2015-01-27 - UPATRE/DYRE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
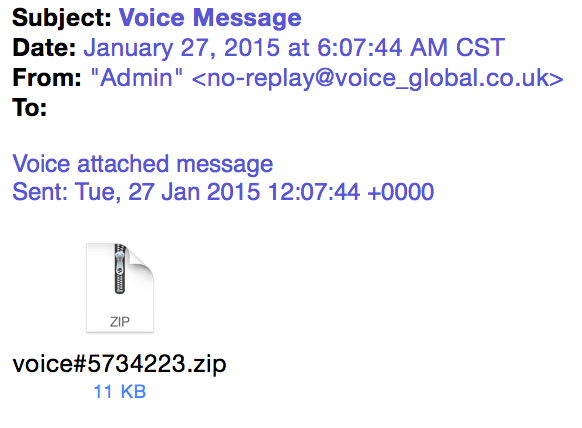
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE CHARACTERISTICS:
Sender (spoofed): "Admin" <no-replay@voice_global[.]co[.]uk>
Subject: Voice Message
Attachment name: voice#[7 random digits].zip
INFECTION TRAFFIC
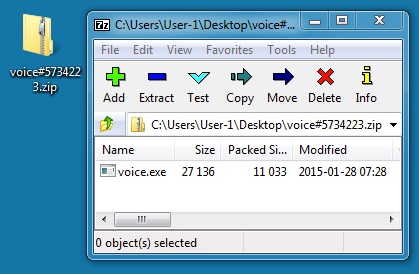
EXTRACTING THE MALWARE FROM THE ZIP ARCHIVE AND INFECTING A VM:
- 2015-01-27 18:21:25 UTC - 202.153.35[.]133 port 15175 - 202.153.35[.]133:15175 - GET /2701uk12/WIN-BS4EUJ1KO34/0/61-SP1/0/
- 2015-01-27 18:21:26 UTC - 202.153.35[.]133 port 15175 - 202.153.35[.]133:15175 - GET /2701uk12/WIN-BS4EUJ1KO34/1/0/0/
- 2015-01-27 18:21:28 UTC - 192.163.217[.]66 port 80 - best-synthetic-motor-oil[.]com - GET /file_k12.pdf
- 2015-01-27 18:21:42 UTC - 202.153.35[.]133 port 15128 - 202.153.35[.]133:15128 - GET /2701uk12/WIN-BS4EUJ1KO34/41/7/4/
- 2015-01-27 18:21:48 UTC - 208.91.197[.]54 port 3478 - UDP STUN traffic to: s2.taraba[.]net
- 2015-01-27 18:22:05 UTC - 173.194.67[.]127 port 19302 - UDP STUN traffic to: stun2.l.google[.]com
- 2015-01-27 18:22:12 UTC - 91.222.152[.]182 port 443 - Encrypted TCP traffic
- 2015-01-27 18:22:27 UTC - 78.143.39[.]41 port 80 - zac-buero[.]de - GET /mandoc/ml1from1.tar
- 2015-01-27 18:22:29 UTC - 37.59.30[.]125 port 443 - Encrypted TCP traffic
- 2015-01-27 18:22:29 UTC - 109.236.84[.]101 port 1025 - Encrypted TCP traffic
- 2015-01-27 18:22:34 UTC - 72.167.2[.]191 port 80 - shopmeyermusic[.]com - GET /boa/pony1.tar
- 2015-01-27 18:22:34 UTC - 83.219.133[.]225 port 81 - 83.219.133[.]225 - POST /dffgbDFGvf465/gate.php
- 2015-01-27 18:22:39 UTC - 95.25.71[.]144 port 443 - i2p.mooo[.]com - repeated attempts for TCP connections RST by the server
ALERTS
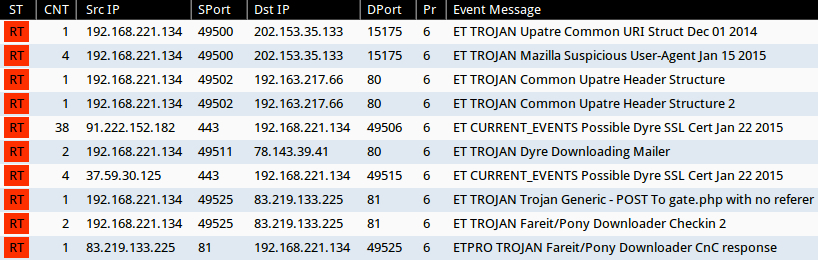
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 202.153.35[.]133 port 15175 - ET TROJAN Upatre Common URI Struct Dec 01 2014 (sid:2019847)
- 202.153.35[.]133 port 15175 - ET TROJAN Mazilla Suspicious User-Agent Jan 15 2015 (sid:2020235)
- 192.163.217[.]66 port 80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 192.163.217[.]66 port 80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 91.222.152[.]182 port 443 - ET CURRENT_EVENTS Possible Dyre SSL Cert Jan 22 2015 (sid:2020290)
- 78.143.39[.]41 port 80 - ET TROJAN Dyre Downloading Mailer (sid:2020308)
- 37.59.30[.]125 port 443 - ET CURRENT_EVENTS Possible Dyre SSL Cert Jan 22 2015 (sid:2020290)
- 83.219.133[.]225 port 81 - ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- 83.219.133[.]225 port 81 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 83.219.133[.]225 port 81 - ETPRO TROJAN Fareit/Pony Downloader CnC response (sid:2805976)
Talos (Sourcefire VRT) ruleset from Snort 2.9.7.0 on Debian 7:
- 202.153.35[.]133 port 15175 - [1:33207:1] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre
- 202.153.35[.]133 port 15175 - [1:33146:2] MALWARE-CNC Win.Trojan.Upatre variant outbound connection (x2)
- 202.153.35[.]133 port 15128 - [1:33207:1] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre
- 192.163.217[.]66 port 80 - [1:33207:1] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre
- 83.219.133[.]225 port 81 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: voice#5734223.zip
File size: 11,149 bytes
MD5 hash: ad6a9ccf06269f3fde4343694f020df9
Detection ratio: 13 / 57
First submission: 2015-01-27 12:15:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/f90a0953931e9a1793e5cc597cd8dd0fc1689b7240169663b7ec9a5633076f58/analysis/
EXTRACTED MALWARE:
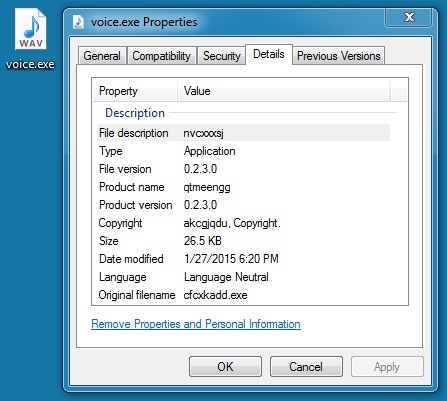
File name: voice.exe
File size: 27,136 bytes
MD5 hash: 39941126cc7e3064c1d3546f6babed79
Detection ratio: 12 / 57
First submission: 2015-01-27 12:17:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/858626c43c6ba34f59c0064168b734610b1dfead0107ba1d27f2049cdcc1386b/analysis/
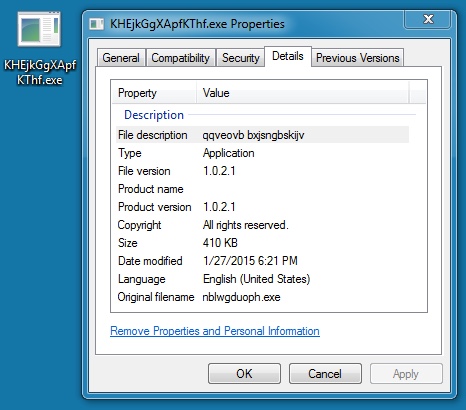
DROPPED MALWARE (1 OF 3):
File name: C:\Windows\KHEjkGgXApfKThf.exe
File size: 419,840 bytes
MD5 hash: 028ebc2c61156781868199de0b44caaf
Detection ratio: 9 / 56
First submission: 2015-01-27 15:20:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/b7194a81a653880c9a084f8628bbfe165f9cb72f5ff2bb385636cfdc9076ce51/analysis/
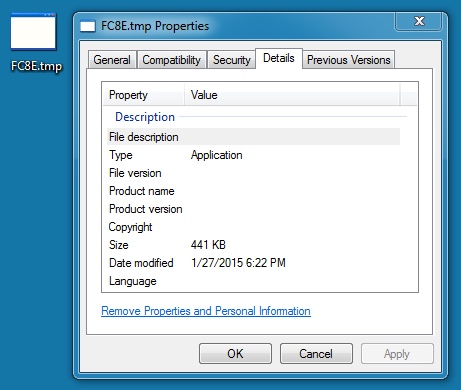
DROPPED MALWARE (2 OF 3):
File name: C:\Windows\Temp\FC8E.tmp
File size: 451,584 bytes
MD5 hash: d9a3d5c3c06f3429b65db7b84b50bed4
Detection ratio: 35 / 57
First submission: 2015-01-26 15:30:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/948f5dee6e752a593949c327781bae2d3e8994d4c00074228bed6e1156fe3402/analysis/
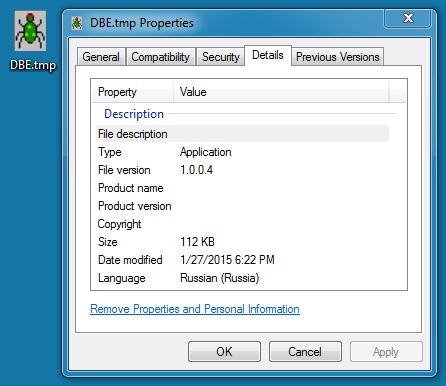
DROPPED MALWARE (3 OF 3):
File name: C:\Windows\Temp\DBE.tmp
File size: 114,688 bytes
MD5 hash: 40a59f55199e4578267dfb883747be9f
Detection ratio: 0 / 57
First submission: 2015-01-27 17:42:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/1fa614e5ae8e7b2307851227e5f7324ea38b57416e14518a730d3071dd0ba956/analysis/
Click here to return to the main page.