2016-04-20 - PSEUDO-DARKLEECH ANGLER EK SENDS BEDEP AND CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-20-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware-3-pcaps.zip 7.9 MB (7,923,862 bytes)
- 2016-04-19-psuedo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap (4,737,274 bytes)
- 2016-04-20-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware-first-run.pcap (184,838 bytes)
- 2016-04-20-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware-second-run.pcap (3,683,146 bytes)
- 2016-04-20-pseudo-Darkleech-Angler-EK-and-Bedep-and-CryptXXX-ransomware-files.zip 1.4 MB (1,389,962 bytes)
- 2016-04-19-page-from-amitandroy_com-with-injected-pseudo-Darkleech-script.txt (95,258 bytes)
- 2016-04-19-pseudo-Darkleech-Angler-EK-flash-exploit.swf (40,379 bytes)
- 2016-04-19-pseudo-Darkleech-Angler-EK-landing-page.txt (176,068 bytes)
- 2016-04-20-page-from-amitandroy_com-with-injected-pseudo-Darkleech-script-first-run.txt (95,092 bytes)
- 2016-04-20-page-from-amitandroy_com-with-injected-pseudo-Darkleech-script-second-run.txt (94,862 bytes)
- 2016-04-20-pseudo-Darkleech-Angler-EK-flash-exploit.swf (66,569 bytes)
- 2016-04-20-pseudo-Darkleech-Angler-EK-landing-page-first-run.txt (73,356 bytes)
- 2016-04-20-pseudo-Darkleech-Angler-EK-landing-page-second-run.txt (73,376 bytes)
- api-ms-win-system-localui-l1-1-0.dll (270,336 bytes) - CryptXXX ransomware from 2016-04-20
- api-ms-win-system-neth-l1-1-0.dll (266,240 bytes) - CryptXXX ransomware from 2016-04-19
- de_crypt_readme.bmp (232,6734 bytes) - CryptXXX ransomware decrypt instructions
- de_crypt_readme.html (3,315 bytes) - CryptXXX ransomware decrypt instructions
- de_crypt_readme.txt (1,638 bytes) - CryptXXX ransomware decrypt instructions
- mpr.dll (344,064 bytes) - Click-fraud malware from 2016-04-20
- shsetup.dll (343,040 bytes) - Click-fraud clickfraud malware from 2016-04-19
NOTES:
- I first saw Bedep and CryptXXX ransomware from the pseudo-Darkleech campaign on Monday 2016-04-18, but I didn't realize what the ransomware was.
- Earlier this week, Proofpoint posted a blog about CryptXXX ransomware and how Angler EK and Bedep are being used to spread it (link).
- This is pretty important, since I've seen a lot of Angler EK from the pseudo-Darkleech campaign (the actors behind Reveton, according to Proofpoint).
- I'm guessing we'll see a lot more CryptXXX ransomware, now that pseudo-Darkleech Angler EK is pushing Bedep/CryptXXX instead of TeslaCrypt ransomware.
- Background on the pseudo-Darkleech campaign can be found here.
TRAFFIC

Shown above: 2016-04-19 traffic filtered in Wireshark.

Shown above: 2016-04-20 traffic filtered in Wireshark -- First run.
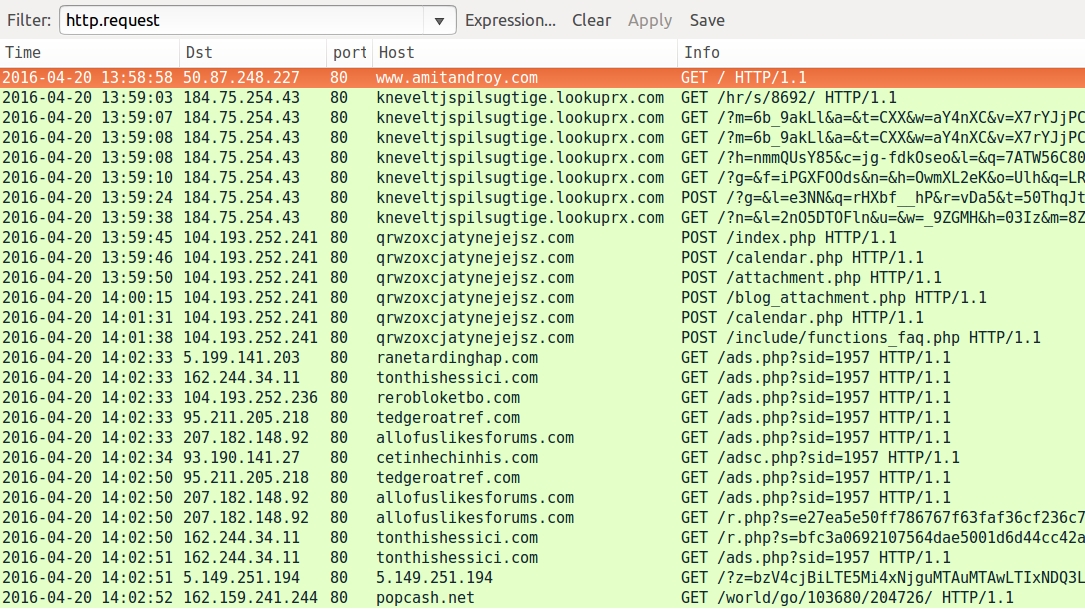
Shown above: 2016-04-20 traffic filtered in Wireshark -- Second run.
ASSOCIATED DOMAINS:
- 95.215.108[.]99 port 80 - kendevilbitchs-padhouvermo.addictionmeditation[.]com - Angler EK on 2016-04-19
- 209.126.123[.]86 port 80 - hiyosihcreation.thelatinshot[.]com - Angler EK on 2016-04-20 (first run)
- 184.75.254[.]43 port 80 - kneveltjspilsugtige.lookuprx[.]com - Angler EK on 2016-04-20 (second run)
- 104.193.252[.]241 port 80 - lwvcdohevypyxyja[.]com - Bedep post-infection on 2016-04-19
- 104.193.252[.]241 port 80 - qrwzoxcjatynejejsz[.]com - Bedep post-infection on 2016-04-20
- 162.244.32[.]123 port 80 - eiwtljjjzxiy7k[.]com - more Bedep post-infection on 2016-04-19
- 146.0.42[.]68 port 443 - CryptXXX ransomware post-infection traffic on 2016-04-19
- 217.23.6[.]40 port 443 - CryptXXX ransomware post-infection traffic on 2016-04-20
- 5.199.141[.]203 port 80 - ranetardinghap[.]com - Post-infection click-fraud (both days)
- 93.190.141[.]27 port 80 - cetinhechinhis[.]com - Post-infection click-fraud (both days)
- 95.211.205[.]218 port 80 - tedgeroatref[.]com - Post-infection click-fraud (both days)
- 162.244.34[.]11 port 80 - tonthishessici[.]com - Post-infection click-fraud (both days)
- 104.193.252[.]236 port 80 - rerobloketbo[.]com - Post-infection click-fraud (both days)
- 207.182.148[.]92 port 80 - allofuslikesforums[.]com - Post-infection click-fraud (both days)
IMAGES
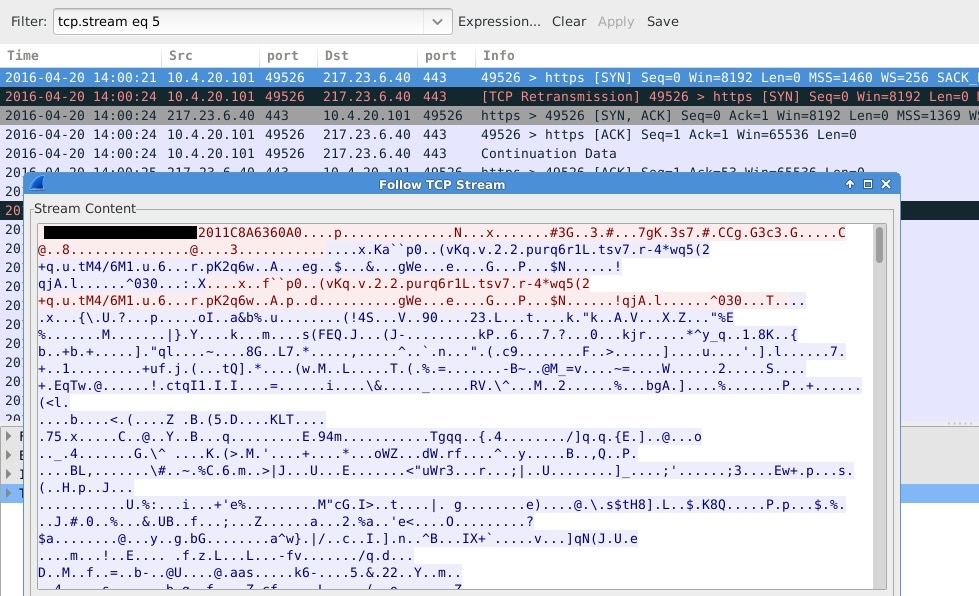
Shown above: An example of the CryptXXX ransomware post-infection traffic on 2016-04-20.
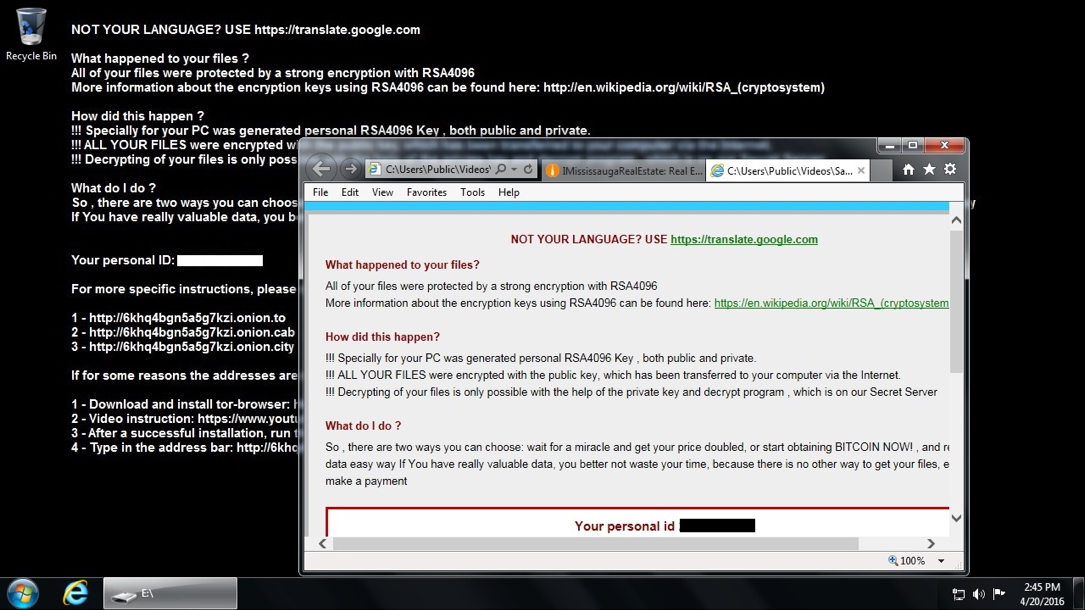
Shown above: Desktop of the infected host after the Angler EK/Bedep/CryptXXX infection on 2016-04-20.
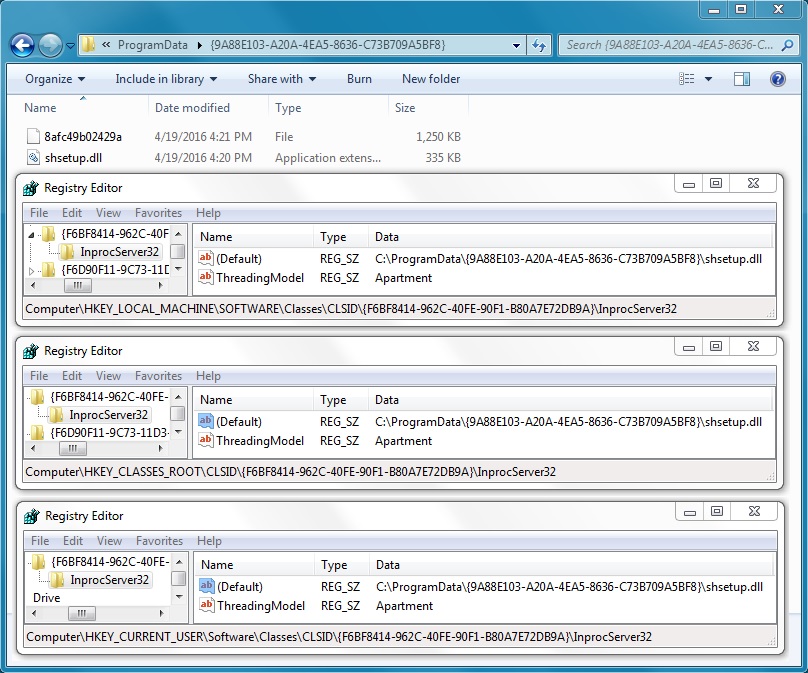
Shown above: Although the CryptXXX ransomwware deletes itself, the click-fraud malware stays resident on the system.
This is the click-fraud malware from 2016-04-19 and some associated registry entries.
Click here to return to the main page.
