2016-05-24 - TUESDAY MALWARE HUNT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-24-traffic-and-files-from-malware-hunt.zip 15.6 MB (15,560,653 bytes)
NOTES:
- On Tuesday 2016-05-24, it seemed like the waves of malicious spam would never end, which gave me plenty of malware samples to detonate in my lab
- This blog post provides 20 malware samples and infection traffic from 5 waves of emails during the day.
- These messages all had .zip attachments containing different types of files designed to infect a Windows host with malware.
- 1st wave: .wsf files - Subject: Re:
- 2d wave: .js files that retrieved Locky ransomware sample 1 - Subject: SAFARI LPO [MAL] [random characters]
- 3d wave: .js files that retrieved Locky ransomware sample 2 - Subject: We Have Received Your Payment - Thank You (#[random characters])
- 4th wave: Word documents with macros that downloaded Dridex - Subject: Account Compromised
- 5th wave: .js files that retrieved Locky ransomware sample 1 - Fake HP Scanjet messages
EMAILS AND ATTACHMENTS
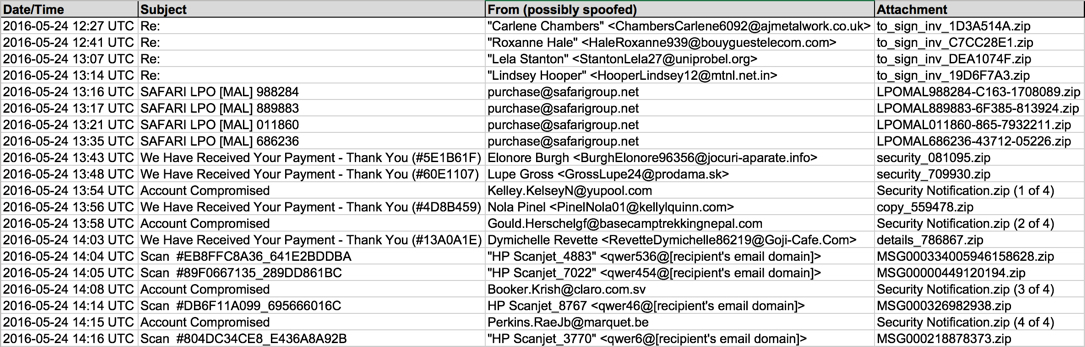
Shown above: Data from the .csv spreadsheet on 20 email examples from Tuesday 2016-05-24.

Shown above: Data from the .csv spreadsheet on 20 attachments from email samples on Tuesday 2016-05-24.
TRAFFIC
Shown above: Example of traffic from zip attachments containing .wsf files.
TRAFFIC GENERATED BY THE .WSF FILES FROM ZIP ATTACHMENTS IN THE EMAILS:
- 31.192.117[.]132 port 80 - pornhub[.]com - GET /x/xff.exe
- 31.192.117[.]132 port 80 - www.pornhub[.]com - GET /x/xff.exe
- 27.123.31[.]81 port 80 - albany.asn.au - GET /tldully
- 103.254.138[.]242 port 80 - australiancheerleader[.]com[.]au - GET /jsc1okam
- 23.229.205[.]70 port 80 - calcoastlogistics[.]com - GET /475v68r5
- 190.107.177[.]245 port 80 - copperbiohealth[.]com - GET /cfym5d
- 192.186.229[.]69 port 80 - deanstum[.]com - GET /okvb22kk
- 192.186.222[.]166 port 80 - muscleinjuries[.]com - GET /ra2gl
- 192.185.107[.]94 port 80 - wimaanburi[.]com - GET /1us6ct
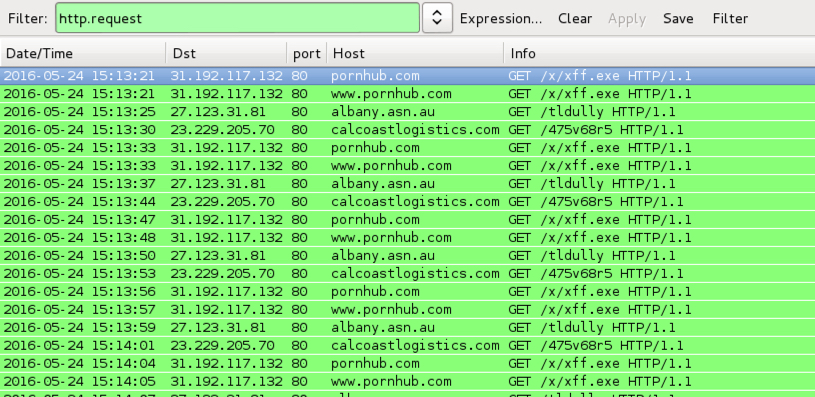
Shown above: Example of traffic from zip attachments containing .js files for first sample of Locky ransomware.
TRAFFIC GENERATED BY THE .JS FILES FROM ZIP ATTACHMENTS IN THE EMAILS FOR FIRST LOCKY RANSOMWARE SAMPLE:
- 31.170.164[.]47 port 80 - wcouto[.]com[.]br - GET /65g434f?BYjksQORYu=oOEcgTUgKm
- 37.140.192[.]214 port 80 - u0086064.cp.regruhosting[.]ru - GET /sdfg4g3?OrrfOT=roqiOxyJb
- 5.101.153[.]13 port 80 - ultramarincentr[.]ru - GET /43454yt32?dRvUUJed=UCpMTVxwDcW
- 5.101.153[.]13 port 80 - ultramarincentr[.]ru - GET /43454yt32?SfdHzDf=VryLtDX
- 69.50.139[.]6 port 80 - rsxxx[.]com - - GET /sdfg4g3?xCcrMQaTTMh=xJmjMBswvGn
- 79.172.201[.]24 port 80 - fdev[.]hu - - GET /43454yt32?wcDlLPVW=WxBBeYNCyix
- 79.98.24[.]9 port 80 - abdera[.]lt - - GET /65g434f?FPFALCX=VoIDDzOYe
- 79.98.28[.]25 port 80 - baltela[.]lt - GET /43454yt32?ebQufpId=vVGSAb
- 79.98.28[.]25 port 80 - baltela[.]lt - GET /43454yt32?vhhhymphK=FCefAU
- 79.98.28[.]54 port 80 - mylimajai[.]lt - GET /65g434f?kWnsWU=knYumWbvg
- 79.98.28[.]54 port 80 - sveikata-jums[.]lt - GET /65g434f?xcizamuIm=iEdQVSeHr
- 87.236.19[.]39 port 80 - siteriqi.bget[.]ru - GET /65g434f?gOftVcUHmCc=dFIFajfNGw
- 93.184.144[.]40 port 80 - edirnedh.gov[.]tr - GET /65g434f?PeIQsrPyQp=QEdRlG
- 107.180.56[.]179 port 80 - cinerd[.]info - GET /sdfg4g3?TDMaMY=FaNhtkMsu
- 166.62.28[.]112 port 80 - colleenthestylist[.]com - GET /43454yt32?VpNJfuhNdHb=fHdhoAO
- 173.236.147[.]27 port 80 - alpadv[.]com - GET /65g434f?oLHTADXe=nAQPux
- 178.20.153[.]53 port 80 - wp.sve-yurchenko[.]com - GET /sdfg4g3?UzKwesaMS=MQqEcvthg
- 178.20.153[.]53 port 80 - wp.sve-yurchenko[.]com - GET /sdfg4g3?xirjsOGcs=aLGGSNFop
- 178.20.153[.]53 port 80 - wp.sve-yurchenko[.]com - GET /sdfg4g3?UzKwesaMS=MQqEcvthg
- 191.101.152[.]144 port 80 - feserver[.]tk - GET /65g434f?XFiXXGAaiH=taXtfFvy
- 191.101.152[.]144 port 80 - srv02.dspinteractive[.]com - GET /sdfg4g3?gmUsGfD=wmQGygK
- 193.169.189[.]62 port 80 - mirstroyki[.]com[.]ua - GET /sdfg4g3?erfbHiH=LRtbKc
- 195.208.1[.]161 port 80 - panaceya.nichost[.]ru - GET /sdfg4g3?BObyzA=aebfvtXz
POST-INFECTION TRAFFIC FROM THE FIRST LOCKY RANSOMWARE SAMPLE:
- 31.41.44[.]45 port 80 - 31.41.44[.]45 - POST /userinfo.php
- 185.82.216[.]45 port 80 - 185.82.216[.]45 - POST /userinfo.php

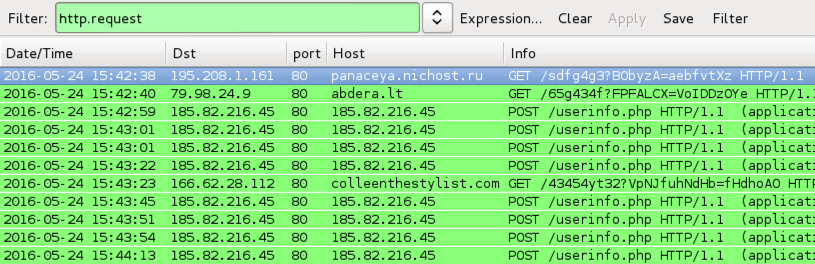
Shown above: Example of traffic from zip attachments containing .js files for second sample of Locky ransomware.
TRAFFIC GENERATED BY THE .JS FILES FROM ZIP ATTACHMENTS IN THE EMAILS FOR SECOND LOCKY RANSOMWARE SAMPLE:
- 52.202.214[.]24 port 80 - sasuraijourney[.]com - GET /8RrwT9.exe
- 178.19.147[.]34 port 80 - bagnifico[.]com - GET /8Jl4NZ.exe
- 212.83.144[.]126 port 80 - bolkaart[.]com - GET /VQ2FoR.exe
- 221.231.139[.]22 port 80 - aumu[.]com - GET /a2Mj6U.exe
POST-INFECTION TRAFFIC FROM THE SECOND LOCKY RANSOMWARE SAMPLE:
- 31.41.44[.]45 port 80 - 31.41.44[.]45 - POST /userinfo.php
- 185.82.216[.]45 port 80 - 185.82.216[.]45 - POST /userinfo.php
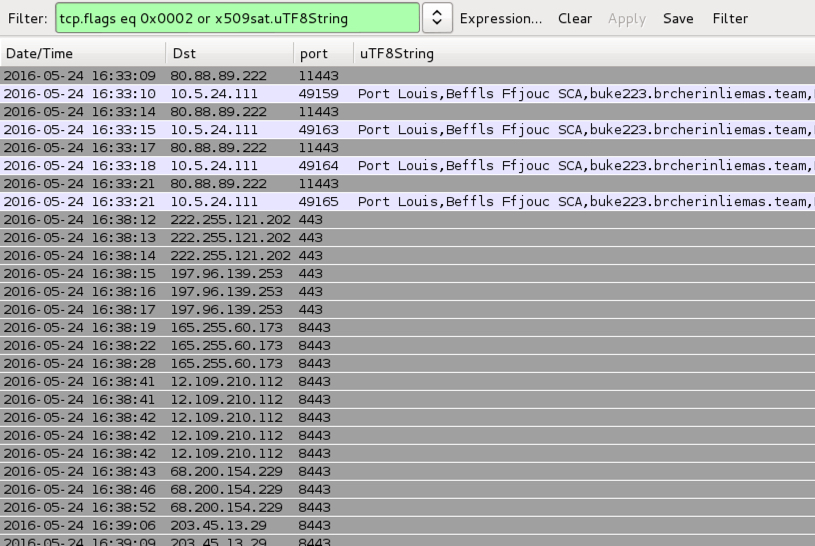
Shown above: Example of traffic from zip attachments containing the .doc files for Dridex.
INITIAL HTTPS TRAFFIC AFTER ENABLING MACROS ON FROM ZIP FILES CONTAINING WORD DOCS FOR DRIDEX:
- 80.88.89[.]222 port 11443 - HTTPS traffic with the following certificate:
- countryName = MU
- localityName = Port Louis
- organizationName = Beffls Ffjouc SCA
- commonName = buke223.brcherinliemas[.]team
ENCRYPTED TRAFFIC OR ATTEMPTED CONNECTIONS FROM THE DRIDEX INFECTIONS:
- 12.109.210[.]112 port 8443
- 68.200.154[.]229 port 8443
- 72.27.47[.]17 port 8443
- 75.67.214[.]42 port 8443
- 96.93.247[.]161 port 8443
- 101.187.28[.]8 port 8443
- 165.255.60[.]173 port 8443
- 197.96.139[.]253 port 443
- 203.45.13[.]29 port 8443
- 222.255.121[.]202 port 443
IMAGES

Shown above: SSL certificate info from one of the Dridex pcaps.
ZIP ARCHIVE CONTENTS
- 2016-05-24-email-tracker.csv (3,419 bytes)
- artifacts-from-infected-hosts/2016-05-24-Dridex-artifact-AppData-LocalLow-(random_characters).tmp (342,528 bytes)
- artifacts-from-infected-hosts/2016-05-24-Dridex-example-AppData-Local-Temp-harakiri.exe (184,320 bytes)
- artifacts-from-infected-hosts/2016-05-24-Dridex-example-AppData-Local-Temp-harakiri.pfx (245,760 bytes)
- artifacts-from-infected-hosts/2016-05-24-Locky-ransomware-sample-1-of-2.exe (249,856 bytes)
- artifacts-from-infected-hosts/2016-05-24-Locky-ransomware-sample-2-of-2.exe (416,256 bytes)
- artifacts-from-infected-hosts/2016-05-24-Locky-ransomware_RESTORE_instructions.bmp (4,006,594 bytes)
- artifacts-from-infected-hosts/2016-05-24-Locky-ransomware_RESTORE_instructions.html (9,940 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-1.exe (179,305 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-2.exe (179,312 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-3.exe (179,311 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-4.exe (179,311 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-5.exe (179,307 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-6.exe (179,307 bytes)
- artifacts-from-infected-hosts/2016-05-24-binary-sent-by-wsf-file-decoded-sample-7.exe (179,312 bytes)
- artifacts-from-infected-hosts/2016-05-24-malware-sent-alongside-Locky-ransomware.exe (787,968 bytes)
- attachments/LPOMAL011860-865-7932211.zip (3,758 bytes)
- attachments/LPOMAL686236-43712-05226.zip (3,798 bytes)
- attachments/LPOMAL889883-6F385-813924.zip (3,772 bytes)
- attachments/LPOMAL988284-C163-1708089.zip (3,750 bytes)
- attachments/MSG00000449120194.zip (3,787 bytes)
- attachments/MSG000218878373.zip (3,775 bytes)
- attachments/MSG000326982938.zip (3,730 bytes)
- attachments/MSG000334005946158628.zip (3726 bytes)
- attachments/Security Notification 1 of 4.zip (137,915 bytes)
- attachments/Security Notification 2 of 4.zip (137,917 bytes)
- attachments/Security Notification 3 of 4.zip (137,917 bytes)
- attachments/Security Notification 4 of 4.zip (137,915 bytes)
- attachments/copy_559478.zip (42,323 bytes)
- attachments/details_786867.zip (41,395 bytes)
- attachments/security_081095.zip (40,495 bytes)
- attachments/security_709930.zip (40,615 bytes)
- attachments/to_sign_inv_19D6F7A3.zip (5,274 bytes)
- attachments/to_sign_inv_1D3A514A.zip (5,032 bytes)
- attachments/to_sign_inv_C7CC28E1.zip (5,013 bytes)
- attachments/to_sign_inv_DEA1074F.zip (5,064 bytes)
- emails/2016-05-24-malspam-1227-UTC.eml (7,859 bytes)
- emails/2016-05-24-malspam-1241-UTC.eml (7,839 bytes)
- emails/2016-05-24-malspam-1307-UTC.eml (7,868 bytes)
- emails/2016-05-24-malspam-1314-UTC.eml (8,168 bytes)
- emails/2016-05-24-malspam-1316-UTC.eml (5,895 bytes)
- emails/2016-05-24-malspam-1317-UTC.eml (5,987 bytes)
- emails/2016-05-24-malspam-1321-UTC.eml (5,960 bytes)
- emails/2016-05-24-malspam-1335-UTC.eml (6,000 bytes)
- emails/2016-05-24-malspam-1343-UTC.eml (56,720 bytes)
- emails/2016-05-24-malspam-1348-UTC.eml (56,874 bytes)
- emails/2016-05-24-malspam-1354-UTC.eml (188,611 bytes)
- emails/2016-05-24-malspam-1356-UTC.eml (59,251 bytes)
- emails/2016-05-24-malspam-1358-UTC.eml (188,712 bytes)
- emails/2016-05-24-malspam-1403-UTC.eml (57,938 bytes)
- emails/2016-05-24-malspam-1404-UTC.eml (6,503 bytes)
- emails/2016-05-24-malspam-1405-UTC.eml (6,559 bytes)
- emails/2016-05-24-malspam-1408-UTC.eml (188,647 bytes)
- emails/2016-05-24-malspam-1414-UTC.eml (6,483 bytes)
- emails/2016-05-24-malspam-1415-UTC.eml (188,640 bytes)
- emails/2016-05-24-malspam-1416-UTC.eml (6,533 bytes)
- extracted-files/DEOF-3315945.js (9,014 bytes)
- extracted-files/LIT-1803889.js (9,000 bytes)
- extracted-files/ONOQ-0201334.js (8,973 bytes)
- extracted-files/ONPC-1404638.js (9,080 bytes)
- extracted-files/Security Report ID(11028949).doc (287,232 bytes)
- extracted-files/Security Report ID(14223913).doc (287,232 bytes)
- extracted-files/Security Report ID(14336017).doc (287,232 bytes)
- extracted-files/Security Report ID(14597593).doc (287,232 bytes)
- extracted-files/XJGN-3701141.js (9,099 bytes)
- extracted-files/XJW-0710211.js (8,900 bytes)
- extracted-files/XLYG-4006858.js (9,212 bytes)
- extracted-files/YXJ-4712391.js (8,794 bytes)
- extracted-files/customers 040.wsf (20,943 bytes)
- extracted-files/customers 4693.wsf (19,852 bytes)
- extracted-files/customers 517.wsf (19,787 bytes)
- extracted-files/customers 578.wsf (19,914 bytes)
- extracted-files/details_JCu4pc.js (59,535 bytes)
- extracted-files/doc_scan_XsVnUl.js (59,848 bytes)
- extracted-files/document_fWdwLI.js (61,663 bytes)
- extracted-files/scan_VOOLp.js (65,037 bytes)
- pcaps/2016-05-24-traffic-after-running-DEOF-3315945.js.pcap (576,958 bytes)
- pcaps/2016-05-24-traffic-after-running-LIT-1803889.js.pcap (1,309,550 bytes)
- pcaps/2016-05-24-traffic-after-running-ONOQ-0201334.js.pcap (455,360 bytes)
- pcaps/2016-05-24-traffic-after-running-ONPC-1404638.js.pcap (574,350 bytes)
- pcaps/2016-05-24-traffic-after-running-Security_Report_ID(11028949).doc.pcap (379,310 bytes)
- pcaps/2016-05-24-traffic-after-running-Security_Report_ID(14223913).doc.pcap (652,956 bytes)
- pcaps/2016-05-24-traffic-after-running-Security_Report_ID(14336017).doc.pcap (395,968 bytes)
- pcaps/2016-05-24-traffic-after-running-Security_Report_ID(14597593).doc.pcap (663,908 bytes)
- pcaps/2016-05-24-traffic-after-running-XJGN-3701141.js.pcap (733,895 bytes)
- pcaps/2016-05-24-traffic-after-running-XJW-0710211.js.pcap (848,242 bytes)
- pcaps/2016-05-24-traffic-after-running-XLYG-4006858.js.pcap (295,240 bytes)
- pcaps/2016-05-24-traffic-after-running-YXJ-4712391.js.pcap (457,281 bytes)
- pcaps/2016-05-24-traffic-after-running-customers_040.wsf.pcap (552,625 bytes)
- pcaps/2016-05-24-traffic-after-running-customers_4693.wsf.pcap (3,579,385 bytes)
- pcaps/2016-05-24-traffic-after-running-customers_517.wsf.pcap (2,813,806 bytes)
- pcaps/2016-05-24-traffic-after-running-customers_578.wsf.pcap (4,235,199 bytes)
- pcaps/2016-05-24-traffic-after-running-details_JCu4pc.js.pcap (407,490 bytes)
- pcaps/2016-05-24-traffic-after-running-doc_scan_XsVnUl.js.pcap (1,204 bytes)
- pcaps/2016-05-24-traffic-after-running-document_fWdwLI.js.pcap (4685,53 bytes)
- pcaps/2016-05-24-traffic-after-running-scan_VOOLp.js.pcap (440,844 bytes)
Click here to return to the main page.
