2016-05-03 - LOCKY RANSOMWARE ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-03-Locky-ransomware-traffic-and-files.zip 2.5 MB (2,511,306 bytes)
NOTES:
The Palo Alto Networks Unit 42 blog about Locky ransomware can be found here.
Proofpoint's blog about Locky ransomware is available here.
Other posts also covering these same items of Locky ransomware emails from today include:
- https://blog.dynamoo.com/2016/05/malware-spam-third-reminder-outstanding.html
- https://blog.dynamoo.com/2016/05/malware-spam-you-are-fired-leads-to.html
EMAILS AND ATTACHMENTS
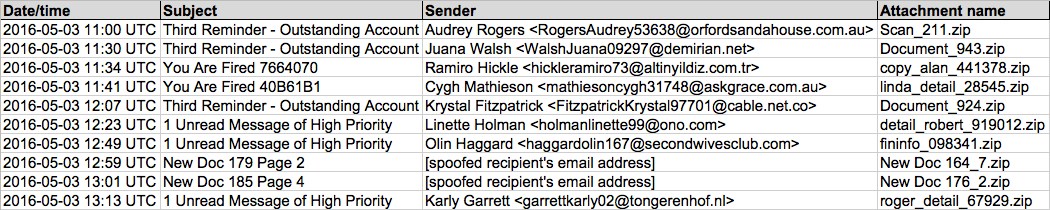
Shown above: Data from the .csv spreadsheet on 10 emails from today's Locky ransomware.
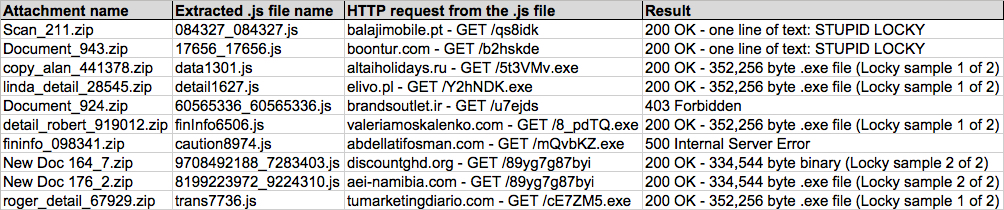
Shown above: Data from the .csv spreadsheet on 10 attachments from today's Locky ransomware.
TRAFFIC
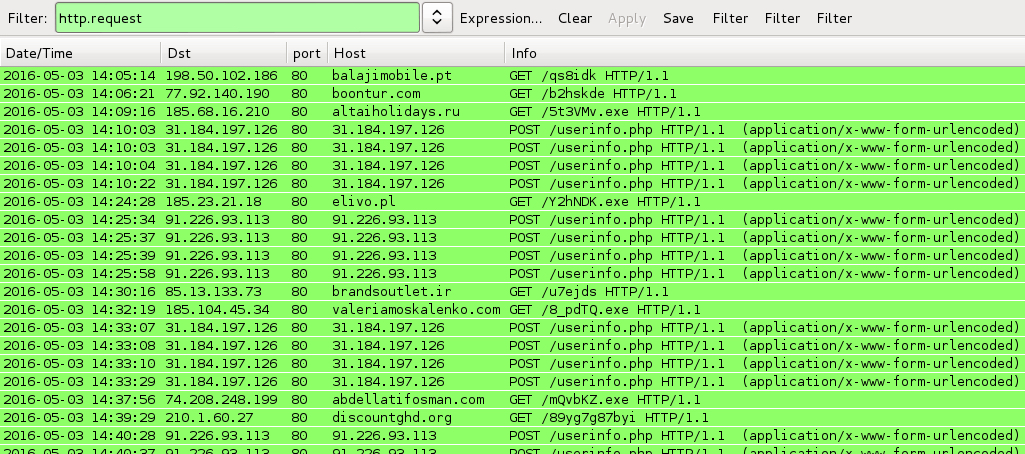
Shown above: Traffic from executing the extracted .js files, filtered in Wireshark.
HTTP REQUESTS FROM THE EXTRACTED .JS FILES:
- 198.50.102[.]186 port 80 - balajimobile[.]pt - GET /qs8idk
- 77.92.140[.]190 port 80 - boontur[.]com - GET /b2hskde
- 185.68.16[.]210 port 80 - altaiholidays[.]ru - GET /5t3VMv.exe
- 185.23.21[.]18 port 80 - elivo[.]pl - GET /Y2hNDK.exe
- 85.13.133[.]73 port 80 - brandsoutlet[.]ir - GET /u7ejds
- 185.104.45[.]34 port 80 - valeriamoskalenko[.]com - GET /8_pdTQ.exe
- 74.208.248[.]199 port 80 - abdellatifosman[.]com - GET /mQvbKZ.exe
- 210.1.60[.]27 port 80 - discountghd[.]org - GET /89yg7g87byi
- 72.52.179[.]2 port 80 - aei-namibia[.]com - GET /89yg7g87byi
- 65.60.47[.]53 port 80 - tumarketingdiario[.]com - GET /cE7ZM5.exe
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLES:
- 31.184.197[.]126 port 80 - 31.184.197[.]126 - POST /userinfo.php
- 91.226.93[.]113 port 80 - 91.226.93[.]113 - POST /userinfo.php
IMAGES
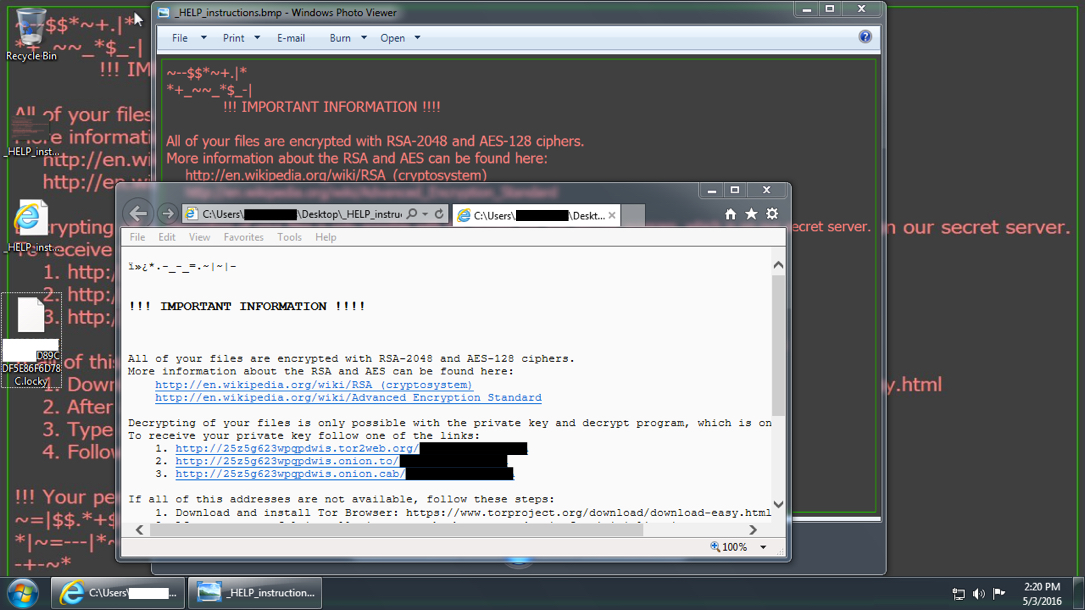
Shown above: Desktop of a Windows host after executing one of the .js attachments from the malspam.
ZIP ARCHIVE CONTENTS
- 2016-05-03-Locky-ransomware-email-tracker.csv (2,238 bytes)
- 2016-05-03-Locky-ransomware-traffic.pcap (2,152,408 bytes)
- attachments/Document_924.zip (75,017 bytes)
- attachments/Document_943.zip (76,062 bytes)
- attachments/New Doc 164_7.zip (5,405 bytes)
- attachments/New Doc 176_2.zip (5,384 bytes)
- attachments/Scan_211.zip (75,082 bytes)
- attachments/copy_alan_441378.zip (5,298 bytes)
- attachments/detail_robert_919012.zip (5,144 bytes)
- attachments/fininfo_098341.zip (4,918 bytes)
- attachments/linda_detail_28545.zip (4,718 bytes)
- attachments/roger_detail_67929.zip (4,995 bytes)
- extracted-files/084327_084327.js (234,965 bytes)
- extracted-files/17656_17656.js (238,237 bytes)
- extracted-files/60565336_60565336.js (234,526 bytes)
- extracted-files/8199223972_9224310.js (12,851 bytes)
- extracted-files/9708492188_7283403.js (12,850 bytes)
- extracted-files/caution8974.js (9,004 bytes)
- extracted-files/data1301.js (9,481 bytes)
- extracted-files/detail1627.js (8,282 bytes)
- extracted-files/finInfo6506.js (9,327 bytes)
- extracted-files/trans7736.js (9,336 bytes)
- malspam/2016-05-03-1100-UTC.eml (103,446 bytes)
- malspam/2016-05-03-1130-UTC.eml (104,686 bytes)
- malspam/2016-05-03-1134-UTC.eml (8,943 bytes)
- malspam/2016-05-03-1141-UTC.eml (8,164 bytes)
- malspam/2016-05-03-1207-UTC.eml (103,330 bytes)
- malspam/2016-05-03-1223-UTC.eml (8,663 bytes)
- malspam/2016-05-03-1249-UTC.eml (8,368 bytes)
- malspam/2016-05-03-1259-UTC.eml (8,334 bytes)
- malspam/2016-05-03-1301-UTC.eml (8,303 bytes)
- malspam/2016-05-03-1313-UTC.eml (8,445 bytes)
- malware-from-the-infected-host/2016-05-03-Locky-ransomware-sample-1-of-2.exe (352,256 bytes)
- malware-from-the-infected-host/2016-05-03-Locky-ransomware-sample-2-of-2.exe (334,544 bytes)
- malware-from-the-infected-host/2016-05-03-Locky-ransomware_HELP_instructions.bmp (3,864,030 bytes)
- malware-from-the-infected-host/2016-05-03-Locky-ransomware_HELP_instructions.html (1,968 bytes)
Click here to return to the main page.
