2016-05-11 - ANGLER EK: TWO CAMPAIGNS, FOUR PCAPS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-11-Angler-EK-two-campaigns-four-pcaps.zip 7.4 MB (7,444,237 bytes)
- 2016-05-10-EITest-Angler-EK-sends-Panda-banker.pcap (1,577,060 bytes)
- 2016-05-10-pseudoDarkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap (3,935,424 bytes)
- 2016-05-11-EITest-Angler-EK-sends-Panda-banker.pcap (1,330,338 bytes)
- 2016-05-11-pseudoDarkleech-Angler-EK-sends-CryptXXX-ransomware.pcap (1,218,541 bytes)
- 2016-05-11-Angler-EK-two-campaigns-four-infections-malware-and-artifacts.zip 2.2 MB (2,178,471 bytes)
- 2016-05-10-CryptXXX-ransomware-decrypt-instructions.bmp (2,023,254 bytes)
- 2016-05-10-CryptXXX-ransomware-decrypt-instructions.html (14,190 bytes)
- 2016-05-10-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-05-10-CryptXXX-ransomware.dll (303,104 bytes)
- 2016-05-10-EITest-Angler-EK-flash-exploit.swf (54,442 bytes)
- 2016-05-10-EITest-Angler-EK-landing-page.txt (67,896 bytes)
- 2016-05-10-EITest-Angler-EK-payload-panda-banker.exe (527,872 bytes)
- 2016-05-10-EITest-Angler-EK-silverlight-exploit.zip (169,132 bytes)
- 2016-05-10-EITest-flash-redirector-from-nzersef_tk.swf (15,495 bytes)
- 2016-05-10-click-fraud-malware.dll (908,448 bytes)
- 2016-05-10-pseudo-Darkleech-Angler-EK-flash-exploit.swf (66,910 bytes)
- 2016-05-10-pseudo-Darkleech-Angler-EK-landing-page.txt (67,918 bytes)
- 2016-05-11-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-11-CryptXXX-ransomware-decrypt-instructions.html (14,190 bytes)
- 2016-05-11-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-05-11-CryptXXX-ransomware.dll (243,200 bytes)
- 2016-05-11-EITest-Angler-EK-flash-exploit.swf (54,448 bytes)
- 2016-05-11-EITest-Angler-EK-landing-page.txt (67,852 bytes)
- 2016-05-11-EITest-Angler-EK-payload-panda-banker.exe (451,072 bytes)
- 2016-05-11-EITest-Angler-EK-silverlight-exploit.zip (169,132 bytes)
- 2016-05-11-EITest-flash-redirector-from-kogojo_tk.swf (15,495 bytes)
- 2016-05-11-pseudo-Darkleech-Angler-EK-flash-exploit.swf (66,914 bytes)
- 2016-05-11-pseudo-Darkleech-Angler-EK-landing-page.txt (67,934 bytes)
BACKGROUND:
- Background on the IETest campaign is available here.
- Background on the pseudo-Darkleech campaign is available here.
- Proofpoint's blog on Angler EK spreading CryptXXX can be found here.
- An ISC diary I wrote about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections is located here.
CRYPTXXX RANSOMWARE NOTES:
- Earlier today, Kafeine saw Neutrino EK drop CryptXXX ransomware as a payload ( link ). It's the first time I've seen CryptXXX from anything other than Angler EK.
- And today, I saw pseudo-Darkleech Angler EK switch just send CryptXXX ransomware. Before today, it was always Angler EK --> Bedep --> CryptXXX ransomware.
- Here's the change in artifacts from pseudo-Darkleech Angler EK for today compared to yesterday:
2016-05-10 (YESTERDAY) ANGLER EK --> BEDEP --> CRYPTXXX RANSOMWARE:
- C:\Users\[username]\AppData\Local\Temp\{602851EB-C432-4D0E-96F9-61DC616687E8}\api-ms-win-system-shsetup-l1-1-0.dll [CryptXXX]
- C:\Users\[username]\AppData\Local\Temp\{602851EB-C432-4D0E-96F9-61DC616687E8}\svchost.exe [runDLL32.exe]
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\vfnws.dll [click-fraud malware]
2016-05-11 (TODAY) ANGLER EK --> CRYPTXXX RANSOMWARE (NO BEDEP):
- C:\Users\[username]\AppData\Local\Temp\2CE.tmp.dll [CryptXXX]
- C:\Users\[username]\AppData\Local\Temp\svchost.exe [runDLL32.exe]
- In a previous post, I said svchost.exe is actually rundll32.exe (a legitimate file) dropped in the same folder as CryptXXX. It's used to run the CryptXXX ransomware DLL.
- In today's CryptXXX ransomware infection, the screen locked and stayed that way, so I had to reboot the infected host. The last line of the lock screen cycled through several colors.
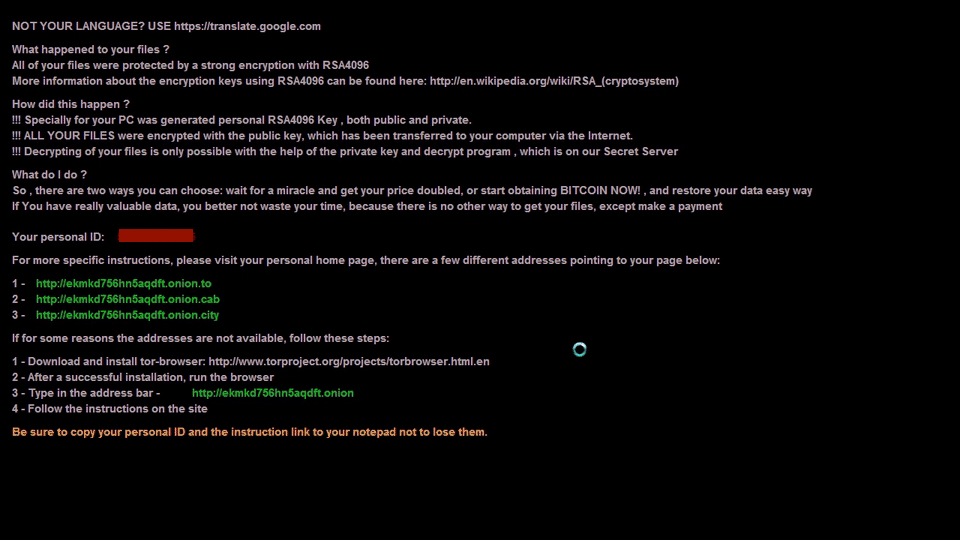
Shown above: There was a lock screen preventing me from accessing the desktop on the infected Windows host.
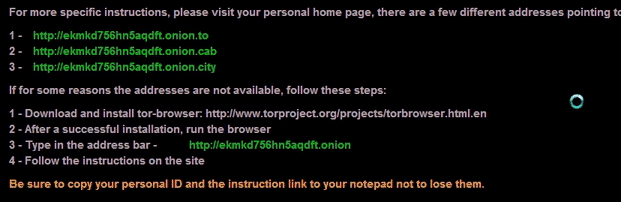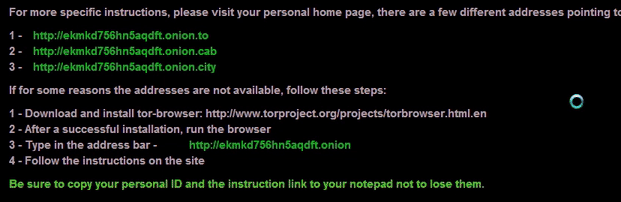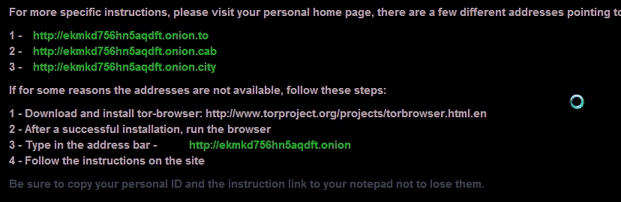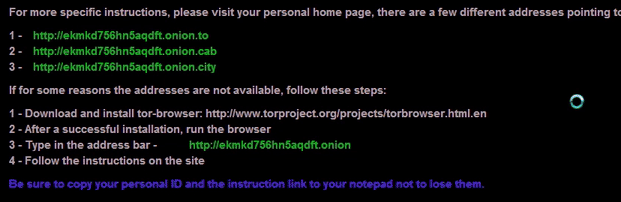
Shown above: Animated gif showing the last line cycling through different colors.
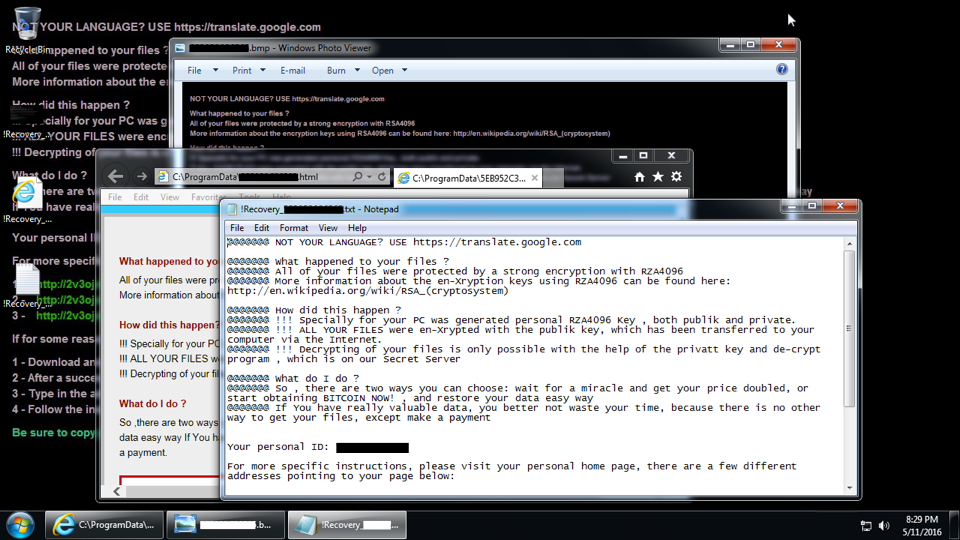
Shown above: The infected Windows host after I rebooted it.
PSEUDO-DARKLEECH TRAFFIC
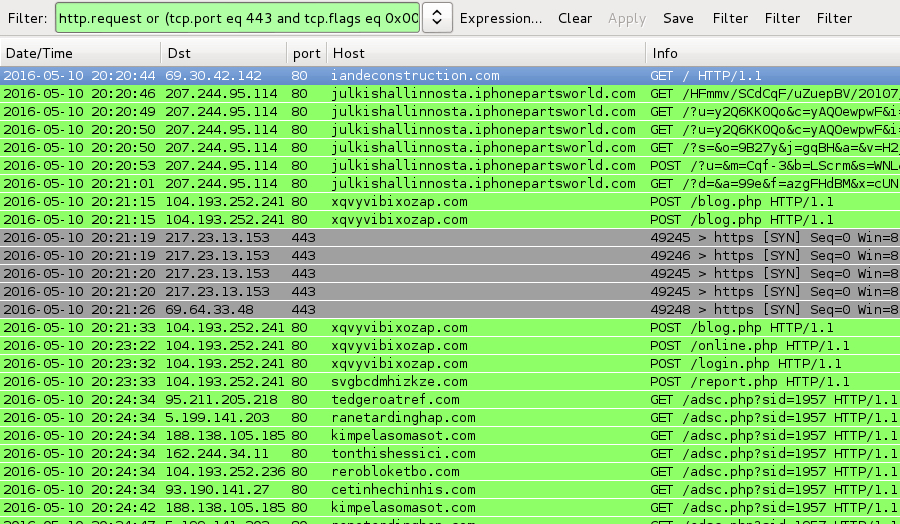
Shown above: Pcap of the traffic from Tuesday 2016-05-10 filtered in Wireshark. http.request or (tcp.port eq 443 and tcp.flags eq 0x0002)
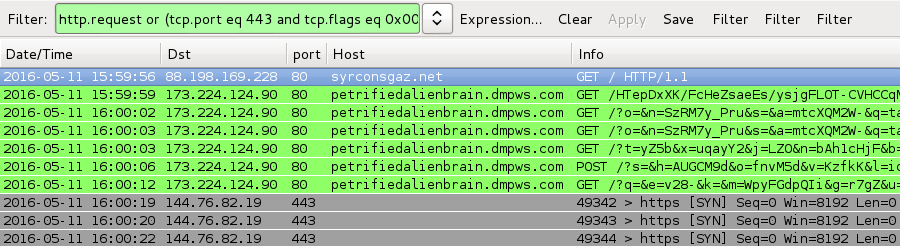
Shown above: Pcap of the traffic from Wednesday 2016-05-11 filtered in Wireshark. http.request or (tcp.port eq 443 and tcp.flags eq 0x0002)
SOME OF THE ASSOCIATED DOMAINS:
- 207.244.95[.]114 port 80 - julkishallinnosta.iphonepartsworld[.]com - Angler EK
- 217.23.13[.]153 port 443 - CryptXXX ransomware callback traffic (custom encoded) on 2016-05-10
- 69.64.33[.]48 port 443 - CryptXXX ransomware callback traffic (custom encoded) on 2016-05-10
- 173.224.124[.]90 port 80 - petrifiedalienbrain.dmpws[.]com - Angler EK
- 144.76.82[.]19 port 443 - CryptXXX ransomware callback traffic (custom encoded) on 2016-05-11
NOTES FOR THE EITEST ANGLER EK
The EITest Angler EK traffic sent Panda Banker malware. Characteristics of the malware from both days are similar, and I saw EmergingThreats events for Panda Banker caused by this malware.
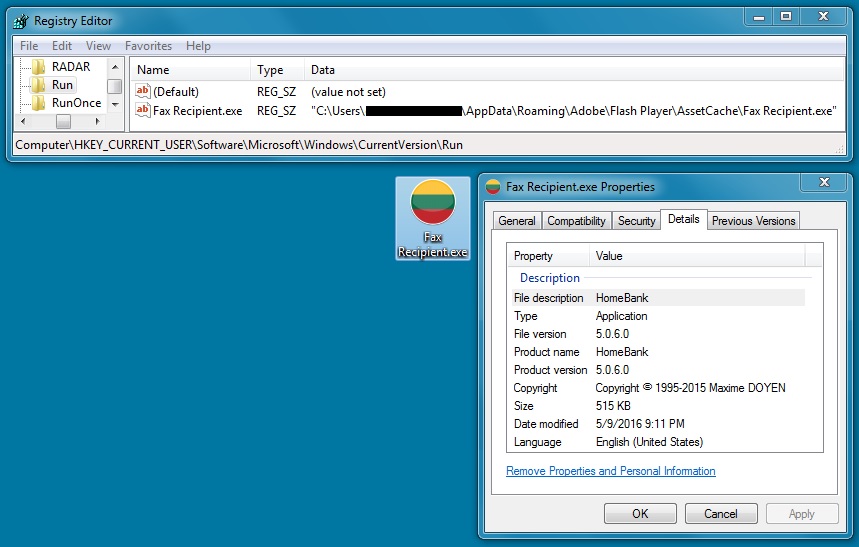
Shown above: Malware from the Tuesday 2016-05-10 EITest Angler EK infection.
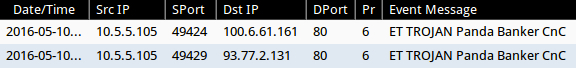
Shown above: Some post-infection alerts after the 2016-05-10 EITest Angler EK.
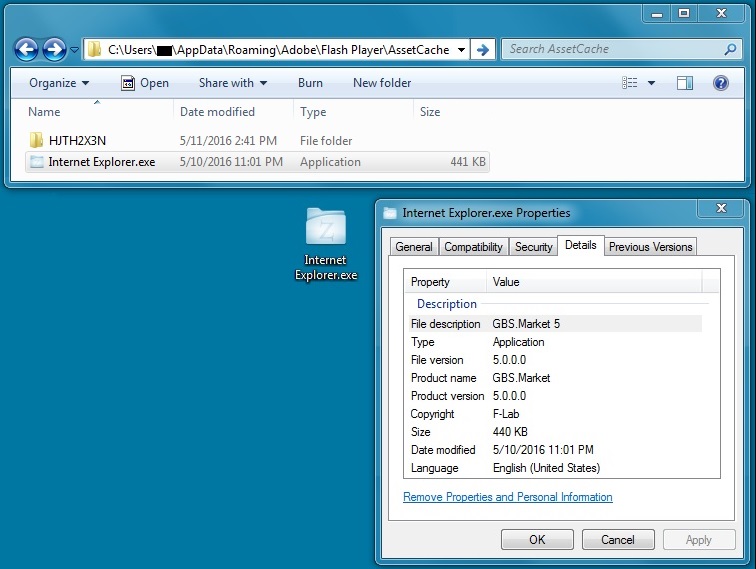
Shown above: Malware from the Wednesday 2016-05-11 EITest Angler EK infection.
Click here to return to the main page.
