2015-01-21 - ANGLER EK FROM 207.182.149[.]13
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 117.104.160[.]130 - www.victorianpoloclub[.]com[.]au - Comrpomised website
- 185.14.28[.]204 - nic.kraview[.]com and usa.musicalmanager[.]com - Redirect
- 207.182.149[.]13 - hydroceppoweron.metalmaidenphotography[.]rocks - Angler EK
- 209.126.97[.]209 - jyjhsvgkpeni0g[.]com - ET TROJAN Bedep Checkin Response
- 188.138.25[.]107 - drain.diskant[.]co[.]uk - ET TROJAN Fareit/Pony Downloader Checkin 2
- 173.224.126[.]19 - asop83uyteramxop[.]com - ET MALWARE Fun Web Products Spyware User-Agent (FunWebProducts)
- 83.69.233[.]133 - ipsalomenatep58highwayroad[.]biz:8080 - ET TROJAN Ursnif Checkin
- 79.99.6[.]187 - 79.99.6[.]187:8080 - ETPRO TROJAN Win32/Injector.BOIK Downloader Checkin
COMPROMISED WEBSITE AND REDIRECT:
- 2015-01-21 23:41:40 UTC - www.victorianpoloclub[.]com[.]au - GET /
- 2015-01-21 23:41:43 UTC - nic.kraview[.]com - GET /js/script.js
ANGLER EK:
- 2015-01-21 23:41:44 UTC - hydroceppoweron.metalmaidenphotography[.]rocks - GET /e4pzex31kf.php
- 2015-01-21 23:41:48 UTC - hydroceppoweron.metalmaidenphotography[.]rocks - GET /4ne_iqmOKEs_KVuX7cfg_qIMuoQsTkJAoA0zfzhLEL7g_b4MRf-RyKV6jMTUJTVr
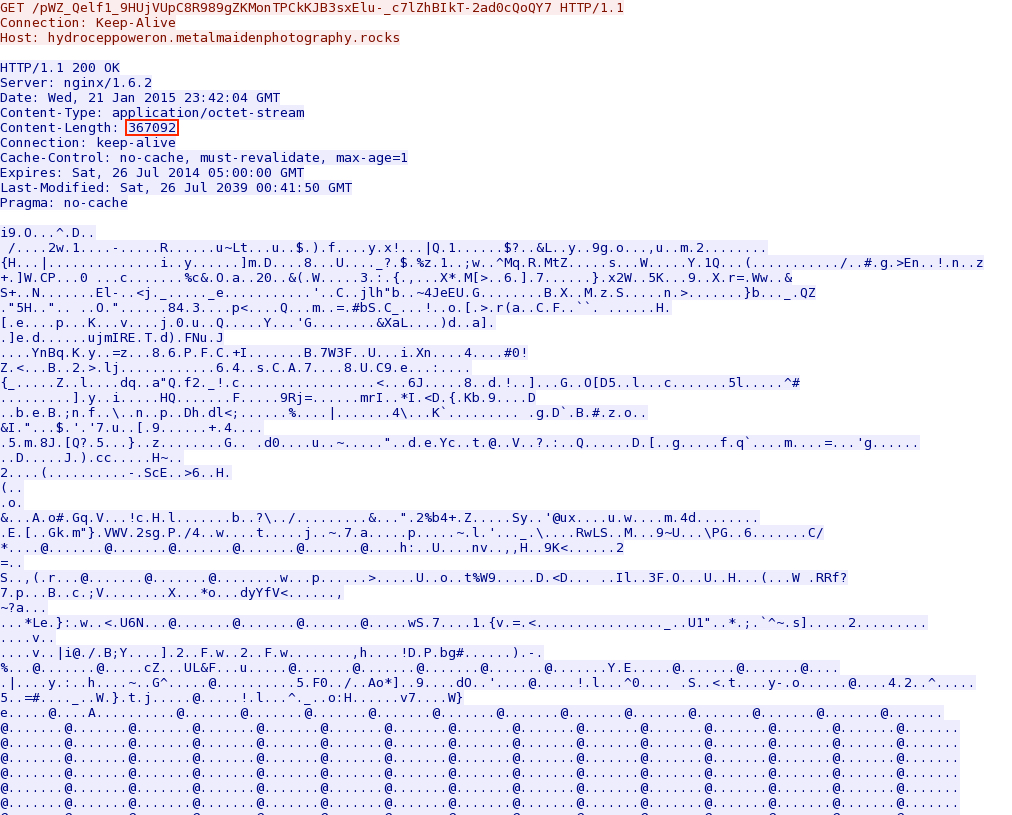
- 2015-01-21 23:41:49 UTC - hydroceppoweron.metalmaidenphotography[.]rocks - GET /pWZ_Qelf1_9HUjVUpC8R989gZKMonTPCkKJB3sxElu-_c7lZhBIkT-2ad0cQoQY7
POST-INFECTION CONNECTIVITY CHECK BY THE MALWARE:
- 2015-01-21 23:41:55 UTC - www.earthtools[.]org - POST /timezone/0/0
- 2015-01-21 23:41:55 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
OTHER POST-INFECTION TRAFFIC:
- 2015-01-21 23:41:57 UTC - jyjhsvgkpeni0g[.]com - POST /
- 2015-01-21 23:41:58 UTC - jyjhsvgkpeni0g[.]com - POST /
- 2015-01-21 23:42:05 UTC - jyjhsvgkpeni0g[.]com - POST /
- 2015-01-21 23:42:10 UTC - drain.diskant[.]co[.]uk - POST /news.php
- 2015-01-21 23:42:11 UTC - jyjhsvgkpeni0g[.]com - POST /
- 2015-01-21 23:42:24 UTC - ipsalomenatep58highwayroad[.]biz:8080 - GET /photoLibrary/?user=632c7580bc5383c43738fd96edcbba95&id=5&ver=111&os=498139398&
os2=256&host=0&k=2953951398&type=555 - 2015-01-21 23:42:28 UTC - ipsalomenatep58highwayroad[.]biz:8080 - POST /photoLibrary/?user=632c7580bc5383c43738fd96edcbba95&id=5&ver=111&os=498139398&
os2=256&host=0&k=2953951398&type=555 - 2015-01-21 23:42:28 UTC - 8ipsalomenatep58highwayroad[.]biz:8080 - GET /photoLibrary/?user=632c7580bc5383c43738fd96edcbba95&id=5&ver=111&os=498139398&
os2=257&host=0&k=1159559117&type=555 - 2015-01-21 23:42:31 UTC - ipsalomenatep58highwayroad[.]biz:8080 - POST /photoLibrary/?user=632c7580bc5383c43738fd96edcbba95&id=5&ver=111&os=498139398&
os2=257&host=0&k=1159559117&type=555 - 2015-01-21 23:42:32 UTC - 79.99.6[.]187:8080 - POST /tbjlqkjsu.php?xvydhmo=YoN8f9DiGsbcNVfj5tPaYhvk1RDfLe8cOHyBmg1BDhdjEvaDV2cwCoWFsZ0WG6t9lxOcZ
IOuqEO5O5A+xzheUNJQu1pEsIyxJWFSv/4fIX4xPCEe948P/BhYyucqrahk - 2015-01-21 23:42:44 UTC - 79.99.6[.]187:8080 - POST /dakqqj.php?iallpins=jUMl95c61J3zxB73MneaRWCqWDqgoSma0rMWLf63ye3n3CFPS4Gd9+UjTXX4HzsN/Z8VM
QtuxO1hFgetnOhnAbM0ExqNgyO5fUpuu/oQddPQN2TYX21wjpOL56R9+wBsaUPbYoGAfq2XZbYVIS8grS== - 2015-01-21 23:45:12 UTC - asop83uyteramxop[.]com - GET /ads.php?sid=1917
- 2015-01-21 23:45:27 UTC - asop83uyteramxop[.]com - GET /r.php?key=b8c06a1ab928f022031c0cd625ae939b
- 2015-01-21 23:45:27 UTC - asop83uyteramxop[.]com - GET /r.php?key=b8c06a1ab928f022031c0cd625ae939b
- 2015-01-21 23:45:27 UTC - asop83uyteramxop[.]com - GET /r.php?key=b8c06a1ab928f022031c0cd625ae939b
- 2015-01-21 23:45:28 UTC - asop83uyteramxop[.]com - GET /r.php?key=b8c06a1ab928f022031c0cd625ae939b
- [The pcap has other traffic, which I believe is click fraud activity.]
ALERTS
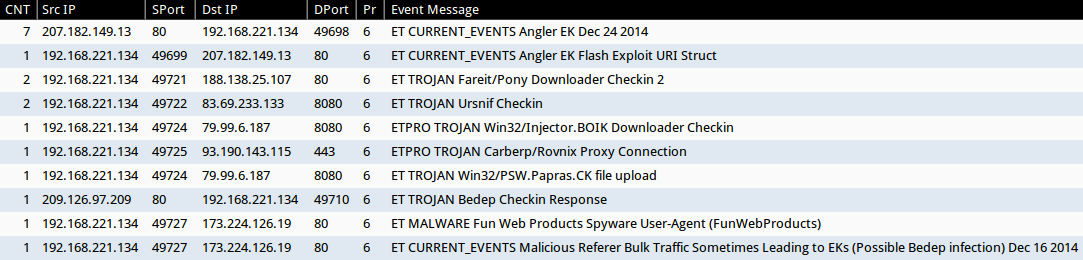
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 207.182.149[.]13 port 80 - ET CURRENT_EVENTS Angler EK Flash Exploit URI Struct (sid:2019513)
- 207.182.149[.]13 port 80 - ET CURRENT_EVENTS Angler EK Dec 24 2014 (sid:2020068)
- 188.138.25[.]107 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 83.69.233[.]133 port 8080 - ET TROJAN Ursnif Checkin (sid:2019678)
- 79.99.6[.]187 port 8080 - ETPRO TROJAN Win32/Injector.BOIK Downloader Checkin (sid:2809167)
- 93.190.143[.]115 port 443 - ETPRO TROJAN Carberp/Rovnix Proxy Connection (sid:2808448)
- 79.99.6[.]187 port 8080 - ET TROJAN Win32/PSW.Papras.CK file upload (sid:2019379)
- 209.126.97[.]209 port 80 - ET TROJAN Bedep Checkin Response (sid:2019952)
- 173.224.126[.]19 port 80 - ET MALWARE Fun Web Products Spyware User-Agent (FunWebProducts) (sid:2001855)
- 173.224.126[.]19 port 80 - ET CURRENT_EVENTS Malicious Referer Bulk Traffic Sometimes Leading to EKs (Possible Bedep infection) Dec 16 2014 (sid:2019950)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 207.182.149[.]13 port 80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 188.138.25[.]107 port 80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- various IPs port 80 - [1:7567:14] PUA-TOOLBARS Win.Adware.MyWebSearch Toolbar funwebproducts variant outbound connection (multiple hits)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-01-21-Angler-EK-flash-exploit.swf
File size: 44,376 bytes
MD5 hash: 5bb88d63a37f296d6e42245421537fe6
Detection ratio: 2 / 57
First submission: 2015-01-21 10:08:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/04596a3ef7239ee9f1054a578504de80f922d65c3c86df3396f22401266d79e8/analysis/
DROPPED FILES IN THE USER'S APPDATA\LOCAL\TEMP FOLDER:
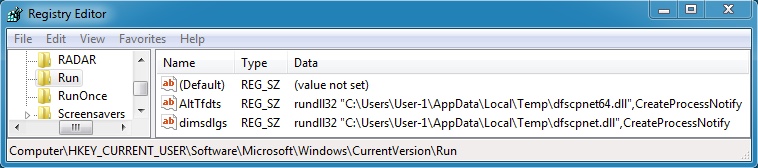
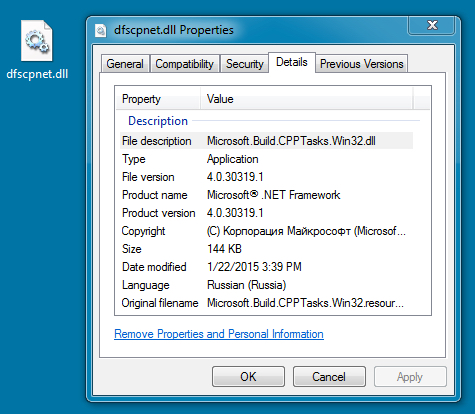
File name: dfscpnet.dll
File size: 147,828 bytes
MD5 hash: cd509fc9a2a8ae8a07ab2086ec6ad93a
Detection ratio: 28 / 57
First submission: 2015-01-14 23:37:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/5f6e3461702e0eeaabb03bc7e6ee3c99f597102ada48321262f6b44b6ed63749/analysis/
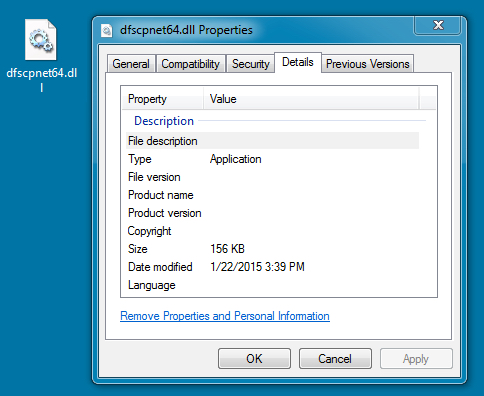
File name: dfscpnet64.dll
File size: 159,744 bytes
MD5 hash: 8aca5883cd15813ac2f05d5ae7db9924
Detection ratio: 9 / 57
First submission: 2015-01-14 23:37:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/26a50199b04361cce4857a253ce4debb5c992fc120f927c2522a35127b9ea4f4/analysis/
SCREENSHOTS
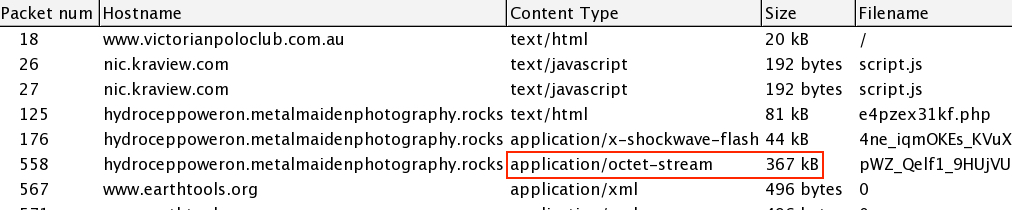
You can easily find the malware payload in Wireshark by exporting HTTP objects and looking through the list.
Unfortunately, the encryption or obfuscation has changed. It doesn't appear to be a strict XOR as we've seen before with Angler EK. I wasn't able to de-obfuscate the payload.
Click here to return to the main page.