2016-02-02 - GUEST BLOG POST BY LENNY CONWAY - PROFILING THE EXPLOIT KIT
NOTES:
- This blog post was submitted by Lenny Conway, a computer security professional from New York.
INTRODUCTION
In the past few days, I've examined some of the Flash Player exploits from Brad's blog entries on exploit kit (EK) traffic. You can usually grab these .swf files from the pcaps and extract any scripts from them using Flare (http://www.nowrap.de/flare.html). Data from these scripts can reveal trends in exploits used by the different EKs. This data can help profile an EK.
EXTRACTING THE FLASH EXPLOIT FROM A PCAP
The image below shows how you can export HTTP objects ( File --> Export Objects --> HTTP ) on one of the pcaps from the malware-traffic-analysis blog. In this case, zas.allutahlistings[.]net is the domain pushing Angler EK, and the Content Type shows applicaion/x-shockwave-flash.
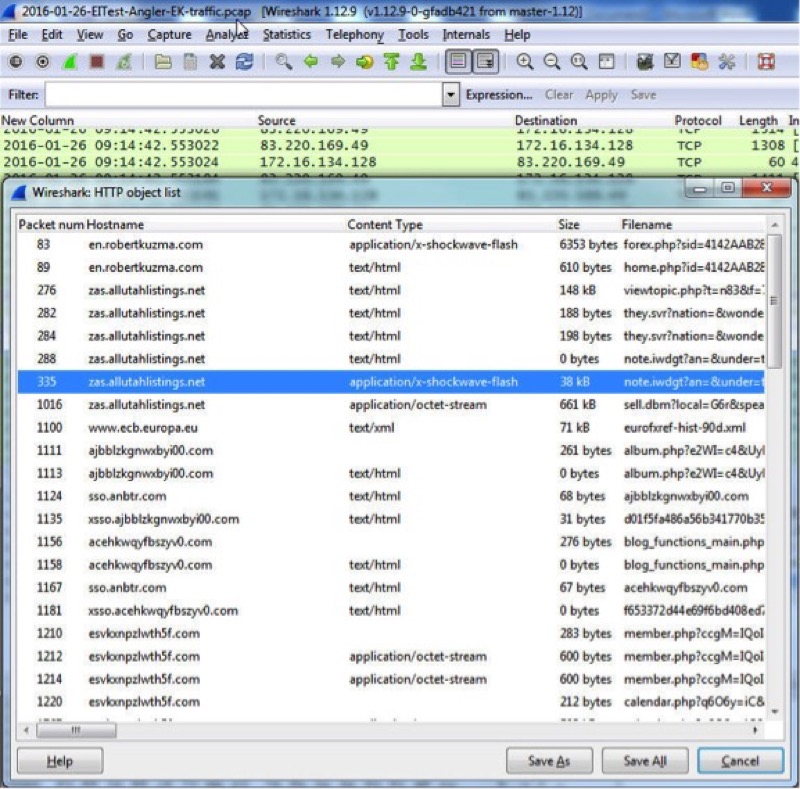
Save the object as an .swf file.
REVIEWING ACTIONSCRIPT FROM THE FLASH FILE
ActionScript is a programming language used for the Flash Player runtime environment. Decompling the .swf file with Flare will produce a text file containing the ActionScript. This text file will have an .flr extension.
You can find metadata about the Flash exploit by reviewing the .flr file in a text editor.
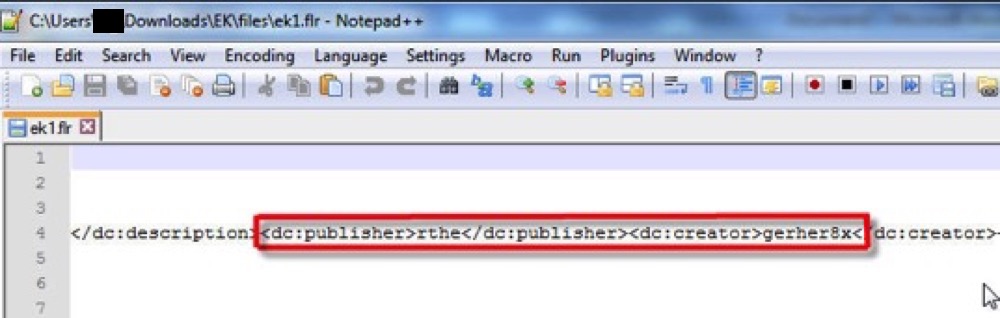
The image below shows some of the metadata I gathered from .swf files in pcaps from Brad's blog entries.
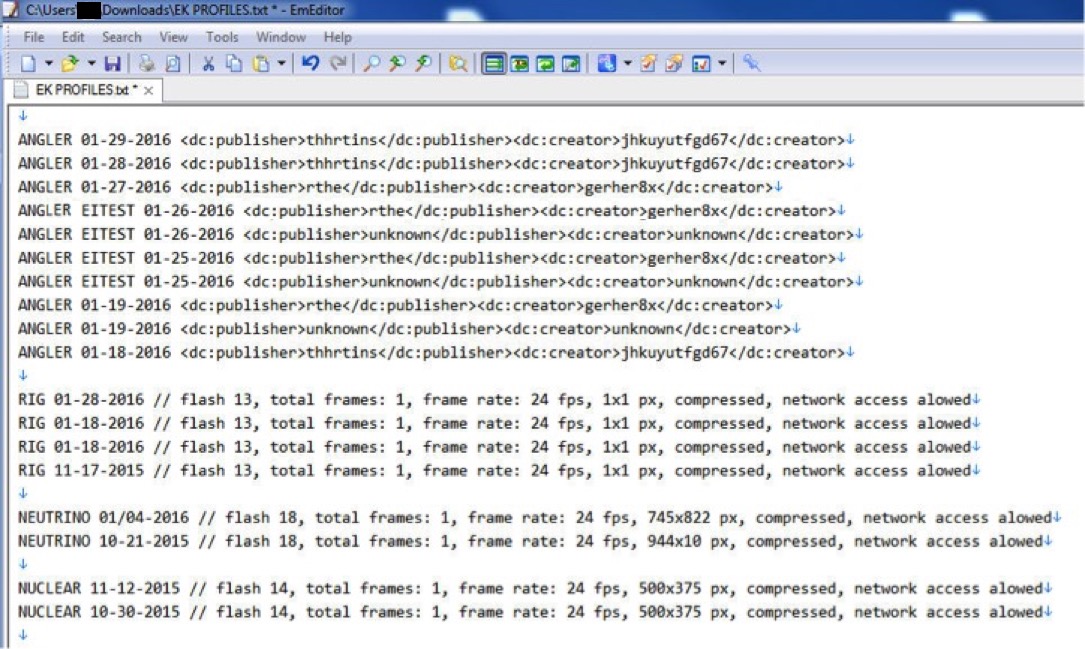
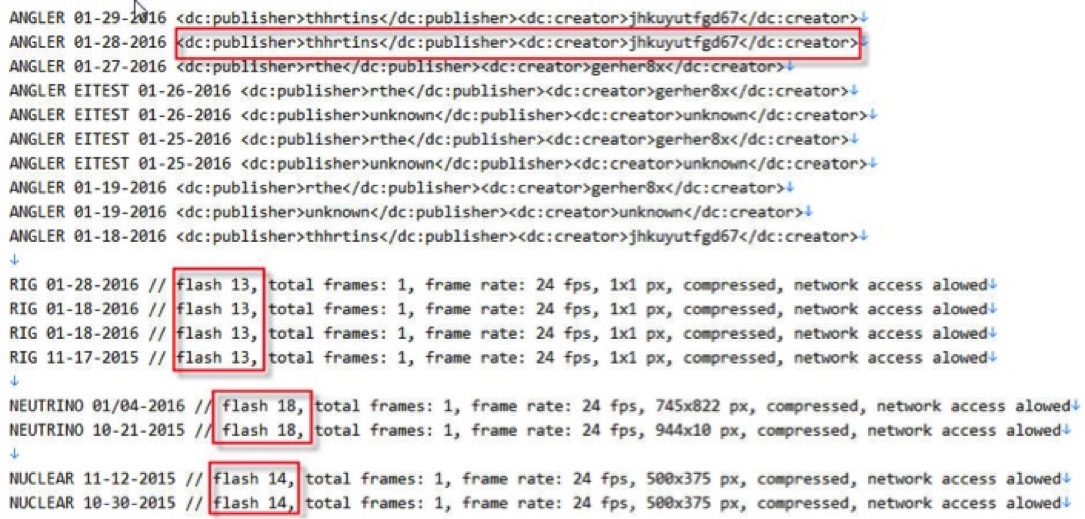
Notable patterns are highlighted below.
PRELIMINARY FINDINGS
Based on this limited sample, Flash exploits from Anger EK appear to always have a publisher and creator. Publisher and creator are absent in Flash exploits from Rig, Neutrino, and Nuclear EKs; however, these other EKs can be identified by their stated Flash version number.
Click here to return to the main page.
