2015-10-28 - TRAFFIC ANALYSIS EXERCISE - MIDGE FIGGINS INFECTED HER COMPUTER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive containing the pcap: 2015-10-28-traffic-analysis-exercise.pcap.zip 9.7 MB (9,654,231 bytes)
- Zip archive of malware found on the infected host: 2015-10-28-traffic-analysis-exercise-malware.zip 74.7 kB (74,704 bytes)
SCENARIO
At your company's Security Operations Center (SOC), an analyst saw an alert for Gootkit and discovered an infected computer. The alert was traced to Midge Figgins, who is an executive assistant for your Chief Executive Officer (CEO).
Midge's Windows desktop computer was confiscated, and the Help Desk re-imaged it. Before it was re-imaged, a Help Desk technician retrieved malware from the infected host.
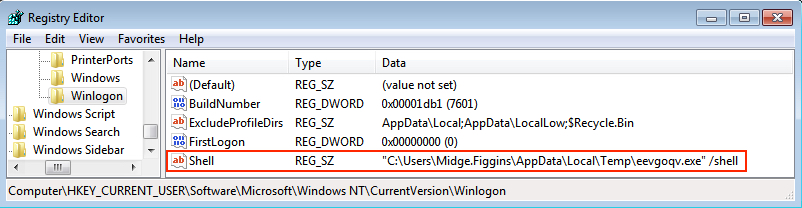
Shown above: Registry key related to malware found on the infected host.
Unfortunately, the analyst didn't document his findings. No one knows how Midge Figgins infected her computer, and people are now asking about it.
You've been tasked to write an incident report. You talk with Midge, but she doesn't remember anything unusual. You only have a pcap of the traffic and malware from the infected host.
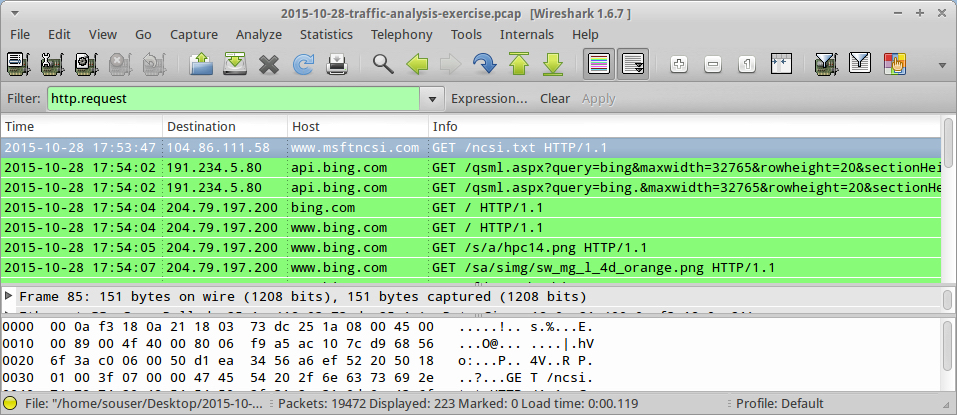
Shown above: Wireshark with a pcap of the infection traffic related to Midge's computer.
REPORTING
Your incident report should include:
- Date and time of the activity.
- The infected computer's IP address.
- The infected computer's MAC address.
- The infected computer's host name.
- Domains and IP addresses of any related traffic.
- The root cause of the infection.
- Information about malware found on the infected host.
ANSWERS
- Click here for the answers.