2016-05-18 - PSEUDO-DARKLEECH ANGLER EK FROM 188.138.70[.]181 SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-18-pseudo-Darkleech-Angler-EK-sends-CryptXXX-ransomware.pcap.zip 1.1 MB (1,108,949 bytes)
- 2016-05-18-pseudo-Darkleech-Angler-EK-sends-CryptXXX-ransomware.pcap (1,266,617 bytes)
- 2016-05-18-pseudo-Darkleech-Angler-EK-and-CryptXXX-ransomware-files.zip 333.9 kB (333,906 bytes)
- 2016-05-18-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-18-CryptXXX-ransomware-decrypt-instructions.html (14,190 bytes)
- 2016-05-18-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-05-18-CryptXXX-ransomware.dll (303,104 bytes)
- 2016-05-18-page-from-hooked-on-nails_com-with-injected-pseudo-Darkleech-script.txt (30,069 bytes)
- 2016-05-18-pseudo-Darkleech-Angler-EK-flash-exploit.swf (66,879 bytes)
- 2016-05-18-pseudo-Darkleech-Angler-EK-landing-page.txt (171,358 bytes)
NOTES:
- Background on the pseudo-Darkleech campaign is available here.
- Proofpoint's blog on Angler EK spreading CryptXXX can be found here.
- An ISC diary I wrote about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections is located here.
- A follow-up from Proofpoint about CryptXXX is here
- Thanks to @BiebsMalwareGuy for the original tweet on this.
Shown above: Tweet near the end of April 2016 about today's compromised website.
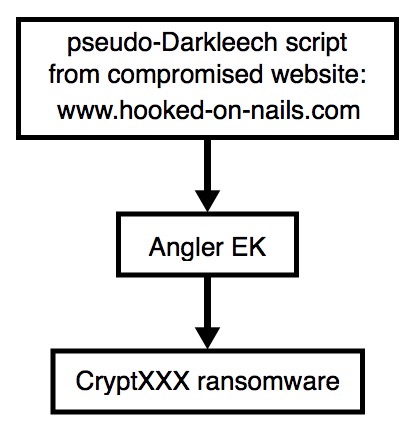
Shown above: Chain of events for today's infection.
TRAFFIC
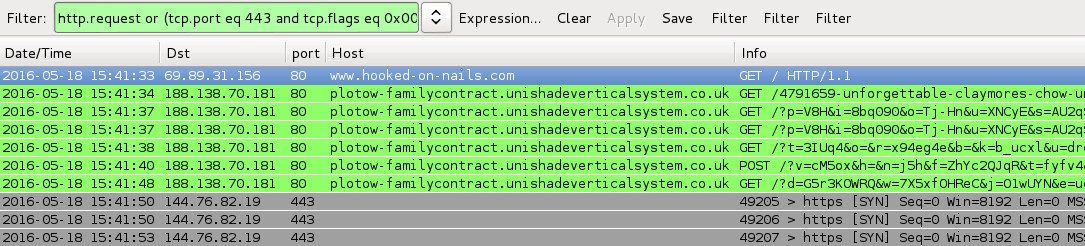
Shown aboe: Pcap of the traffic on a normal host filtered in Wireshark. http.request or (tcp.port eq 443 and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- 188.138.70[.]181 port 80 - plotow-familycontract.unishadeverticalsystem[.]co[.]uk - Angler EK
- 144.76.82[.]19 port 443 - post-infection traffic from today's CryptXXX ransomware (custom encoded)
IMAGES
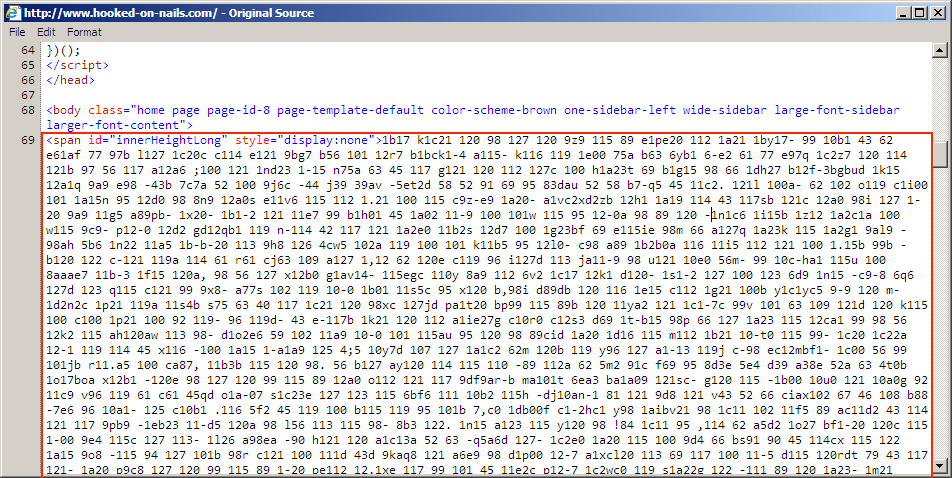
Shown above: Start of injected pseudo-Darkleech script from the compromised website.
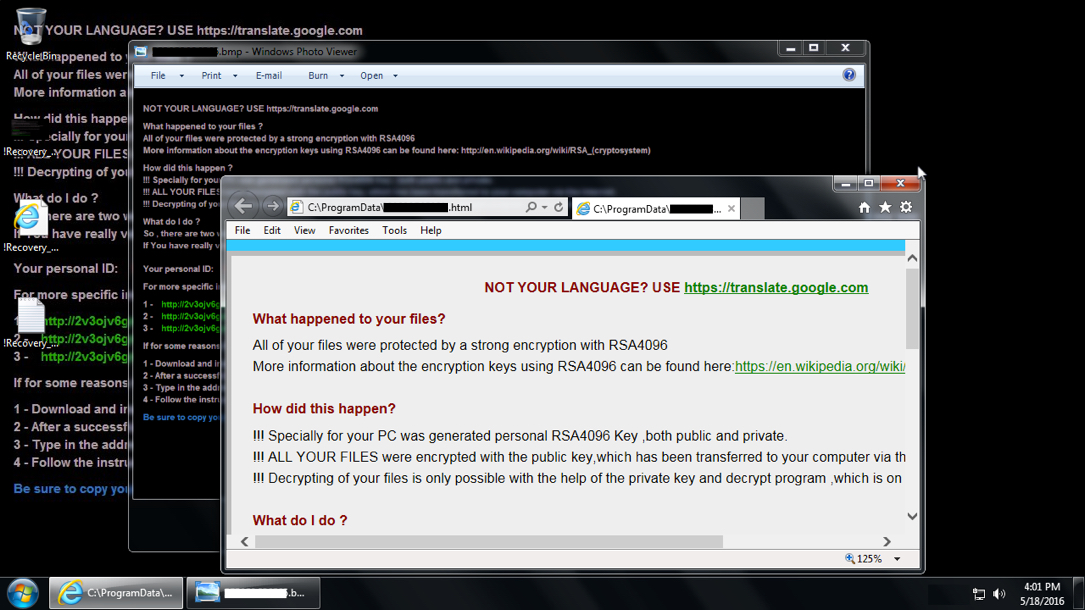
Shown above: Infected host after rebooting it to get past the lock screen.
Click here to return to the main page.