2015-05-06 - RIG EK CHANGED HOW IT SENDS THE MALWARE PAYLOAD
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
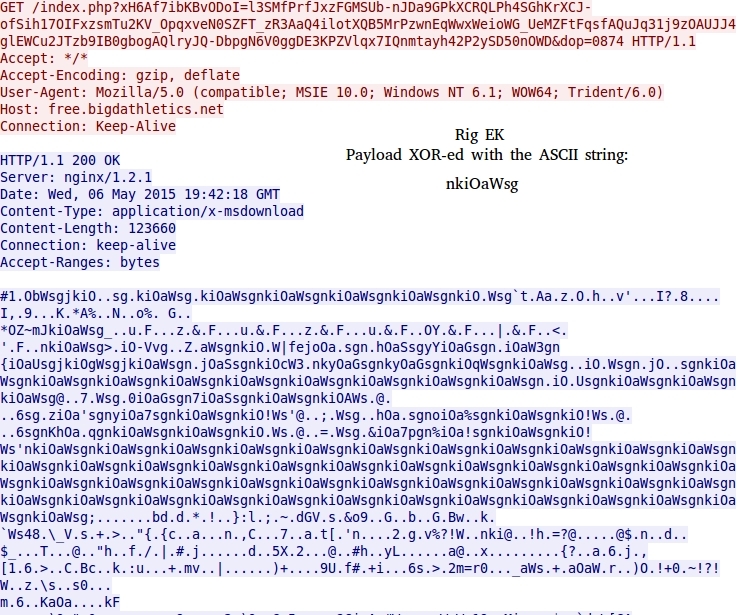
- Rig EK is now using Nuclear EK-style ASCII strings to XOR the malware payload.
- I originally noticed this in in a pcap from a Threatglass entry.
- Didn't think to ask around about it until now.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 162.255.119[.]254 port 80 - dobuntu[.]com - Compromised website
- 93.190.142[.]195 port 80 - fatburningfast[.]net - Redirect (gate)
- 95.128.182[.]108 port 80 - free.bigdathletics[.]net - Rig EK
- 80.242.123[.]144 port 80 - androjose[.]com and andromike[.]com - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
- 2015-05-06 19:42:09 UTC - dobuntu[.]com - GET /
- 2015-05-06 19:42:10 UTC - fatburningfast[.]net - GET /images/order.php
RIG EK:
- 2015-05-06 19:42:12 UTC - free.bigdathletics[.]net - GET /?xH6Af7ibKBvODoI=l3SKfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN
0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioWG_UeMZFtFqsfAQuJq31j9zOAUJJ4glEWCu2JTzb9IB0gbrA
- 2015-05-06 19:42:13 UTC - free.bigdathletics[.]net - GET /index.php?xH6Af7ibKBvODoI=l3SMfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioWG_UeMZFtFqsfAQuJq31j9zOAUJJ4glEWCu2JTzb9IB0gbogAQlryJQ-DbpgN6V0ggEkqfPZVlqx7IQnmtayh42P
28QTJwkKM
- 2015-05-06 19:42:14 UTC - free.bigdathletics[.]net - GET /favicon.ico
- 2015-05-06 19:42:16 UTC - free.bigdathletics[.]net - GET /index.php?xH6Af7ibKBvODoI=l3SMfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioWG_UeMZFtFqsfAQuJq31j9zOAUJJ4glEWCu2JTzb9IB0gbogAQlryJQ-DbpgN6V0ggDE3KPZVlqx7IQnmtayh42
P2ySD50nOWD&dop=0874
POST-INFECTION TRAFFIC:
- 2015-05-06 19:43:24 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:43:25 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:29 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:32 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:36 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:40 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:40 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:43:41 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:41 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:43:45 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:48 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:43:48 UTC - andromike[.]com - GET /down/spread23.exe
- 2015-05-06 19:43:49 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:50 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:43:52 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:56 UTC - andromike[.]com - GET /spread23.exe
- 2015-05-06 19:43:57 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:43:58 UTC - andromike[.]com - GET /down/spread23.exe
- 2015-05-06 19:44:00 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:44:00 UTC - androjose[.]com - POST /rep159.php
- 2015-05-06 19:44:29 UTC - androjose[.]com - POST /rep159.php
Click here to return to the main page.