2016-04-19 - TELSACRYPT RANSOMWARE ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-19-TeslaCrypt-ransomware-email-tracker.csv.zip 1.1 kB (1,083 bytes)
- 2016-04-19-emails-pushing-TeslaCrypt-ransomware-10-examples.zip 46.6 kB (46,597 bytes)
- 2016-04-19-TeslaCrypt-ransomware-files.zip 405.3 kB (405,287 bytes)
- 2016-04-19-TeslaCrypt-ransomware-infection.pcap.zip 223.5 kB (223,511 bytes)
NOTES:
- This subject line has been used in previous waves of malicious emails.
- It was documented in January 2016 dropping Dridex as seen in Dynamoo's Blog (link).
- A quick Google search shows many others have also seen this subject line used in other malicious emails.
- Today, this theme was used to distribute TeslaCrypt ransomware.
EMAILS
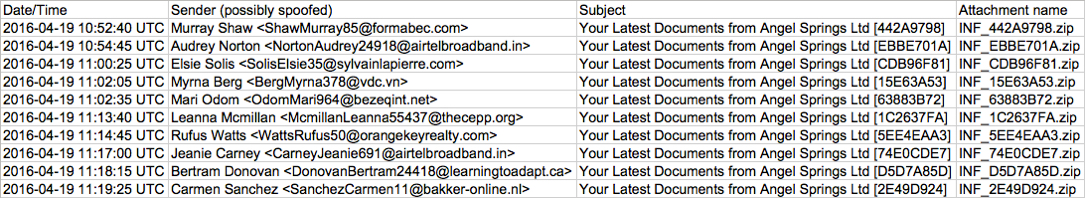
Shown above: Ten examples from this wave of emails pushing TeslaCrypt ransomware.
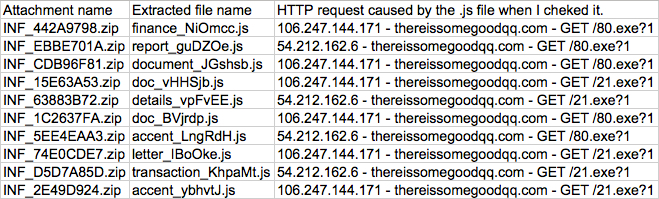
Shown above: More information on the attachments from those 10 emails.
SCREENSHOT FROM ONE OF THE EMAILS:
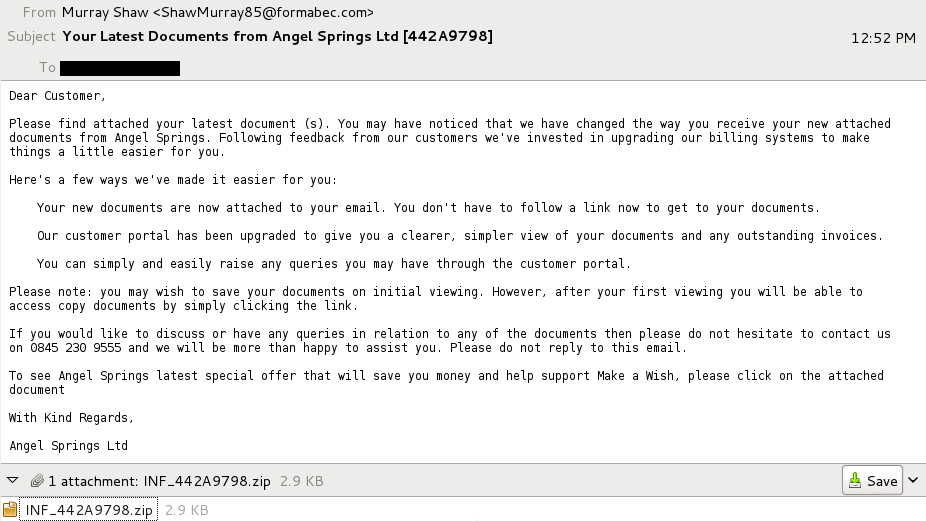
TEXT OF THE MESSAGE:
Dear Customer,
Please find attached your latest document (s). You may have noticed that we have changed the way you receive your new attached documents from Angel Springs. Following feedback from our customers we've invested in upgrading our billing systems to make things a little easier for you.
Here's a few ways we've made it easier for you:
Your new documents are now attached to your email. You don't have to follow a link now to get to your documents.
Our customer portal has been upgraded to give you a clearer, simpler view of your documents and any outstanding invoices.
You can simply and easily raise any queries you may have through the customer portal.
Please note: you may wish to save your documents on initial viewing. However, after your first viewing you will be able to access copy documents by simply clicking the link.
If you would like to discuss or have any queries in relation to any of the documents then please do not hesitate to contact us on 0845 230 9555 and we will be more than happy to assist you. Please do not reply to this email.
To see Angel Springs latest special offer that will save you money and help support Make a Wish, please click on the attached document
With Kind Regards,
Angel Springs Ltd
TRAFFIC
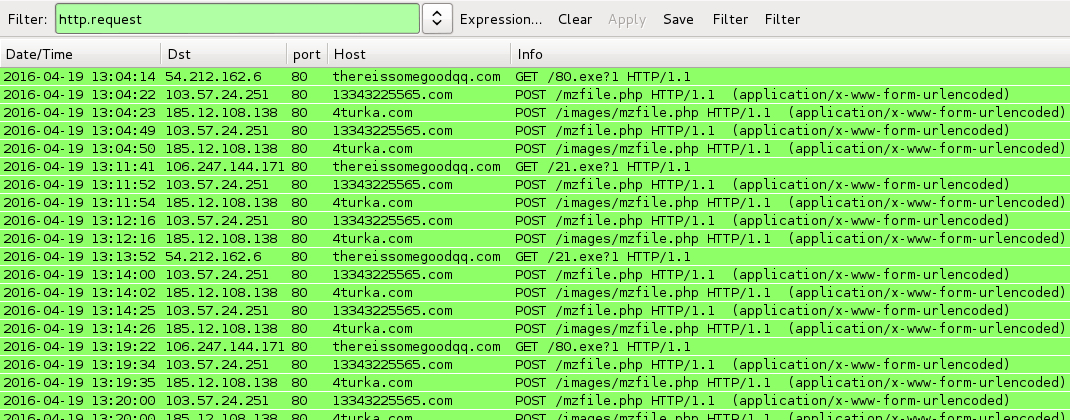
Shown above: Traffic from executing the extracted .js files, filtered in Wireshark.
.JS FILE DOWNLOADING THE TESLACRYPT RANSOMWARE .EXE FILE:
- 54.212.162[.]6 port 80 - thereissomegoodqq[.]com - GET /21.exe?1
- 54.212.162[.]6 port 80 - thereissomegoodqq[.]com - GET /80.exe?1
- 106.247.144[.]171 port 80 - thereissomegoodqq[.]com - GET /21.exe?1
- 106.247.144[.]171 port 80 - thereissomegoodqq[.]com - GET /80.exe?1
TESLACRYPT RANSOMWARE POST-INFECTION TRAFFIC:
- 103.57.24[.]251 port 80 - 13343225565[.]com - POST /mzfile.php
- 185.12.108[.]138 port 80 - 4turka[.]com - POST /images/mzfile.php
IMAGES
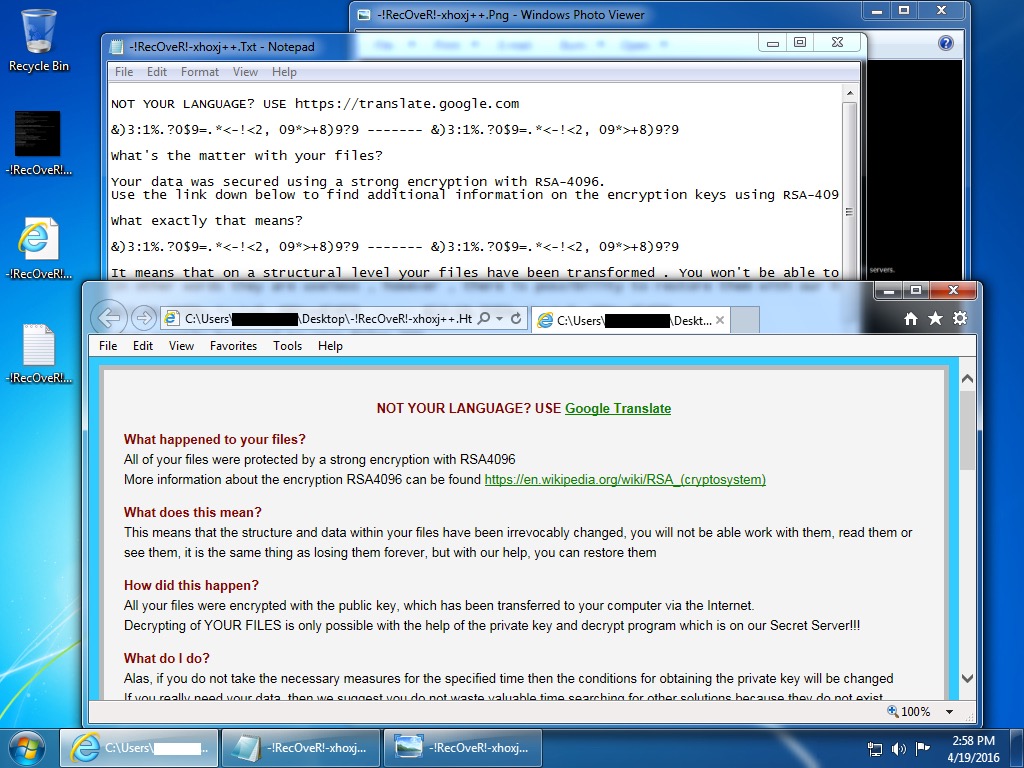
Shown above: Desktop of the Windows host after it was infected with the TeslaCrypt ransomware.
Click here to return to the main page.
