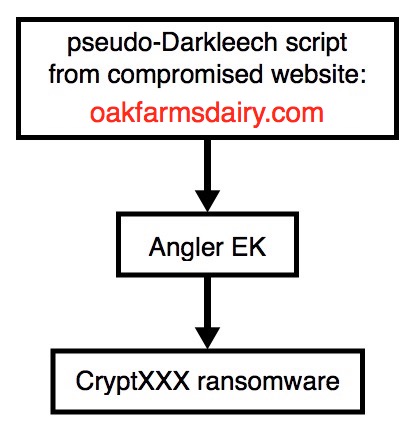
2016-05-23 - PSEUDO-DARKLEECH ANGLER EK FROM 91.134.206[.]131 SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-23-pseudo-Darkleech-Angler-EK-sends-CryptXXX-ransowmare-2-pcaps.zip 2.3 MB (2,288,824 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-sends-CryptXXX-ransomware-first-run.pcap (1,279,554 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-sends-CryptXXX-ransomware-second-run.pcap (1,247,480 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-and-CryptXXX-ransomware-files.zip 474.7 kB (474,696 bytes)
- 2016-05-23-CryptXXX-ransomware_decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-23-CryptXXX-ransomware_decrypt-instructions.html (14,190 bytes)
- 2016-05-23-CryptXXX-ransomware_decrypt-instructions.txt (1,755 bytes)
- 2016-05-23-page-from-oakfarmsdairy_com-with-injected-pseudoDarkleech-script-first-run.txt (16,096 bytes)
- 2016-05-23-page-from-oakfarmsdairy_com-with-injected-pseudoDarkleech-script-second-run.txt (17,105 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-flash-exploit-vs-flash-20.0.0.306.swf (66,735 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-flash-exploit-vs-flash-21.0.0.213.swf (67,574 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-landing-page-first-run.txt (104,443 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-landing-page-second-run.txt (104,475 bytes)
- 2016-05-23-pseudo-Darkleech-Angler-EK-payload-CryptXXX-ransomware.dll (311,296 bytes)
NOTES:
- Background on the pseudo-Darkleech campaign is available here.
- Proofpoint's blog on Angler EK spreading CryptXXX ransomware can be found here.
- An ISC diary I wrote about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections is located here.
- A follow-up from Proofpoint about CryptXXX ransomware is here
- As reported by @kafeine, Flash exploits for CVE-216-4117 are now in Angler EK ( link ).
- I did a second run of today's infection traffic to grab one of the CVE-2016-4117 flash exploits.
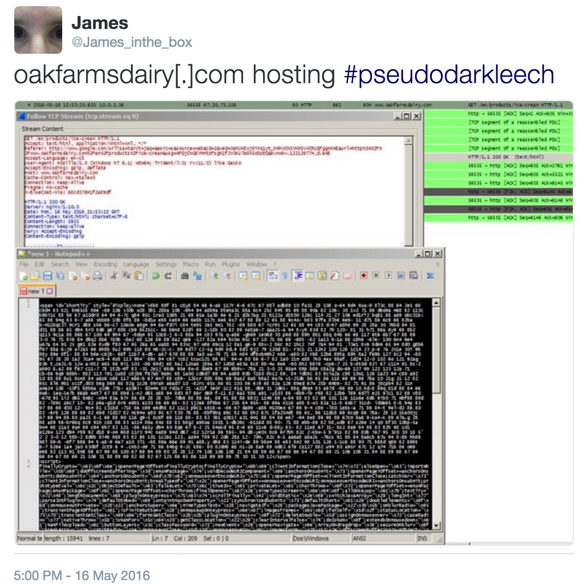
- Pseudo-Darkleech script from today's compromised website first reported by @James_inthe_box one week ago on 2016-05-16, and the website is still compromised.
Shown above: Tweet from last week about today's compromised website.
Shown above: Chain of events for today's infection.
TRAFFIC
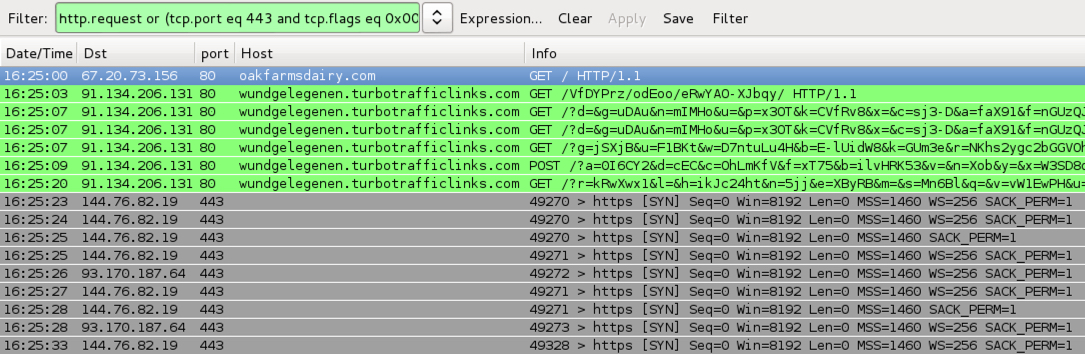
Shown aboe: Pcap of the traffic filtered in Wireshark, first run http.request or (tcp.port eq 443 and tcp.flags eq 0x0002)
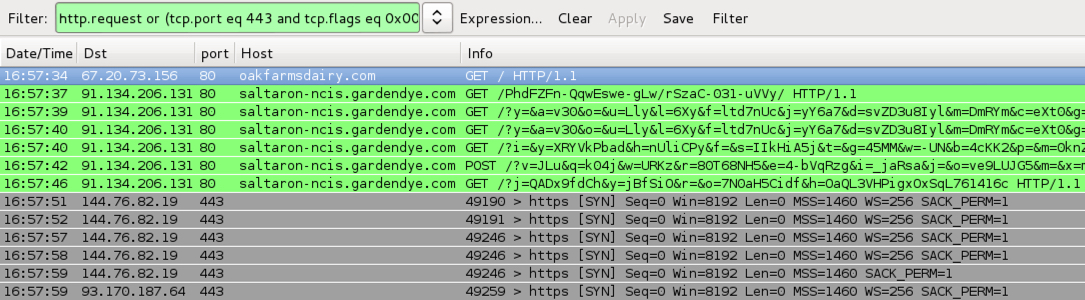
Shown aboe: Pcap of the traffic filtered in Wireshark, second run http.request or (tcp.port eq 443 and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- 91.134.206[.]131 port 80 - wundgelegenen.turbotrafficlinks[.]com - Angler EK (first run)
- 91.134.206[.]131 port 80 - saltaron-ncis.gardendye[.]com - Angler EK (second run)
- 144.76.82[.]19 port 443 - post-infection traffic from today's CryptXXX ransomware (custom encoded)
- 93.170.187[.]64 port 443 - post-infection traffic from today's CryptXXX ransomware (custom encoded)
Click here to return to the main page.