2015-01-20 - MALWARE INFECTION FROM LINK IN EMAIL IMPERSONATING BBVA BANCOMER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-20-initial-infection-traffic.pcap.zip
- 2015-01-20-post-infection-traffic.pcap.zip
- 2015-01-20-malware-from-the-infection.zip
- 2015-01-20-malicious-email-example.eml.zip
NOTES:
- Although this email is in Spanish, it was not sent to any Spanish or Latin American recipients.
- From our end, the recipients were publicly-known English language email addresses.
EXAMPLE OF THE EMAILS
SCREENSHOTS:
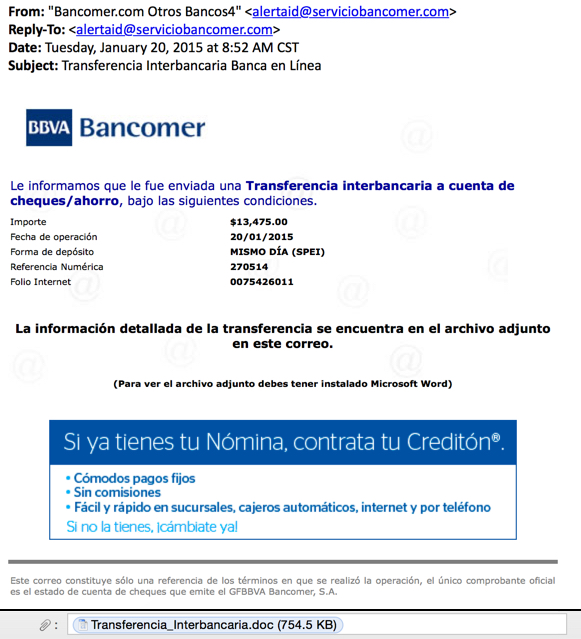
MESSAGE TEXT:
From: "Bancomer[.]com Otros Bancos4" <alertaid@serviciobancomer[.]com>
Reply-To: <alertaid@serviciobancomer[.]com>
Date: Tuesday, January 20, 2015 at 8:52 AM CST
Subject: Transferencia Interbancaria Banca en Línea
Le informamos que le fue enviada una Transferencia interbancaria a cuenta de cheques/ahorro, bajo las siguientes condiciones.
Importe $13,475.00
Fecha de operación 20/01/2015
Forma de depósito MISMO DÍA (SPEI) Referencia Numérica 270514
Folio Internet 0075426011
La información detallada de la transferencia se encuentra en el archivo adjunto en este correo.
(Para ver el archivo adjunto debes tener instalado Microsoft Word)
Este correo constituye sólo una referencia de los términos en que se realizó la operación, el único comprobante oficial es el estado de cuenta de cheques que emite el GFBBVA Bancomer, S.A.
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: Transferencia_Interbancaria.doc
File size: 571,904 bytes
MD5 hash: 285a97a0a7adb4e7e97e6927009ebc33
Detection ratio: 10 / 57
First submission: 2015-01-20 11:57:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/48791c0ea6c3d34d267452bf32cbe8346d9d29ebd48f0b323cd811d952d4febd/analysis/
DOWNLOADED EXE:
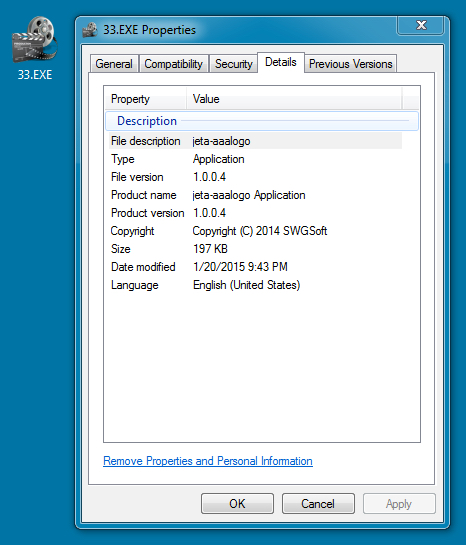
File name: ss.exe (stored on the infected host as 33.EXE)
File size: 201,728 bytes br> MD5 hash: 85a7dd41140f87fc0e3e455dcb95a00b
Detection ratio: 4 / 57
First submission: 2015-01-20 18:17:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/a296b4ffbb424f5aa11d62bcb295c798c32322c85daf9337b1d2e63f4b5f6b15/analysis/
FOLLOW-UP MALWARE DOWNLOADED DURING THE POST-INFECTION TRAFFIC:
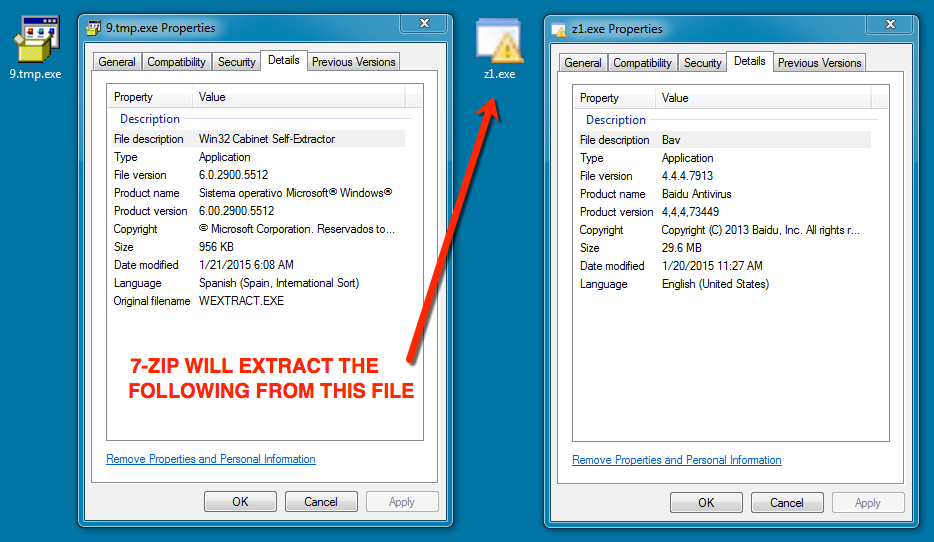
File name: z7.exe (stored on the infected host as 9.tmp.exe)
File size: 978,944 bytes
MD5 hash: a752bedbbf6b73e52e2d7f8f3cd6a227
Detection ratio: 4 / 57
First submission: 2015-01-20 18:13:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/98589d73e06c0587d5e3463146b01f4f47072a68f6ce4ae033de1013a4c1de86/analysis/
INFECTION TRAFFIC
ASSOCIATED DOMAINS:
- 192.185.183[.]121 - e-trebol[.]com - Domain for initial EXE file
- 104.171.118[.]144 - sinpp[.]su - Post-infection callback
- 69.31.136[.]17 - fs03n4.sendspace[.]com - Post-infection request for another EXE file
RUNNING THE WORD DOCUMENT ON A VM:
- 2015-01-20 21:25:18 UTC - e-trebol[.]com - GET /404/ss.exe
FINALLY GOT THE DOWNLOADED MALWARE TO RUN ON ANOTHER HOST:
- 2015-01-20 22:09:12 UTC - www.msn[.]com - GET /
- 2015-01-20 22:09:31 UTC - www.adobe[.]com - POST /
- 2015-01-20 22:09:35 UTC - www.adobe[.]com - POST /
- 2015-01-20 22:09:38 UTC - www.adobe[.]com - POST /
- 2015-01-20 22:09:42 UTC - www.adobe[.]com - POST /go/flashplayer_support/
- 2015-01-20 22:09:46 UTC - go.microsoft[.]com - POST /fwlink/?LinkId=96416
- 2015-01-20 22:09:50 UTC - www.microsoft[.]com - POST /management
- 2015-01-20 22:09:53 UTC - sinpp[.]su - POST /store/
- 2015-01-20 22:09:56 UTC - support.microsoft[.]com - POST /
- 2015-01-20 22:10:00 UTC - www.adobe[.]com - POST /
- 2015-01-20 22:10:04 UTC - go.microsoft[.]com - POST /fwlink/?LinkId=98075
- 2015-01-20 22:10:07 UTC - www.microsoft[.]com - POST /management
- 2015-01-20 22:10:11 UTC - sinpp[.]su - POST /store/
- 2015-01-20 22:10:15 UTC - fs03n4.sendspace[.]com - GET /dlpro/2cecac96b40517083ff1eb9399a0ff00/54be710f/nhkub2/z7.exe
- 2015-01-20 22:10:17 UTC - sinpp[.]su - POST /store/
- 2015-01-20 22:10:19 UTC - sinpp[.]su - POST /store/
- 2015-01-20 22:10:30 UTC - sinpp[.]su - POST /store/
ALERTS
Signature hits noted from the Emerging Threats and ETPRO rulesets on Security Onion (not counting ET POLICY or ET INFO events):
- ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile (sid:2019714)
Signature hits noted from the VRT/Talos ruleset from Snort 2.9.7.0 on Debian 7:
- [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- [1:11192:16] FILE-EXECUTABLE download of executable content
- [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
Click here to return to the main page.