2016-05-06 - RIG EK FROM 46.30.46[.]38 SENDS TOFSEE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-06-Rig-EK-sends-Tofsee.pcap.zip 147.6 kB (147,590 bytes)
- 2016-05-06-Rig-EK-sends-Tofsee.pcap (322,674 bytes)
- 2016-05-06-Rig-EK-and-Tofsee-files.zip 483.4 kB (483,389 bytes)
- 2016-05-06-Rig-EK-flash-exploit.swf (38,826 bytes)
- 2016-05-06-Rig-EK-landing-page.txt (4,829 bytes)
- 2016-05-06-Rig-EK-payload-tofsee.exe (217,088 bytes)
- 2016-05-06-tofsee-dropped-malware.exe (49,344,512 bytes)
NOTES:
- Post-infection activity matches what I've seen before for Tofsee.
- Other examples I've documented on this same campaign are:
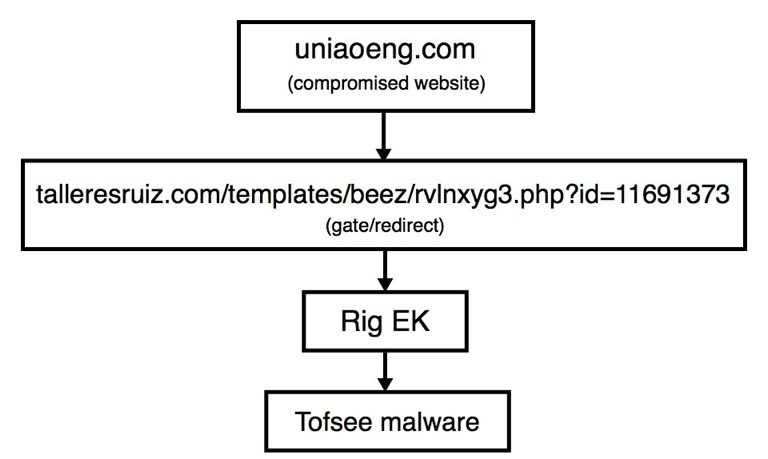
Shown above: Flow of events for today's infection.
TRAFFIC
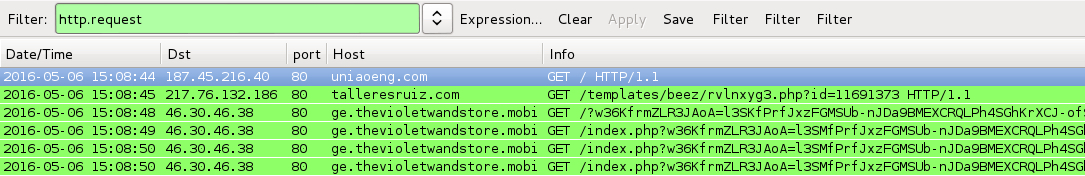
Shown above: Pcap of the pseudo-Darkleech example filtered in Wireshark.
ASSOCIATED DOMAINS
- 217.76.132[.]186 port 80 - talleresruiz[.]com - gate/redirect
- 46.30.46[.]38 port 80 - ge.thevioletwandstore[.]mobi - Rig EK
- 111.121.193[.]242 port 443 - Post-infection encrypted Tofsee traffic
- 113.163.97[.]192 port 5818 - Post-infection encrypted Tofsee traffic
- Attempts to connect to various mail servers
IMAGES
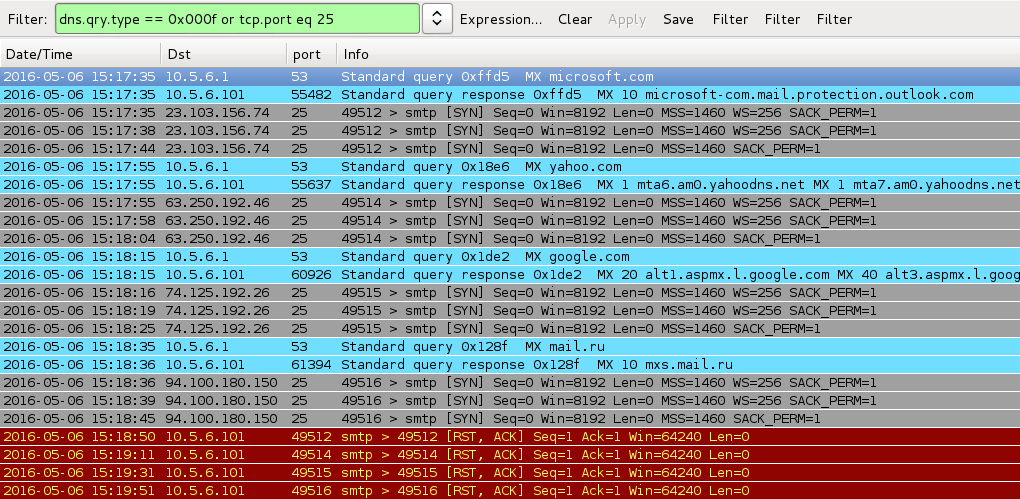
Shown above: Filtering in Wireshark to show the attempted SMTP traffic: dns.qry.type == 0x000f or tcp.port eq 25.

Shown above: Filtering in Wireshark to check for post-infection callback: !(tcp.port eq 80) and !(tcp.port eq 25) and tcp.flags eq 0x0002
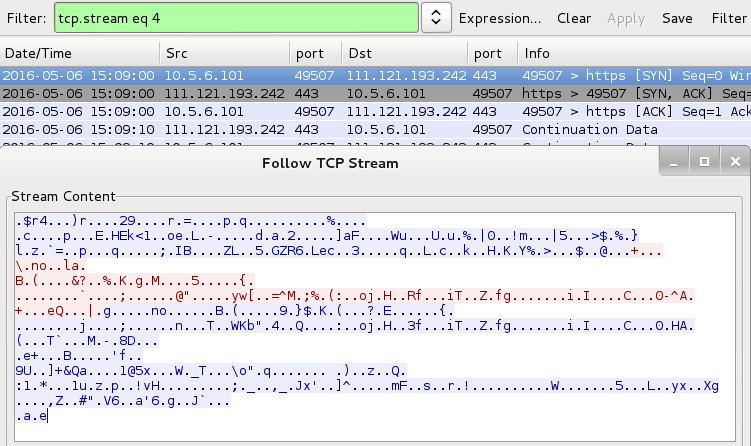
Shown above: Tofsee post-infection traffic on 111.121.193[.]242 over TCP port 443.
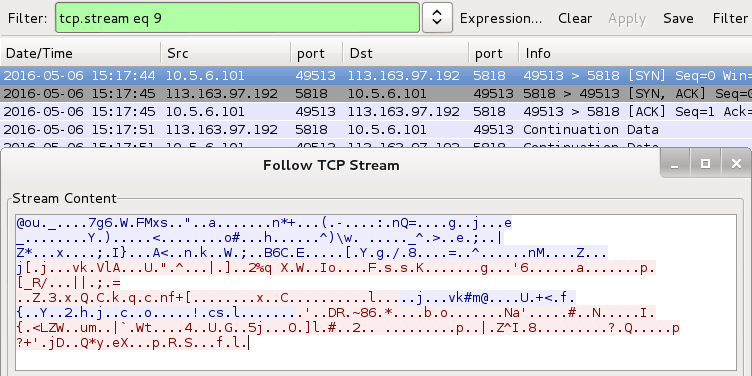
Shown above: Tofsee post-infection traffic on 113.163.97.192 over TCP port 5818.
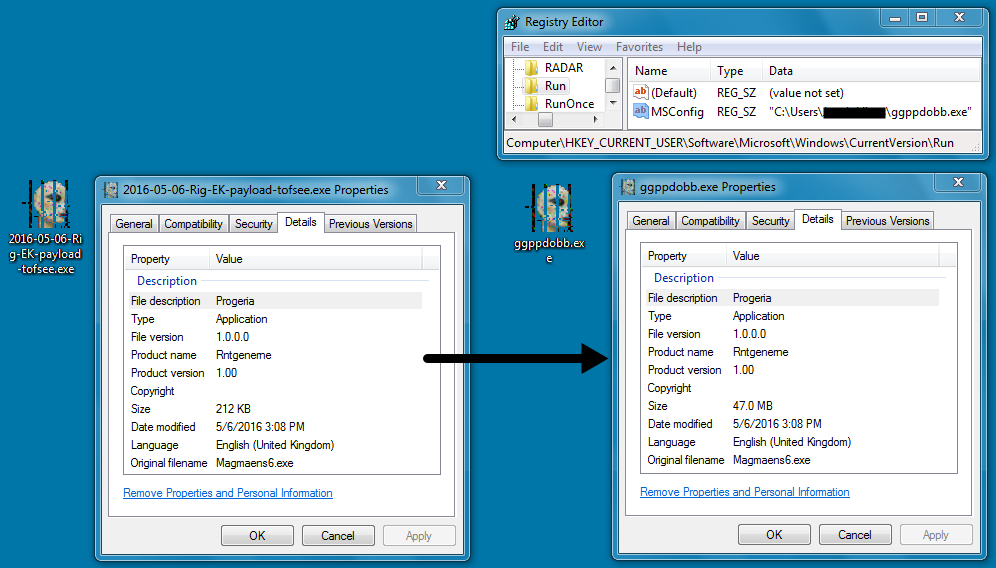
Shown above: Malware dropped by the Rig EK Tofsee payload.
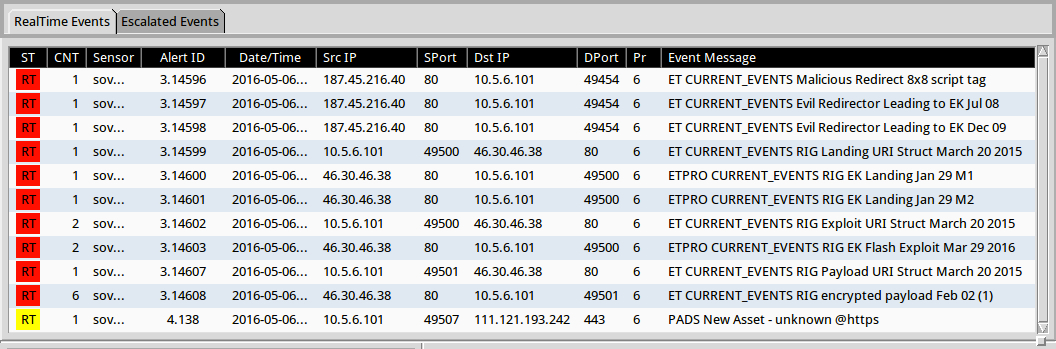
Shown above: Checking the ET Pro ruleset on SecurityOnion using Suricata.
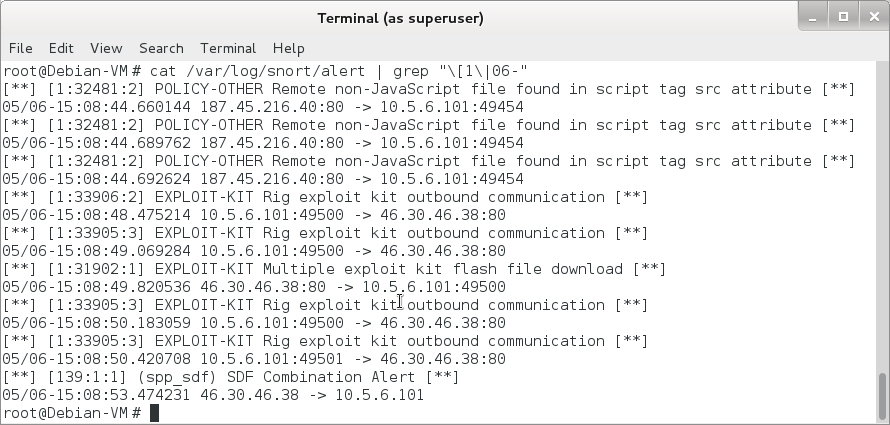
Shown above: Checking the Talos subscriber ruleset using Snort.
Click here to return to the main page.