:40:12 UTC - 212.26.132[.]65:443 - POST /cb/board.pl
- 18:42:33 UTC - 212.129.21[.]210:443 - POST /index.php
- 18:44:35 UTC - 212.129.21[.]210:443 - POST /index.php
- 18:46:29 UTC - 72.51.46[.]206:8080 - POST /cb/board.pl
- 18:46:37 UTC - 212.129.21[.]210:443 - POST /index.php
- Lots of SMTP traffic [I let this run much longer than I intended...]
TRAFFIC FOR THE WEB PAGE THAT APPEARED WHEN I CLICKED TO REGISTER THE PRODUCT:
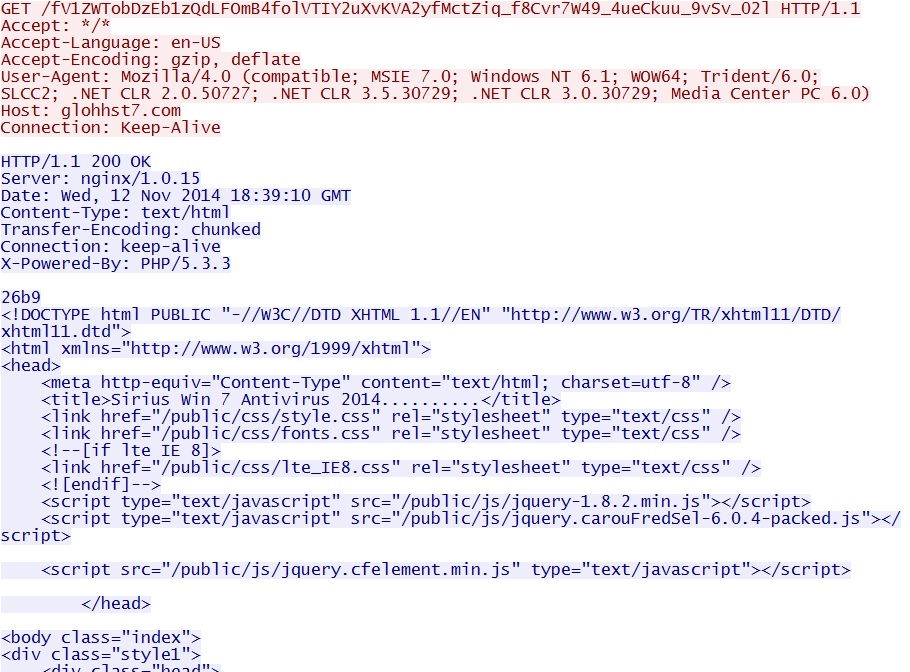
- 18:39:10 UTC - 89.144.14[.]44:80 - glohhst7[.]com - GET /fV1ZWTobDzEb1zQdLFOmB4folVTIY2uXvKVA2yfMctZiq_f8Cvr7W49_4ueCkuu_9vSv_02l
- 18:39:10 UTC - 89.144.14[.]44:80 - glohhst7[.]com - serveral other HTTP GET requests for the web page components
SNORT EVENTS
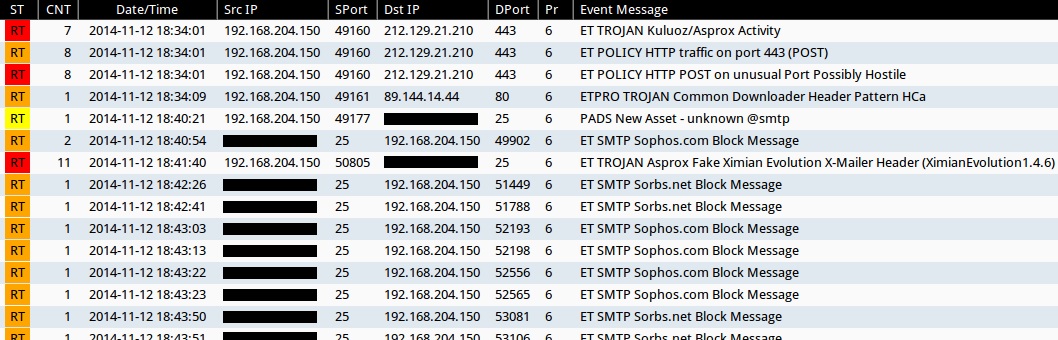
Signature hits from Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- ET TROJAN Kuluoz/Asprox Activity (sid:2017895)
- ET TROJAN Kuluoz/Asprox CnC Response (sid:2019187)
- ET TROJAN Asprox Fake Ximian Evolution X-Mailer Header (XimianEvolution1.4.6) (sid:2018336)
- ETPRO TROJAN Common Downloader Header Pattern HCa (sid:2803304)
SCREENSHOTS
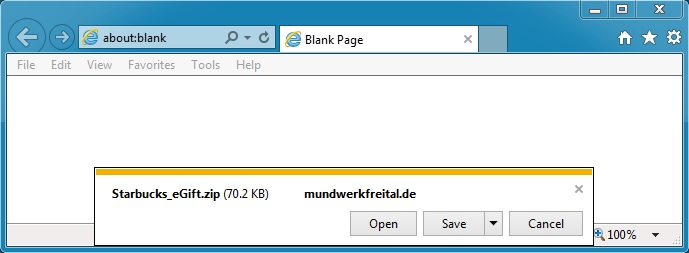
Trying one of the email links in a web browser got me the malicious zip file:
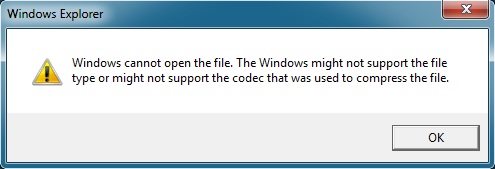
When I ran the fake Starbucks malware, I got the following message:
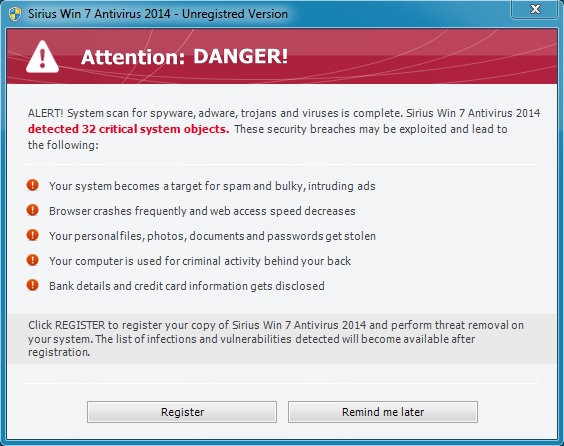
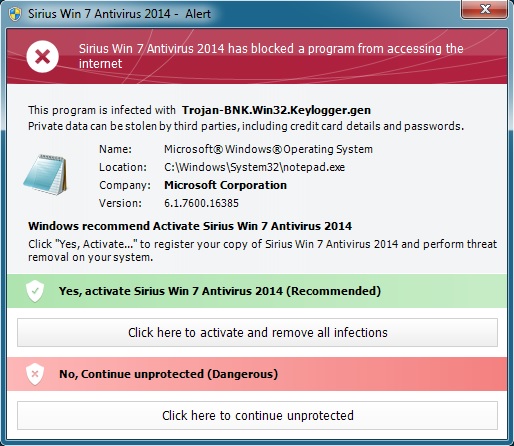
Shortly after running the malware, I got a notification from the fake anti-virus that my system had been breached:
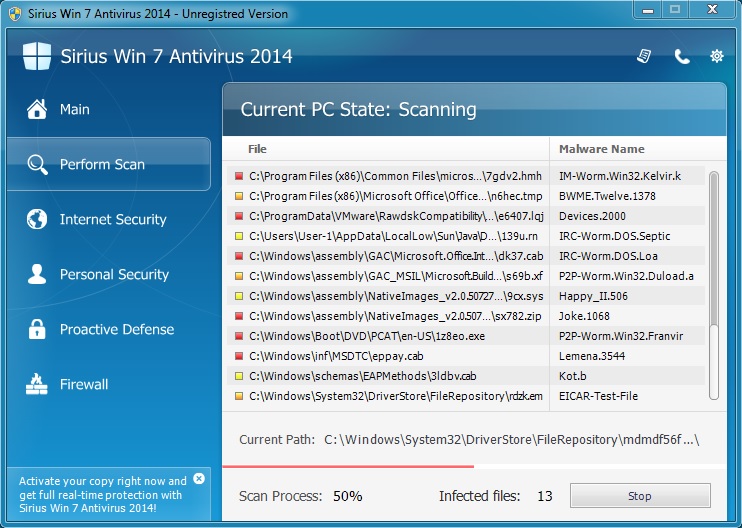
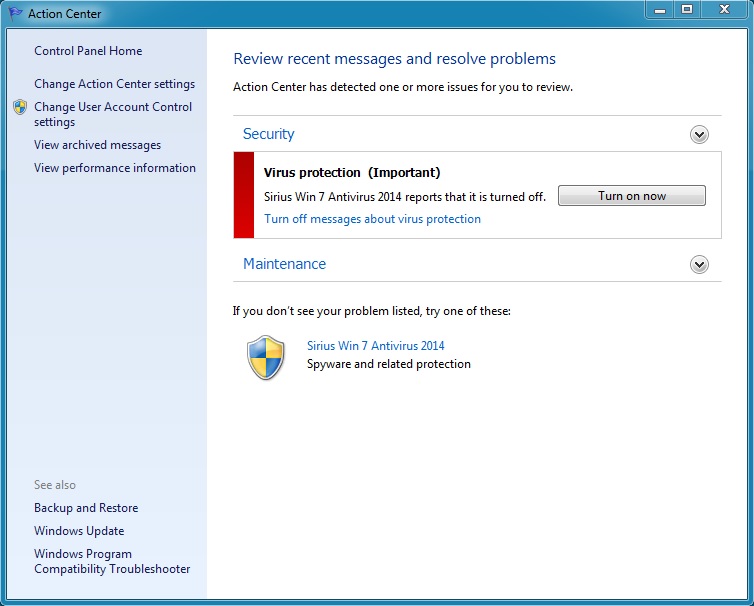
Here's the fake anti-virus Sirius Win 7 Antivirus 2014 doing a fake scan on the infected VM:
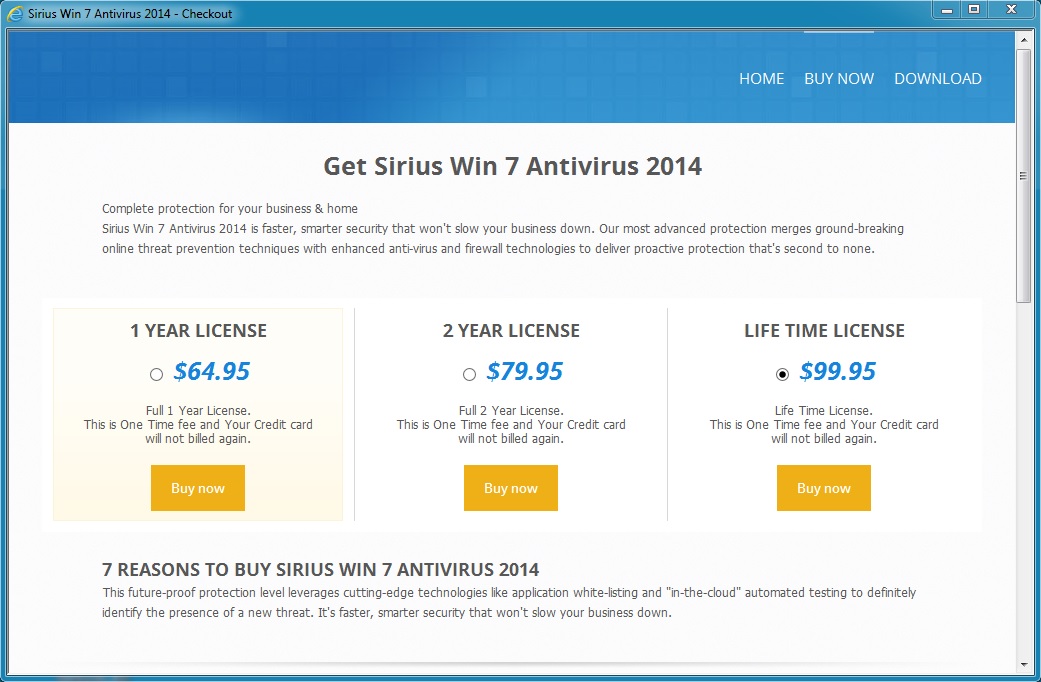
Another fake reminder, as the malware tries to get me to register:
Here's the window that pops up when you try to register:
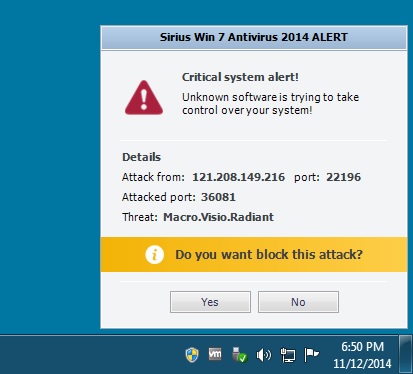
The infected VM will occasionally generate more fake anti-virus alerts like this one:
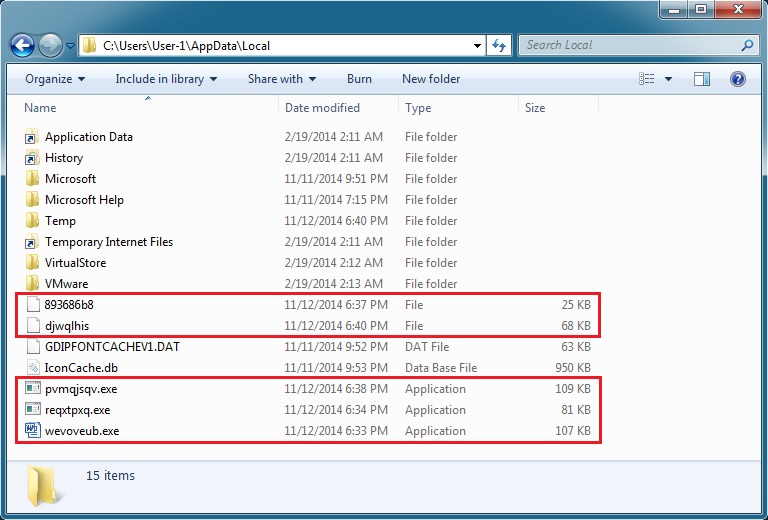
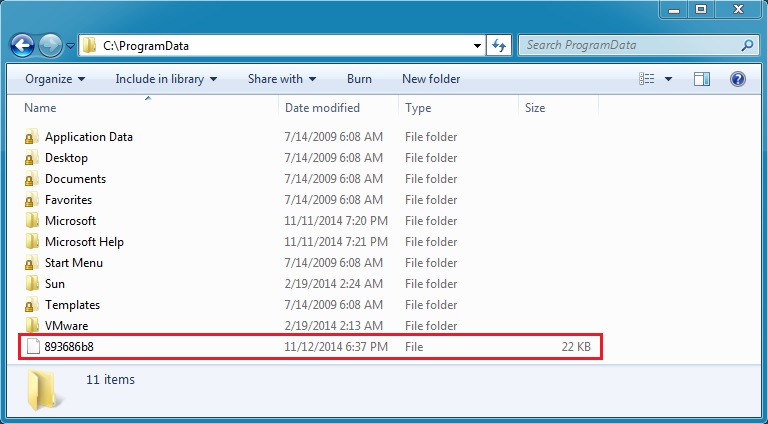
I couldn't run the registry editor or look at any of the files in my infected VM's AppData\Local\Temp directory. I would always get one of these warnings:
Meanwhile, here's some of the HTTP POST traffic generated by the infected VM:
Here's HTTP web traffic associated with this particular version of the Sirius Win 7 Antivirus 2014 malware:
Here's an example of the fake Delta Airlines phishing emails sent by my infected VM before I took it off-line:
Click here to return to the main page.