2015-02-09 - CHANITOR/VAWTRAK ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-02-09-Chanitor-Vawtrak-infection-traffic.pcap.zip
- 2015-02-09-Chanitor-Vawtrak-malware-and-email-samples.zip
NOTES:
- Like many other email campaigns, this appears to be botnet-based, with several different senders world-wide.
- In traffic from the infected VM, the malicious Word document downloaded Chanitor, then Chanitor used Tor traffic to download Vawtrak.
- No actual Vawtrak traffic from the infected VM, but the malware is stored using the exact same file path as previous Vawtrak samples.
- I've noticed other people may use "chaintor" instead of "chanitor". From what I can tell, it should be Chanitor.
EXAMPLE OF THE EMAILS
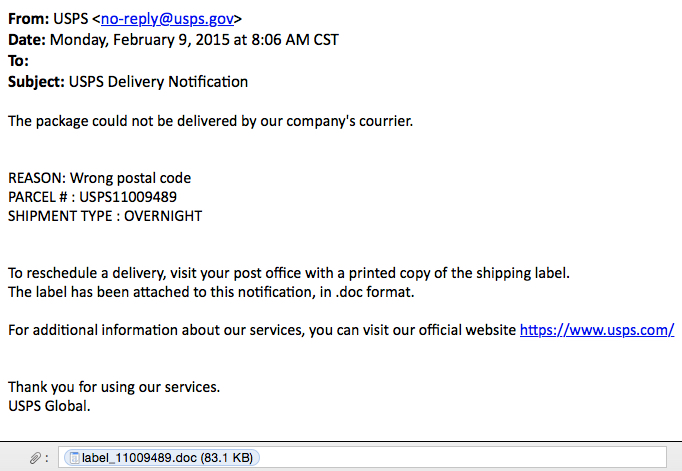
SCREENSHOT:
MESSAGE TEXT:
From: USPS <no-reply@usps[.]gov>
Date: Monday, February 9, 2015 at 8:06 AM CST
To:
Subject: USPS Delivery Notification
The package could not be delivered by our company's courrier.
REASON: Wrong postal code
PARCEL # : USPS11009489
SHIPMENT TYPE : OVERNIGHT
To reschedule a delivery, visit your post office with a printed copy of the shipping label.
The label has been attached to this notification, in .doc format.
For additional information about our services, you can visit our official website hxxps[:]//www.usps[.]com/
Thank you for using our services.
USPS Global.
Attachment: label_11009489.doc (83.1 KB)
INFECTION TRAFFIC
FROM RUNNING THE MALICIOUS WORD DOCUMENT ON A VM:
- 2015-02-09 15:54:12 UTC - 91.220.131[.]29 port - GET /upd/install.exe
- 2015-02-09 15:55:01 UTC - port 443 - HTTPS traffic to: api.ipify[.]org
- 2015-02-09 15:55:02 UTC - 192.251.226[.]206 port 443 - start of HTTPS traffic to: bc7cxr6v3arxkffn.tor2web.blutmagie[.]de
- 2015-02-09 16:00:09 UTC - 82.130.26[.]27 port 443 - start of HTTPS traffic to: bc7cxr6v3arxkffn.tor2web[.]fi
- 2015-02-09 16:00:10 UTC - port 80 - aia.startssl[.]com - GET /certs/sub.class2.server.ca.crt
- 2015-02-09 16:00:10 UTC - port 80 - aia.startssl[.]com - GET /certs/ca.crt
- 2015-02-09 16:01:17 UTC - 38.229.70[.]4 port 443 - start of HTTPS traffic to: bc7cxr6v3arxkffn.tor2web[.]org
- 2015-02-09 16:01:18 UTC - 194.150.168[.]70 port 443 - start of HTTPS traffic to: bc7cxr6v3arxkffn.tor2web[.]org
ALERTS FROM THE INFECTED VM
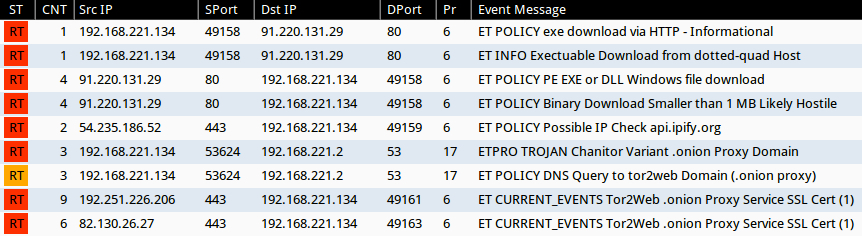
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- DNS queries for arious tor2web[.]org domain names - ETPRO TROJAN Chanitor Variant .onion Proxy Domain (sid:2809696)
- Various IP addresses - ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (1) (sid:2016806)
Talos (Sourcefire VRT) ruleset from Snort 2.9.7.0 on Debian 7:
- Pings to 1.1.2[.]2 - [1:29456:2] PROTOCOL-ICMP Unusual PING detected
- 91.220.131[.]29 port 80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 91.220.131[.]29 port 80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- DNS queries for arious tor2web[.]org domain names - [1:33216:1] INDICATOR-COMPROMISE DNS request for known malware domain tor2web[.]org
PRELIMINARY MALWARE ANALYSIS
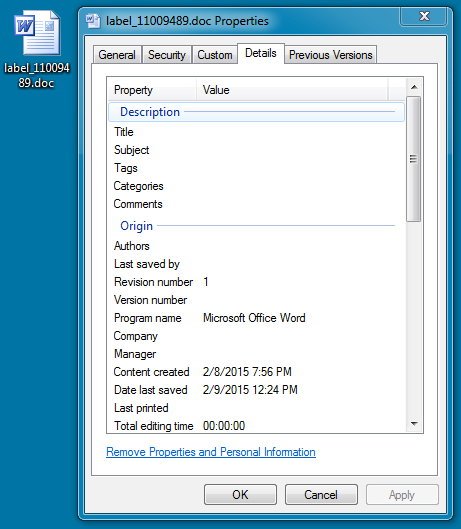
EMAIL ATTACHMENT:
File name: label_11009489.doc
File size: 62,976 bytes
MD5 hash: 97f6d88dcfe5fdcbf6cde2a588ad48bc
Detection ratio: 5 / 57
First submission: 2015-02-09 14:22:02
VirusTotal link: https://www.virustotal.com/en/file/0616f04ec50d2745f50b40b3ff6c7bf99924f8dea084569afa6fb3b971114b41/analysis/
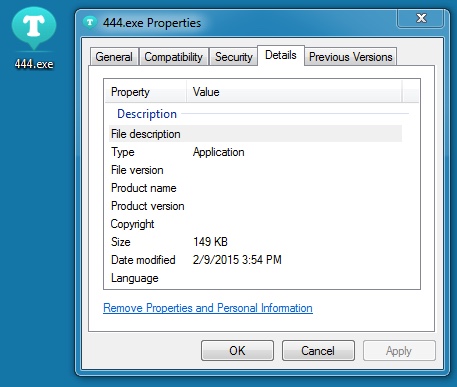
MALWARE FROM THE INFECTED VM - CHANITOR:
File name: C:\Users\User-1\AppData\Local\Temp\444.exe
File name: C:\Users\User-1\AppData\Roaming\Windows\winlogin.exe
File size: 153,088 bytes
MD5 hash: 559213eb0689549b424bc3aeafce0086
Detection ratio: 5 / 57
First submission: 2015-02-09 15:02:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/c20ffd843f1568e635478286721636af0aae0928d4f0b2b910037efe79d620f4/analysis/
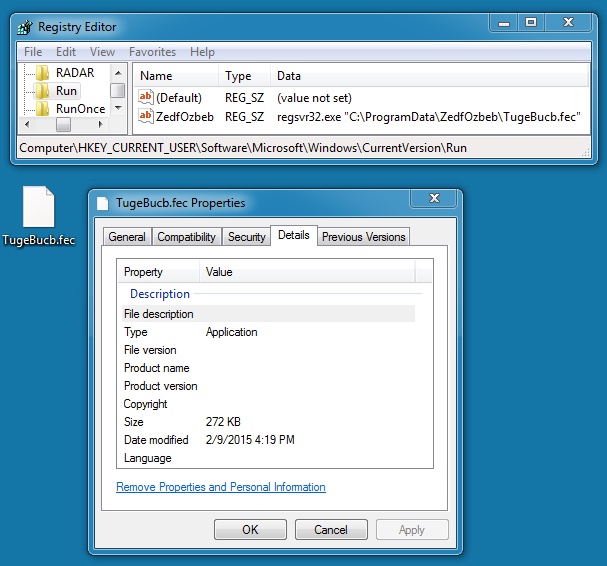
MALWARE FROM THE INFECTED VM - VAWTRAK:
File name: C:\ProgramData\ZedfOZbeb\TugeBucb.fec
File size: 278,528 bytes
MD5 hash: 337a01565dc614651d05a37c7cc8f477
Detection ratio: 7 / 57
First submission: 2015-02-09 16:19:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/71dcc32891588d60acbe7cbe04c038170e9f44120b03dba27a8ab6744674b875/analysis/
Click here to return to the main page.