2016-06-01 - RIG EK FROM 46.30.46[.]6 SENDS TOFSEE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-01-Rig-EK-sends-Tofsee.pcap.zip 629.7 kB (629,723 bytes)
- 2016-06-01-Rig-EK-sends-Tofsee.pcap (1,449,812 bytes)
- 2016-06-01-Rig-EK-and-Tofsee-files.zip 573.7 kB (573,717 bytes)
- 2016-06-01-Rig-EK-flash-exploit.swf (37,819 bytes)
- 2016-06-01-Rig-EK-landing-page.txt (4,982 bytes)
- 2016-06-01-Rig-EK-payload-Tofsee.exe (241,664 bytes)
- 2016-06-01-lluuitgg.exe (42,704,896 bytes) [Found on the infected host at: C:\Users\username\lluuitgg.exe]
NOTES:
- Same type of infection seen on 2016-04-21, with the same compromised website and same gate domain (link).
TRAFFIC
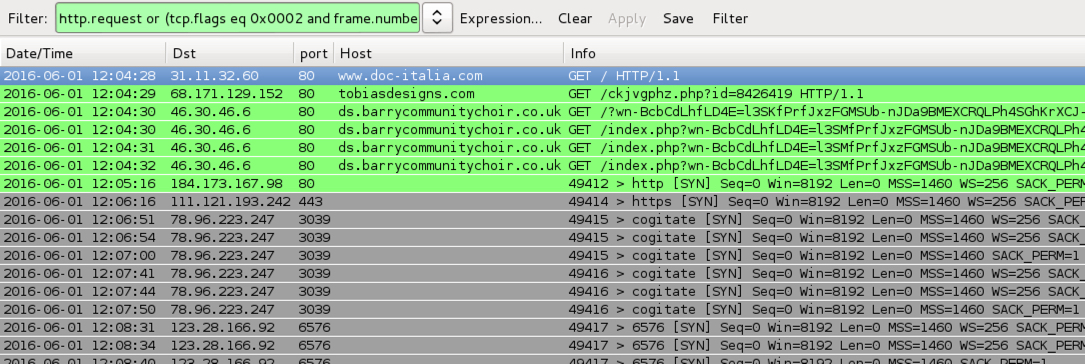
Shown above: Pcap of the traffic filtered in Wireshark.
GATE AND RIG EK:
- 68.171.129[.]152 port 80 - tobiasdesigns[.]com - GET /ckjvgphz.php?id=8426419 [gate/redirect]
- 46.30.46[.]6 port 80 - ds.barrycommunitychoir[.]co[.]uk - Rig EK
TOFSEE POST-INFECTION TRAFFIC:
- 111.121.193[.]242 port 443
OTHER TCP CONNECTIONS OR ATTEMPTED CONNECTIONS FROM THE INFECTED HOST:
- 23.96.52[.]53 port 80
- 27.76.200[.]236 port 1480
- 78.96.223[.]247 port 3039
- 86.101.172[.]244 port 2639
- 88.247.23[.]60 port 6859
- 94.111.35[.]133 port 1103
- 103.62.255[.]92 port 8575
- 104.40.211[.]35 port 80
- 112.201.214[.]21 port 7371
- 115.73.16[.]161 port 9980
- 120.63.221[.]199 port 1061
- 122.160.166[.]241 port 3205
- 122.163.24[.]91 port 3879
- 122.163.193[.]181 port 4146
- 123.28.166[.]92 port 6576
- 176.113.145[.]235 port 2358
- 180.183.195[.]29 port 5674
- 184.173.167[.]98 port 80
- 202.91.73[.]186 port 9393
Click here to return to the main page.
