2015-01-18 - NUCLEAR EK FROM 188.226.241[.]6 - NIGHTGLASS.CF & NIGHTGLASS.GA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I infected two different VMs.
- The first run was done on a Windows 7 64-bit VM with IE 10.
- The second run was done on a Windows 7 32-bit VM with IE 8.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 188.226.241[.]6 - nightglass[.]cf and nightglass[.]ga - Nuclear EK
- 193.107.17[.]24 - burtander[.]com - Vawtrak/NeverQuest callback traffic, unsuccessful TCP connection
- 217.12.203[.]3 - ederfiner[.]com - Vawtrak/NeverQuest callback traffic, unsuccessful TCP connection
- 89.253.222[.]26 - erbuders[.]com - Vawtrak/NeverQuest callback traffic, successful TCP connection
NUCLEAR EK - FIRST RUN:
- 2015-01-18 19:27:00 UTC - nightglass[.]cf - GET /XhBWV0gBT08OVFVW.html
- 2015-01-18 19:27:01 UTC - nightglass[.]cf - GET /AwoVGwxQAEcOVRleDlRTBgMFR0tUV1YOVFcAHAJDQUhXVlxUVgdOVRtA
- 2015-01-18 19:27:03 UTC - nightglass[.]cf - GET /ABsJAkgKUURCGlYaShlWAAACQUJfV1RCGVYEBh1GRlVLVEJLVgUBT0AONi0fCB0j
- 2015-01-18 19:27:08 UTC - nightglass[.]cf - GET /ABsJAkgKUURCGlYaShlWAAACQUJfV1RCGVYEBh1GRlVLVEJLVgUBT0AOMzc1FB0bBg
NUCLEAR EK - SECOND RUN:
- 2015-01-18 19:32:19 UTC - nightglass[.]ga - GET /XhNdAUgBT08OVFVW.html
- 2015-01-18 19:32:21 UTC - nightglass[.]ga - GET /AwoVGwxTCxEOVRleDlRTBgMFR0tTV1YOVFIAHAJFRUhTVFxSVkhUX0U
- 2015-01-18 19:32:23 UTC - nightglass[.]ga - GET /ABsJAkgKUk8UGlYaShlWAAACQUJfUFRCGVYBBh1GQFFLUEBLUAVOBgsrIDETIyId
- 2015-01-18 19:32:29 UTC - nightglass[.]ga - GET /ABsJAkgKUk8UGlYaShlWAAACQUJfUFRCGVYBBh1GQFFLUEBLUAVOBgs7Kw8OGRlV
- 2015-01-18 19:32:34 UTC - nightglass[.]ga - GET /ABsJAkgKUk8UGlYaShlWAAACQUJfUFRCGVYBBh1GQFFLUEBLUAVOBAsrIDETIyId
- 2015-01-18 19:32:44 UTC - nightglass[.]ga - GET /ABsJAkgKUk8UGlYaShlWAAACQUJfUFRCGVYBBh1GQFFLUEBLUAVOBAs7Kw8OGRlV
- 2015-01-18 19:32:44 UTC - nightglass[.]ga - GET /AwoVGwxTCxEOVRleDlRTBgMFR0tTV1YOVFIAHAJFRUhTVFxSVkhBWhsEAxc
- 2015-01-18 19:32:46 UTC - nightglass[.]ga - GET /ABsJAkgKUk8UGlYaShlWAAACQUJfUFRCGVYBBh1GQFFLUEBLUAVOCwsrIDETIyId
- 2015-01-18 19:32:54 UTC - nightglass[.]ga - GET /ABsJAkgKUk8UGlYaShlWAAACQUJfUFRCGVYBBh1GQFFLUEBLUAVOCws7Kw8OGRlV
VAWTRAK/NEVERQUEST TRAFFIC:
- 2015-01-18 19:32:34 UTC - DNS query for burtander[.]com - resolved to: 193.107.17[.]242
- 2015-01-18 19:32:57 UTC - DNS query for ederfiner[.]com - resolved to: 217.12.203[.]3
- NOTE: The above DNS queries generated TCP connections to their IP addresses that were reset by the servers.
- 2015-01-18 19:33:26 UTC - erbuders[.]com - POST /collection/0000004E/00/9EBD6132
- 2015-01-18 19:33:28 UTC - erbuders[.]com - POST /collection/0000004E/02/9EBD6132
- 2015-01-18 19:33:33 UTC - erbuders[.]com - POST /collection/0000004E/02/9EBD6132
ALERTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion monitoring the infection traffic using Suricata (not including ET INFO or ET POLICY rules):
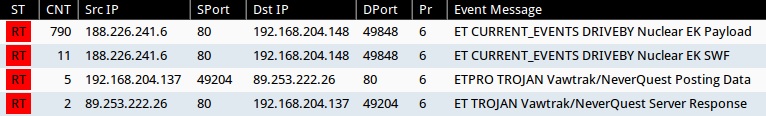
- 188.226.241[.]6 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 188.226.241[.]6 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 89.253.222[.]26 port 80 - ETPRO TROJAN Vawtrak/NeverQuest Posting Data (sid:2809464)
- 89.253.222[.]26 port 80 - ET TROJAN Vawtrak/NeverQuest Server Response (sid:2019499)
Sourcefire/VRT/Talos ruleset from Snort 2.9.7.0 on Debian 7 using tcpreplay:
- 188.226.241[.]6 port 80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt (x2)
- 188.226.241[.]6 port 80 - [1:32879:1] EXPLOIT-KIT Nuclear exploit kit payload delivery (x3)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-01-18-Nuclear-EK-flash-exploit.swf
File size: 23,631 bytes
MD5 hash: 759c2d4d526940a03e3187bcff52df55
Detection ratio: 1 / 57
First submission: 2015-01-15 10:52:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/7f8ceced652b3af0996a97efa986f25ad7ee99ec22b5c4162eedaeaed949f53d/analysis/
SILVERLIGHT EXPLOIT:
File name: 2015-01-18-Nuclear-EK-silverlight-exploit.xap
File size: 18,032 bytes
MD5 hash: c3cf4a7b7c7c32b787bb07f9dbe35a11
Detection ratio: 0 / 56
First submission: 2015-01-18 20:42:49 UTCC
VirusTotal link: https://www.virustotal.com/en/file/241472414d584676abdde9d337b2c5420bfc51b30239a12a3bf12e55b6def0d2/analysis/
MALWARE PAYLOAD:
File name: 2015-01-18-Nuclear-EK-malware-payload.exe
File size: 454,656 bytes
MD5 hash: 74b87899fe6d4533c039648f8f4fd9fd
Detection ratio: 5 / 57
First submission: 2015-01-18 20:43:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/db4fb59eccecdd664cde3c6f9e2c4b69c17f4676e407a8e9b2f7e7b7fbf0c1fb/analysis/
DROPPED MALWARE FOUND ON INFECTED VM:
File name: 2015-01-18-Nuclear-EK-dropped-malware-found-on-infected-VM.exe
File size: 303,104 bytes
MD5 hash: f37658583f6ebca548eaa9db571c1ad2
Detection ratio: 6 / 57
First submission: 2015-01-18 20:43:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/36ec575b51d85ea1abe1ea15ac344ceb32b76714d357a29937e7aa287bfd3fb3/analysis/
Click here to return to the main page.
