2015-05-07 - ANGLER EK FROM 94.242.255[.]60 DELIVERS AN UNNAMED RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-05-07-Angler-EK-sends-an-unnamed-ransomware.pcap.zip
- 2015-05-07-Angler-EK-and-the-unnamed-ransomware-files.zip
NOTES:
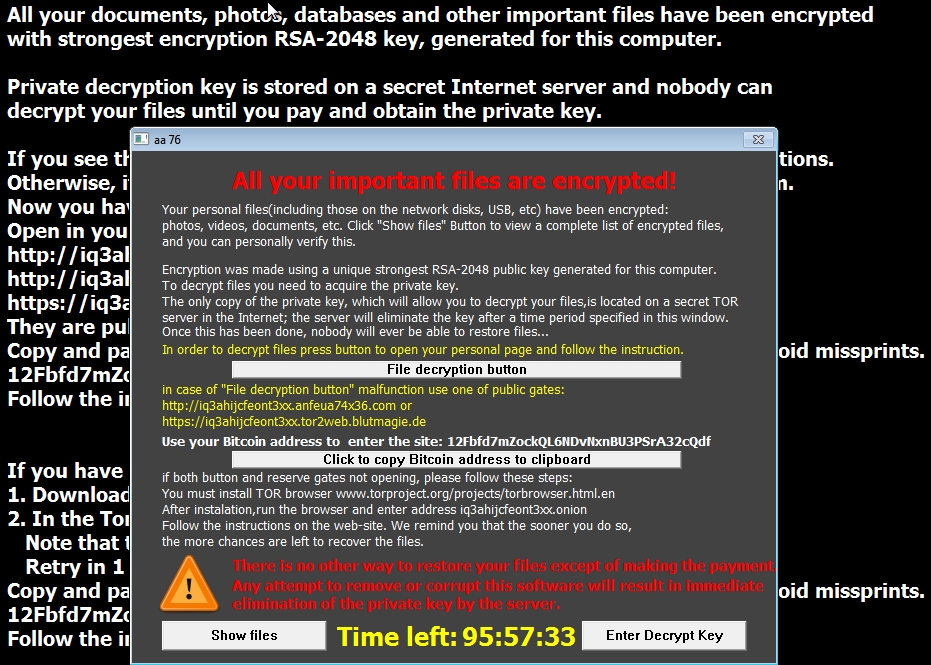
- About 2 hours after my last blog post (Angler EK delivering Alpha Crypt), I got a similar CryptoLocker-like sample from a different Angler EK infection.
- Previous Alpha Crypt posts are at 2015-04-30, 2015-05-06, and 2015-05-07 (earlier today).
- I tried all the URLs from the ransomware instructions, so the pcap has all the domains/IP addresses involved.
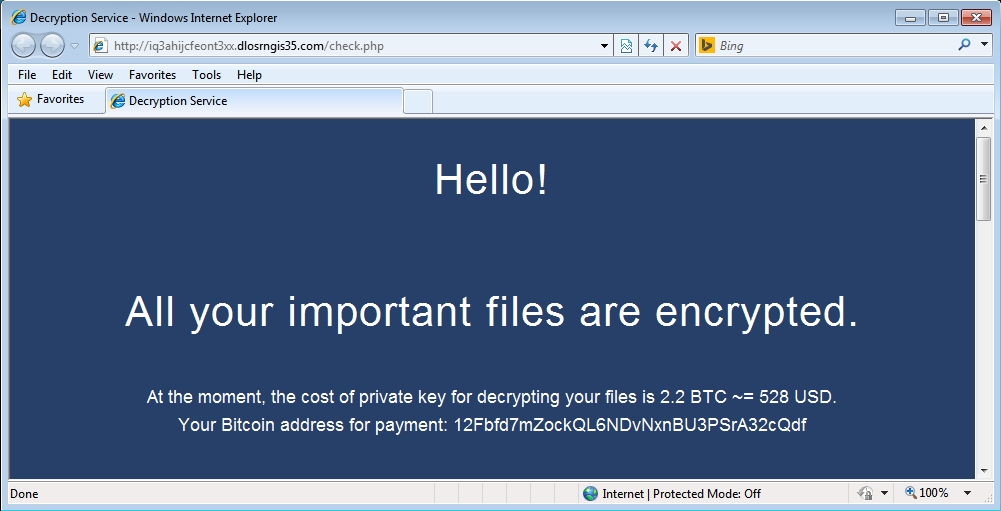
- Bitcoin address for this sample's ransom payment is: 12Fbfd7mZockQL6NDvNxnBU3PSrA32cQdf
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 5.101.118[.]147 port 80 - cndqezvmp.servepics[.]com - Redirect/gate to Angler EK
- 94.242.255[.]60 port 80 - geloofsywer-sukulumb.globaltechdeals[.]net - Angler EK
- 52.6.1[.]107 port 80 - ipinfo[.]io - IP address check by the malware [not inherently malicious]
- 104.18.63[.]63 port 80 - 24u4jf7s4regu6hn.dlosrngis35[.]com - ransomware post-infection traffic
- 104.18.62[.]63 port 80 - iq3ahijcfeont3xx.dlosrngis35[.]com - ransomware post-infection traffic
- 104.18.55[.]35 port 80 - iq3ahijcfeont3xx.anfeua74x36[.]com - ransomware post-infection traffic
- 192.251.226[.]206 port 443 - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - ransomware post-infection traffic
REDIRECT/GATE TO ANGLER EK:
- 2015-05-07 19:23:45 UTC - cndqezvmp.servepics[.]com - GET /wordpress/?bf7N&utm_source=le
ANGLER EK:
- 2015-05-07 19:23:46 UTC - geloofsywer-sukulumb.globaltechdeals[.]net - GET /quavers-patrol-comfort-ingress/216044123933311401
- 2015-05-07 19:23:48 UTC - geloofsywer-sukulumb.globaltechdeals[.]net - GET /0QOXr7VPVyKQLk1u4-3JIFIe2EoL-y3mPYrT2pvLbaH5a7vM
- 2015-05-07 19:23:49 UTC - geloofsywer-sukulumb.globaltechdeals[.]net - GET /CX6i9DGTd9NRjFaF0cv8RpuGLBFC7L-SOg7xASQtxljWePp6
POST-INFECTION TRAFFIC:
- 2015-05-07 19:23:50 UTC - ipinfo[.]io - GET /ip
- 2015-05-07 19:23:50 UTC - 24u4jf7s4regu6hn.dlosrngis35[.]com - GET /ping.php?U3ViamVjdD1QaW5nJmtleT05NDU2ND[long string of characters]
- 2015-05-07 19:24:10 UTC - 24u4jf7s4regu6hn.dlosrngis35[.]com - GET /ping.php?U3ViamVjdD1DcnlwdGVkJmtleT05ND[long string of characters]
- 2015-05-07 19:24:16 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /?enc=12Fbfd7mZockQL6NDvNxnBU3PSrA32cQdf
- 2015-05-07 19:24:18 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /check.php
- 2015-05-07 19:24:19 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /style.css
- 2015-05-07 19:24:19 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /style.css
- 2015-05-07 19:24:20 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /img/curr.svg
- 2015-05-07 19:24:20 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /img/decrypt.svg
- 2015-05-07 19:24:22 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /favicon.ico
- 2015-05-07 19:26:26 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /img/curr_hover.svg
- 2015-05-07 19:26:30 UTC - iq3ahijcfeont3xx.dlosrngis35[.]com - GET /img/curr_hover.svg
- 2015-05-07 19:27:08 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /
- 2015-05-07 19:27:09 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /style.css
- 2015-05-07 19:27:11 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /img/base.svg
- 2015-05-07 19:27:12 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /favicon.ico
- 2015-05-07 19:27:30 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /index.php?enc=12Fbfd7mZockQL6NDvNxnBU3PSrA32cQdf
- 2015-05-07 19:27:32 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /check.php
- 2015-05-07 19:27:33 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /img/curr.svg
- 2015-05-07 19:27:33 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /img/decrypt.svg
- 2015-05-07 19:27:34 UTC - iq3ahijcfeont3xx.anfeua74x36[.]com - GET /favicon.ico
- 2015-05-07 19:27:50 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-07 19:27:51 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-07 19:27:51 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-07 19:28:19 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD:
File name: 2015-05-07-ransomware-sample.exe
File size: 260,608 bytes
MD5 hash: 17a8119f8a6c17937bc2f9549b7e2e42
Detection ratio: 3 / 36
First submission to VirusTotal: 2015-05-07 20:00:25 UTC
Click here to return to the main page.