2015-02-06 - RIG EK FROM 46.182.30[.]163 PUSHING KRONOS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The malware payload appears to be Kronos.
- More info on Kronos is at: https://threatpost.com/new-kronos-banking-malware-advertised-on-russian-forums/107210/
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 46.182.30[.]163 - booster.daily-mood-booster[.]com - Rig EK
- 92.87.96[.]9 - bitcoind[.]su - Post-infection traffic (Kronos checkin) over port 80
RIG EK:
- 2015-02-06 16:17:55 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /?PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu|MzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU - 2015-02-06 16:18:00 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /index.php?req=mp3&num=81&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu%7CMzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU - 2015-02-06 16:18:06 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /index.php?req=swf&num=754&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu|MzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU - 2015-02-06 16:18:08 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /index.php?req=mp3&num=1607&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu|MzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU&dop=1 - 2015-02-06 16:18:17 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /index.php?req=mp3&num=91593&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu%7CMzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU&dop=04 - 2015-02-06 16:18:22 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /index.php?req=xap&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu|MzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU - 2015-02-06 16:18:34 UTC - 46.182.30[.]163:80 - booster.daily-mood-booster[.]com - GET /index.php?req=mp3&num=34763585&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJkuHbwvnPVsbu%7CMzE1MWY4MjZhOTZhYTU4NDAwNDhmZjQ4ZjQwNTI0NDU&dop=095
POST-INFECTION TRAFFIC:
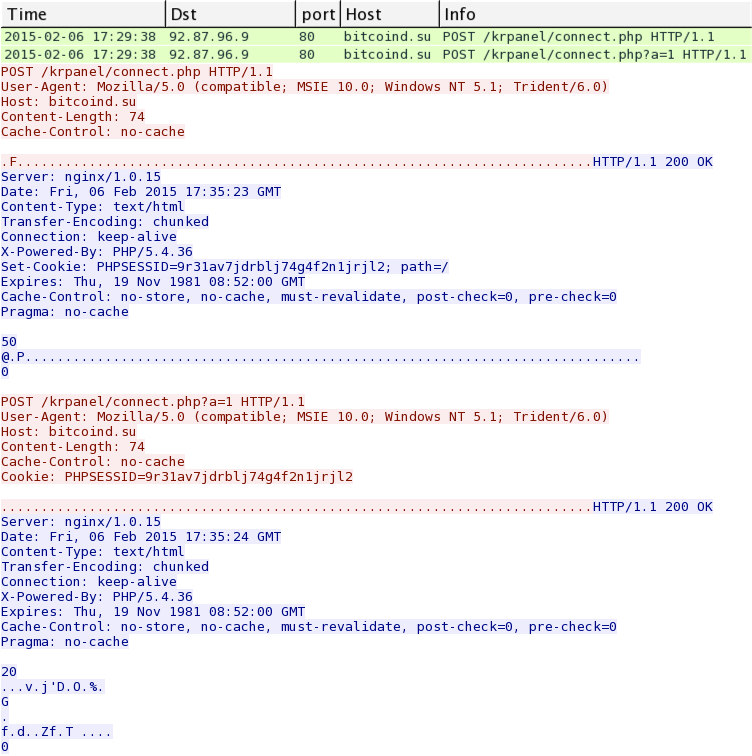
- 2015-02-06 17:29:38 UTC - 92.87.96[.]9 port 80 - bitcoind[.]su - POST /krpanel/connect.php
- 2015-02-06 17:29:38 UTC - 92.87.96[.]9 port 80 - bitcoind[.]su - POST /krpanel/connect.php?a=1
NOTE: The malware wouldn't run on a VM, and I saw nothing from the malwr.com analysis, so I had to use another malware analysis tool. No pcap on this, but here's a screenshot of the traffic:
ALERTS
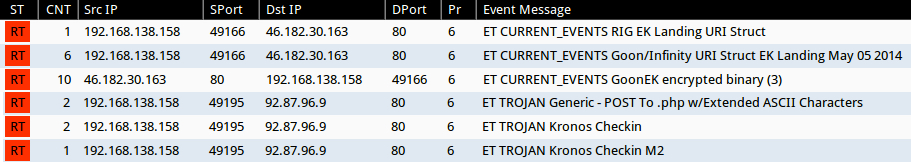
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 46.182.30[.]163 port 80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 46.182.30[.]163 port 80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 46.182.30[.]163 port 80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
- 92.87.96[.]9 port 80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters (sid:2016858)
- 92.87.96[.]9 port 80 - ET TROJAN Kronos Checkin (sid:2020080)
- 92.87.96[.]9 port 80 - ET TROJAN Kronos Checkin M2 (sid:2020077)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 46.182.30[.]163 port 80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure (x6)
- 46.182.30[.]163 port 80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 46.182.30[.]163 port 80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 92.87.96[.]9 port 80 - [1:25050:5] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
PRELIMINARY MALWARE ANALYSIS
NOTE: The exploits and malware payload from 2015-02-05 have the same file hashes as the ones from 2015-02-06.
FLASH EXPLOIT:
File name: 2015-02-06-Rig-EK-flash-exploit.swf
File size: 20,239 bytes
MD5 hash: 82a81b6f9ee1ec433678e3daabc8be59
Detection ratio: 4 / 56
First submission: 2015-02-05 14:11:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/79d84426dea00871efd41a1ba19547ef8fad672e12a2f5776f03c1da2f5d8c0d/analysis/
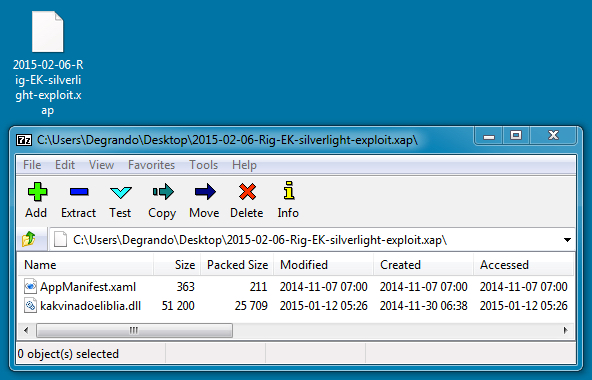
SILVERLIGHT EXPLOIT:
File name: 2015-02-06-Rig-EK-silverlight-exploit.xap
File size: 26,238 bytes
MD5 hash: 5fa5959789a97d83f6b7625b86b434b9
Detection ratio: 6 / 56
First submission: 2015-01-14 14:37:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/a35bc9d0db540fd8d33b7b1232d4e8714d79f12e8b6c0ecb2732a43e3d443409/analysis/
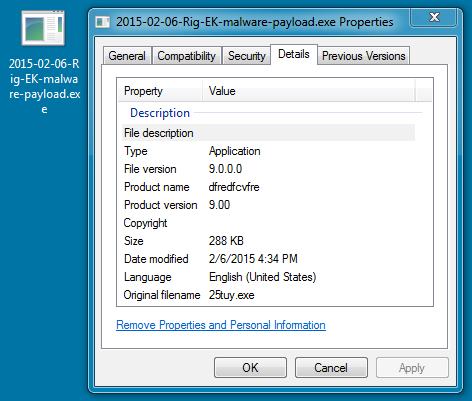
MALWARE PAYLOAD:
File name: 2015-02-06-Rig-EK-malware-payload.exe
File size: 294,912 bytes
MD5 hash: 40118fcf2d286c60ee8ecd3f71aa6f52
Detection ratio: 19 / 56
First submission: 2015-02-06 17:16:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/99bd37770622b05a0c3d4179c4f8615fa00f2cc1f7c663e37f92a668d1adbf3a/analysis/
Click here to return to the main page.