2016-06-02 - EK DATA DUMP (ANGLER EK, KAIXIN EK, RIG EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-02-EK-dump-6-pcaps.zip 2.7 MB (2,738,033 bytes)
- 2016-06-02-KaiXin-EK-from-98.126.83_188-port-82.pcap (169,581 bytes)
- 2016-06-02-KaiXin-EK-from-cbat_or_kr.pcap (113,097 bytes)
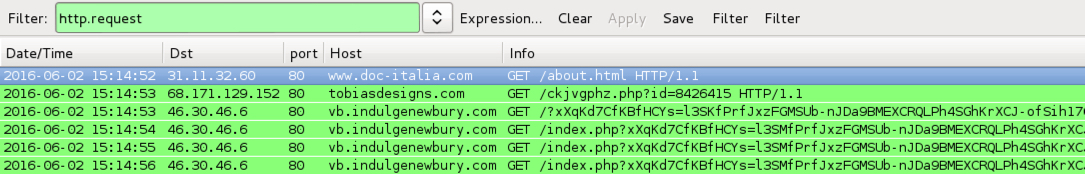
- 2016-06-02-Rig-EK-after-doc-italia_com.pcap (325,318 bytes)
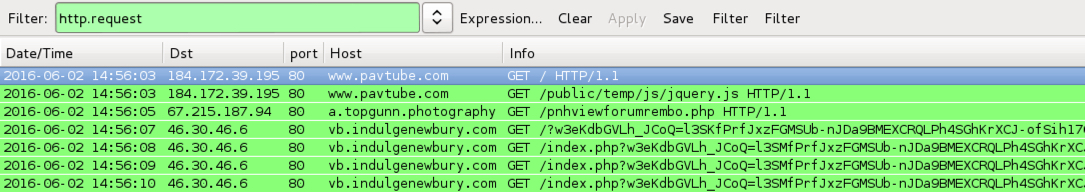
- 2016-06-02-Rig-EK-after-pavtube_com.pcap (482,411 bytes)
- 2016-06-02-other-Angler-EK-after-woogerworks_com.pcap (1,093,571 bytes)
- 2016-06-02-pseudoDarkleech-Angler-EK-after-mfgsci_com.pcap (1,175,862 bytes)
- 2016-06-02-EK-data-dump-malware-and-artifacts.zip 989.3 kB (989,325 bytes)
- 2016-06-02-98.126.83_188-port-82-ZnUaLm.html.txt (16,122 bytes)
- 2016-06-02-98.126.83_188-port-82-index.html.txt (15,663 bytes)
- 2016-06-02-98.126.83_188-port-82-jquery.js.txt (15,728 bytes)
- 2016-06-02-98.126.83_188-port-82-logo.swf (30,337 bytes)
- 2016-06-02-98.126.83_188-port-82-swfobject.js.txt (12,624 bytes)
- 2016-06-02-98.126.83_189-port-82-smss.exe (56,064 bytes)
- 2016-06-02-Angler-EK-flash-exploit.swf (40,784 bytes)
- 2016-06-02-Rig-EK-flash-exploit.swf (378,17 bytes)
- 2016-06-02-Rig-EK-landing-page-after-doc-italia_com.txt (4,910 bytes)
- 2016-06-02-Rig-EK-landing-page-after-pavtube_com.txt (4,906 bytes)
- 2016-06-02-Rig-EK-payload-after-doc-italia_com.exe (249,856 bytes)
- 2016-06-02-Rig-EK-payload-after-pavtube_com.exe (339,968 bytes)
- 2016-06-02-a.topgunn_photography-pnhviewforumrembo.php.txt (944 bytes)
- 2016-06-02-cbat_or_kr-MzVuOo.html.txt (16,104 bytes)
- 2016-06-02-cbat_or_kr-SmSnRq.html.txt (10,183 bytes)
- 2016-06-02-cbat_or_kr-index.html.txt (9,507 bytes)
- 2016-06-02-cbat_or_kr-jquery.js.txt (15,728 bytes)
- 2016-06-02-cbat_or_kr-logo.swf (30,349 bytes)
- 2016-06-02-cbat_or_kr-swfobject.js.txt (12,624 bytes)
- 2016-06-02-other-Angler-EK-payload-CryptXXX-ransomware-after-woogerworks_com.dll (155,648 bytes)
- 2016-06-02-other-Angler-EK-payload-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-02-other-Angler-EK-payload-CryptXXX-ransomware-decrypt-instructions.html (14,190 bytes)
- 2016-06-02-other-Angler-EK-payload-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-06-02-page-from-mfgsci_com-with-injected-pseudoDarkleech-script.txt (50,490 bytes)
- 2016-06-02-pseduoDarkleech-Angler-EK-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-02-pseduoDarkleech-Angler-EK-CryptXXX-ransomware-decrypt-instructions.html (14,190 bytes)
- 2016-06-02-pseduoDarkleech-Angler-EK-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-06-02-pseudoDarkleech-Angler-EK-landing-page-after-mfgsciphotographycom.txt (7,1657 bytes)
- 2016-06-02-pseudoDarkleech-Angler-EK-payload-CryptXXX-ransomware-after-mfgsciphotographycom.dll (286,720 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
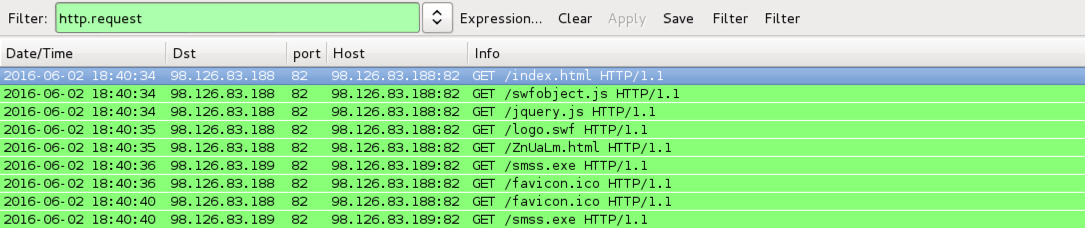
- 98.126.83[.]188 port 82 - 98.126.83[.]188:82 - KaiXin EK
- 98.126.83[.]189 port 82 - 98.126.83[.]189:82 - GET /smss.exe - KaiXin EK payload
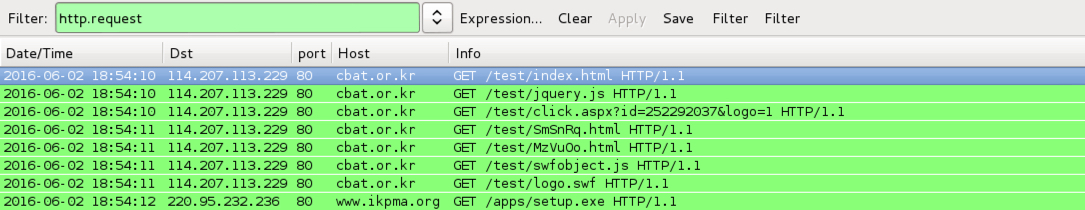
- 114.207.113[.]229 port 80 - cbat[.]or[.]kr - KaiXin EK
- 220.95.232[.]236 port 80 - www.ikpma[.]org - GET /apps/setup.exe - KaiXin EK payload (nothing returned)
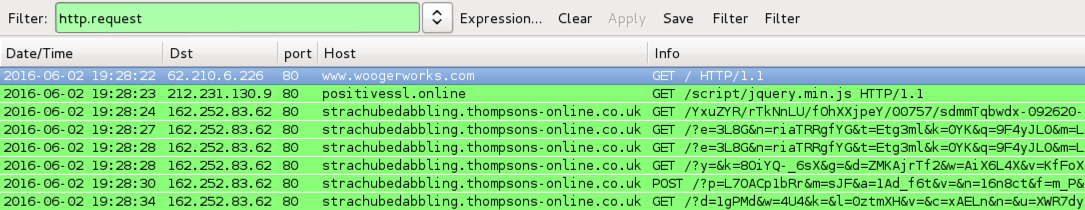
- 212.231.130[.]9 port 80 - positivessl[.]online - GET /script/jquery.min.js - possible gate to Angler EK (I think)
- 162.252.83[.]62 port 80 - strachubedabbling.thompsons-online[.]co[.]uk - Angler EK
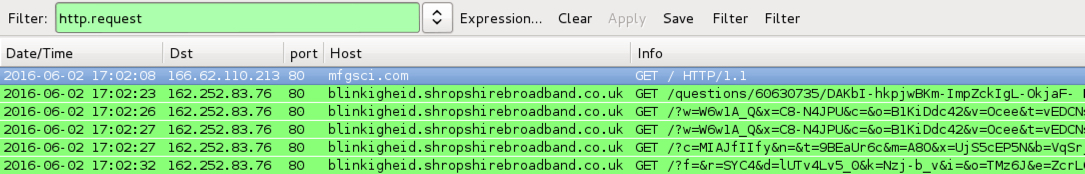
- 162.252.83[.]76 port 80 - blinkigheid.shropshirebroadband[.]co[.]uk - Angler EK
- 85.25.194[.]116 port 443 - CryptXXX ransomware callback traffic
- 68.171.129[.]152 port 80 - tobiasdesigns[.]com - GET /ckjvgphz.php?id=8426415 - gate pointing to Rig EK
- 67.215.187[.]94 port 80 - a.topgunn[.]photography - Gate/redirect data pointing to Rig EK
- 46.30.46[.]6 port 80 - vb.indulgenewbury[.]com - Rig EK
Click here to return to the main page.
