2016-05-10 - TUESDAY MALWARE HUNT - CERBER RANSOMWARE, LOCKY RANSOMWARE, AND MALWARE FROM BRAZIL EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILE:
- 2016-05-10-malware-data.zip 7.3 MB (7,292,443 bytes)
EMAILS AND ATTACHMENTS
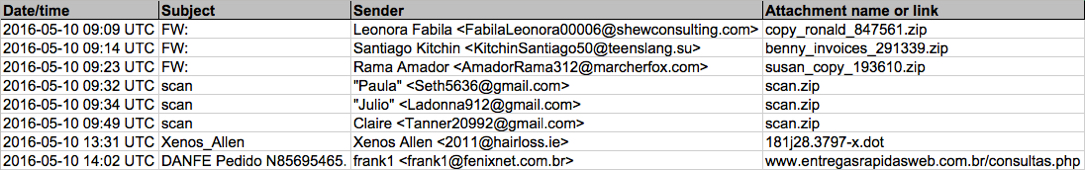
Shown above: Data from the .csv spreadsheet on 8 malicious emails from today.
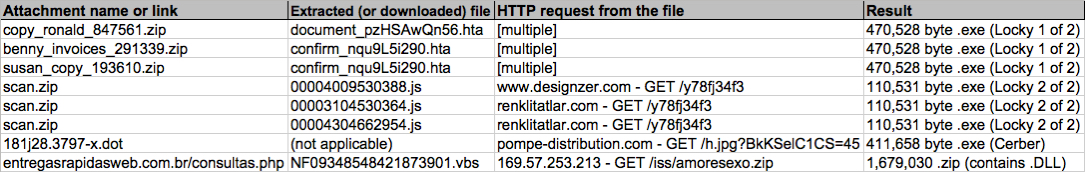
Shown above: Data from the .csv spreadsheet on 8 attachments from today's emails.
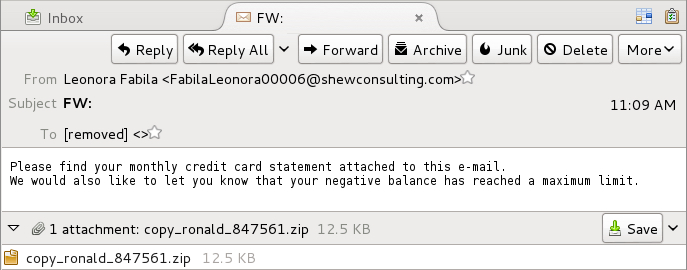
Shown above: Email pushing Locky ransomware example 1 of 2.
Shown above: Email pushing Locky ransomware example 2 of 2.
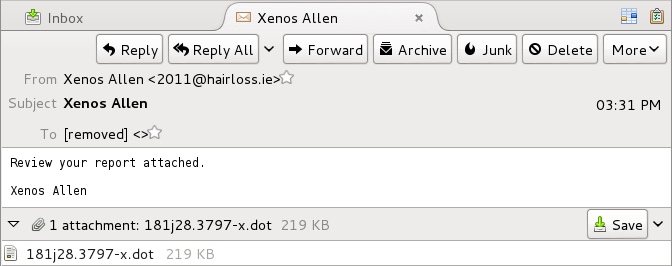
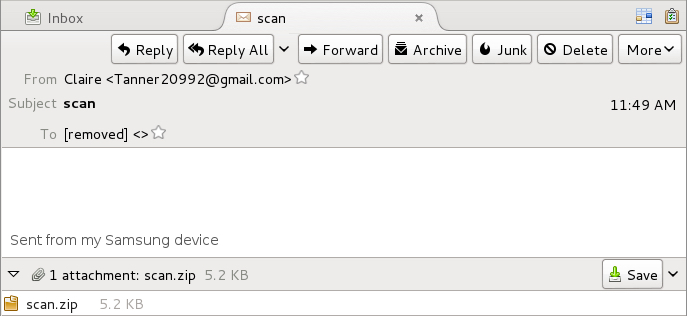
Shown above: Email pushing Cerber ransomware example.
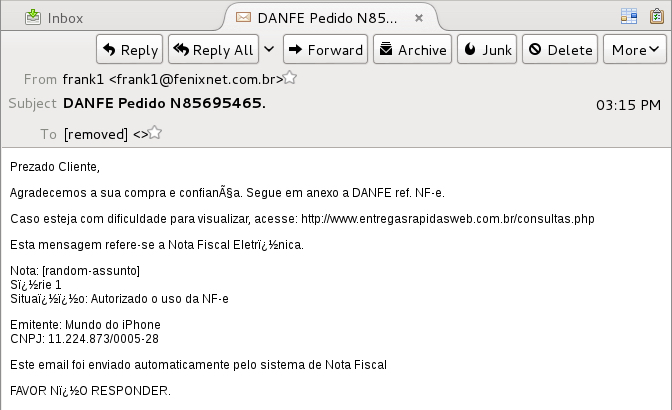
Shown above: Brazil email example.
TRAFFIC
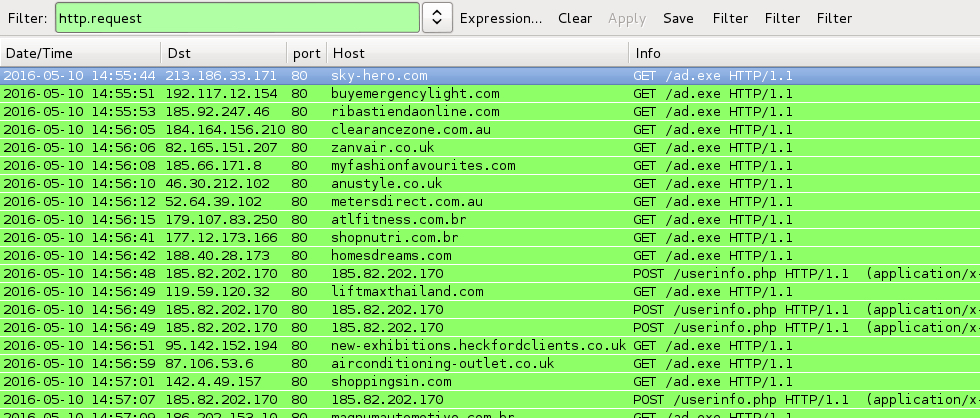
Shown above: Traffic from executing one of the extracted .hta files, filtered in Wireshark.
ASSOCIATED DOMAINS:
HTTP REQUESTS FOR LOCKY RANSOMWARE FROM ONE OF THE .HTA FILES:
- 87.106.53[.]6 port 80 - airconditioning-outlet[.]co[.]uk - GET /ad.exe
- 46.30.212[.]102 port 80 - anustyle[.]co[.]uk - GET /ad.exe
- 179.107.83[.]250 port 80 - atlfitness[.]com[.]br - GET /ad.exe
- 160.153.33[.]104 port 80 - aw-store[.]com - GET /ad.exe
- 54.241.22[.]111 port 80 - bedbugsurvivalguide[.]com - GET /ad.exe
- 139.162.58[.]95 port 80 - bellenuits[.]com - GET /ad.exe
- 192.117.12[.]154 port 80 - buyemergencylight[.]com - GET /ad.exe
- 52.6.107[.]10 port 80 - casarenodirect[.]com - GET /ad.exe
- 200.98.197[.]36 port 80 - cenasuniformes[.]com[.]br - GET /ad.exe
- 184.164.156[.]210 port 80 - clearancezone[.]com[.]au - GET /ad.exe
- 52.65.92[.]194 port 80 - coating-supplies[.]com[.]au - GET /ad.exe
- 103.16.128[.]166 port 80 - davidjubermann[.]com - GET /ad.exe
- 50.62.168[.]5 port 80 - demarcojewels[.]com - GET /ad.exe
- 192.249.113[.]43 port 80 - elitesup[.]com - GET /ad.exe
- 66.147.244[.]66 port 80 - fashionpoppers[.]com - GET /ad.exe
- 50.63.119[.]14 port 80 - getdattee[.]com - GET /ad.exe
- 103.38.10[.]109 port 80 - gmdengineering[.]com[.]au - GET /ad.exe
- 188.40.28[.]173 port 80 - homesdreams[.]com - GET /ad.exe
- 192.249.113[.]43 port 80 - lcdistributing[.]com - GET /ad.exe
- 69.162.104[.]130 port 80 - lcdonline[.]com[.]br - GET /ad.exe
- 119.59.120[.]32 port 80 - liftmaxthailand[.]com - GET /ad.exe
- 23.229.242[.]166 port 80 - lyintl[.]com - GET /ad.exe
- 186.202.153[.]10 port 80 - magnumautomotivo[.]com[.]br - GET /ad.exe
- 50.62.227[.]32 port 80 - mailboxesflorida[.]com - GET /ad.exe
- 23.235.196[.]128 port 80 - melodyderm[.]com - GET /ad.exe
- 186.202.153[.]108 port 80 - merlindistribuidora[.]com[.]br - GET /ad.exe
- 52.64.39[.]102 port 80 - metersdirect[.]com[.]au - GET /ad.exe
- 162.213.193[.]150 port 80 - mikronjoalheria[.]com[.]br - GET /ad.exe
- 23.235.220[.]84 port 80 - millersportsaspen[.]com - GET /ad.exe
- 109.228.9[.]247 port 80 - mosaicworld[.]co[.]uk - GET /ad.exe
- 185.66.171[.]8 port 80 - myfashionfavourites[.]com - GET /ad.exe
- 95.142.152[.]194 port 80 - new-exhibitions.heckfordclients[.]co[.]uk - GET /ad.exe
- 67.20.76[.]133 port 80 - outletsmarcas[.]com - GET /ad.exe
- 160.153.50[.]192 port 80 - pgkdistribution[.]co[.]uk - GET /ad.exe
- 192.186.229[.]215 port 80 - pittora[.]com - GET /ad.exe
- 185.92.247[.]46 port 80 - ribastiendaonline[.]com - GET /ad.exe
- 67.20.84[.]126 port 80 - seatsshop[.]com - GET /ad.exe
- 74.220.207[.]142 port 80 - shoesmackers[.]com - GET /ad.exe
- 177.12.173[.]166 port 80 - shopnutri[.]com[.]br - GET /ad.exe
- 142.4.49[.]157 port 80 - shoppingsin[.]com - GET /ad.exe
- 213.186.33[.]171 port 80 - sky-hero[.]com - GET /ad.exe
- 67.231.106[.]60 port 80 - store.pinkupcape[.]com - GET /ad.exe
- 186.202.126[.]233 port 80 - videale[.]com[.]br - GET /ad.exe
- 136.243.204[.]62 port 80 - vizyt-shop[.]com - GET /ad.exe
- 177.12.173[.]214 port 80 - volparts[.]com[.]br - GET /ad.exe
- 166.62.10[.]30 port 80 - warehousestudiochicago[.]com - GET /ad.exe
- 46.166.163[.]195 port 80 - wholesalejaipurkurti[.]com - GET /ad.exe
- 82.165.151[.]207 port 80 - zanvair[.]co[.]uk - GET /ad.exe
HTTP REQUESTS FOR LOCKY RANSOMWARE FROM THE .JS FILES:
- 46.235.10[.]71 port 80 - renklitatlar[.]com - GET /y78fj34f3
- 108.174.196[.]88 port 80 - www.designzer[.]com - GET /y78fj34f3
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE INFECTIONS:
- 185.82.202[.]170 port 80 - 185.82.202[.]170 - POST /userinfo.php
HTTP REQUEST FOR CERBER RANSOMWARE FROM THE .DOT FILE:
- 188.165.242[.]106 port 80 - pompe-distribution[.]com - GET /h.jpg?BkKSelC1CS=45
HTTP REQUESTS FROM THE BRAZIL EMAIL:
- 52.39.113[.]52 port 80 - www.entregasrapidasweb[.]com[.]br - GET /consultas.php [link from the email]
- 169.57.253[.]213 port 80 - 169.57.253[.]213 - GET /iss/amoresexo.zip [caused by executing the downloaded .js file]
ZIP ARCHIVE CONTENTS
- 2016-05-10-Cerber-ransomware-traffic.pcap (440,078 bytes)
- 2016-05-10-Locky-ransomware-traffic-1-of-2.pcap (7,341,712 bytes)
- 2016-05-10-Locky-ransomware-traffic-2-of-2.pcap (225,956 bytes)
- 2016-05-10-email-tracker.csv (1,603 bytes)
- 2016-05-10-infection-traffic-from-Portuguese-malspam.pcap (1,704,304 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Cerber-ransomware-sample.exe (411,648 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Cerber-ransomware_# DECRYPT MY FILES #.html (12,579 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Cerber-ransomware_# DECRYPT MY FILES #.txt (11,247 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Cerber-ransomware_# DECRYPT MY FILES #.vbs (204 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Locky-ransomware-sample-1-of-2.exe (470,528 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Locky-ransomware-sample-2-of-3.exe (110,531 bytes)
- artifacts-from-infected-hosts / 2016-05-10-Locky-ransomware.bmp (3,436,338 bytes)
- artifacts-from-infected-hosts / 2016-05-10-LLocky-ransomware_HELP_instructions.html (1,780 bytes)
- artifacts-from-infected-hosts / 2016-05-10-boleto-malspam-artifact-from-infected-host.dll (324,608 bytes)
- attachments / 181j28.3797-x.dot (224,085 bytes)
- attachments / benny_invoices_291339.zip (12,893 bytes)
- attachments / copy_ronald_847561.zip (12,831 bytes)
- attachments / scan-1-of-3.zip (5,341 bytes)
- attachments / scan-2-of-3.zip (5,390 bytes)
- attachments / scan-3-of-3.zip (5,342 bytes)
- attachments / susan_copy_193610.zip (12,893 bytes)
- extracted-or-downloaded-files / 00003104530364.js (15,237 bytes)
- extracted-or-downloaded-files / 00004009530388.js (15,178 bytes)
- extracted-or-downloaded-files / 00004304662954.js (15,169 bytes)
- extracted-or-downloaded-files / NF09348548421873901.vbs (10,452 bytes)
- extracted-or-downloaded-files / confirm_nqu9L5i290.hta (24,625 bytes)
- extracted-or-downloaded-files / document_pzHSAwQn56.hta (24,602 bytes)
- emails / 2016-05-10-0909-UTC.eml (19,195 bytes)
- emails / 2016-05-10-0914-UTC.eml (19,287 bytes)
- emails / 2016-05-10-0923-UTC.eml (19,295 bytes)
- emails / 2016-05-10-0932-UTC.eml (8,682 bytes)
- emails / 2016-05-10-0934-UTC.eml (8,743 bytes)
- emails / 2016-05-10-0949-UTC.eml (8,719 bytes)
- emails / 2016-05-10-1331-UTC.eml (304,048 bytes)
- emails / 2016-05-10-1402-UTC.eml (1,475 bytes)
Click here to return to the main page.
