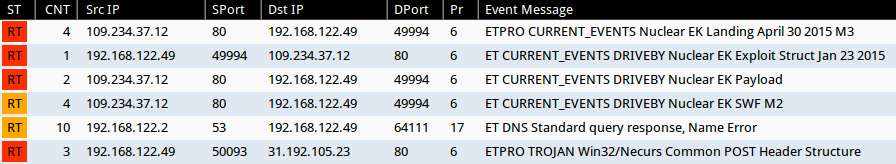
2015-05-14 - NUCLEAR EK FROM 109.234.37[.]12 - SENDS NECURS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-05-14-Nuclear-EK-traffic.pcap.zip
- Malware payload is available at the links listed in the preliminary malware analysis section.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 185.14.30[.]218 port 80 - dir.mentetransicao[.]com - Redirect/gate
- 109.234.37[.]12 port 80 - web.yunisatiarahayu[.]com - Nuclear EK
- 31.192.105[.]23 port 80 - 31.192.105[.]23 - Post-infection HTTP traffic
- 185.14.28[.]149 port 80 - 185.14.28[.]149 - Post-infection HTTP traffic
- various domains and IP addresses - other post-infection UDP traffic and DNS queries
REDIRECT/GATE:
- 2015-05-14 20:52:37 UTC - 185.14.30[.]218 port 80 - dir.mentetransicao[.]com - GET /js/script.js
NUCLEAR EK:
- 2015-05-14 20:52:39 UTC - 109.234.37[.]12 port 80 - web.yunisatiarahayu[.]com -
GET /U1YNUgpIBBlOUQQaTBBXXRVVQQxYRgdcVBxMGgVbWA.html
- 2015-05-14 20:52:40 UTC - 109.234.37[.]12 port 80 - web.yunisatiarahayu[.]com -
GET /UB1JSAAHAQNVSFdIBBlOUQQaTBBXXRVVQQxYRgdcVBxMGgVbWBkBBEgGAVYXBVECG1cMABoFAVYIAlUCAlAASABYBA
- 2015-05-14 20:52:41 UTC - 109.234.37[.]12 port 80 - web.yunisatiarahayu[.]com -
GET /UwxVURpSBlFfWBoFSVRFQwNWGxxMWg9HVBFQVRRVXQRAQUhXWghFDFYaB1EKGlcDA0sLAVJIBFEKBVAHA1IMDRoDSTVRZDRuXjZJXQ
- 2015-05-14 20:52:42 UTC - 109.234.37[.]12 port 80 - web.yunisatiarahayu[.]com -
GET /UwxVURpSBlFfWBoFSRlOUQQaTBBXXRVVQQxYRgdcVBxMGgVbWBkBBEgGAVYXBVECG1cMABoFAVYIAlUCAlAASFFIRjN_eyxefCxNVg
POST-INFECTION HTTP TRAFFIC:
- 2015-05-14 20:53:58 UTC - 31.192.105[.]23 port 80 - 31.192.105[.]23 - POST /forum/db.php
- 2015-05-14 20:53:59 UTC - 31.192.105[.]23 port 80 - 31.192.105[.]23 - POST /forum/db.php
- 2015-05-14 20:55:50 UTC - 185.14.28[.]149 port 80 - 185.14.28[.]149 - POST /forum/db.php
POST-INFECTION DNS QUERIES:
- 2015-05-14 20:52:45 UTC - fikfijthbxykmgx[.]com [server response: no such name]
- 2015-05-14 20:52:45 UTC - wuxccplzcfiowte[.]com [server response: no such name]
- 2015-05-14 20:52:45 UTC - petpxvruqwuybi[.]com [server response: no such name]
- 2015-05-14 20:52:45 UTC - rfyjxuejjq[.]com [server response: no such name]
- 2015-05-14 20:52:49 UTC - npkxghmoru[.]biz [server response: no such name]
- 2015-05-14 20:54:45 UTC - cwnypbagpgiaw[.]com [server response: no such name]
- 2015-05-14 20:54:45 UTC - tshgjsneqwgibi[.]com [server response: no such name]
- 2015-05-14 20:54:45 UTC - diayygcaiugkhqz[.]com [server response: no such name]
- 2015-05-14 20:54:45 UTC - cmlcrsvrgu[.]com [server response: no such name]
- 2015-05-14 20:55:44 UTC - npkxghmoru[.]biz [server response: no such name]
POST-INFECTION UDP TRAFFIC:
- 2015-05-14 20:52:49 UTC - 190.112.99[.]83 port 22858
- 2015-05-14 20:52:54 UTC - 139.191.135[.]110 port 18321
- 2015-05-14 20:52:59 UTC - 181.208.20[.]70 port 6693
- 2015-05-14 20:53:04 UTC - 88.87.21[.]131 port 15342
- 2015-05-14 20:53:04 UTC - 88.87.21[.]131 port 15342
- 2015-05-14 20:53:14 UTC - 212.50.76[.]64 port 27635
- 2015-05-14 20:53:24 UTC - 151.237.116[.]213 port 31953
- 2015-05-14 20:53:29 UTC - 186.138.87[.]54 port 25194
- 2015-05-14 20:53:34 UTC - 200.109.210[.]162 port 30132
- 2015-05-14 20:53:39 UTC - 46.252.56[.]92 port 11647
- 2015-05-14 20:53:44 UTC - 74.197.207[.]50 port 32050
- 2015-05-14 20:53:49 UTC - 130.204.96[.]245 port 17263
- 2015-05-14 20:53:54 UTC - 158.109.236[.]131 port 20245
- 2015-05-14 20:54:31 UTC - 86.124.94[.]244 port 16122
- 2015-05-14 20:54:41 UTC - 190.193.115[.]193 port 14752
- 2015-05-14 20:54:46 UTC - 200.90.115[.]3 port 21837
- 2015-05-14 20:54:51 UTC - 5.15.177[.]237 port 30901
- 2015-05-14 20:54:56 UTC - 71.88.140[.]246 port 6465
- 2015-05-14 20:55:01 UTC - 186.223.76[.]237 port 13559
- 2015-05-14 20:55:06 UTC - 89.215.36[.]121 port 26312
- 2015-05-14 20:55:11 UTC - 186.88.206[.]180 port 16066
- 2015-05-14 20:55:21 UTC - 216.171.33[.]252 port 25370
- 2015-05-14 20:55:26 UTC - 186.93.102[.]161 port 5572
- 2015-05-14 20:55:36 UTC - 89.136.251[.]73 port 30273
- 2015-05-14 20:55:41 UTC - 190.105.47[.]149 port 30123
- 2015-05-14 20:57:51 UTC - 187.245.144[.]160 port 29466
- 2015-05-14 20:58:51 UTC - 81.196.99[.]94 port 13947
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD:
File name: 2015-05-14-Nuclear-EK-malware-payload.exe
File size: 115,200 bytes
MD5 hash: 0db7cbfc1220b22b47eddd945f99940c
Detection ratio: 10 / 57
First submission to VirusTotal: 2015-05-14 21:27:25 UTC
Click here to return to the main page.