2016-02-22 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-22-Angler-EK-data-dump-4-pcaps.zip 3.0 MB (3,010,755 bytes)
- 2016-02-22-Angler-EK-data-dump-malware-and-artifacts.zip 1.6 MB (1,590,772 bytes)
NOTES:
- 3 out of the 4 pcaps have injected script from the compromised website leading to Angler EK.
- 1 of the 4 pcaps has an "admedia" gate between the compromised website and Angler EK.
- For more background on "admedia" Angler EK, see the following posts:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741

Shown above: An example of injected script in pages from the compromised websites (3 of the 4 that led directly to Angler EK).
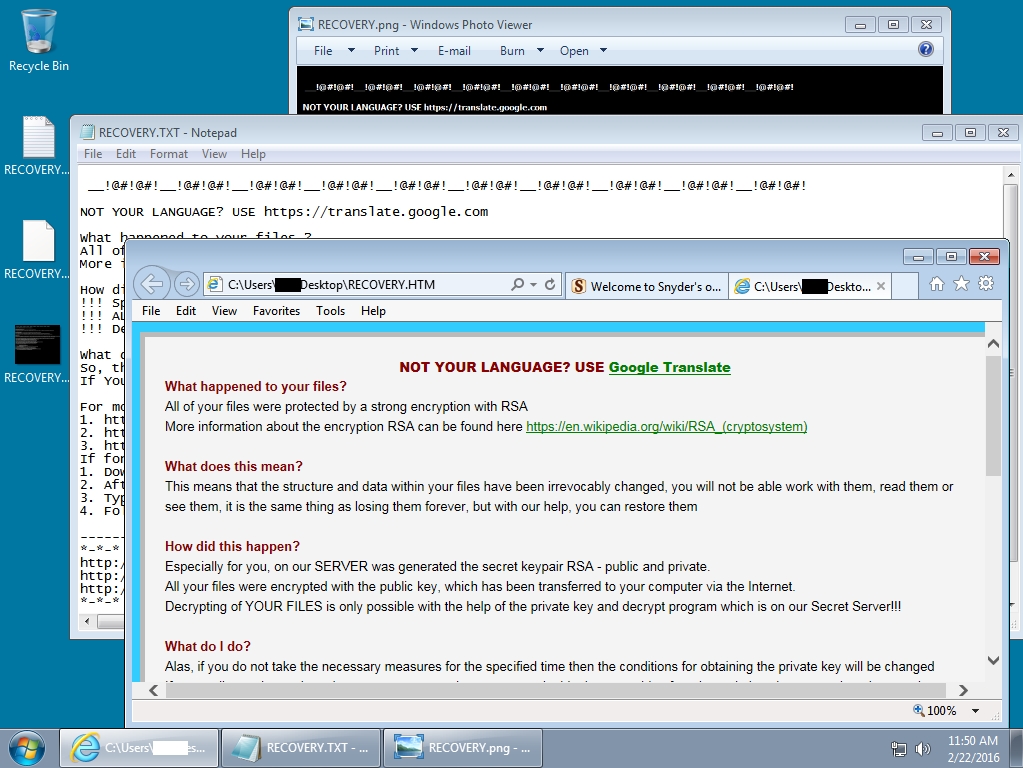
Shown above: A screenshot from the infected Windows host after Angler EK delivered TeslaCrypt ransomware.
DETAILS
2016-02-22 17:46 UTC:
- www.snydersofhanover[.]com - Compromised website
- 66.225.241[.]138 port 80 - hosialactaga.yourfinalfarewell[.]org - Angler EK
- 108.174.112[.]194 port 80 - dustywinslow[.]com - TeslaCrypt ransomware callback traffic
2016-02-22 18:39 UTC:
- www.todoimpresion[.]com - Compromised website
- 66.225.241[.]138 port 80 - dampfmengen-lovepearls.finalfarewell[.]me - Angler EK
- 108.174.112[.]194 port 80 - dustywinslow[.]com - TeslaCrypt ransomware callback traffic
2016-02-22 20:08 UTC:
- www.skinnymom[.]com - Compromised website
- 188.166.149[.]17 port 80 - js.ogromnuezadnicu[.]info - "admedia" gate
- 80.78.253[.]141 port 80 - away.luvdawgtshirtandgiftcompany[.]net - Angler EK
- 108.174.112[.]194 port 80 - dustywinslow[.]com - TeslaCrypt ransomware callback traffic
- 103.27.60[.]14 port 80 - dongxinh[.]com - TeslaCrypt ransomware callback traffic
2016-02-22 20:59 UTC:
- naplesbug[.]com - Compromised website
- 66.225.241[.]138 port 80 - langveisfrsotilasjohdossa.fallinthe4th[.]com - Angler EK
- 107.180.2[.]115 port 80 - salaeigroup[.]com - TeslaCrypt ransomware callback traffic
$ md5sum *.exe
- 9ad23a7b836d0ae4e75fb427ce9d3a96 2016-02-22-Admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-skinnymom_com.exe
- bb312126da8010e571d6691c8ff3ce2b 2016-02-22-Angler-EK-payload-TeslaCrypt-ransomware-after-naplesbug_com.exe
- d5a0c3c9cbd4164710bdf16fbd044687 2016-02-22-Angler-EK-payload-TeslaCrypt-ransomware-after-snydersofhanover_com.exe
- 9eeaa6c28bd07aa354a368538e94e85c 2016-02-22-Angler-EK-payload-TeslaCrypt-ransomware-after-todoimpresion_com.exe
$ md5sum *.swf
- e0d253cd3efe69c947a3b7277aebfd3e 2016-02-22-Admedia-Angler-EK-flash-exploit-after-skinnymom_com.swf
- 7b1d7e34870fd470a1751f5a36bb38dc 2016-02-22-Angler-EK-flash-exploit-after-naplesbug_com.swf
- 75c69901efed0bb80252a2ecba39ee77 2016-02-22-Angler-EK-flash-exploit-after-snydersofhanover_com.swf
- 75c69901efed0bb80252a2ecba39ee77 2016-02-22-Angler-EK-flash-exploit-after-todoimpresion_com.swf
Click here to return to the main page.
