2015-02-16 - CHANITOR/VAWTRAK ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
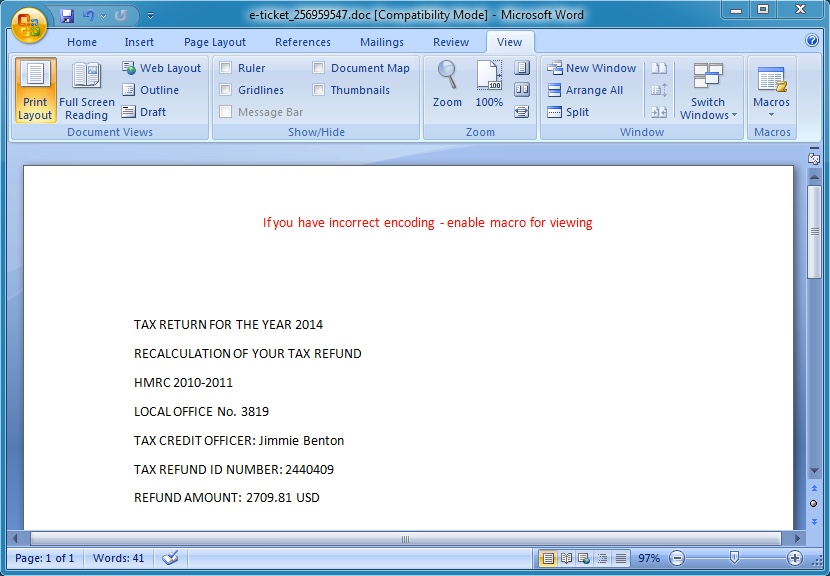
- When I'm looking for a fake e-ticket, I don't expect to see a fake tax return... These guys are sloppy.
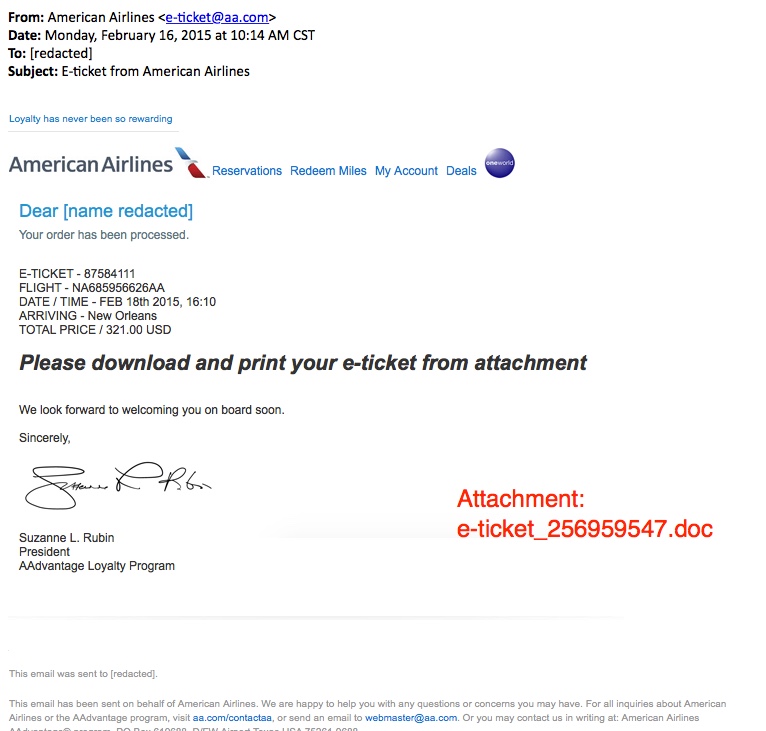
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: American Airlines <e-ticket@aa[.]com>
Date: Monday, February 16, 2015 at 10:14 AM CST
To:
Subject: E-ticket from American Airlines
Loyalty has never been so rewarding
Reservations Redeem Miles My Account Deals oneworld
Dear [recipient's name]
Your order has been processed.
E-TICKET - 87584111
FLIGHT - NA685956626AA
DATE / TIME - FEB 18th 2015, 16:10
ARRIVING - New Orleans
TOTAL PRICE / 321.00 USD
Please download and print your e-ticket from attachment
We look forward to welcoming you on board soon.
Sincerely,
Suzanne L. Rubin
President
AAdvantage Loyalty Program
Attachment: e-ticket_256959547.doc (90.6 KB)
TRAFFIC FROM INFECTED VM
ASSOCIATED DOMAINS:
- 66.33.209[.]254 - gmedsport[.]com - Malicious word document calls to this domain hosting Chanitor malware
- 192.251.226[.]206 - ukzo73z4inzpenmq.tor2web.blutmagie[.]de - Chanitor-related traffic for tor2web domain
- 82.130.26[.]27 - ukzo73z4inzpenmq.tor2web[.]fi - Chanitor-related traffic for tor2web domain
- 194.150.168[.]70 - ukzo73z4inzpenmq.tor2web[.]org - Chanitor-related traffic for tor2web domain
TRAFFIC FROM INFECTED VM:
- 2015-02-16 15:44:54 UTC - gmedsport[.]com - GET /plugins/xmlrpc/file.exe
- 2015-02-16 15:45:40 UTC - HTTPS traffic to api.ipify[.]org
- 2015-02-16 15:45:41 UTC - HTTPS traffic to: ukzo73z4inzpenmq.tor2web.blutmagie[.]de
- 2015-02-16 15:45:51 UTC - HTTPS traffic to: ukzo73z4inzpenmq.tor2web[.]fi
- 2015-02-16 15:45:52 UTC - aia.startssl[.]com - GET /certs/sub.class2.server.ca.crt
- 2015-02-16 15:45:52 UTC - aia.startssl[.]com - GET /certs/ca.crt
- 2015-02-16 15:45:53 UTC - HTTPS traffic to: ukzo73z4inzpenmq.tor2web[.]org
ALERTS FROM INFECTED VM
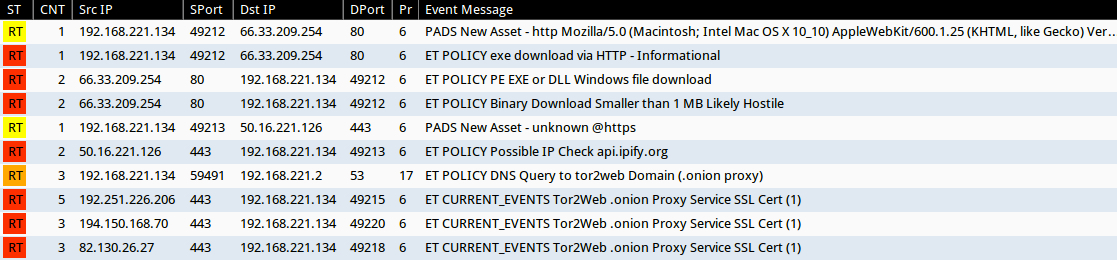
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- Various IP addresses - ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (1) (sid:2016806)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Debian 7:
- 1.1.2[.]2 - [1:29456:2] PROTOCOL-ICMP Unusual PING detected
- 66.33.209[.]254 port 80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- DNS request for: ukzo73z4inzpenmq.tor2web[.]org - [1:33216:1] INDICATOR-COMPROMISE DNS request for known malware domain tor2web[.]org
PRELIMINARY MALWARE ANALYSIS
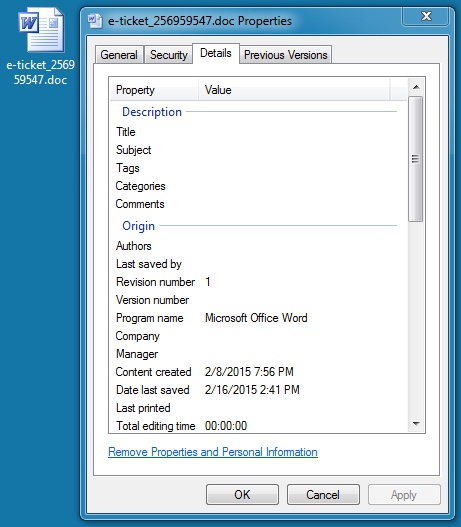
EMAIL ATTACHMENT:
File name: e-ticket_256959547.doc
File size: 68,608 bytes
MD5 hash: c075bcd452d7ff56968ed7a213459bdc
Detection ratio: 1 / 57
First submission: 2015-02-16 15:36:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/78d84f8368b44692b74500f6071788170bc2fef27363586b6d569d745d1cf2a2/analysis/
CHANITOR DOWNLOADED BY THE MALICIOUS WORD DOCUMENT:
File name: C:Users\username\AppData\Local\Temp\444.exe
File size: 142,848 bytes
MD5 hash: 53752a41ed21172343f678423d6c9a44
Detection ratio: 1 / 57
First submission: 2015-02-16 15:27:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/f5b1deee9f83f8567e02e1f303a35606e2cd60f01136f8b5eea264239538e60a/analysis/
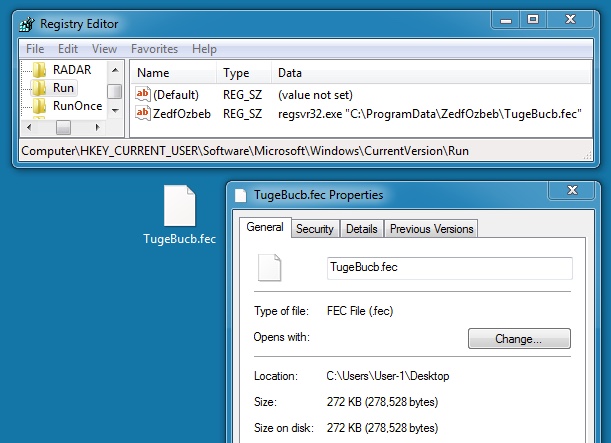
VAWTRAK DOWNLOADED BY CHANITOR:
File name: C:\ProgramData\ZedfOzbeb\TugeBucb.fec
File size: 278,528 bytes
MD5 hash: 1d154d14527fef4e3ae0f9da997ca7e2
Detection ratio: 39 / 57
First submission: 2015-02-16 16:14:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/a6a203be00ae8155e495e0f47931d76b730fa11707e449bb7e04f0f2df6499ec/analysis/
Click here to return to the main page.