2015-03-23 - ANGLER EK PUSHES RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-03-23-Angler-EK-with-post-infection-traffic.pcap.zip
- 2015-03-23-Angler-EK-malware-and-artifacts.zip
NOTES:
- Matthew Mesa informed me the malware payload is Reveton.
Shown above: Partial view of lock screen generated by the malware payload from Angler EK.
CHAIN OF EVENTS
ANGLER EK:
- 144.76.177[.]42 port 80 - bezbronnybullfinches.evolvingnutritionllc[.]com - GET /pews-bathrobe-understatement/2333676765
- 144.76.177[.]42 port 80 - bezbronnybullfinches.evolvingnutritionllc[.]com - GET /eS9vXVpGOZhiD1CflWv8J9AeWGa_auetZVWzsTeBZqZTSXlR
- 144.76.177[.]42 port 80 - bezbronnybullfinches.evolvingnutritionllc[.]com - GET /VZsq9DV0HzNyc0_HxSiYUpc4_NiyZW729YthGRWUQOssgshN
POST-INFECTION TRAFFIC:
- 107.181.174[.]5 port 443 - encrypted or obfuscated traffic
- 107.181.174[.]5 port 80 - encrypted or obfuscated traffic
- 109.200.5[.]91 port 443 - encrypted or obfuscated traffic
- 109.200.5[.]91 port 80 - encrypted or obfuscated traffic
- 162.244.33[.]159 port 443 - encrypted or obfuscated traffic
- 162.244.33[.]159 port 80 - encrypted or obfuscated traffic
ALERTS
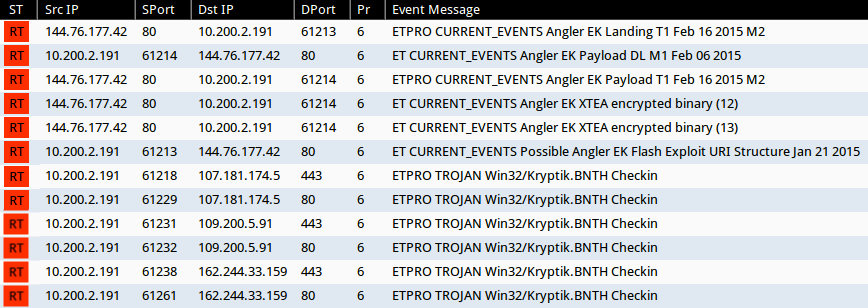
Signature hits from the Emerging Threats and ETPRO rulesets using Suricata on Security Onion (without ET POLICY or ET INFO events):
- 144.76.177[.]42 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing T1 Feb 16 2015 M2 (sid:2809810)
- 144.76.177[.]42 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing T1 Feb 16 2015 M2 (sid:2809811)
- 144.76.177[.]42 port 80 - ETPRO CURRENT_EVENTS Angler EK Payload T1 Feb 16 2015 M2 (sid:2809815)
- 144.76.177[.]42 port 80 - ET CURRENT_EVENTS Angler EK Payload DL M1 Feb 06 2015 (sid:2020385)
- 144.76.177[.]42 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (12) (sid:2020591)
- 144.76.177[.]42 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (13) (sid:2020592)
- 144.76.177[.]42 port 80 - ET CURRENT_EVENTS Possible Angler EK Flash Exploit URI Structure Jan 21 2015 (sid:2020234)
- 107.181.174[.]5 port 443 - ETPRO TROJAN Win32/Kryptik.BNTH Checkin (sid:2807230)
- 107.181.174[.]5 port 80 - ETPRO TROJAN Win32/Kryptik.BNTH Checkin (sid:2807230)
- 109.200.5[.]91 port 443 - ETPRO TROJAN Win32/Kryptik.BNTH Checkin (sid:2807230)
- 109.200.5[.]91 port 80 - ETPRO TROJAN Win32/Kryptik.BNTH Checkin (sid:2807230)
- 162.244.33[.]159 port 443 - ETPRO TROJAN Win32/Kryptik.BNTH Checkin (sid:2807230)
- 162.244.33[.]159 port 80 - ETPRO TROJAN Win32/Kryptik.BNTH Checkin (sid:2807230)
Signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.2 on Debian 7:
- 144.76.177[.]42 port 80 - [1:33182:1] EXPLOIT-KIT Angler exploit kit outbound Adobe Flash request
- 109.200.5[.]91 port 80 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 109.200.5[.]91 port 80 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 162.244.33[.]159 port 80 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 162.244.33[.]159 port 80 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 107.181.174[.]5 port 80 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 107.181.174[.]5 port 80 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
MALWARE FROM THE INFECTED HOST
File name: C:\ProgramData\ADC290768.cpp (decrypted Angler EK malware payload, a DLL file)
File size: 237,568 bytes
MD5 hash: 95a0cafb24e9edcbdb52e685f7b5a5b3
Detection ratio: 22 / 57
First submission: 2015-03-23 18:56:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/d46699b085adb4e235c80c5359cff975c5b5e3f9e136400d89ad29af8fad4c72/analysis/
File name: C:\ProgramData\C328CD902.zot (another DLL)
File size: 358,912 bytes
MD5 hash: 2479dd9b68bd7c137edae000c728f86d
Detection ratio: 9 / 57
First submission: 2015-03-23 18:59:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/fe3598d7ce646329c95d17f8a6706a4a8f758e780f426b4ec527ff33c4df3b55/analysis/
Click here to return to the main page.

